Black Basta Ransomware: In-Depth Analysis, Detection, and Mitigation
Summary of Black Basta Ransomware
Black Basta first emerged in early 2022. The ransomware family is an evolution of the Hermes/Ryuk/Conti families. Black Basta was heavily advertised in underground cybercrime markets. Black Basta practices double extortion – demanding payment for a decryptor, as well as for the non-release of stolen data. There are Windows and LInux variants of Black Basta ransomware. The group is responsible for hundreds of attacks against global targets of varying sectors.

February 2025 Update: Nearly a year’s worth of Black Basta chat logs have been released on Telegram, providing detailed insight into the groups operational workflow, reconnaissance activities, and specific userID and details on their tactics, techniques, and procedures (TTPs).
What Does Black Basta Ransomware Target?
Black Basta ransomware has been known to target a wide range of industries, including healthcare, government, financial services, education, and media. Targeting within the CIS (Commonwealth of Independent States) is discouraged. Across 2023 and 2024, Black Basta operators heavily impacted healthcare, manufacturing, and financial services organizations. Their estimated earnings, towards the end of 2024, was in the hundreds of millions of dollars.
How Does Black Basta Ransomware Spread?
Black Basta is deployed in multiple ways: via Cobalt Strike or a similar framework, and through email phishing. BlackBasta is often delivered as a secondary infection. For example, following a Qakbot infection. Cobalt Strike is the group’s preferred attack framework. Configurations, deployments, and data extraction are automated via Ansible playbooks. The group dynamically generates C2 profiles via open-source methods (random_c2_profile). Black Basta operators rely on massive spam campaigns in conjunction with device exploitation where necessary. Multiple dropper formats have been observed including VBS, DLL, and DOC payloads.
Black Basta Ransomware Technical Details
Black Basta variants have been observed on Windows and Linux systems. Black Basta infections began with Qakbot delivered by email and macro-based MS Office documents, ISO+LNK droppers and .docx documents exploiting the MSDTC remote code execution vulnerability, CVE-2022-30190.
Manual reconnaissance is performed when Black Basta operators connect to victims through the Qakbot backdoor.
Reconnaissance utilities used by the operator are staged in a directory with deceptive names such as “Intel” or “Dell”, created in the root drive C:\.
