Each year, Amazon Web Services’s re:Inforce event serves as a reminder to the cyber defense community of the importance of organizational security. Over the past two days, AWS brought together many security leaders to share industry best practices and the latest in cloud security technology.
As security teams face challenges presented by the dynamic nature of the cloud surface, SentinelOne reaffirms its goal of providing speed, scale, and flexibility to enterprises without compromising agility or availability. The SentinelOne team brought this energy to this year’s AWS re:Inforce event at California’s Anaheim Convention Center and to the thousands of others in attendance, demonstrating AI-powered cloud security and Amazon Security Lake integration.

For those who couldn’t join us in person, here’s a recap of the main talking points and innovations presented by SentinelOne and AWS to advance cloud security to the next level.
Presentation Highlights | SentinelOne vs. Cloud Ransomware
Cloud ransomware has become a much discussed topic in the security community with both myths and facts surrounding its rising threat to enterprises. One misconception that has been busted is that “cloud ransomware is not a real cause for concern”. The reality? Cloud ransomware is a very real and quickly-growing threat. As more businesses move their data to the cloud, cybercriminals are honing their techniques to launch advanced attacks on this surface.
“Over the last 12 months, we’ve actually investigated over 8.5 million indicators of compromise (IOCs),” said SentinelOne Field CISO Director, Albert Caballero, in the re:Inforce Lightning Theater on the Expo Floor. “So, this is happening on a daily basis.”
In this presentation, Caballero broke down the types of cloud threats that SentinelOne sees regularly, including the actors behind the attacks, and their methods. He referenced several malware threats and toolsets such as AlienFox, “Doki” malware and container escapes, and IceFire ransomware; all investigated by the SentinelLabs and Vigilance MDR teams.
“It’s no longer that malware only targets Windows, but it’s actually moving towards Linux, Docker, and container environments.”
Caballero explained that the role of MDR in a cloud environment is a critical one, enhancing a SOC teams’ ability to react quickly and contain cloud-based threats.
Using SentinelOne’s Vigilance MDR, security professionals can centralize incoming alerts and telemetry in a highly performant backend data lake which uses the power of AI to automate correlations across hybrid environments. Learn more about how SentinelOne can support the speed and accuracy needed to defend your cloud environments here.
Presentation Highlights | Real-Time Identification & Remediation in Ransomware Attacks
Cloud-centric attacks are rising fueled by mass digital transformations and the challenge of architecting a cloud security framework. Today, 60% of the world’s corporate data is stored in the public cloud and 80% of companies have experienced at least one cloud security incident in the last year alone.
“There’s an interesting change that seems to be occurring: Attackers are following the money,” said SentinelOne’s Jeremy “Howie” Howerton, Cloud Technical Leader, in a presentation to start Day 2 of re:Inforce. “They’re figuring out that Linux systems and actual cloud systems are where most data these days are being housed.”
Building robust and effective cloud security takes more than just proper configuration and daily scanning though. While AWS ensures the cloud itself is secure and having a well-defined Cloud Shared Responsibility Model does much to improve overall cloud security posture, targeted attacks against cloud environments require another layer of security.
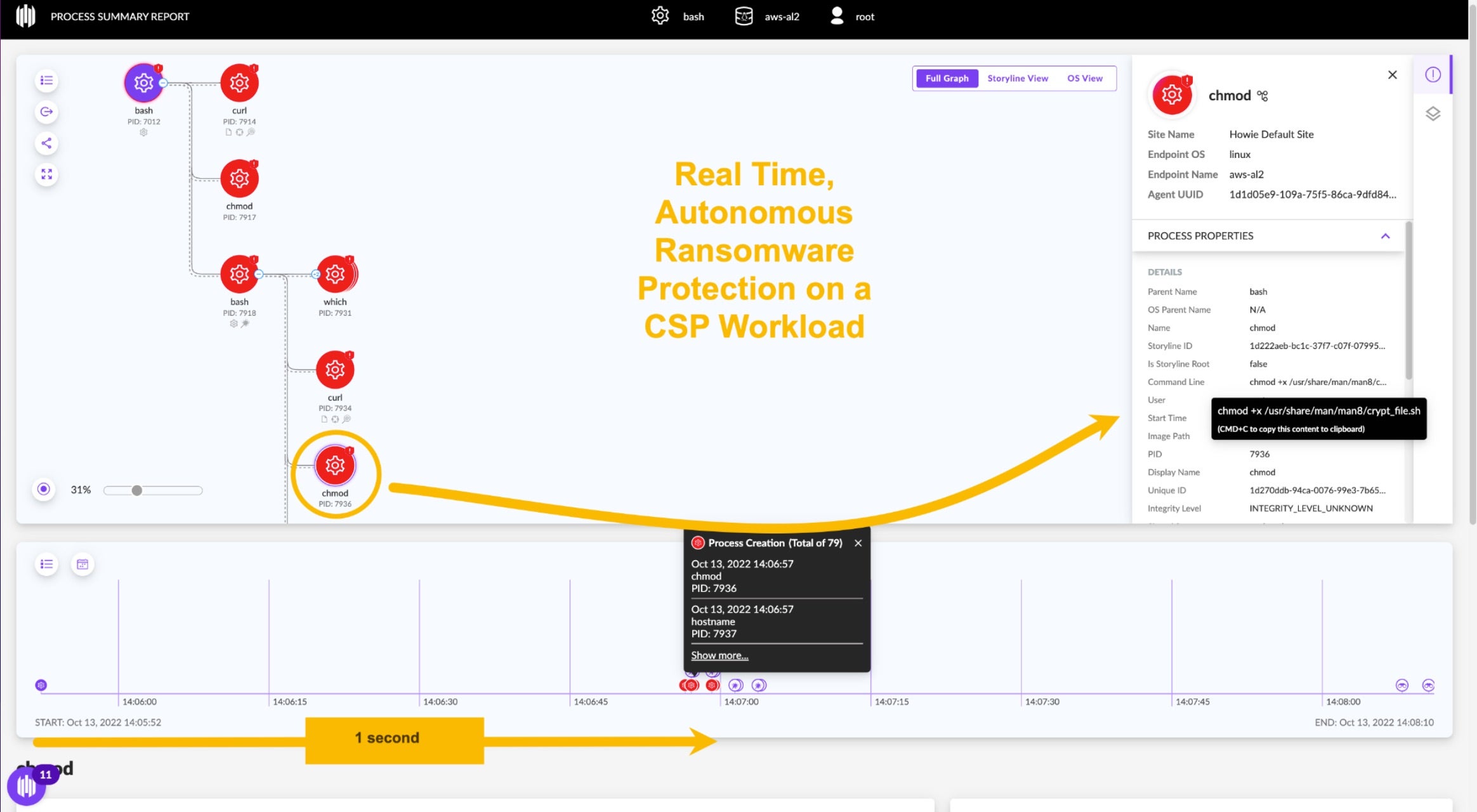
Howerton explained that when it comes to cloud-based ransomware attacks, lateral movement and exfiltration can happen in minutes and cause critical damage. Using a demo showing how SentinelOne blocks a DarkRadiation ransomware attack, Howie proved the value of having real-time, at runtime detection and response and how it augments best practices for workload protection and cloud threat hunting.
