The National Vulnerability Database (NVD) is a critical – yet often overlooked – element of an organization’s security defenses. Established to provide a catalog of known software vulnerabilities, it has become an authoritative source of vulnerability intelligence. However, the NVD faces a troubling backlog of vulnerabilities raising existential concerns about its efficacy.
This blog post takes a dive into what this means for organizations, what actions the industry leaders are taking to mitigate the challenges, and how solutions like Singularity Vulnerability Management are set to help businesses identify and prioritize all types of risk across their attack surfaces.

A Brief History of the NVD
Launched in 2005 by the National Institute of Standards and Technology (NIST), the NVD was created as a repository for the U.S. government to standardize and communicate information on publicly disclosed vulnerabilities. Utilizing the Common Vulnerabilities and Exposures (CVE) system, the NVD provides a centralized source for identifying and evaluating security flaws. Over the years, the NVD has evolved, integrating additional metrics such as the Common Vulnerability Scoring System (CVSS) to assess vulnerabilities’ severity and prioritize remediation efforts.
One of the most important benefits of the NVD is standardization, ensuring that all stakeholders from researchers, security teams, and security vendors, are on the same page regarding how they identify and mitigate vulnerabilities. The NVD enables organizations of all sizes to improve their security posture by offering open access to vulnerability data.
This democratization of information allows smaller businesses, which may lack extensive cybersecurity resources, to leverage the same vulnerability data as larger enterprises. To support the dissemination of this information, the NVD offers integration of vulnerability data via public APIs that many vendors integrate into their IT and Security products. The NVD API has its own set of challenges at enterprise scale with API rate limiting and occasional API call failures.
The NVD in Crisis | Backlogs & Wait Times
Despite its historical and practical significance, the NVD has been grappling with a substantial backlog of vulnerabilities since issues emerged in February of this year. Just in 2024, there have been over 18,000 vulnerabilities submitted to the NVD, yet 75% remain unprocessed waiting to be analyzed. The volume of submissions to the NVD has skyrocketed in recent years as the sheer number of vulnerabilities being discovered overwhelmed the systems and resources in place.
As the volume has grown, so has the complexity and sophistication of vulnerability exploits, which now require more time to analyze. Coupled with the recent cuts to NIST’s budgets, it’s a perfect storm of vulnerability overload and staffing shortages that create delays in vulnerability processing.
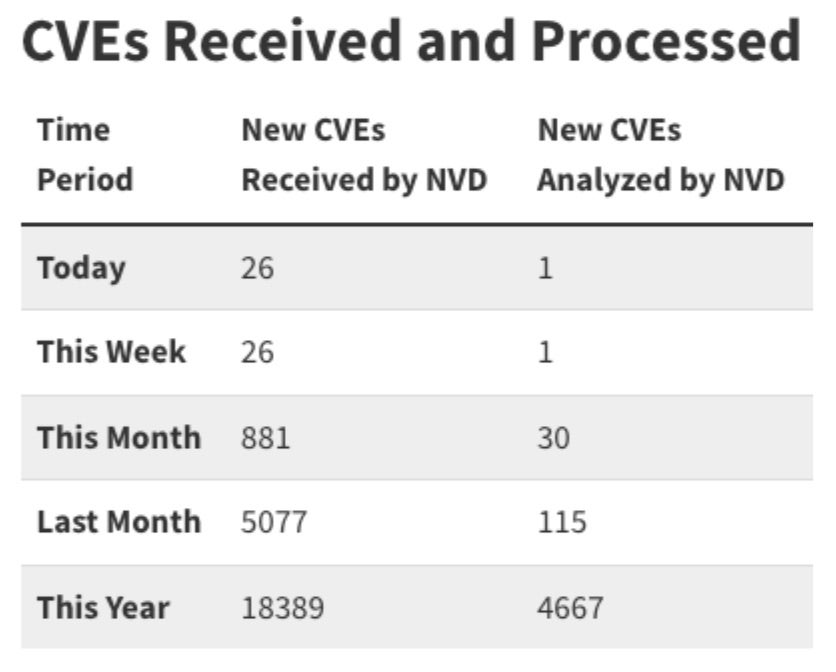
On average it takes 44 days from a vulnerability disclosure to it being exploited in the wild. Adelay in processing and publishing new vulnerabilities means that security teams are operating with outdated information and aren’t able to assess and mitigate risk promptly. If vulnerabilities aren’t addressed in a timely manner it could lead to an incident.. Without the enrichment and context the NVD provides – including CVSS scoring – vulnerabilities become more difficult to prioritize. A critical vulnerability may be overlooked without that context, while teams spend time chasing lower priority vulnerabilities. Many customers who rely on NVD feeds are now questioning the future viability of the NVD and whether NIST is the right organization to lead it.
