Organizations always find it challenging to derive the maximum value from their security investment and deployment, and on top of these, different managed services options and new buzzwords in the market add to the problem. Every service provider claims to be doing everything that the organization wants, but it may not solve the problem in hand for the organization.
In this post, we explore the different services on offer and the needs that they aim to meet. We explore a framework that can help organizations understand which services are able to meet their particular requirements.

Facing the Challenge of Protecting the Enterprise
Organizations need a combination of People, Process and Technology to derive value out of their security technology investments. It is quite a common practice to buy the security technology first without understanding the need of managing and operating it, which ends up just becoming a tick in the box exercise and a lot of unrealized potential.
In the recent past, we saw organizations adopt EDR to solve the failure of legacy AV, assuming that it would work in ‘set and forget’ mode. Despite 24/7 monitoring, many organizations using EDR still aren’t engaging in active threat hunting, which leaves a lot of value and potential unrealized.
Managing and operating some security technologies has been made more challenging as a result of the skills shortage in the cybersecurity industry, which can be understood in two aspects:
- Talent Capacity Shortage: Not having the required number of people in-house or in the team to run operations 24/7 (a numbers problem)
- Talent Capability Shortage: Unable to find the find suitably skilled professionals to run the operations (a skills problem)
The Need for Managed Services
In such scenarios, organizations typically decide to outsource security to a third party such as Managed Security Service Providers (MSSPs). However, the service is limited to mostly management of the security technology rather than security operations. It’s very important to understand the difference between ‘security tool management’ and ‘security operations’ in the context of a SOC.
Security Tool Management – focuses on maintaining the general hygiene and administration of the security product such as policy enforcement, policy modification, setting role-based access control, changing access requirements, provisioning, and de-provisioning on the tools; in case of on-prem deployment, patching the underlying infrastructure, scaling the storage, upgrade of the application, etc. In some cases, it involves basic monitoring of alerts.
