vBulletin, a popular software for building dynamic online communities and forums, has been discovered to house a severe security vulnerability. This critical flaw, CVE-2023-25135, affects vBulletin versions 5.6.0 through 5.6.8. The potential security risk is immense, given its broad usage across numerous online forums.
The severity of CVE-2023-25135 considered as Critical, as it allows a remote attacker to execute arbitrary code on a vulnerable system. On March 8, 2023, vBulletin acknowledged this vulnerability and swiftly issued security updates to mitigate it. Exploiting this Remote Code Execution (RCE) vulnerability occurs when a specifically crafted request dispatched to the vBulletin server, escalating the potential damage to the compromised system.
The risk associated with CVE-2023-25135 is profound. As it allows an attacker to execute arbitrary code, the potential threats range from data theft and unauthorized system access to the installation of malware. In the subsequent sections, we’ll delve into the intricacies of this vulnerability, the mechanics of its exploitation, and the recommended countermeasures to safeguard your vBulletin installations.
What is vBulletin?
Before diving deeper into the vulnerability, let’s understand what vBulletin is. vBulletin is a proprietary Internet forum software package developed by vBulletin Solutions, a division of Internet Brands. It’s written in PHP and uses a MySQL database server. Since its launch in 2000, it has become a dominant force in the online forum and community niche, providing rich features and robust functionality that enables users to create vibrant online communities.
The Details of the Vulnerability
The vulnerability lies in how vBulletin handles the deserialization of untrusted data. During this process, vBulletin attempts to read the object’s properties and methods. However, if the object contains malicious code, the code could potentially executed on the system.
Here is the flawed function verify_serialized():
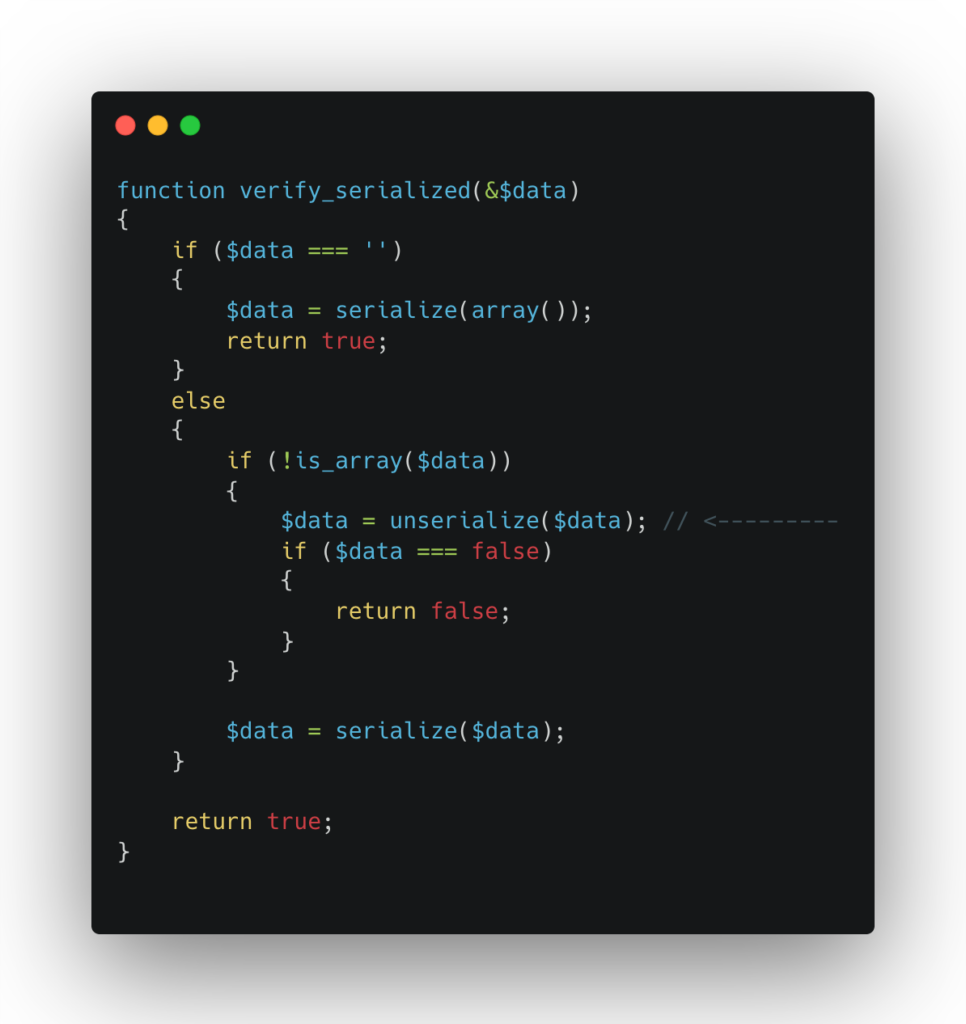
This function verifies whether a value serialized by deserializing it and checking for errors. This approach is flawed because it allows for the execution of malicious code during the deserialization process.
