On May 31, 2023, Progress Software Corporation announced a critical vulnerability in their MOVEit Transfer software application. The vulnerability, assigned the CVE identifier CVE-2023-34362, is a SQL injection vulnerability that could allow an unauthenticated attacker to gain access to the MOVEit Transfer database.
The vulnerability exists in the MOVEit Transfer web application. It was found in all versions of MOVEit Transfer prior to 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1).
An attacker who successfully exploits this vulnerability could gain access to the MOVEit Transfer database. This could allow the attacker to steal sensitive data, such as usernames, passwords, and credit card numbers. The attacker could also use this access to install malware on the affected system or to launch other attacks.
What is Moveit?
MOVEit Transfer is a file transfer application allowing users to transfer files between different systems securely. It is used by businesses of all sizes to transfer files between offices, customers, and partners.
CVE-2023-34362 Vulnerability Detail
The MOVEit Transfer vulnerability, known as CVE-2023-34362, is a severe security issue targeted by the Clop ransomware group. This group exploited a SQL injection zero-day vulnerability in the MOVEit Transfer software to install a previously unseen web shell known as LemurLoot, allowing them to exfiltrate victims’ data and extort payments.
MOVEit is a managed file transfer solution that supports MySQL, Microsoft SQL Server, and Azure SQL database engines. The vulnerability lies in the MOVEit Transfer web application, which was found to be susceptible to SQL injection attacks. Successful exploitation of this vulnerability could lead to remote code execution, granting unauthenticated adversaries the ability to execute arbitrary code, disable anti-virus solutions, or deploy malware payloads.
The LemurLoot web shell installed by the attackers, initially observed under the name “human2.aspx,” was designed to blend in with legitimate files as part of the MOVEit Transfer software. Upon installation, the web shell generates a random 36-character password used for authentication. It then interacts with its operators by waiting for HTTP requests containing a header field named “X-siLock-Comment”, which must have a value assigned equal to the password set upon the web shell’s installation.
After authenticating with the web shell, operators can send commands that can:
- Retrieve Microsoft Azure system settings and enumerate the underlying SQL database.
- Store a string sent by the operator and then retrieve a file with a name matching the string from the MOVEit Transfer system.
- Create a new administrator-privileged account with a randomly generated username and LoginName and RealName values set to “Health Check Service.”
- Delete an account with LoginName and RealName values set to “Health Check Service.”
As of late May 2023, there were approximately 2,500 exposed MOVEit instances, primarily located in the U.S., demonstrating the software’s prevalence in enterprise environments.
The Progress Software Corporation, which is responsible for MOVEit Transfer, has issued advisories and provided patches for the affected versions of the software, which include:
MOVEit Transfer 2023.0.0
MOVEit Transfer 2022.1.x
MOVEit Transfer 2022.0.x
MOVEit Transfer 2021.1.x
MOVEit Transfer 2021.0.x
MOVEit Transfer 2020.1.x
MOVEit Transfer 2020.0.x
Exploitation by ATP’s
Here are the steps for the exploit that the CL0P ransomware group used to take advantage of the SQL injection vulnerability in MOVEit Transfer (CVE-2023-34362):
- Initial Access: The attacker targets the MOVEit Transfer web application that supports MySQL, Microsoft SQL Server, and Azure SQL database engines.
- Exploit Vulnerability: The attacker uses the SQL injection vulnerability (CVE-2023-34362) to send a crafted payload to a MOVEit Transfer application endpoint. This results in the modification and disclosure of MOVEit database content.
- Install Web Shell: The attacker installs a web shell named LEMURLOOT, on the MOVEit Transfer web application. This web shell was observed to masquerade as the legitimate file “human.aspx” by using the name “human2.aspx”.
- Create Authentication Password: Upon installation, the web shell creates a random 36-character password that will be used for authentication.
- Command and Control: The web shell waits for HTTP requests containing a header field named “X-siLock-Comment”. This field must have a value assigned equal to the password established upon the installation of the web shell. This serves as the authentication mechanism for the web shell.
- Execute Commands: After authenticating with the web shell, the attacker can pass commands to the web shell. The commands can perform various actions, such as:
- Retrieve Microsoft Azure system settings and enumerate the underlying SQL database.
- Store a string sent by the operator and then retrieve a file with a name matching the string from the MOVEit Transfer system.
- Create a new administrator-privileged account with a randomly generated username and LoginName and RealName values set to “Health Check Service.”
- Delete an account with LoginName and RealName values set to “Health Check Service.”
Impacts on Organization
The MOVEit Transfer vulnerability (CVE-2023-34362) has been exploited by the Clop ransomware group since May 2023, resulting in a series of breaches. The exploit chain for the vulnerability involves using SQL injection to obtain a sysadmin API token and executing remote code execution with elevated privileges. Clop ransomware group has been utilizing a previously unseen web shell, LemurLoot, to exfiltrate victims’ data and extort payments.
The vulnerability has affected several U.S. government agencies. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the FBI issued a joint advisory warning about the vulnerability of MOVEit, which later was found to have been used to breach several U.S. agencies, including ones tied to the US Energy Department.
In addition to the U.S. government, several businesses worldwide have also been impacted.
Two additional vulnerabilities (CVE-2023-35036 and CVE-2023-35708) have been found in MOVEit Transfer solutions, but they weren’t being actively exploited at the time of the reporting. Progress Software has released patches for these vulnerabilities, and it’s recommended to apply these patches, modify firewall rules to deny traffic to MOVEit Transfer until the patch can be applied, continuously monitor networks, update network firewall rules and remote access policies, and enable multi-factor authentication
OSINT & Threat Hunting
Open Source Intelligence (OSINT) can be used to discover potentially vulnerable instances of MOVEit Transfer on the internet. Two Shodan discovery methods and one Google Dork method have been identified:
Shodan Discovery Method 1: MOVEit SFTP Discovery
By searching for servers with the header “MOVEit+Transfer+SFTP”, we can identify potential MOVEit Transfer servers. However, it is essential to note that the SFTP protocol is not vulnerable but can be used to identify servers. As of June 15, 2023, 534 servers were found using this method.