Security Operations – focuses on the use of the tool to fulfill the objective or the meet the goal for which tool was originally deployed; for example, EDR is deployed to protect and detect sophisticated attacks on endpoints and take timely response on detected attacks, so security operations would include monitoring to identify incidents, then contain, investigation and respond to the incident.
Organizations buy and deploy technology not just to manage it but to extract value out of it; hence, security operations should be at the core of investment in a security technology.
When it comes to challenges with security operations and adding the people and process part to the technology, organizations are often confused about what they need, whether they need Managed Detection & Response (MDR), Managed Threat Hunting (MTH), or Managed Security Service Provider (MSSP). Let’s explore these terms for a better understanding of what each provides.
Managed Detection & Response
MDR services perform proactive 24/7 monitoring of threat-facing security technologies and detect, investigate, and respond to attacks.
Managed Threat Hunting
MTH takes a proactive approach that goes beyond the tool alerting to detect attacks using attackers TTPs, IoAs and attacker hypothesis based on the security telemetry being collected by security technologies. This helps you in identifying attacks that are currently active and even compromise assessment.
Managed Security Service Provider
MSSPs mostly focus on the upkeep of the security technologies like firewalls, email gateways, web gateways, EDR, SIEM, and others. They provide basic alert triaging and alert an organization of a possible attack but don’t take action or consolidate various alerts into an incident. MSSP focuses on Security Tool management.
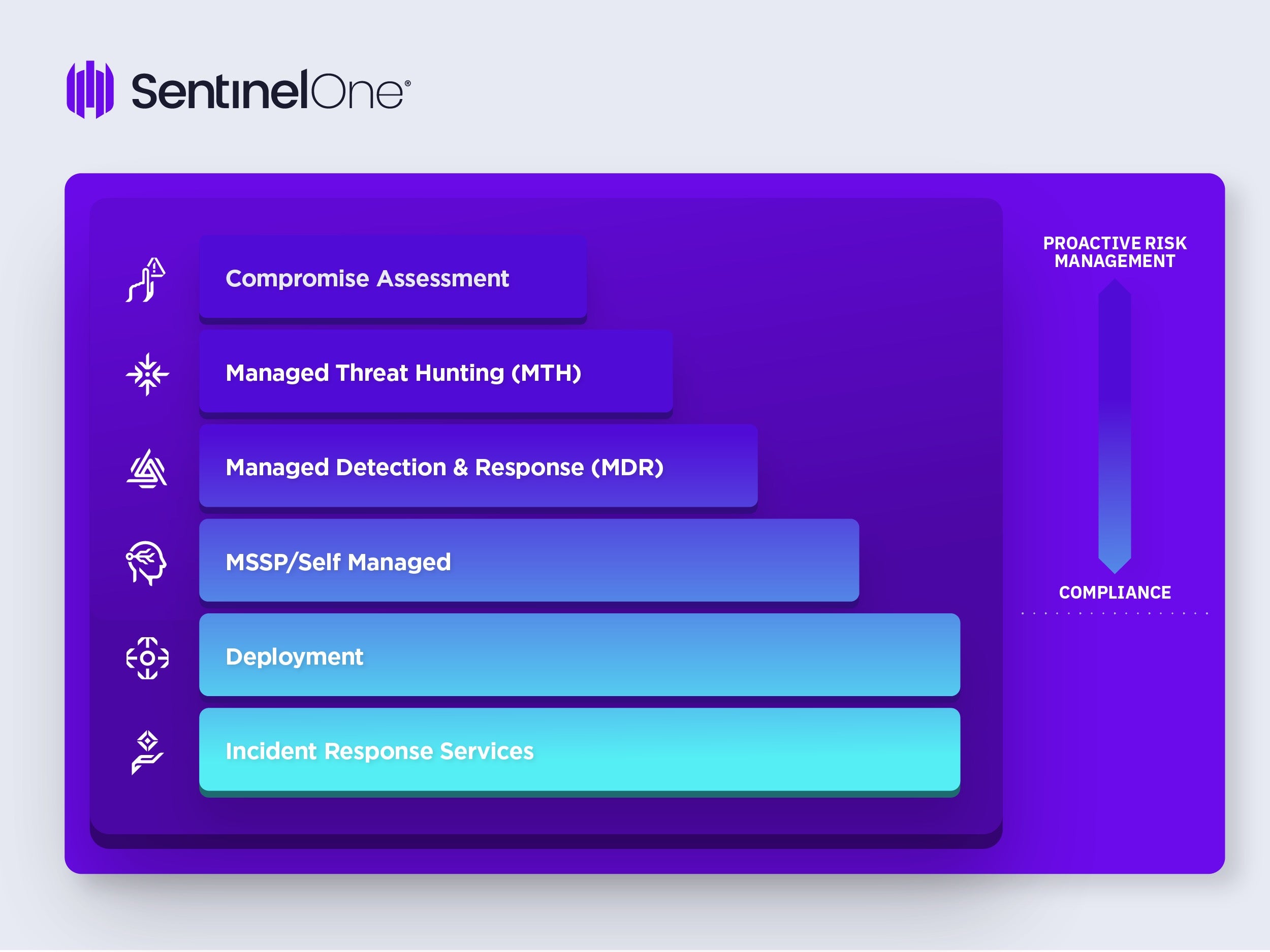
Given these differentiations, it is important to understand the organization’s context and requirements to identify the right kind of service. The following provides a helpful framework.
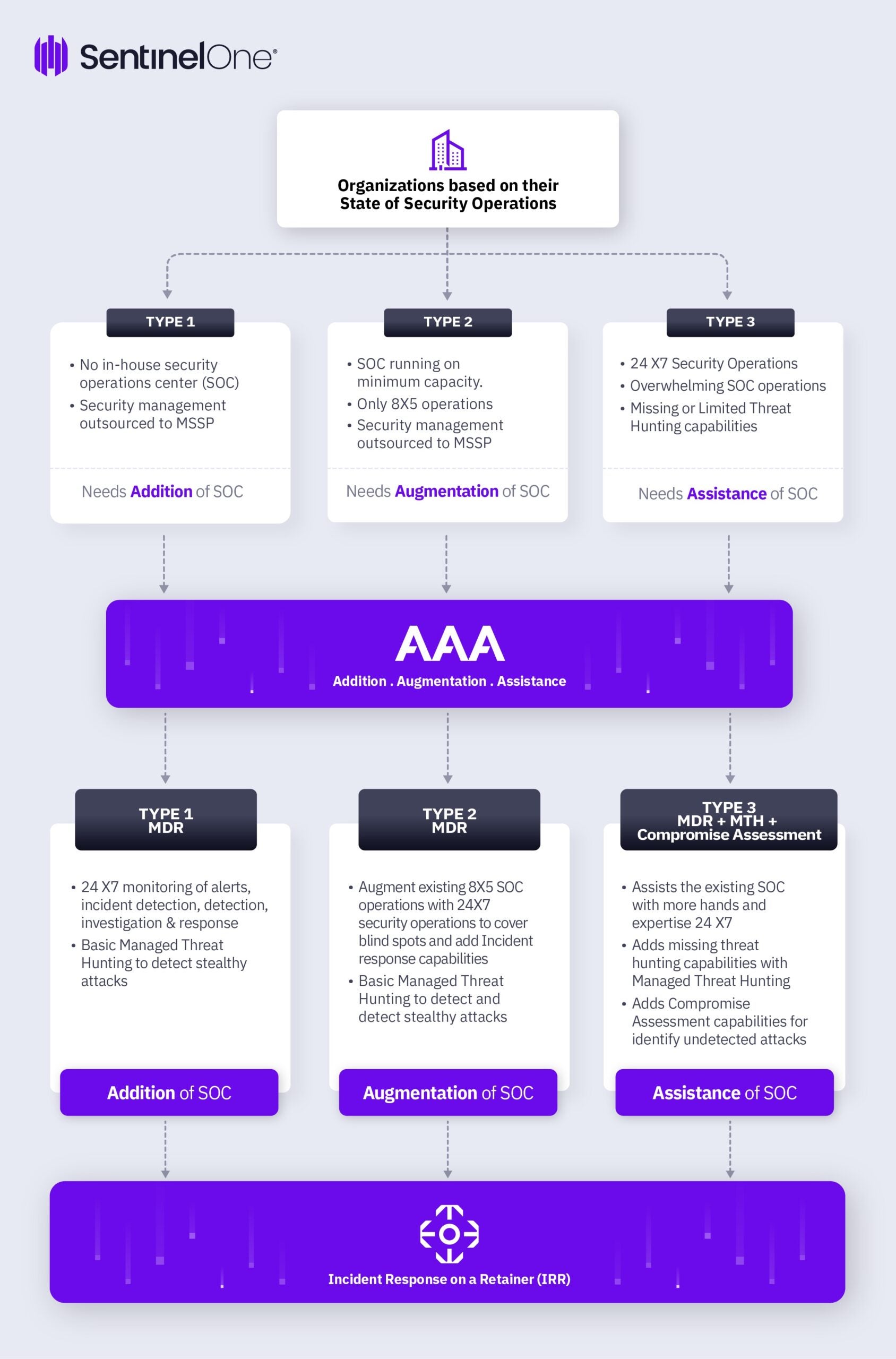
People and Process are essential for effective security operations and organizations should be using the framework above to understand which option is the best fit for their organization, given the context. Although the framework highlights different services such as MSSP, MDR, and MTH, these services can come from the same or multiple providers.