For network scanning, Black Basta uses the SoftPerfect network scanner, netscan.exe. In addition, the WMI service is leveraged to enumerate installed security solutions. The ransomware will take steps to disable commonly used endpoint security products prior to initiating the encryption process.
Beyond the reconnaissance stage, Black Basta attempts local and domain level privilege escalation through a variety of exploits. We have seen the use of ZeroLogon (CVE-2020-1472), NoPac (CVE-2021-42287, CVE-2021-42278) and PrintNightmare (CVE-2021-34527).
Black Basta also employs an array of custom scripts and tools within their campaigns. The February 2025 Black Basta Chat Leaks provide a great deal more insight into the group’s TTPs, including specifics on tool use and victim reconnaissance.
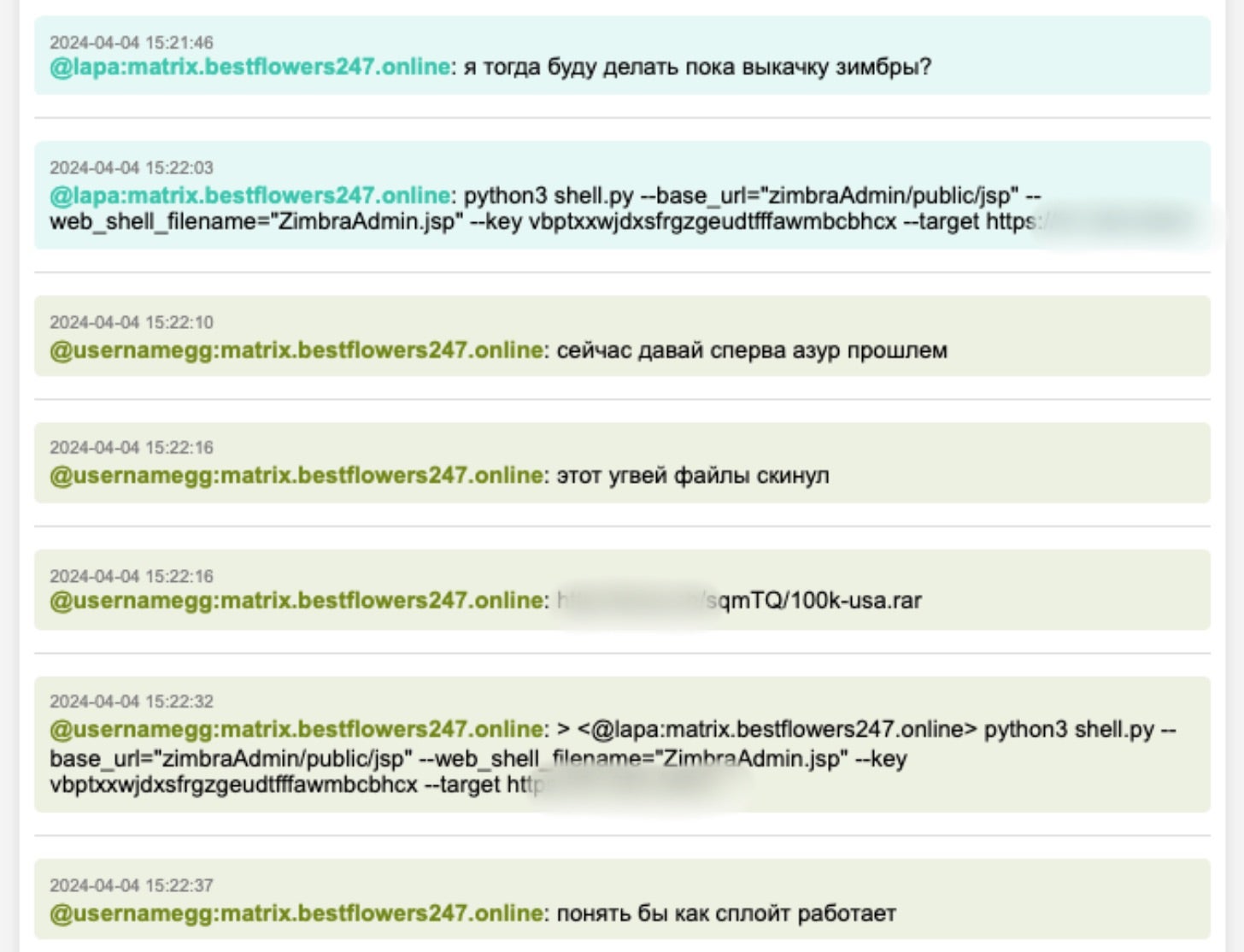
Black Basta operators controlled an extensive infrastructure to support their storage and traffic management requirements. This includes NgINX-based proxies, rotating VPS instances for C2, FTP servers for staging and data storage. The preferred communication platforms were Matrix and Telegram. The specific CVEs highlighted across the leaks (discussed for use in targeting) are:
CVE-2023-23397 Microsoft Outlook CVE-2023-29357 Microsoft Windows CVE-2023-35628 Microsoft Windows CVE-2023-36394 Microsoft Windows CVE-2023-36745 Microsoft Exchange Server CVE-2023-36844 Juniper Networks Junos OS CVE-2023-36845 Juniper Networks Junos OS CVE-2023-36874 Microsoft Windows CVE-2023-36884 Microsoft Windows CVE-2023-4966 Citrix NetScaler ADC CVE-2023-7028 GitLab CE/EE GitLab CE/EE CVE-2023-6875 WordPress, POST SMTP Mailer – Email log, Delivery Failure Notifications, Mail SMTP for WordPress plugin CVE-2024-1086 Linux Kernel, Linux kernel's netfilter: nf_tables component CVE-2024-1708 ConnectWise,ScreenConnect CVE-2024-1709 ConnectWise,ScreenConnect CVE-2024-21338 Microsoft,Windows CVE-2024-21413 Microsoft,Outlook CVE-2024-23897 Jenkins, Jenkins 2.441 and earlier CVE-2024-26169 Microsoft Windows CVE-2024-3400 Palo Alto Networks,GlobalProtect CVE-2024-21762 Fortinet Fortinet FortiOS CVE-2024-23108 Fortinet FortiSIEM CVE-2021-40444 Microsoft MSHTML CVE-2022-27925 Zimbra Collaboration Suite CVE-2017-5715 Intel CPUs CVE-2017-5753 Intel CPUs CVE-2017-5754 Intel CPUs CVE-2023-3519 Citrix ADC and Gateway CVE-2023-3466 Citrix ADC and Gateway CVE-2023-3467 Citrix ADC and Gateway
The group employs secretsdump.py alongside various other commodity keyloggers for credential harvesting and extraction. PowerShell commands and other LOL methods are used for firewall manipulation and traffic tunneling.
