Market research soon to be published in the first annual SentinelOne Cloud Security Report shows that cloud security professionals are drowning in data, yet lacking insights. While many point-specific solutions like cloud security posture management (CSPM), cloud detection and response (CDR), and cloud workload protection platforms (CWPP) are now mainstream, organizations are struggling with data silos as they seek to derive meaning from a long list of cloud security alerts. SentinelOne’s AI-powered CNAPP, Singularity Cloud Native Security (CNS) solves each of these pain points.
In this blog post, learn how Singularity Cloud Security combines the rapid insights and value realization of an agentless CNAPP, with the stopping and forensics power of a runtime agent, to realize AI-powered protection for modern cloud operations. SentinelOne consolidates security data from native and third-party security sources into the Singularity Data Lake.

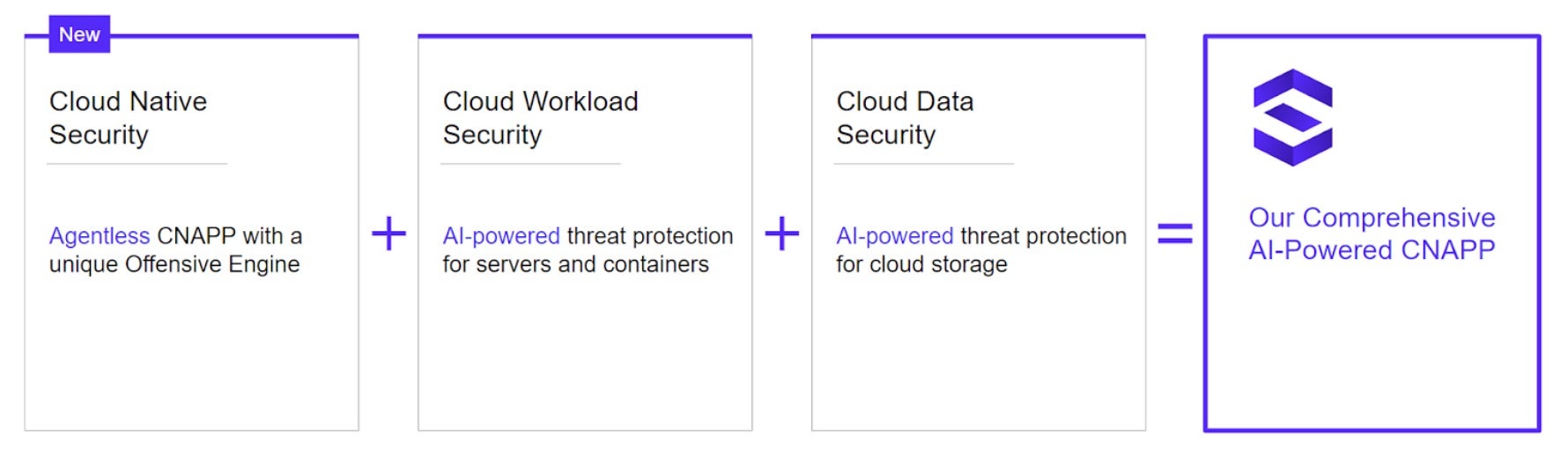
Agentless CNAPP and The Attacker’s Mindset
Singularity Cloud Native Security (CNS) from SentinelOne is an agentless CNAPP with a unique Offensive Security Engine™ that thinks like an attacker, to automate red-teaming of cloud security issues and present evidence-based findings. We call these Verified Exploit Paths™. Going beyond simply graphing attack paths, CNS finds issues, automatically and benignly probes them, and presents its evidence.
The Offensive Security Engine might indicate something like, “We found this misconfigured Amazon EC2 instance. We were able to curl out to our dummy C2 server and install a random file. Here is the proof.” With this, cloud security practitioners can prioritize their backlog better and focus on what is truly important rather than tread water in a sea of theoretical noise.
Beyond offensive security, CNS includes many more multi-cloud CNAPP capabilities. Here are just a few:
- CSPM (Cloud Security Posture Management) includes over 2,000 built-in resource configuration checks, with support for custom policies.
- Secrets Scanning – CNS finds over 750 types of cloud secrets and access keys. That’s an order of magnitude more than most alternatives.
