CVE-2023-20052 is a possible remote information leak vulnerability (XXE) in the DMG file parser of ClamAV. The issue affects versions 1.0.0 and earlier, 0.105.1 and earlier, and 0.103.7 and earlier. Attackers can exploit this vulnerability to gain unauthorized access to sensitive data, execute malicious code, and cause denial of service attacks.
Understanding the CVE-2023-20052 ClamAV XXE Vulnerability
The vulnerability is classified as an XML external entity injection (XXE) vulnerability with a CVSS score of 5.3, which is considered medium.
ClamAV is vulnerable to an XML external entity injection (XXE) attack when processing XML data caused by enabling an XML entity substitution. By sending a specially crafted DMG file to ClamAV, which scans this document and executes the embedded code, which can cause various malicious activities, a remote attacker could exploit this vulnerability to view bytes from any file that may be read by the ClamAV scanning process.
Patch review
CVE-2023-20052 is fixed with this patch:
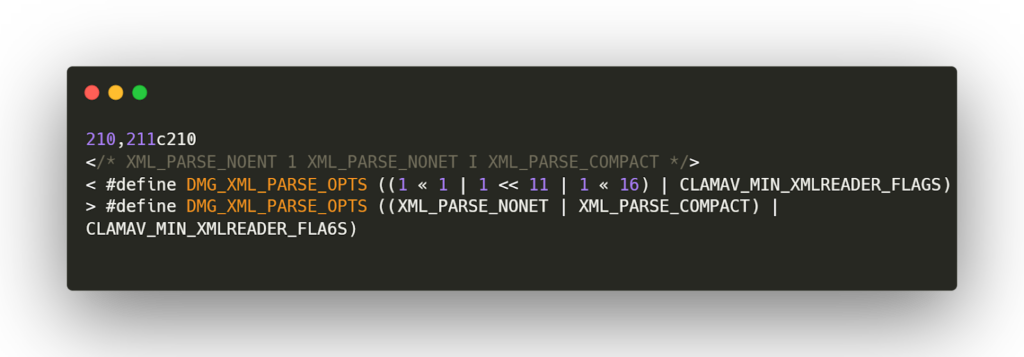
The fix removes the `XML_PARSE_NOENT` flag from the libxml2 parsing options. This flag controls whether the parser can perform entity substitutions and can lead to XML External Entity Injection (XXE) if left enabled.
This is a common mistake, especially with a counter-intuitive name like “NOENT” introduced in 2016. exploitation Strategy.
Exploitation strategy
DMG files contain a ‘Data fork’ containing disk blocks, followed by a Property List and a trailer. Here’s an excerpt from our DMG handler in Unblob with some nice
ASCII art:
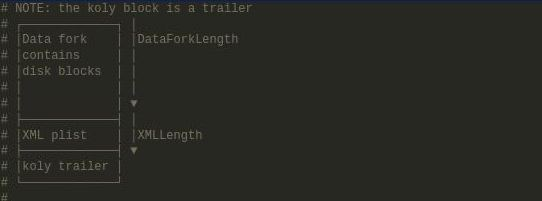
To exploit this vulnerability, you must place your malicious XXE payload within the property list to make libxml2 substitute and resolve external entities.
Exploitation
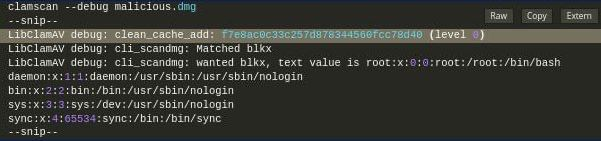
It’s possible to leak local files if the binary runs with –debug enabled. In the excerpt below, we make it dump the content of /etc/passwd through XXE:
How to prevent the CVE-2023-20052 ClamAV XXE vulnerability?
The ClamAV team is releasing critical patch versions to address CVE-2023-20052. The following patch versions are available:
- 0.103.8
- 0.105.2
- 1.0.1
To patch for the remote code execution vulnerability and remote information leak vulnerability, it is highly recommended that all users update their ClamAV antivirus software to one of these patch versions as soon as possible. Note that ClamAV 0.104 has reached end-of-life and will not receive a patch. Users currently using ClamAV 0.104 must switch to a supported version.
Conclusion
The CVE-2023-20052 ClamAV XXE vulnerability is a serious threat to organizations using ClamAV antivirus software. Attackers can exploit this vulnerability to gain unauthorized access to sensitive data, execute malicious code, and cause denial of service attacks.
It is crucial that organizations update their software to the latest version and practice good cybersecurity hygiene to prevent such vulnerabilities from being exploited. By staying vigilant and taking proactive measures, organizations can protect themselves from these security threats.



