Secura researchers have disclosed a vulnerability, CVE-2020-1472 Zerologon, that affects all Microsoft Windows Server versions, allowing attackers unauthenticated access to domain controllers, and has given it a CVSS score of 10.0.
They also published a technical analysis of the exploit, Proof of Concept (POC) code in a GitHub repository, that demonstrates a Netlogon authentication bypass. Essentially, the attack allows an external threat actor or malicious insider on the local network to compromise the Windows domain controller without any user authentication credentials.
The POC code requires passing the domain controller name and domain controller IP address to launch an attack.
./zerologon_tester.py EXAMPLE-DC 1.2.3.4
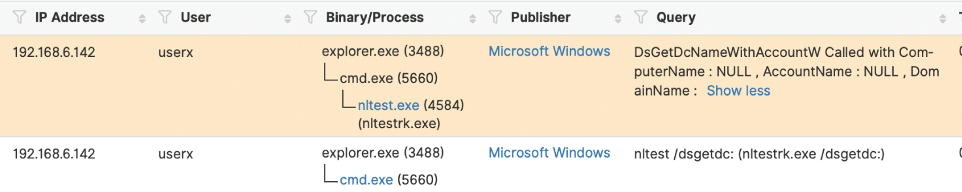
Attackers inside the network need to perform reconnaissance to discover domain controller names and IP addresses within an organization.
Attackers can use built-in Windows commands, PowerShell scripts, etc. to discover domain controller information.
Below are a few methods to discover domain controllers:
1.nltest /dclist: outputs a list of DCs in a domain
2.nltest /dsgetdc lists the IP addresses associated with a DC
3.nslookup lists the logged-on domain controller
4.echo %LOGONSERVER% outputs the current domain controller that authenticated the user
After attackers discover the domain controller and its IP address, they can run the published tool to compromise the domain controller.
python zerologon_tester.py adcontroller.local 192.168.2.148
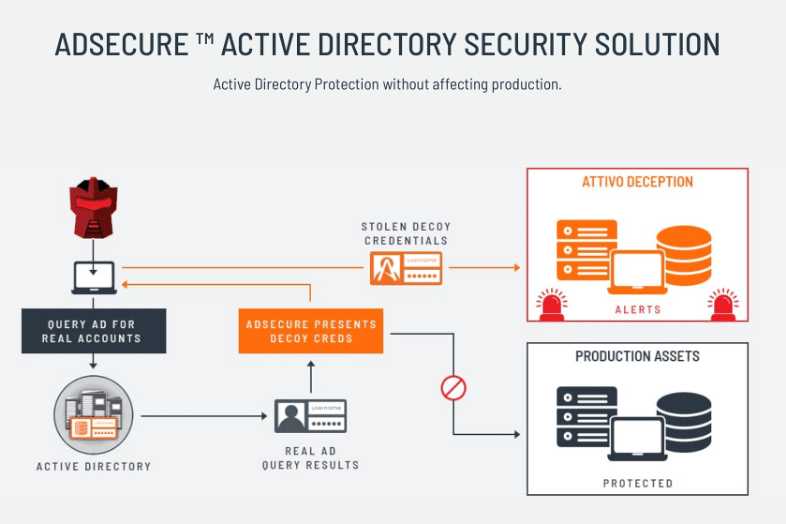
This blog discusses how the Attivo Networks ThreatDefend® platform and ADSecure solution offer early detection and protection against such 0-day attacks targeted against organization domain controllers or high-value assets.
The ADSecure solution is a modular component of the ThreatDefend platform, designed to defend against unauthorized AD data gathering. It augments the existing AD defense capabilities the platform already offers, such as deceptive credentials based on production accounts and decoy AD infrastructure servers.
The ADSecure solution sits at every endpoint and responds to queries attempting to harvest AD data from an unauthorized system. The solution inserts deceptions to counter the AD attack by replying with deceptive data, hiding the privileged credentials, and altering real credentials values. This interception includes engagement of the activities into the deception environment where the system safely studies the attack and collects threat intelligence.
What follows is a description of how the ThreatDefend platform and the ADSecure solution protect AD in the context of an attack.
Step 1:
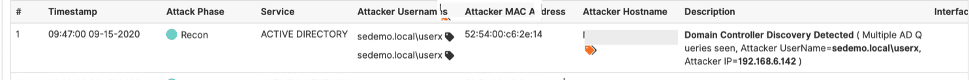
Attackers discover domain controllers and find the IP address of the domain controller.
The ADSecure solution captures the attacker’s discovery methods and provides early alerting on the domain reconnaissance activity. The ADSecure solution returns deceptive data pointing back to decoys, protecting the actual domain controllers from attack.
Step 2:
Attackers launch an attack on the discovered domain controller.
The Attivo ThreatDefend platform captures the attack activity on the endpoint and in the decoys during the engagement.
