Update: As of January 12, 2023
The vulnerability in JsonWebToken, CVE-2022-23529, discovered by Unit 42 researchers on January 9, 2023, has been revoked. It says that if specific conditions meet, an attacker could potentially execute code on a server verifying a malicious JSON web token request.
However, the likelihood of this happening in real-world situations is considered low due to the specific requirements needed for exploitation.
After careful consideration, it has been decided that the vulnerability is invalid, and CVE-2022-23529 is being revoked. However, the revocation may take some time to propagate throughout the entire system.
The maintainers and researchers are also updating their respective advisories to include more context around the issue and potential exploitation.
Introduction
On the 9th of January 2023, security researchers from Unit 42 disclosed a high vulnerability in JSON Web Token (JWT) libraries. JsonWebToken is an open-source project that aims to create web tokens. The vulnerability, tracked as CVE-2022-23529, allows attackers to bypass the verification of JWT tokens, potentially leading to remote code execution (RCE) on a server.
Initially, the vulnerability had a high severity rating and an EPSS score of 0.108550000. However, after further investigation, it has been concluded that no prerequisites can allow an attacker to perform exploitation of the vulnerability in real-world applications.
Everything you need to know about JsonWebToken
The JsonWebToken package is an open-source JavaScript package that allows users to verify and sign JWTs. It’s primarily used for authentication and authorization purposes.
In other words, a simple and compact way to securely transmit information is the JSON Web Token. It can be used for various purposes, such as authentication, authorization and exchange of information. Furthermore, the compact size of the JSON object allows it to be transferred in various ways, such as in POST parameters, URLs, and HTTP headers.
Auth0 is responsible for maintaining and developing this library, which is written in JavaScript and supports various platforms, such as browser-based applications and node.js. In addition, this library provides a set of APIs that allow developers to create JWT tokens easily. With this, they can quickly and securely implement user authentication systems and integrate them with third-party services.
What is JWT 101?
JWT refers to an open standard that enables people to transfer data by encoding and signing JSON data securely. A JSON object is created to express trust between two parties, such as an online application and a service provider. Its string structure is composed of three separate parts:
Header.Payload.Signature
Header – This contains information about how the JWT is encoded. The encoded JWT is typically represented by two parts. The first is the token type, and the second is the signing algorithm used.

Payload – This contains the claims. These statements typically include information about an entity or metadata. There are three different types of claims, namely, public, private, or registered claims.
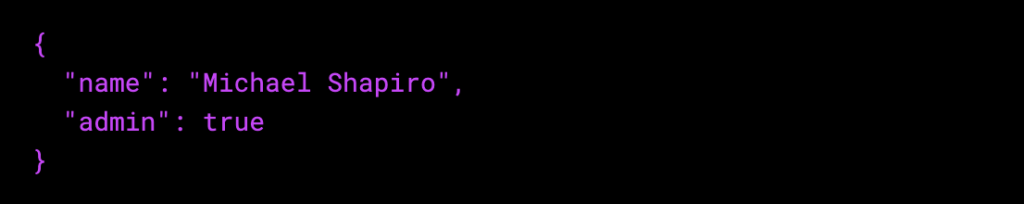
Signature – This is done to ensure the message isn’t altered along the route and to confirm that the sender of the JWT is who they claim to be. The header and payload are used to create the signature.
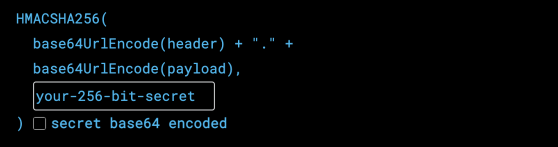
About the vulnerability (CVE-2022-23529)
A typical attack on JWT involves using different forgery techniques. In addition, the techniques used in these attacks usually involve abusing the buggy implementations of JWT. These attacks carry severe consequences, as a successful attack can allow an attacker access to sensitive information, such as confidential information or steal and/or modify data.