How to Detect Black Basta Ransomware
- The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to Black Basta.
In case you do not have SentinelOne deployed, detecting this ransomware requires a combination of technical and operational measures, which are designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
- Use antimalware software, or other security tools, which are capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic, and look for indicators of compromise, such as unusual network traffic patterns, or communication with known command-and-control servers.
- Conduct regular security audits and assessments, to identify vulnerabilities in the network and the system, and to ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including how to identify and report suspicious emails, or other threats.
- Implement a robust backup and recovery plan, to ensure that the organization has a copy of its data, and can restore it in case of an attack.
How to Mitigate Black Basta Ransomware
The SentinelOne Singularity XDR Platform detects and prevents malicious behaviors and artifacts associated with Black Basta.
- The SentinelOne Singularity XDR Platform can return systems to their original state using either the Repair or Rollback feature.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of ransomware attacks:
- Educate employees: Employees should be educated on the risks of ransomware and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments and avoid opening them or clicking on links or buttons.
- Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts and regularly update and rotate these passwords. Passwords should be at least eight characters long and include a combination of uppercase and lowercase letters, numbers, and special characters.
- Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or the use of physical tokens or smart cards.
- Update and patch systems: Organizations should regularly update and patch their systems to fix any known vulnerabilities and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices and disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks or other disasters. This includes creating regular backups of all data and systems and storing these backups in a secure, offsite location. The backups should be tested regularly to ensure they work and can be restored quickly and easily.
Indicators of Compromise (IoCs)
databasebb.top bastad5huzwkepdixedg2gekg7jk22ato24zyllp6lnjx7wdtyctgvyd.onion aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd.onion stniiomyjliimcgkvdszvgen3eaaoz55hreqqx6o77yvmpwt7gklffqd.onion orders44vz5yl7y6xajzxsdo2n6niaqu73ty4tx6ncwqnc752yzae4ad.onion 45.63.1.88 144.202.42.216 144.202.38.240 185.244.216.102 179.60.149.5 betterbossing.com appconfigdev.com cloudnetrecovery.com itechnetworkbd.com techservconsult.com thefetchapi.com docu-duplicator.com posetoposeschool.com blazingradiancesolar.com 104.255.220.21 65.181.111.9, 213.108.22.46 94.228.169.123 178.236.247.73 149.248.76.130 23.81.246.14 192.52.166.141 bestflowers247.online matrixtcFJHPDblmt2rg.network matrix.bestflowers247.online a996ccd0d58125bf299e89f4c03ff37afdab33fc ff57cda4829978d8b6f7f1f31356f291b37acaa6 fde1579fe21407b14c803ce472d39dece44fa640 