What Is the Industry Doing About It?
In an open letter addressed to U.S. Congress and the Secretary of Commerce, 50 cybersecurity professionals including SentinelOne’s Staff Product Manager Maor Kuriel urged Congress to urgently “establish a plan, with clear timelines and accountability, to improve NVD processes and operations.” In the letter, the NVD was described as “the backbone of vulnerability management across the globe” and that delays “have disrupted essential resilience efforts across the public and private sectors”. The letter goes on to offer recommendations on how the NVD should be treated as critical infrastructure given its importance to U.S. cyber infrastructure.
Recently, NIST announced additional resourcing for an initiative to clear the backlog through a consortium of industry partners, which may go into effect as soon as the end of this year. Despite the contract to improve processing rates, the outdated NVD infrastructure persists. NIST is working on longer-term modernization plans and reiterated that it’s the right agency to maintain the NVD going forward, however, some in the industry are skeptical.
“No modern database should choke and be down for 3 ½ months (and counting) due to a sudden increase in workload”, said Tom Alrich, leader of the OWASP SBOM Forum project. “In fact, no modern database should be down for even a day due to any technical problem, let alone 3 ½ months. But, we’ve known for a long time that there are multiple single points of failure in the NVD’s infrastructure.”
Vendors like VulnCheck have stepped in to help fill the gap by offering free feeds like NVD++, a free community alternative to the NVD APIs that provide similar enrichment of vulnerability data while the NVD issues are being resolved. The Cybersecurity and Infrastructure Security Agency (CISA) is also contributing to help clear the backlog, announcing a “Vulnrichment” initiative in which it analyzed and enriched 1,300+ vulnerabilities.
The Path Forward | Asking the Right Questions
Given the current state of the NVD, cybersecurity and IT operations teams need to adopt a proactive stance. Here are key questions business leaders can ask their security vendors to ensure robust vulnerability management:
- How do you prioritize vulnerabilities amidst NVD delays? Vendors should have a clear strategy for prioritizing and addressing vulnerabilities, even without immediate updates from the NVD.
- What supplementary sources do you use? Vendors should integrate multiple sources of threat and vulnerability intelligence to mitigate the impact of NVD backlogs.
- Can you provide real-time updates on emerging threats? Real-time intelligence is crucial for staying ahead of potential exploits.
- What are your plans for future-proofing against emerging vulnerabilities? As technology evolves, so do potential threats. Vendors should articulate their strategies for anticipating and countering future vulnerabilities.
Best Practices for Security Teams
Security teams can also refine their internal processes to navigate the current landscape effectively. Essential best practices include:
- Regularly Auditing Your Security Posture – Continuous assessment of an organization’s security measures ensures preparedness and improves security posture.
- Investing in Vulnerability Intelligence – Proactively sourcing vulnerability intelligence from multiple sources can provide a more comprehensive understanding of the threat & vulnerability landscape and reduce reliance on the NVD.
- Implementing Intelligent Solutions – Leveraging AI tools in vulnerability management can help identify, prioritize, and remediate issues more rapidly.
- Encouraging Vendor Collaboration – Maintain open communication channels with vendors to ensure alignment on security priorities and product coverage updates.
SentinelOne’s Answer | Singularity Vulnerability Management
As part of the Singularity Platform, Singularity Vulnerability Management is a network discovery and vulnerability management solution that identifies and prioritizes risk to your enterprise attack surface. Singularity Vulnerability Management detects vulnerabilities across applications and OSs and provides dynamic prioritization based on the likelihood of exploitation by threat actors and business criticality. SentinelOne utilizes multiple third-party intelligence sources and analysis methods to provide coverage and context of the latest vulnerabilities despite the shortcomings at the NVD, helping IT and security teams prioritize active risks and exploitations.