Shodan Discovery Method 2: Cookie Discovery
The second method involves looking for servers with the header “DMZCookieTest=ifyoucanreadthisyourbrowsersupportscookies”. This is based on official MOVEit documentation . As of June 15, 2023, this method revealed 13,450 servers.
Google Dork Method 1: /human.aspx
The Google Dork method involves searching for Google results from “inurl:/human.aspx?”. This method has not been thoroughly verified, and additional software may use the same .aspx file name. However, it returns a significant number of MOVEit pages. As of June 16, 2023, this method returned approximately 6,690 results, but this number may be inflated as non-MOVEit results are included in the search results.
There are several ways to detect successful exploitation of this vulnerability. These include:
- Monitoring for unauthorized access to the MOVEit Transfer database.
- Monitoring for unusual activity in the MOVEit Transfer logs.
- Monitoring for signs of malware infection on the affected system.
If you notice any of these signs, it is essential to take action immediately to investigate and remediate the issue.
Threat Hunting
The diagram illustrates the steps an attacker would take to exploit the vulnerability:
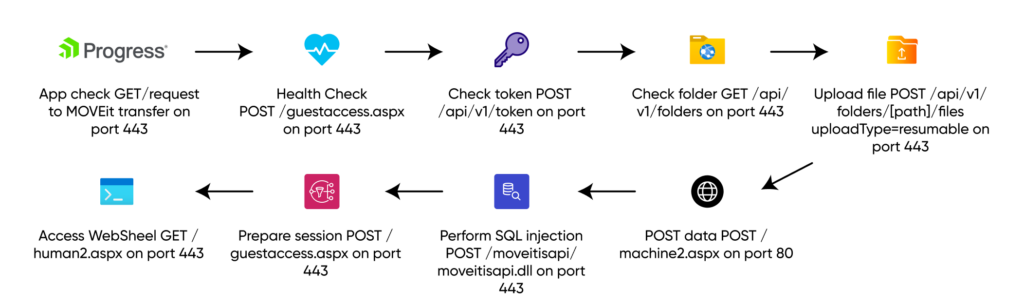
- App check – GET /
- Health check – POST /guestaccess.aspx
- Check token – POST /api/v1/token
- Check folder – GET /api/v1/folders
- Upload file – POST /api/v1/folders/[PATH]/files uploadType=resumable
- Post data – POST /machine2.aspx
- Perform SQL injection – POST /moveitisapi/moveitisapi.dll
- Prepare session – POST /guestaccess.aspx
- Upload file – PUT /api/v1/folders/[PATH]/files uploadType=resumable&fileId=[FILEID]
- Post data – /machine2.aspx
- Access WebShell – GET /human2.aspx
After these steps, the attacker interacts with the database and can exfiltrate data.
Mitigation
Immediate Mitigation Steps for MOVEit Transfer CVE-2023-35708:
Disable HTTP and HTTPS Traffic: This involves modifying firewall rules to deny HTTP and HTTPS traffic to MOVEit Transfer on ports 80 and 443. This step prevents users from logging into the MOVEit Transfer web UI, halts the functioning of MOVEit Automation tasks using the native MOVEit Transfer host, and disables REST, Java, and .NET APIs, as well as the MOVEit Transfer add-in for Outlook. However, SFTP and FTP/s protocols will continue to work as usual.
Administrative Access via Localhost: As a workaround for this mitigation, administrators can still access MOVEit Transfer by using a remote desktop to access the Windows machine and then accessing https://localhost/. More information on localhost connections can be found at: https://docs.progress.com/bundle/moveit-transfer-web-admin-help-2023/page/Security-Policies-Remote-Access_2.html.
Apply the Patch: As patches for supported MOVEit Transfer versions become available, they should be applied immediately. The list of supported versions can be found at: https://community.progress.com/s/products/moveit/product-lifecycle. Note that the license file remains the same when applying the patch within a major release.
Re-enable HTTP and HTTPS Traffic: Once the patch is applied and the security of the MOVEit Transfer environment is ensured, HTTP and HTTPS traffic should be re-enabled to restore standard functionality.
In addition to these steps, indicators of a potential breach can be found in certain database tables and log entries. The database tables “userexternaltokens”, “trustedexternaltokenproviders”, and “hostpermits” all had entries inserted to achieve the sysadmin access token. The “fileuploadinfo” table was altered to obtain RCE. Inspect these tables to look for any anomalous entries.
Log entries for endpoint traffic can be found in the following areas:
- <InstallDir>/Logs/DMZ_WebApi.log when requests are made to /api/v1/ endpoints.
- <InstallDir>/Logs/DMZ_WEB.log when requests are made to /guestaccess.aspx and relayed messages to /machine2.aspx .
- <InstallDir>/Logs/DMZ_ISAPI.log when requests are made to /moveitisapi/moveitisapi.dll?action=m2.
Monitor these logs for unusual activity or requests.
Conclusion
The MOVEit Transfer vulnerability CVE-2023-34362 is a stark reminder of the ever-present threats in our digital ecosystem. While patching and implementing recommended mitigations are vital in reducing risk, it is also crucial for organizations to maintain an ongoing, proactive approach to security. This includes regular audits, continuous monitoring, and ensuring all systems are up-to-date. We hope to stay one step ahead of the threats through these measures.



