The Good
This week we have another law enforcement victory to highlight. The grand jury indictment (in USA and Canada) of Mathew Philbert was the result of “Project CODA”, a joint operation between Europol, the FBI, and Canada’s Ontario Provincial Police (O.P.P.). Project CODA began in early 2020 after the FBI contacted Canadian law enforcement for help with an investigation into various ransomware attacks on U.S. businesses originating in Canada.
Philbert, described as one of Canada’s “most prolific cybercriminals’, was formally charged in connection with numerous claims of fraud and cyber crime, including ransomware attacks and bot operation. The indictment covers multiple counts from the 2018 timeframe, though the individual is allegedly tied to a host of other attacks dating back many years. Authorities also seized a plethora of laptops, phones, drives, carding blanks, and crypto-wallet metadata that assist in tying Philbert to the crimes.

Philbert was notoriously one of the original Darkode forum members back in 2009, as well as being active on many other established underground forums and markets. He has also been tied to the operation of at least one Mariposa-based botnet. Perhaps the most eye-opening aspect of the charges is the clear indication that Philbert was attacking medical facilities during the alleged time.
While the events in question predate the current global situation, any attack on a medical entity is reprehensible, so we have one more victory for global law enforcement to cheer and one less prolific criminal off the grid. Hooray!
The Bad
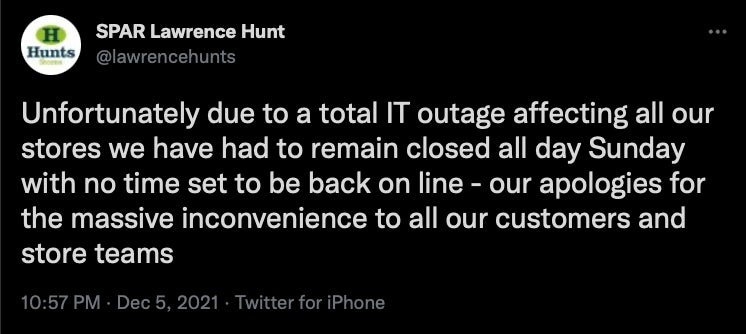
This was a rough week for the retail industry with regard to ransomware attacks. North of 300 outlets of the SPAR supermarket chain were affected by an apparent ransomware incident. As a result of the attack, many locations were forced to close, while others had to resort to processing transactions on paper.
A SPAR spokesperson stated that the attack was:
At the time of writing, there is no clear indication of the ransomware family involved, nor is there any detail on the payment status of the ransom.
A similar scenario played out at The Delta-Montrose Electric Association (DMEA). The member-owned electric cooperative in Colorado has also revealed they were the subject of a breach, including the use of “file-encrypting malware”. At the time, the attack led to nearly 90% of their internal systems being out or affected in a negative way. As with the SPAR situation, there is currently no confirmed data on which ransomware family was involved.
Both victims are on the road to recovery, but these attacks serve as a reminder of the importance of prevention when it comes to ransomware.
The Ugly
Life in Russia became much more difficult for TOR users this week. On December 1, Russia’s Roskomnadzor (aka the Federal Service for Supervision of Communications, Information Technology, and Mass Media) started blocking traffic on TOR nodes. That was followed this week by a block on access to TOR’s main site.
Attempting to explain the reasons for the action, a spokesperson for Roskomnadzor said:
The country’s crackdown on Tor is just the latest in a wave of censorships over the last few months that have seen Apple forced to turn off its Private Relay service, Opera to remove its browser’s VPN and ten other VPNs being blocked. In response to the latest action, the TOR team have created a website mirror which can be persistently accessed, even by citizens in Russia.

Meanwhile, a non-amateur level and persistent group threat actor has been running thousands of TOR relays for at least four years in what looks like a systematic Sybil attack, essentialy an attempt to deanonymize TOR traffic or collect information on users to map their routes through the network.
It is estimated that, at one point, as much as 10% of the TOR network could have been under the control of a single entity. All the identified servers have been removed, but researchers believe the effort is ongoing and are actively hunting for more suspicious relays.