SentinelOne at AWS Security LIVE!
In an AWS Security LIVE! broadcast on Twitch, SentinelOne Field CISO Albert Caballero was asked by hosts Ryan Orsi and Temi Adebambo about Purple AI, a first-of-its-kind generative AI tool for SOC teams and threat hunters, first announced in April at this year’s RSA Security Conference in San Francisco.
AI is, no doubt, one of the most disruptive technologies of our time. While cybercriminals are leveraging generative AI to execute malicious attacks that can take down companies and governments, SentinelOne uses the power of AI as a force for good.
“AI is scary for a lot of people, but the reality is that it’s just another tool in our arsenal. The hackers are using it – the defenders need to use it,” said Caballero during the livestream. “It’s just something that if we don’t leverage, then we’re just going to fall behind and the cat-and-mouse game chase starts all over again.”
Purple AI uses a variety of open source and proprietary models to arm security analysts with an engine that identifies, analyzes, and mitigates threats using conversational prompts and an interactive dialog. With Purple AI on hand, analysts can shave down hours of research and queries and, instead, get rapid, accurate and detailed responses to any question, in any language.
“What [Purple AI] will do is, not only perform that query on your backend and give you those results, but also give you some recommended actions and build out the actual query syntax for you,” said Cabellero, a veteran security leader who has held previous positions in divisions of Warner Bros., HBO, and Verizon Business. “When I first saw this, I was like, ‘Man, if only I had that when I ran a SOC 10 years ago.’”
A first-of-its-kind offering, Purple AI is designed from the ground up to accelerate threat hunting capabilities. It seamlessly fuses together real-time, embedded neural networks and a large language model (LLM)-based natural language interface to help security teams monitor and operate all security data and boost their productivity and scale their operations.
“That’s something that allows us to elevate the SOC analysts, especially those new to the SOC that typically would have to escalate a ticket to a level two,” continued Caballero. “They can perform a lot more triage, a lot more analysis, without necessarily understanding how to query the backend.”
In addition to discussing Purple AI, Caballero also talked about investing in real-time, agent-based protection to help build operational resilience.
“It’s important to understand where the threats are and tackle them where they are. The threats are at the operating-system level, they are at layer seven, they are at the application layer,” said Caballero. “You run Kubernetes, you run Docker, you run anything, you need an agent on those containers.” You can tune into the full conversation here.
GA Announcement | SentinelOne’s Integration with Amazon Security Lake to Power Cloud Investigations
Following AWS’s announcement two weeks ago of its general availability for Amazon Security Lake, AWS CISO, CJ Moses, emphasized its importance onstage at re:Inforce. SentinelOne is a proud launch partner for Amazon Security Lake.
“This streamlined process greatly reduces complexity and enhances efficiency in threat investigations, enabling a unified data source that automatically correlates events, empowering automated correlation of events to reconstruct threats from inception to resolution,” said SentinelOne’s SVP of Product Management, Jane Wong.
Following this GA release, security teams can now bring Amazon Security Lake telemetry into the SentinelOne Singularity™ platform. This allows joint customers to automatically ingest the Amazon Security Lake telemetry, search and analyze within the Singularity™ platform, and leverage SentinelOne’s correlation and automation capabilities. Learn more here.
Closing Thoughts On re:Inforce 2023
Whether on the re:Inforce Expo Floor, in theater presentations, web broadcasts, or at customer meetings, the SentinelOne team emphasized the importance of securing the cloud in real-time, the winning combination of automation and managed detection and response (MDR), and the strength of partnerships with AWS, Wiz, Red Canary, and others.
The past two days served as a reminder of the good work cyber defenders are doing to keep everyone safe in the cloud. Events like re:Inforce keep us together and show how important it is to continue the conversations around cloud security best practices and cyber innovation. Thank you to AWS for a memorable conference – we look forward to more chances to collaborate with fellow vendors and attendees!
Contact us to learn more about SentinelOne’s cloud security offerings and how we can help you improve your cloud security strategy through a combination of endpoint detection and response (EDR) capability, autonomous threat hunting, and runtime solutions.