The JsonWebToken package provides a method called verify, which checks the validity of JWT. It receives three parameters: token, options, and secretOrPublicKey. It verifies the validity of a JWT and returns its decoded payload part.
The values of the privacy-enhanced mail (PEM) file will be assigned based on the secretOrPublickey parameter when no options algorithms are provided in the list. The issue is that the secretOrPublicKey parameter needs to be put in place to ensure that it is a valid PEM file’s content. This means that the toString method used by this unverified object is being blindly used. Attackers can provide their own toString method to the JsonWebToken’s verify process.
The CVE is not remotely exploitable as it requires an attacker to create an object within the context of an application to execute malicious code, which means that instead of just parsing JSON, they have to implement an executable function. This can only be performed if the attacker can modify the source code, and if they can, they can directly execute the malicious code.
How does JWT authentication work?
When a user logs in using a password or username, the server validates their credentials and creates a signed JWT with a secret key. This will be stored in a different location. Subsequently, the user will be asked to provide a secret key by the JWT, which will be used to verify the request. Finally, the server will use the secret key stored to verify if the token is valid or not.
Prerequisites for exploitation
The vulnerability requires several prerequisites to be exploitable, such as using a specific algorithm and a specific configuration of the JWT library. However, the fact that JWT is widely used in many applications and that the vulnerability can lead to RCE makes it a critical issue that should be addressed as soon as possible.
A few prerequisites must be met to exploit the vulnerability:
- Secret keys are not securely stored on the server.
- The attacker needs to have access to and control the secret keys.
These requirements imply that an application is insecure, which means it can be exploited regardless of the vulnerability.
When can an attacker perform an exploit?
The attacker can create a malicious token to access the server if the prerequisites are met.
After taking the requested token as input, the server uses the verify() procedure to determine if the secret key is correct.
The three parameters used in the verify() method are token, option, and secretOrPublicKey. When the algorithm in the option is empty, the values from the secretOrPublicKey will be assigned instead.
The toString() method returns a string that represents an object that has been represented. If the object has not been shown, the user implementation will be triggered.
How to fix CVE-2022-23529- JsonWebToken?
To mitigate the vulnerability, affected organizations should update their JWT libraries to the latest version, including a fix for this issue. Additionally, they should review their applications and systems using JWT, verify that they are properly configured, and use recommended algorithms and libraries.
The technical details of the vulnerability indicate that it affects all the versions of the Json Web Token Library below 8.5.1 or an earlier version. Therefore, to fix the issue, the community is urged to migrate the library to a newer version and suggest updating to JsonWebToken library 9.0.0, which includes a fix for this vulnerability.
Do you need to worry about CVE-2022-23529?
The affected package is very popular, with over 20 thousand dependents and over 10 million weekly downloads. The prerequisites for this vulnerability are less likely to be met, as attackers cannot easily access and control the secret keys. If they could do so, they could create their own key and would not need to exploit this issue.
The security community generally believes that the vulnerability is exaggerated, and it is unlikely that an exploit would occur in the wild.
Although there’s no cause for alarm, it’s still important to practice good security hygiene and patch this vulnerability.
In conclusion, the CVE-2022-23529 vulnerability is a high issue that can lead to RCE on a server that verifies maliciously crafted JWT tokens. Organizations should take immediate steps to update their JWT libraries and review their applications and systems that use JWT to ensure that they are properly configured and protected against this vulnerability.
How SentinelOne detects vulnerabilities in seconds?
SentinelOne’s advanced cybersecurity AI platform helps you identify and detect critical vulnerabilities across hybrid and multi-cloud environments. It offers state-of-the-art runtime detection, agentless vulnerability management, cloud workload protection, threat intelligence, and incident response capabilities.
Defend against zero-day attacks and get a holistic overview of your cloud security posture. Secure cloud VMs, serverless functions, containers, entitlements and identities, and perform real-time secret scanning. Improve your organization’s reputation and stay ahead of your attackers with SentinelOne Singularity


