The Good
Eight months ago, Kaseya’s remote network management product (VSA) was abused in order to push REvil ransomware. The attacker(s) pushed a malicious update, effectively encrypting thousands of machines at hundreds of organizations. This week, the Justice Department announced the arrest of one of the alleged perpetrators. Yaroslav Vasinskyi, a 22 year old Ukranian national, was arrested in Poland and extradited to the United States. Charged with conspiracy to commit fraud, damage to protected computers, and conspiracy to commit money laundering, Vasinskyi faces a total 115 years in prison if convicted.
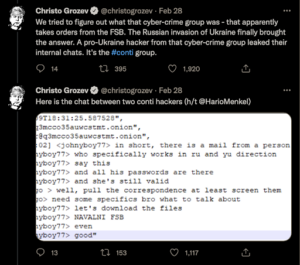
Additional unexpected gains are being made in the fight against ransomware as schisms in some of the biggest ransomware cartels have resulted in extensive leaks. The result is an unprecedented level of visibility into the inner workings of infamous groups like Conti and Trickbot. Soon after Conti announced its support for the Russian government’s invasion of Ukraine, a disgruntled insider released years worth of the group’s internal Jabber chat logs. The logs include a wealth of clues pointing to the identities of Conti operators previously known only by their online handles.
Researchers continue to dig into these chat logs, uncovering all sorts of details about the organization’s structure, leadership, and day-to-day operations. The mundane inner workings include office politics, management issues, and requests for paid leave. More notably, the leak also establishes explicit levels of coordination between Conti’s leadership and the Russian government in attempts to collect information on Alexey Navalny, a Russian opposition leader and anti-corruption activist.
While the Conti leaks are still being analyzed by researchers and journalists, the Trickbot leaks are being dropped in a more organized and purposeful fashion. A series of twitter accounts have been steadily disseminating dossiers of different Trickbot operators alongside their respective chat logs. In some cases, the PDFs associate an online handle with personally identifiable information including real names, dates of birth, passport numbers, addresses, and residential history.

Work has gone into these profiles, which makes us naturally suspicious of their provenance and reliability. In the case of both leaks, there’s the possibility of data being altered to misdirect investigators. Nonetheless, the leaks paint some explicit targets for law enforcement agencies to follow up on.
The Bad
There’s an onslaught of attacks attempting to disconnect Ukranians from the internet. This week has seen at least two instances of attacks on satellite internet operators servicing Ukraine. In an apparent attempt to disable critical communication channels, attackers have been bricking or jamming satellite modems. The first reports of satellite internet outages originated from Germany where early reports suggested that wind turbines were rendered inoperable due to a loss of internet service, apparent fallout from attacks aimed at Ukrainian customers. Viasat later confirmed that their KA-SAT service was down due to a ‘cyber event’. While technical details are sparse, it appears that the attackers may have pushed a malicious update to all KA-SAT modems, effectively bricking them. Similarly, Starlink terminals were subjected to signal jamming.
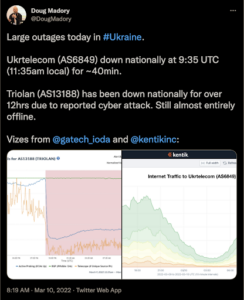
Interfering with satellite internet connections isn’t the only attempt to isolate Ukrainian citizens and organizations. Reports indicate that Urktelecom, Ukraine’s main telco and internet service provider, was down nationwide for 40 minutes. This was followed by an announcement by Triolan, a Ukrainian internet service provider, of an extensive outage due to a ‘cyber attack’. The company addressed concerns via Telegram, referring to the attack as a ‘dastardly enemy strategy that is trying to […] disrupt the operation of information networks and leave people without communication’. There are sparse technical details at this time.
The Ugly
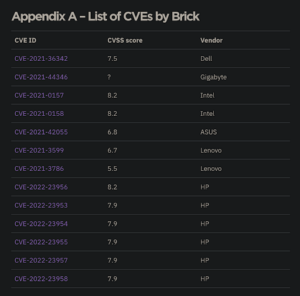
Firmware underlies all of our devices. It’s the layer of software that provides the low-level controls for the specific hardware we use. Unfortunately, the more security researchers pay attention to this software layer, the more it becomes clear that most firmware is riddled with serious vulnerabilities. This week, researchers at Binarly announced the discovery of 16 high-impact vulns in HP firmware, affecting laptops, desktops, point-of-sale systems, and edge computing nodes. If that’s not enough, this is the same team of researchers that announced the discovery of 23 vulnerabilities in a firmware software development kit (SDK) affecting 25 different vendors.
Firmware vulnerabilities are particularly troubling because components like the System Management Mode (SMM) have privileges greater than the operating system’s kernel. That concern is compounded by a lack of visibility into these components and the fact that attackers have not failed to exploit this porous layer. Multiple firmware rootkits have been discovered recently in-the-wild, including MoonBounce and ESPecter.
If you’re interested in learning more about firmware vulnerabilities, SentinelLabs researcher Assaf Carlsbad has published a six-part series introducing UEFI and SMM bug hunting. The series walks aspiring firmware security researchers through the process of dumping firmware, analyzing it statically and dynamically, fuzzing it, and identifying vulnerabilities. This week’s installment introduces a new plugin called ‘Brick’ that automates the discovery of SMM vulnerabilities with surprising results.