Type 1 Organizations
These are small and midsize organizations for which cybersecurity decisions are mostly based on compliance requirements. They also generally don’t have dedicated cybersecurity teams, heavily outsource security functions to managed security service providers (MSSP) and only have a security leader (shared capacity) to make cybersecurity decisions.
However, as the data and attack statistics suggests, ransomware threats are more actively targeting midsized organizations as they see them as low hanging fruit. A ransomware attack can result in significant business loss, and even lead to closure of the business. Hence, Type 1 organizations should look beyond just security technology management and actively invest in continuous monitoring for threats and alerts. As it is difficult for Type 1 organizations to build their own team, they should actively look at Managed Detection and Response providers (MDR) to add Security Operations Center Capabilities.
Type 2 Organizations
Type 2 organizations are mainstream and have mid to high maturity in cybersecurity. They are more likely to have a SOC in-house with some functions outsourced to an MSSP. However, the existing SOC may not be 24/7 and more likely to be focusing on compliance requirements and basic alert monitoring.
Because of their limited SOC capabilities, type 2 organizations should look at augmenting SOC capabilities with an MDR service to make the existing SOC 24/7 and add threat detection and response capabilities.
Type 3 Organizations
These are highly mature organizations and run a 24/7 SOC with dedicated analysts for threat detection and response use cases. However, because of the overwhelming nature of the SOC, scaling the SOC operations becomes difficult.
Type 2 organizations can also find it challenging to operationalise and perform continuous threat hunting. Thus, these organizations need help with MDR providers to scale their SOC operations, Managed Threat Hunting for continuous threat hunting across their environment and continuous compromise assessment. These services can provide assistance in SOC to type 3 organizations.
Incident Response Retainers (IRR)
Irrespective of Type 1, 2 and 3 organizations, every organization needs an incident response service on a retainer to help them manage a crisis situation. IRRs are available in Prepaid and Zero Dollar agreements. Though it is advisable to have a Prepaid Retainer agreement in place, organizations with limited budgets should at least have a ‘Zero Dollar’ retainer agreement to save crucial time in the event of a security incident.
It is worth noting that when buying Managed Services (MDT,MTH, etc.) from a technology vendor such as EDR, the services should be used to augment the product offerings and not complete the product offerings.
It is recommended that MSSP and MDR are from two separate service providers to avoid conflict of interest as these services focus on different objectives: MSSP provide security management and monitoring and MDR specialize in threat detection and response.
The IRR agreement can be sourced through a current MSSP/MDR provider as well given that they have expertise and the required credentials in the IR domain.
Security incidents are a matter of when and not if. When a security incident occurs, the organization’s preparedness will help prevent the incident turning into a crisis. Incident Response Retainers have evolved from just being reactive to being proactive and should also be used before an incident to prepare better for a security incident to reduce the time to detect, contain and recover from an attack.
Conclusion
It is no news that threats and their tactics, techniques and procedures are evolving fast and becoming more sophisticated.
Despite rapid advances in AI-assisted security technology, it remains the case that no technology can guarantee to detect 100% of attacks. An effective cybersecurity approach requires a human-machine teaming where the sum becomes greater than the parts.
This additional cybersecurity value will add more business value in terms of less business disruption, less compliance and regulatory fines, higher customer confidence and lower TCO of the cybersecurity investment.
SentinelOne offers robust Managed Detection & Response (MDR), Managed Threat Hunting (MTH), Compromise Assessment and Incident Response Services. To learn more contact us or visit SentinelOne Global Services.