Exploitation
Exploiting CVE-2023-25135, as it turns out, involves using the user registration process to inject malicious code. The vulnerability lies in the ‘searchprefs’ field, which users can manipulate upon registration. This field not properly sanitized, meaning it does not correctly check or clean the data input by users.
An attacker can exploit this vulnerability by sending a specially crafted request to a vulnerable vBulletin server. The request would contain a serialized malicious object that gets deserialized by the server, leading to the execution of the malicious code.
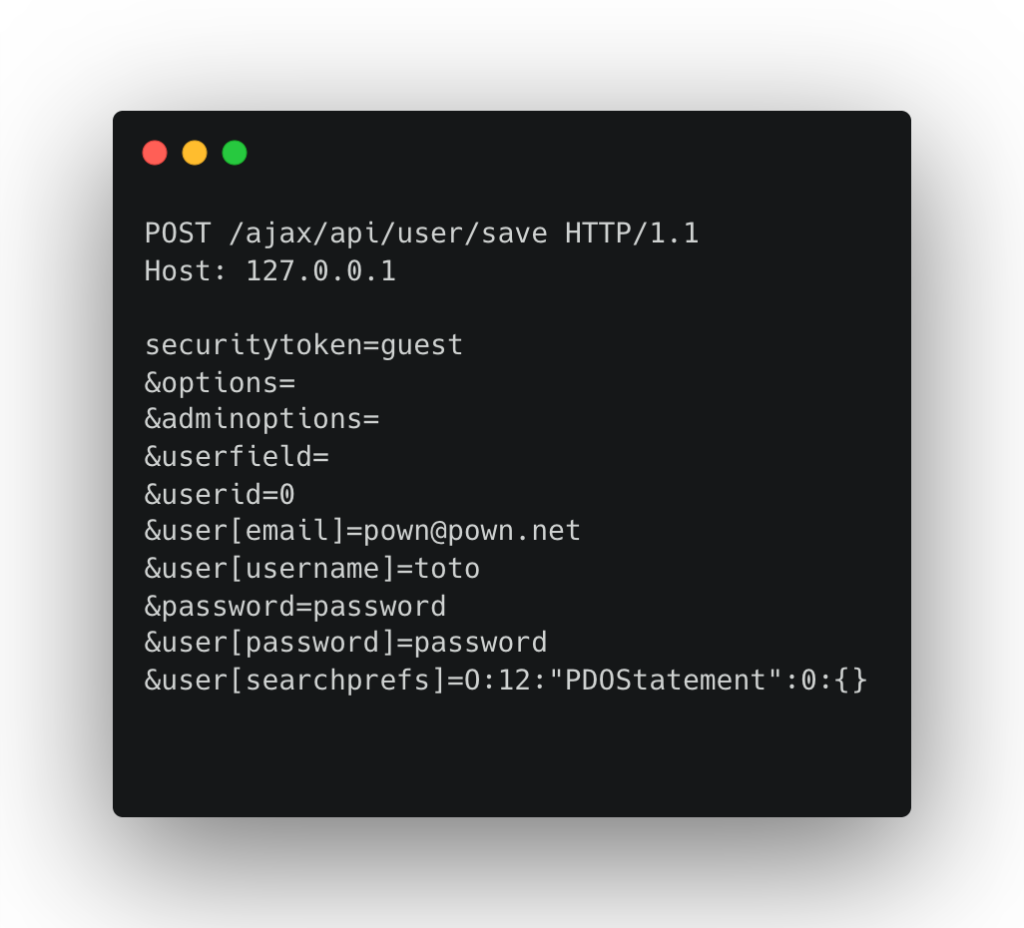
In this POC, the attacker sends a POST request to the “/ajax/api/user/save” endpoint on the vBulletin server. The security token set to ‘guest,’ meaning the request did send without needing any authentication. The user[searchprefs] field is the main point of interest. It now sets to a serialized PDOStatement object. When the server processes this request, the verify_serialized() function will attempt to unserialize the PDOStatement object, potentially executing any malicious code embedded within it.