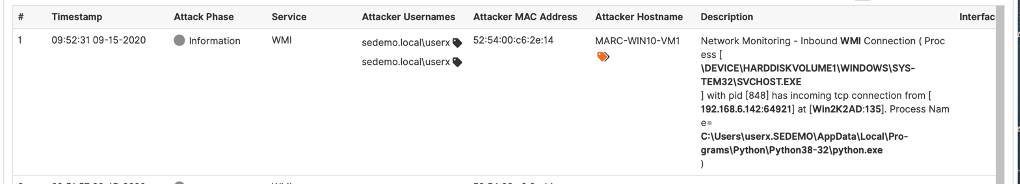
Below is an example of the attacker activity captured on the endpoint:
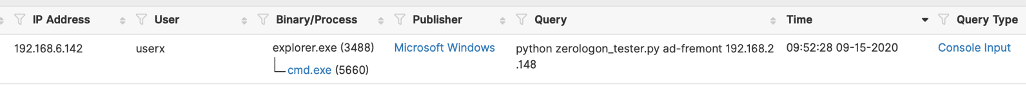
The following image shows the attack activity captured on a decoy system as the ADSecure information redirects the attacker away from a production domain controller to engage the decoy.
Below is a packet capture of the attack on the decoy system:
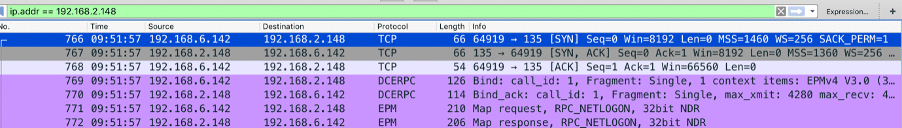
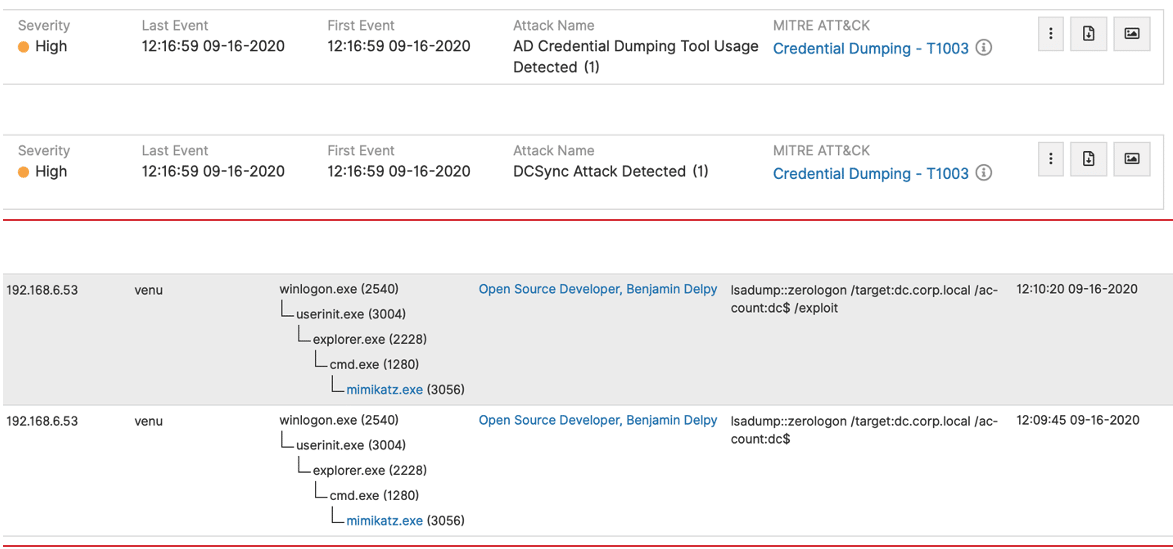
Mimikatz has released a ZeroLogon exploitation module for CVE-2020-1472, which targets Domain Controllers and performs DC Sync attack.
The Attivo ThreatDefend platform captures attacker activity on the endpoint and provides early visibility into the attack, as shown below.
If the organization has successfully patched the CVE, it can still create the impression that there are vulnerable systems within the environment by using the ThreatDefend platform’s Windows servers decoy systems to identify attackers that attempt to leverage the vulnerability.
The ThreatDefend platform and the ADSecure solution offer a unique capability to both detect the attack and misdirect malicious activity by hiding and denying access to sensitive or critical data while giving the attacker fake data that leads away from the production domain controllers and into decoys for engagement. Attackers won’t know that they’ve received deceptive data, nor that they are engaging with decoy servers. At the same time, the defenders gain early detection and valuable adversary intelligence on the TTPs that the attacker is using. To see these capabilities in action, please visit attivonetworks.sentinelone.com and request a demo of the ThreatDefend platform or a 30-day trial of the ADSecure solution.