The Good
European Union regulators have announced progress in their attempts to force ‘big tech’ companies to police the content promoted on their platforms. The ‘Digital Services’ and ‘Digital Markets’ Acts come at a time of heightened concern about the role that social media, ad platforms, and search engines play in the spread of misinformation and disinformation.
The past six years have seen an increase in coordinated disinformation campaigns ranging from stoking conspiracy theories to spreading false claims about vaccines, with some resulting in tragic real-world consequences. Attempts to self-regulate content have not curbed the prevalence of this intentionally toxic content, and there’s a perception that the companies managing these services could do more to improve the situation but are besieged by perverse incentives.

These concerns have gained traction in the wake of the Facebook whistleblower Frances Haugen’s allegations of intentional disregard for the health and wellbeing of users in favor of greater profits. The larger concern is that a paradigm of targeted ads allows for unprecedented targeting of specific user verticals (race, gender, religion, political-leaning, etc) that allow malicious actors to widen societal rifts by promoting conflicting incompatible narratives in different social silos.
While the EU regulations are not final and still subject to change, they mark a concerted first step towards regulating ‘dark patterns’ and perverse incentives in the content promotion space.
The Bad
As if cryptocurrency weren’t fraught with enough perils, the FBI, Treasury Department, and CISA released a joint advisory detailing yet another North Korean campaign targeting cryptocurrency organizations and users. The campaign, titled ‘TraderTraitor’, involved spearphishing campaigns offering lucrative opportunities to encourage victims to download cryptocurrency-themed malware.
Open-source cryptocurrency trading and price-predicting applications were altered to include an ‘update’ mechanism that would instead download and execute a malicious payload. Victims were served Windows or macOS variants of a known Lazarus Group backdoor named ‘Manuscrypt’ that serves as a custom-written general purpose backdoor allowing the attackers to conduct post-compromise activities.
This is far from the first time that North Korean APTs target cryptocurrency exchanges and users. A previous operation in 2018, referred to as ‘AppleJeus’, employed a similar approach of trojanizing a legitimate cryptocurrency trading application. The malware presented itself as an application called Celas Trade Pro, with versions for Windows and macOS, and was used to deliver a second-stage RAT. In mid-2019, another variant of a cryptocurrency trading application delivering malware was discovered, signed and distributed by a seemingly legitimate company called JMT Trading. Continuing the trend, yet another variant UnionCryptoTrader was discovered in December of the same year.
The worst aspect of this is that it’s proven successful enough to bear repeating. North Korean threat actors have shown that a heavily sanctioned state can still effectively use cybercrime to partially circumvent sanctions. South Korean media outlets have claimed that North Korean hackers have pilfered a staggering $1.7 billion from cryptocurrency exchanges alone. Considering that the recently acknowledged breach of the Ronin network allegedly netted them $620 million in cryptocurrency, the real number is likely much higher.
We can’t help but wonder what an increasingly sanctioned Russian state will take away from the success of North Korea’s illicit tactics.
The Ugly
Cyber attacks on Industrial Control Systems are a nightmare scenario often bandied about but thankfully seldom witnessed. In the past week, that peaceful streak has been broken twice as notable attacks targeting ICS were uncovered.
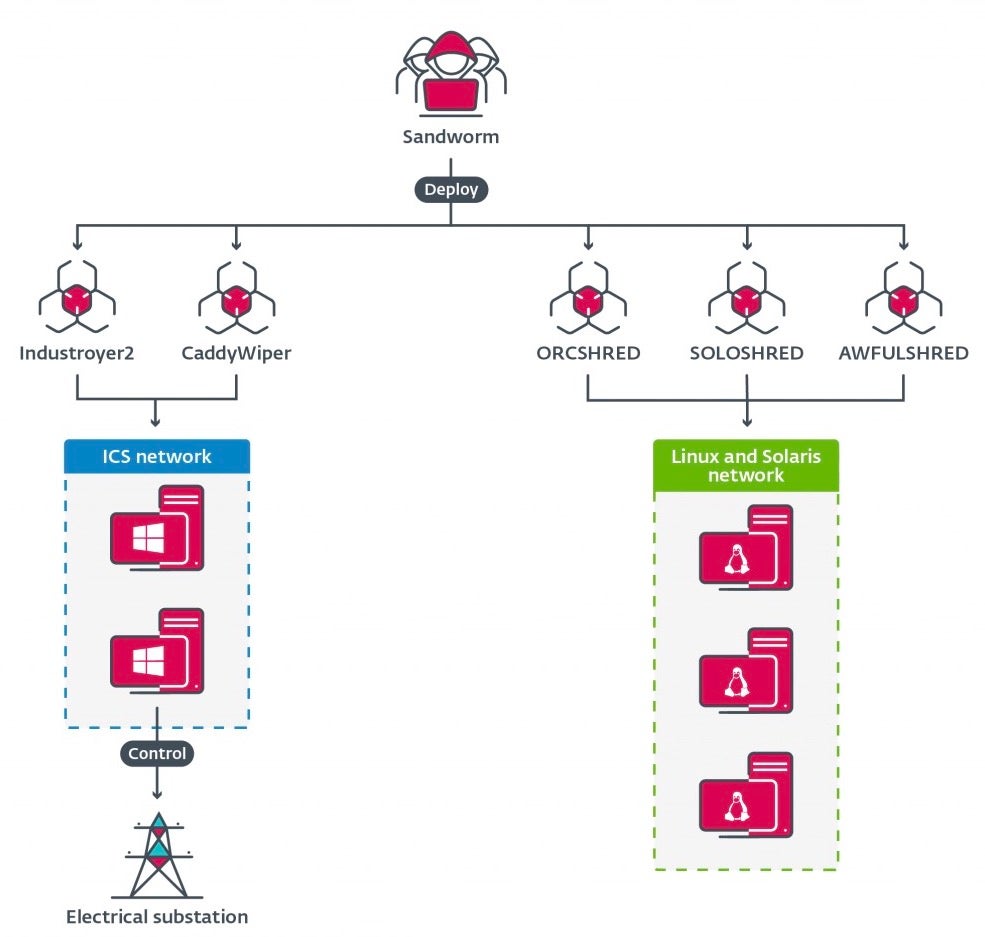
First, Cert-UA and ESET announced the discovery of Industroyer2, malware used by the Russian GRU team known as ‘Sandworm’, to attack power generation companies in Ukraine. The original Industroyer was used to disrupt the Ukrainian power grid in 2016. The attackers are back with a newer simplified version of the malware aimed once again at disrupting power for large swaths of Ukrainian territory. The attack was accompanied by 4 different strains of wiper malware targeting Windows, Linux, and Solaris systems.
