The Good | US and UK Sanction Russian Cybercrime Gang
The US and UK governments imposed joint sanctions on 11 Russian individuals this week for their part in ransomware and other cybercrime activities widely attributed to the Conti and TrickBot gangs. Nine of the eleven have further been charged with ransomware offences in the US.
The individuals took part in or facilitated attacks on hospitals and other critical infrastructure, a statement from the British government said on Thursday.
According to the UK’s National Crime Agency (NCA), the group has extorted more than $180 million in attacks on hospitals, schools, local authorities and businesses around the world. The new sanctions will target the 11 Russian men with asset freezes and travel bans in an attempt to hamper their ability to monetize their cybercrime activities. They also prohibit ransomware victims from making payments or transferring funds to the sanctioned individuals.
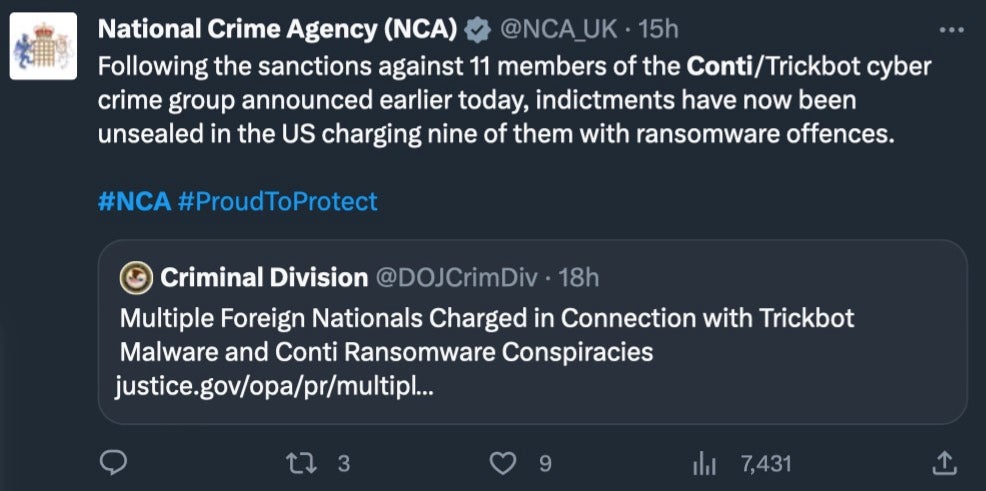
The 11 sanctioned individuals are:
- Andrey Zhuykov (aka ‘Defender’, ‘Dif’ and ‘Adam’),
- Maksim Galochkin (aka ‘Bentley’, ‘Volhvb’ and ‘Max17’)
- Maksim Rudenskiy (aka ‘Buza’, ‘Silver’ and ‘Binman’)
- Mikhail Tsarev (aka ‘Mango’, ‘Fr*ances’ and ‘Khano’)
- Dmitry Putilin (aka ‘Grad’ and ‘Staff’)
- Maksim Khaliullin (aka ‘Kagas’)
- Sergey Loguntsov (aka ‘Begemot’, ‘Begemot_Sun’ and ‘Zulas’)
- Alexander Mozhaev (aka ‘Green’ and ‘Rocco’)
- Vadym Valiakhmetov (aka ‘Weldon’, ‘Mentos’ and ‘Vasm’)
- Artem Kurov (aka ‘Naned’)
- Mikhail Chernov (aka ‘Bullet’ and ‘m2686’)
The UK government said that by stripping away the anonymity of the criminals who hide behind online pseudonyms and monikers, they hope to disrupt their ability to conduct criminal businesses.
The Bad | NSO Pegasus Exploit Caught In the Wilds of Washington DC
A report from Citizen Lab this week revealed that an iPhone zero-click zero day exploit was used to deliver NSO’s Pegasus spyware to an employee of a Washington DC-based civil society organization.
Although full details have yet to be disclosed, the attack involves exploiting Apple Wallet Passes – digital images containing information that can be used instead of tickets or plastic cards. It appears that a threat actor sent a maliciously-crafted Apple Wallet pass to the target’s iMessage account. The exploit was then used to deliver Pegasus spyware, a product developed and sold by US-sanctioned company and private sector offensive actor, NSO.

This is not the first time Pegasus has been caught in the wild making use of a zero-click Apple zero day. In 2021, Citizen Lab discovered that FORCEDENTRY, a vulnerability in Apple’s Core Graphics framework, was used to deliver Pegasus to an iOS device belonging to a Saudi activist.
Dubbing the entire exploit chain BLASTPASS, Citizen Lab says that it is capable of compromising the current version of iOS (16.6) without interaction from the target. Apple has reportedly said that devices operating in Lockdown Mode are not vulnerable to BLASTPASS.
