Nokoyawa Ransomware: In-Depth Analysis, Detection, and Mitigation
Summary of Nokoyawa Ransomware
The Nokoyawa is a ransomware family first discovered in February 2022 that has since been rewritten in the Rust programming language. It utilizes Elliptic Curve Cryptography (ECC) with SECT233R1 and Curve25519 and Salsa20 for file encryption and runtime flexibility via a command-line configuration parameter. Nokoyawa is an evolution of the Nemty and Karma ransomware families. The authors of Nokoyawa utilized (direct code-reuse) many functions from the leaked Babuk source code. Nokoyawa practices a double extortion technique, demanding payment for a decryptor and the non-release of stolen data. It is delivered via a third-party framework (aka Cobalt Strike) and phishing emails, and its authors have reused functions from the leaked Babuk source code. Nokoyawa ransomware can exfiltrate sensitive data from organizations and encrypt users’ files. Its operators have a limited command set that grants them fine control over the execution and outcome of the infection.

What Does Nokoyawa Ransomware Target?
Nokoyawa ransomware generally targets businesses and organizations, particularly those in the healthcare, financial services, government, and manufacturing sectors.
How Does Nokoyawa Ransomware Spread?
Nokoyawa can be delivered via Cobalt Strike or similar frameworks, as well as through email phishing. Nokoyawa operators are known to employ Commercial off the Shelf Tools (COTS) to explore and expand within infected environments. These tools include PC Hunter and GMER.
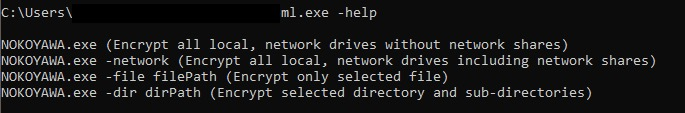
Nokoyawa Ransomware Technical Details
Nokoyawa is an evolution of the Karma and Nemty ransomware families. Similar to its predecessors, Nokoyawa accepts certain command-line parameters during operation. These include options to toggle network spreading as well as the ability to only encrypt specific files or paths.
There are minor differences between Karma and Nokoyawa with regards to how individual file encryption is accomplished. Both Nokoyawa and Karma variants dynamically load bcrypt.dll and call BCryptGenRandom to generate 0x20 random bytes. They generate an ephemeral Sect233r1 key pair using the generated random bytes as the seed. The malware then uses the private ephemeral key and the public embedded key to generate a shared Salsa20 key, which is subsequently used for the file encryption. The Salsa20 nonce is hardcoded as “lvcelvce” in Nokoyawa, whereas in the Karma version it was “11111111”.
Nokoyawa uses multi-threading to quickly and efficiently encrypt files, skipping some extensions in the process. Each encrypted file has a “.NOKOYAWA” extension added to it, and a ransomware note called “NOKOYAWA_readme.txt” is dropped into each folder with both an English and Chinese version.
How to Detect Nokoyawa Ransomware
- The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to Nokoyawa.
In case you do not have SentinelOne deployed, detecting ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To mitigate the risk of this Ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate Nokoyawa Ransomware
- The SentinelOne Singularity XDR Platform can return systems to their original state using either the Repair or Rollback feature.
After the existing text:
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of ransomware attacks:
- Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
- Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
- Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
- Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
Nokoyawa Ransomware FAQs
What is Nokoyawa Ransomware?
Nokoyawa Ransomware is a harmful program that locks your files and demands money to unlock them. It often arrives through bad links or disguised email attachments, making it easy to miss if you’re not paying attention. Once inside, it can scramble important data and leave you stuck. You can lower your risk by checking file sources, keeping your system updated, and watching for weird email activity.
When was Nokoyawa Ransomware first discovered?
Security experts started talking about Nokoyawa Ransomware around early 2022. They spotted it in a few attacks, then noticed more reports popping up across different regions. Researchers used samples collected from infected systems to learn about its behavior and spread. You can stay informed by reading cyber threat bulletins and following trusted tech news outlets. Keeping track of new threats helps you prepare better.
How does Nokoyawa Ransomware spread?
Nokoyawa usually sneaks into your computer through infected email attachments, shady links, or vulnerable software. Once it lands on your machine, it starts running scripts that scramble your files. Hackers may also break into unsecured remote desktop connections and drop the malware by hand. You can slow its spread by checking attachments carefully, patching your software often, and avoiding free downloads from unknown or risky sites.
Which operating systems are targeted by Nokoyawa Ransomware?
Researchers mainly see Nokoyawa going after Windows systems in both home and office settings. Sometimes it attacks older versions that don’t have the newest security fixes. Certain rumors say hackers experiment with other systems, but the biggest wave hits Windows due to its popularity. You can stay safer by keeping your operating system current, turning on built-in security features, and using programs that detect this ransomware.
What types of files does Nokoyawa Ransomware encrypt?
Nokoyawa can lock a broad set of files, such as photos, work docs, spreadsheets, and even archives. It scans your folders for anything that might matter to you or your organization, then scrambles them with tough-to-break cryptography. You can limit the damage by keeping backups somewhere safe, like offline or on external drives, and double-checking any file before you open it.
Which industries are most targeted by Nokoyawa Ransomware?
Nokoyawa often goes after businesses that can’t afford downtime—like healthcare, manufacturing, and finance. Attackers know these fields hold valuable records or run critical operations, so paying ransom can seem like the fastest fix. You can stay ready by running frequent security drills and storing backups. Learn from industry reports to see if threats like Nokoyawa are picking favorites and then adjust your defenses accordingly.
Can Nokoyawa Ransomware spread laterally across a network?
Yes. If it slips into a single computer, it can often move around through shared drives, weak credentials, or unsecured remote connections. Once it hops from one system to another, the damage can grow bigger. You can slow lateral spread by segmenting your network, limiting user rights, and watching for sudden spikes in file changes. Plugging these gaps keeps Nokoyawa from roaming freely through your environment.
What security best practices help prevent Nokoyawa Ransomware infections?
Pick a strong antivirus tool and update it often. Review email attachments for anything that feels shady, and never click links from random senders. Turn on multi-factor login methods, and ensure your software is patched. Pay attention to server logs so you notice odd spikes or weird traffic. You can also run regular security checks and training sessions so everyone knows how to handle suspicious content.