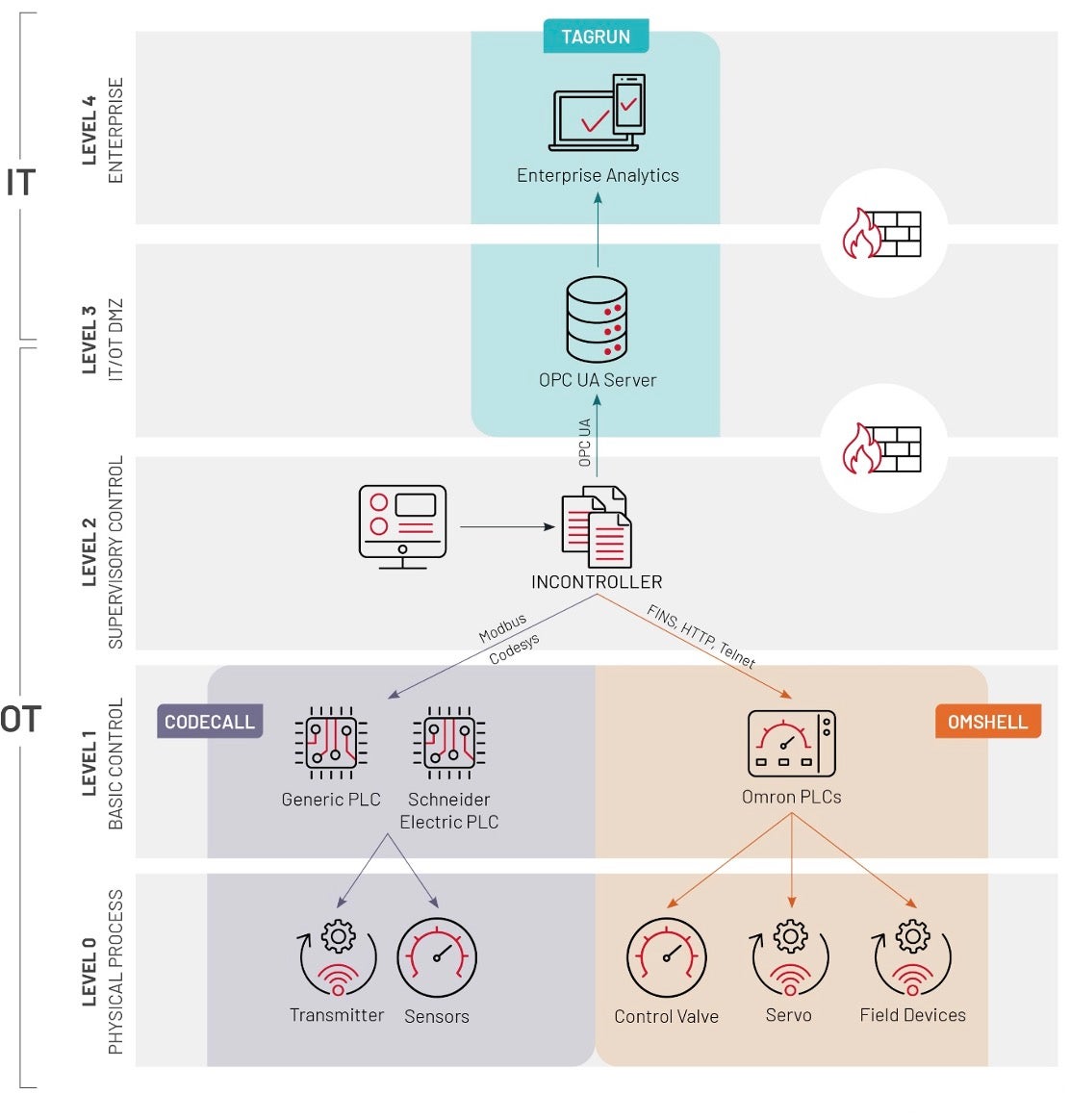
Then, CISA and Mandiant announced the discovery of INCONTROLLER (a.k.a. PIPEDREAM), a different malware toolkit targeting ICS systems. In the case of INCONTROLLER, the attackers are targeting Schneider Electric programmable logic controllers (PLCs), Omron servo drives, and OPC servers. The combination of devices suggests targeting of liquid natural gas (LNG) and electric power facilities.
Fortunately, a collaborative effort between the U.S. government and the private sector was able to miraculously disrupt this capability before its deployment. However, it’s a reminder that APT actors are willing and able to attack the very systems we rely on for our most fundamental societal necessities.