The vulnerabilities making the exploit chain possible have been tagged as CVE-2023-41061 and CVE-2023-41064. Apple released an emergency software update for both iOS and macOS on Thursday to address the issue and all iPhone and Mac users are urged to update immediately.
The Ugly | Unpatched Zero Day in ‘Popular Software Package’ Targets Researchers
Cybersecurity researchers are on alert this week as news comes of a zero-day in an unnamed ‘popular software package’ being exploited by North Korean-linked threat actors to compromise infosec professionals.
Google’s Threat Analysis Group says it discovered the vulnerability as part of its tracking of an ongoing campaign targeting security researchers. However, they have declined to name either the vendor or the package concerned until a patch is available in order to prevent other cybercriminals and threat actors from taking advantage.
It is believed that the exploit is delivered to selected targets after a lengthy-period of grooming on social media. In one reported incident, a threat actor posing as a researcher made initial contact with the victim via X (Twitter) and Mastodon, using the account names of Paul091_ and paul354, respectively. They then engaged in a conversation for several months around the topic of collaborating on security research.
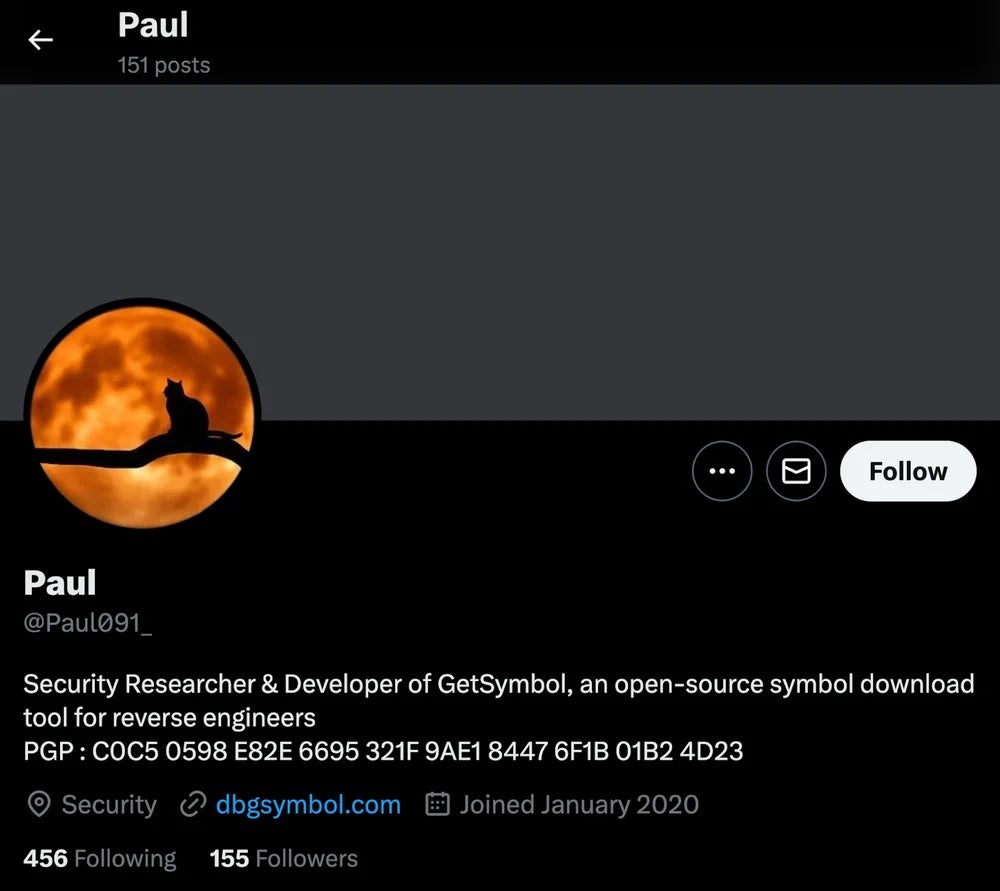
After building trust with the target, the attackers moved the conversation to an encrypted messaging app, from which they eventually sent a malicious file containing the zero day exploit.
The exploit was used to deliver shellcode to the victim’s computer that first runs checks to ensure the device is not running on a virtual machine. The shellcode then sends data including a screenshot back to the attacker’s command-and-control server. Analysis of the shellcode reveals similarities to that seen in previous North Korean-linked attacks.
While security researchers may have been the target in this campaign, it should serve as a timely reminder to anyone that unsolicited social media contacts are a vector for compromise and appropriate caution and security controls need to be in place.



