As organizations go beyond simply migrating to the cloud and use cloud services strategically to accelerate their business outcomes, securing the cloud footprint has become a key element of this strategy. It’s also becoming increasingly complex with most organizations using multiple clouds, Saas-based tools, and security solutions within their stack to protect them. Gaining consistent visibility, prioritizing the most critical alerts and risks, and having the data to complete robust threat hunting and remediation means organizations can ensure strong security outcomes.
Many cloud service providers, including Amazon Web Services (AWS), are increasing the number of native security services and integration points for security partners to help customers gain the data they need to protect their business. These include AWS Security Hub, Amazon GuardDuty, Amazon Security Lake, and more. SentinelOne’s integrations with AWS native services and ingestion of AWS logs is a strategic focus to help customers stay secure.
This blog post explores the benefits of this integration, focusing on how it enhances security outcomes, leverages the AWS shared responsibility model, and improves visibility and threat hunting capabilities through the SentinelOne Singularity Platform.

Revisiting the Shared Responsibility Model
AWS focuses on security, both of the infrastructure and in equipping customers to make the best security decisions for their environments. Although AWS provides many security focused features and services, it recognizes the value and expertise of security vendors and chooses to prioritize a partner model, for innovation, integration, and even co-selling, that matches customers with the right security solutions for their business.
Part of the security approach with AWS is the Shared Responsibility Model, which delineates the security responsibilities between AWS and the customer. AWS is responsible for the security “of” the cloud, ensuring the infrastructure (hardware, software, networking, and facilities) that runs all AWS services. Customers are responsible for security “in” the cloud, which includes the configuration and management of the AWS services they use, data protection, and identity management. By partnering in security technologies, AWS and SentinelOne help organizations effectively manage their responsibilities within this model with leading-edge security solutions such as Singularity Cloud Security and Purple AI.
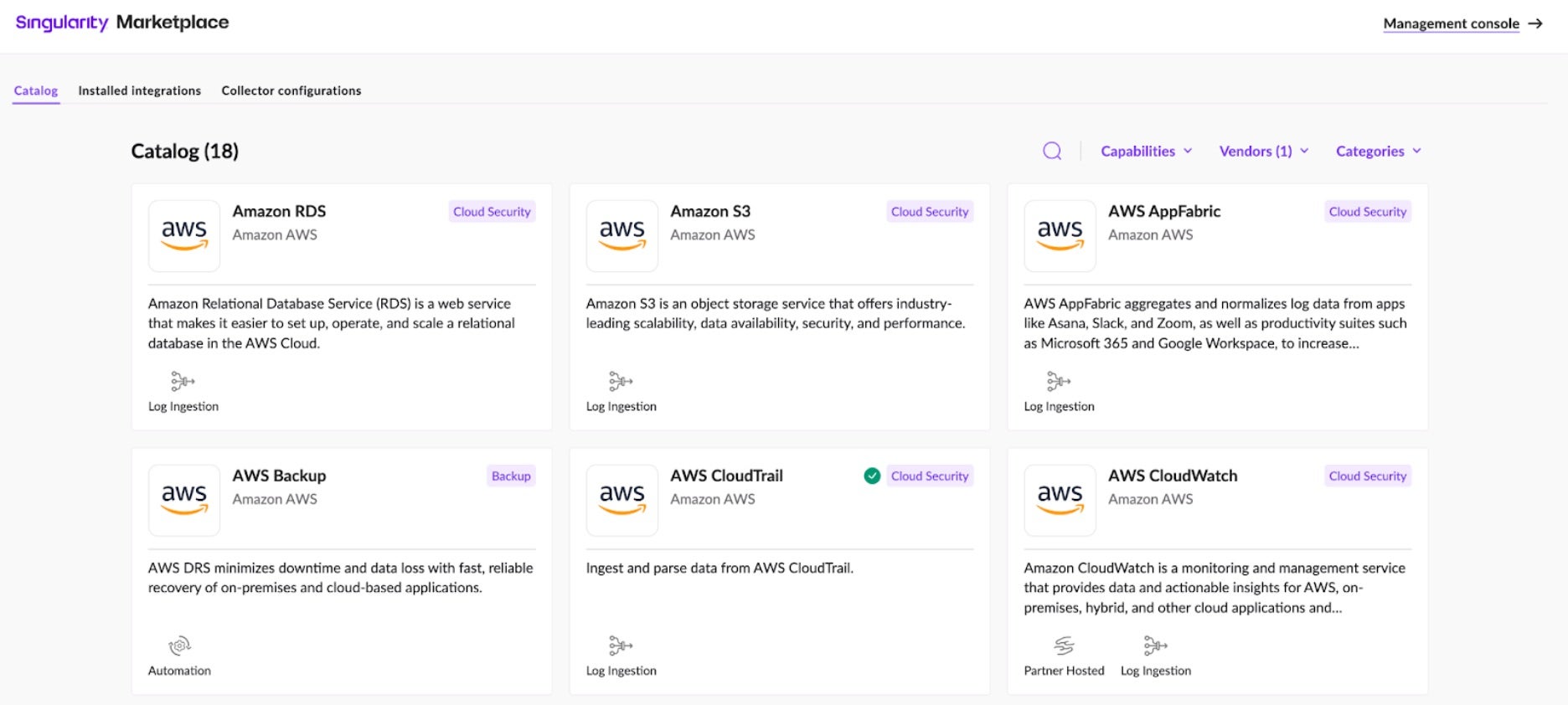
Singularity Marketplace
All SentinelOne integrations with AWS (and other technology partners) are available in the Singularity Marketplace, accessed directly from the SentinelOne management console. The process of downloading and installing these applications and integrations is user-friendly, involving simple click-throughs with clear guidance and documentation. This not only simplifies the operational aspect of security deployments but also minimizes the need for extensive manual configuration, allowing teams to focus more on strategic security tasks rather than technical setup.