Despite the initial discovery, exploiting this vulnerability to achieve Remote Code Execution (RCE) proved more challenging than initially anticipated. This is primarily because, although the PDOStatement object successfully unserialized, its methods cannot be directly controlled, which is necessary to achieve RCE.
In PHP, the deserialization of a PDOStatement object does not typically lead to code execution. This means further steps must taken to convert the deserialization into a full RCE exploit. This often requires intimate knowledge of the target framework, vBulletin, and potential interaction points where the deserialized object could lead to code execution.
For CVE-2023-25135, a ready-made POC script is available on GitHub, which can used for testing. This script can help you understand the exploit better and can also e used to test whether your vBulletin installation is vulnerable.
You can find the script here: vbulletin-exploits
How to Use the POC Script
To use the script, you need to follow these steps:
- Clone the repository to your local system. You can do this by opening a terminal and typing the following command:
` git clone https://github.com/ambionics/vbulletin-exploits.git `
- Navigate to the directory containing the script:
` cd vbulletin-exploits `
- Run the script against your vBulletin instance. Make sure to replace <url> with the URL of your vBulletin instance:
` python3 exploit.py <url> <command>
If your vBulletin instance is vulnerable, the script will return a successful exploitation message.
Mitigation
vBulletin has released a security update that addresses this vulnerability, and users strongly advised to update their vBulletin installations to the latest version to mitigate the vulnerability.
In addition to the update, further measures should taken to secure systems:
- Use a Web Application Firewall (WAF) to filter traffic and block malicious requests.
- Keep systems and software up-to-date with the latest security patches.
- Monitor systems for any suspicious activity.
- Implement this Yara rule in your SIEM
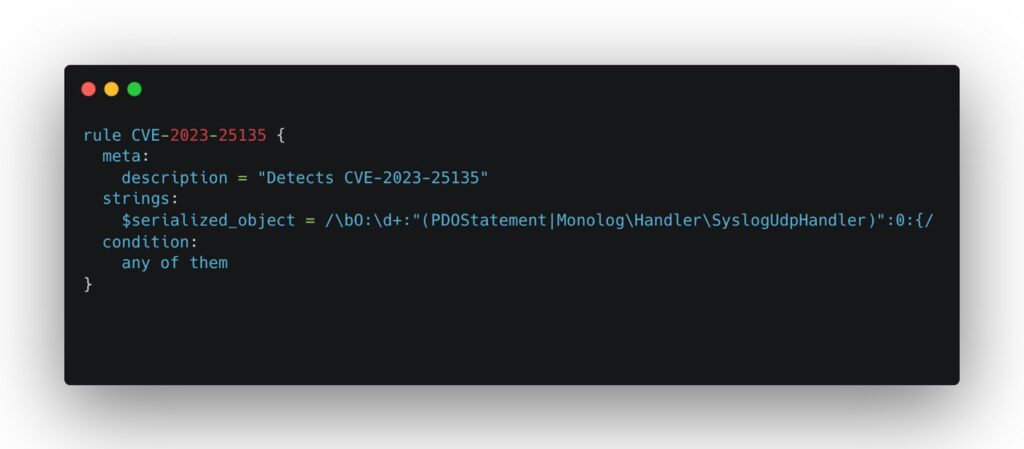
This rule will match any string that contains a serialized object of the type PDOStatement or MonologHandlerSyslogUdpHandler. These two types of objects can be used to exploit the vulnerability.
By following these recommendations, you can help protect your systems from attacks and mitigate the risk of exploitation of CVE-2023-25135.
Conclusion
CVE-2023-25135, a severe vulnerability in vBulletin, exposes the critical importance of regular software updates for cybersecurity. Given its potential for remote code execution, this vulnerability could have severe repercussions if left unpatched. This case is a stark reminder of the complexity of cybersecurity threats and the necessity of understanding the intricacies of potential exploits. Regular patching, continuous monitoring, and a solid grasp of underlying technical concepts remain crucial in maintaining a robust defense against such threats.