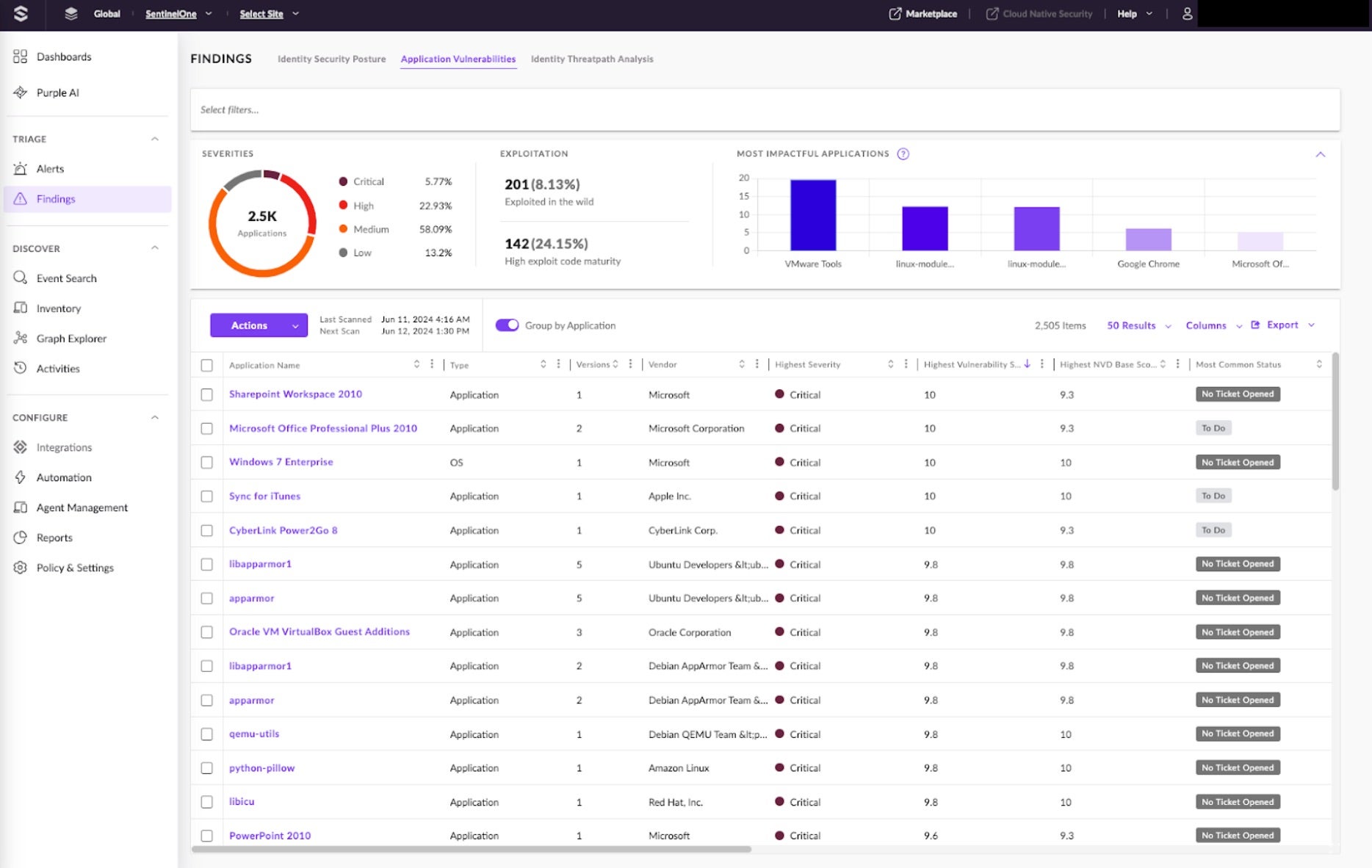
The SentinelOne agent can fulfill EDR, vulnerability management, and compliance requirements, without having to deploy network scanners which add cost, complexity, and bandwidth challenges. Consolidation of EDR and vulnerability management workflows in the Singularity Platform enables graph-based correlation of vulnerabilities and threats so teams can visualize risk from pre-compromise to post-compromise. The Singularity Platform offers single agent, single console simplicity to achieve maximum risk reduction with minimum efforts.
Conclusion
The National Vulnerability Database remains a cornerstone of cybersecurity, but its current backlog forces IT and security teams to ask tough questions about their vulnerability management practices. Security teams can better navigate these challenges by asking their vendors the right questions about how they are evolving their products to deal with persistent NVD issues. SentinelOne is at the forefront of solving challenges in vulnerability management and can be a partner to help you navigate the complexities and mitigate the risk of the NVD. Take a tour of Singularity Vulnerability Management here.