Streamlining Data for Better Security Outcomes
Many of the SentinelOne and AWS integrations focus on SentinelOne ingesting key AWS data, or even third-party data stored in AWS, to help connect disparate or siloed datasets. By using AI and normalizing data using the latest in Open Cybersecurity Scheme Framework (OCSF) standards, the entire security process can be streamlined.
Key benefits of these types of integrations include:
- Accelerated threat detection, including advanced threat hunting – With real-time data from AWS services and data collected from SentinelOne solutions, customers can detect and respond to threats more quickly and accurately using AI-powered engines and the SentinelOne Storyline™ feature.
- Faster response and remediation times – By integrating first and third-party resources, threats can be mitigated quickly in entirety, ensuring business continuity.
- Streamlined security operations – By automating the ingestion, normalization, and analysis of logs, it reduces the workload on security teams. Purple AI can further streamline this as an automated SOC assistant.
- Improved compliance and reporting – Centralized logging and monitoring help meet regulatory requirements and simplify audit processes.
Integrating SentinelOne with AWS native services such as AWS AppFabric, Security Hub, Amazon Security Lake, and GuardDuty offers today’s businesses a comprehensive and leading-edge approach to securing their cloud environments.
Integrations with AWS Native Services
The SentinelOne Singularity Platform has had integrations with AWS native services for several years, and the list grows every year, notably with Amazon Security Lake and Amazon AppFabric. SentinelOne’s platform is known for being AI-driven, able to do advanced threat hunting using features like Storyline™. With the addition of Cloud Native Security (CNS) and Singularity™ Data Lake it’s become the ideal enterprise security platform for AWS customers to use. Here is a brief overview of just some of the newest, and most commonly used integrations between SentinelOne and AWS.
Resource Control Policies (RCPs)
Resource Control Policies (RCPs) are a new authorization policy managed in AWS Organizations that can be used to set the maximum available permissions on resources for the whole organization in order to establish data perimeters, and restrict external access. SentinelOne’s support for RCPs on AWS enables cloud administrators to secure access to resources confidently without restricting essential tools like SentinelOne’s Cloud Native Security (CNS).
By centralizing access control rules for key resources, RCPs allow for easy configuration of policies that permit SentinelOne’s CNS to scan for issues, vulnerabilities, and attack paths, minimizing the risk of over-permissioning or unintended external access. This integration enables a secure, compliant, and efficient environment for CNS operations on AWS.
AWS Security Hub
AWS Security Hub provides a centralized platform to manage and aggregate security alerts from multiple AWS accounts and services, enhancing the visibility and management of security threats. The SentinelOne integration for Security Hub sends threat information from SentinelOne Agents running on AWS workloads to AWS Security Hub. AWS Security Hub then aggregates, organizes, and prioritizes security alerts that enable security teams to respond to any threats in progress. The integration retrieves results, including metadata from the SentinelOne Management Console, and pushes them to Security Hub. The incidents are converted to the AWS Security Finding Format (ASFF) for incident investigation.
Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors AWS accounts and workloads for malicious activity and delivers detailed security findings for visibility and remediation. This integration enables collection and analysis of logs from GuardDuty into the Singularity Cloud Security Platform for correlation and further analysis.
Amazon Security Lake
Amazon Security Lake is an AWS security service that unifies and evaluates security logs from cloud and on-premises sources. Singularity™ Cloud Security and the Amazon Security Lake use OCSF to simplify log analysis. This is a particularly interesting integration as both SentinelOne and AWS offer Security Lakes with SentinelOne’s new solution, Singularity™ Data Lake. SentinelOne will ingest logs from the Amazon Security Lake as part of the initial integration. The second phase of this integration, a bi-directional feed, is planned and will allow customers to choose the best option depending on their requirements.
AWS CloudTrail
AWS CloudTrail records actions by a user, role, or AWS service from the AWS Management Console, command-line interface, SDKs, or APIs. This integration lets you ingest CloudTrail logs. In SentinelOne you can view, monitor, and query the data in Singularity™ Data Lake.