- Agentless Vulnerability Scanning for deployed VMs, containers, and registries, to identify known vulnerabilities.
- IaC Scanning – Shift left to identify pre-production issues in IaC templates with over 700 checks across popular IaC frameworks like Terraform, CloudFormation, etc.
- Container & Kubernetes Security (KSPM) finds overly permissive roles, exposed APIs, and more.
- CDR (Cloud Detection & Response)
- Graph Explorer visualizes attack paths and streamlines analysis. Graphical query of vulnerabilities is both intuitive and powerful.
Real-Time Runtime Security
Alongside CNS, customers can also benefit greatly from Singularity Cloud Workload Security (CWS). CWS is real-time cloud workload protection (CWPP) for hybrid cloud workloads. CWS detects and stops runtime attacks like zero-days, ransomware, and fileless memory injection exploits. The two primary benefits of a CWPP agent are real-time threat detection and remediation response, and forensic visibility of workload telemetry.
The Significance of Real-Time Threat Protection
Why the emphasis on real-time? What makes real-time threat protection so important? Runtime attacks are automated – they occur and spread in seconds. A runtime attack example on AWS Fargate on Amazon ECS was discussed in yesterday’s blog post. In brief, a threat actor exploits a known vulnerability and curls out to C2 infrastructure to download and run a malicious shell script that, in turn, runs a malicious python script that runs base64-encoded malware. The entire attack sequence happens in seconds.
The longer an attack is allowed to fester, the costlier and messier the clean-up. In addition to being intuitively obvious, the data in the annual IBM X-Force Cost of Data Breach Report continue to prove this out, year after year. Only an agent can deliver real-time threat detection and response.
The Importance of a Forensic Data Log
When there is a runtime attack, incident responders rely upon a record of workload telemetry to conduct their analysis. Understanding the root cause of an incident is foundational to determining its resolution. Only a CWPP agent can observe and record kernel-level telemetry.
CWS delivers real-time runtime protection for workloads whether in public or private cloud. Considering AWS for example, whether those workloads run on Amazon EC2, Amazon ECS or EKS, or even on AWS Fargate, SentinelOne delivers proven performance that is:
- Powered by AI
- Built on eBPF since 2019
- Easily deployed
AI-Powered Data Security for Amazon S3
Amazon S3 (Simple Storage Storage) is one of AWS most popular services. Amazon S3 is an object storage service that offers industry-leading scalability, availability, and performance. To prevent S3 buckets from becoming a forward operating base of threat actors in which they can deposit malware and to prevent downstream data risks, SentinelOne launched Threat Detection for Amazon S3 (TD4S3).
Part of the Singularity Cloud Data Security product line, TD4S3 is machine-speed protection which detects and eliminates malware from S3 buckets. New files are automatically scanned, and existing files can be scanned on-demand. All file scans happen locally, so that no sensitive data ever leaves an organization’s AWS network.
TD4S3 leverages SentinelOne’s proprietary Static AI Engine, trained on nearly a billion malware samples over the last 10 years. Any files judged to be malicious are automatically encrypted and quarantined. Flexible policies automatically discover buckets at scale, so you do not have to name them one by one.
Learn More at AWS re:Inforce 2024
Come see SentinelOne’s AI-powered CNAPP at AWS re:Inforce 2024, Booth #427 for a demo and in-depth discussion. Notable integrations with AWS native services include Amazon Security Lake, AWS Security Hub, Amazon GuardDuty, AWS CloudTrail, and many more.
Conclusion
Singularity Cloud Security is SentinelOne’s unique approach to CNAPP. We combine the best of agentless and agent-based capabilities to deliver unmatched performance and convenience. Cloud Native Security (CNS) is the agentless component that uses an attacker’s mindset to help cloud security practitioners focus on proven exploitable issues. All solutions within Singularity Cloud Security are integral to SentinelOne’s Singularity Platform and Singularity Data Lake for unified visibility and AI-powered insights.
To learn more about the value of agentless CNAPP and applying an attacker’s mindset to better secure your AWS cloud operations, head over to the Cloud Native Security homepage for a 2-minute, self-guided tour. Connect with one of our cloud security experts for a personalized demo today.