AWS Config
AWS Config is a service that provides an inventory and configuration history of AWS resources. The service helps you understand how your infrastructure is set up, how it is evolving, and whether it complies with your organization’s policies and security standards. The integration lets you import AWS Config events into SentinelOne so you can view, monitor, and query the data in Singularity™ Data Lake.
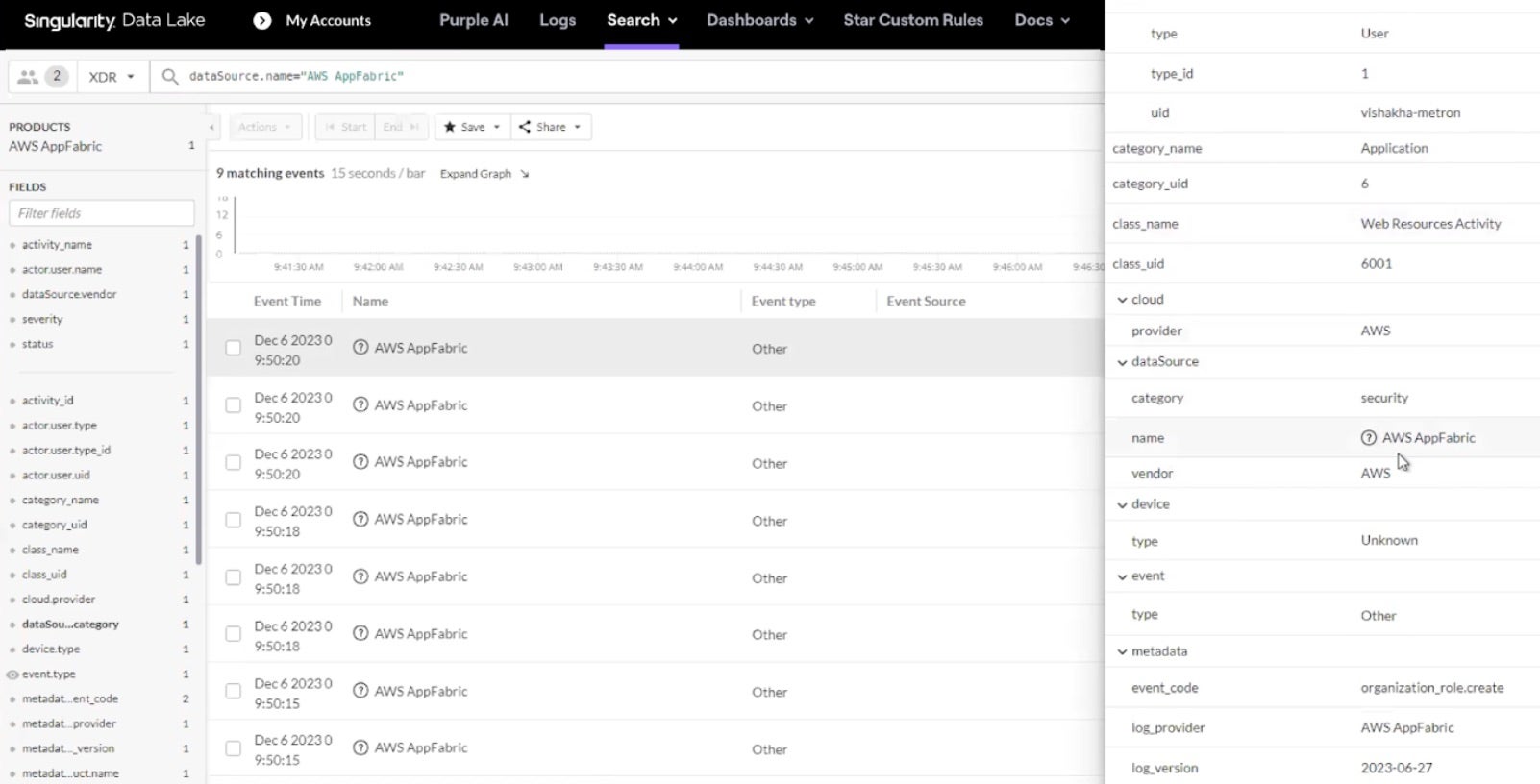
AWS AppFabric
AWS AppFabric gathers and organizes log information from commonly used apps and productivity tools like Asana, Slack, Zoom, Microsoft 365, and Google Workspace. This makes it easier to monitor all your applications and saves money by avoiding the need for individual connections between each one. This integration allows logs from AppFabric to be collected and analyzed in the Singularity Cloud Security Platform using the OCSF format.
Conclusion
Incorporating SentinelOne with AWS native services and logs is a strategic move for organizations looking to bolster their security posture. By leveraging the AI-powered capabilities of SentinelOne and the comprehensive capabilities of AWS services such as AppFabric, Security Hub, Amazon Security Lake, and GuardDuty, organizations can achieve better security outcomes. These integrations enhance visibility, streamline operations, and enable proactive threat management, all while aligning with the AWS shared responsibility model.
Take a self guided tour of the SentinelOne Singularity™ solutions here or, see our CNAPP solution available in the AWS Marketplace.