f70a68cb9c9548e644b14fa7f6af0e86cd3720ed f607fe3750a01bf778c72f67feedeabac50e39e1 f5ef789c9faa54e39fdf5392eb072f6f39fd6cab f562348d01bde3e3d4af3ebdf6cd74121222ad3e f30fe1945291dd09770a0886c0f984e0d7e44850 f269ddffa7a741c879d712d7009a112402aaa0b2 f0edb016733e67cda8d0bdf60ed036c90dc5dc4d ec1408f8cfb118ab3f0a2c8ffe411f5bf2f94091 ebc0863d9b5296ba6f923eb784872c4b2ae26a36 e6868b55afbc3279ae4cd81ae9a9528ac2063b99 e5ba4839853c118e20fd59ec99216d64548accc3 e46a78ef1ac84a0a5ff81fec20c1c4bb1a882eab dfd3cb8070999ddc09e87d1603bbdc0bb79c34f5 df1c7a2b6e79b4739b35dfae7f6294d26365fe28 ded15a2c5b75b8ff1256e35c0d6f270f9bc0ec3e de355b70f27a6d6a899daf17a5fa98b7ad6a4f4f db497b95c79e41212577db0ba06777b62db209ff dad124d9700e973dd9a7f654fe03783b43264cd8 d9e452495d6d90465a3bbec3cad5ec921242e21e d6a29e373bb094cdc5ff9d403f5791024ca559bb d442065cd24ee151b2890b214ae09d1dc76c5011 d32e44f7e04a8c84e7159ed020dcf26b6e51416e ce043b1a6906a69aa1a82bfbbedda53fb86205d1 cb41d4512b2ecedda63b2c273e5af15a8dd90da1 cb2ca7306b8df952a4135b1f3c0b29b82a85a065 c6497099760d5badb5b2bf800bf8d502b486f36d c5dbae856d81bb1c1df14160db219158e3a045a1 c4b7d00b14abb3b7c98cdcd50e95332959909784 c420f58eb9822a8550b37ec33175b0e88d18ab44 c3742b6251c5ac1769767c550a8a89b156898375 bcc5f688ffbde19923c90a61e12f1bc4d8094f5b ba1a39bcedd7ddc7f069e96e220035d5c4844d32 b95c516bce5ff142acbe27db112d2e7e07fce3f8 b77875ba47716cc7f05ec86c02467b486c222563 b2cc8f434e6fb012dbdae89d7c8b1d8ea95a7ad3 b075ae2ecd30f9716911c707e2dbdcc261c9735e afec262477d24c9bd40fa3aad3a8a2fa4900e4bd abc6420dab7630472cb1d6e0a2619f19e007962f ab72e3c2c6b7ee7c6d075a120d8a867091158478 aa644941c54bf7e76ff20ba6fc208c176ed865a0 aa54013aeb502b4a936331deb76a6411f1f1ade7 aa4bf9c81235757291517154d9884b57eaa3bd4b a839f034fca187c7f7ab9a68c9b24a45e7a3ea40 a6699abff7b82cd1d25ec704ee2258a671816b00 a61bfc3b133116463d6a8fc43e0f0d3e781589ee a3c0d50d743a0b6aeff4db45e8ca2c1c708156d5 a3a791a550bc6cedaf8d9f654137b5ff6fa562e7 a23f991ebffff8e534e65495793618310457eed0 9e24c4e231b93142419ac20e58dd71388f7d8ab7 9d7da836b2374f95ea647bf1c33fa26d279ffd5c 9bcb241f07654ecefaf58aca39e44fa0790c4668 9aa3e3b4374693f6ae972494b9589b5b97fe39c5 9a2255123befedc1932f22feed1cc26e245f158a 988fc0d23e6e30c2c46ccec9bbff50b7453b8ba9 97efc80a2e771a20fe00d67d7883323a446c38dc 97e360b73616b8a4acf253eb5979958c65e96e76 96b24cfafc899c611fbf10cd71c2ea164d494498 96171852a5f058519de4c5f26057da4a09a36ce8 95d4b880698accfff08734644600c93f2a104c74 959da0fb174a8e4db238d08a3f5076a2f43c0f25 9468012acf6df7a0e593f41e0da8123f541277df 919c33adb648ce13ee8bd7c11bffbfd836936c00 9084f80c81c320dc696b0e134c34778ff21ef5e0 8ec6dd9509451e038c883b8ddf8f43706b93f901 8e98f5ffeebbf4c2101a2d1f80d3b2f5b2a2b779 8d7ce314adb046f98f1d0abfb8e951884de183da 8af8c027cb0f56b6775115383f4d5bdf010a6352 892f2bd2f7582a6a8a98bc5e8c3876f6ec7a5af0 88ae66f949e2ee06890f4ded031cb5bb1db36c10 84e388acc4c32e2e0aa754902bb0931cbd4cc4ee 829401a6d4061bd41dc07a56005f80a05c46a732 80a973c3da41c6479cc9d7036090adc1264c02a4 7b076fecb16a343cb488d034a2807b9e264616f0 7af4b47c19a433a77c8060e928853464433cd3d6 79ce29609ca633f7ab3fd9cecf147a8ba58ba6a8 78b8c5e115da2838db31f7313eee0fb3b02f3f91 78227f3a159478bd377add728d206675aa3963a6 77e869d2cdb86aea090f14a444e0d1ee39e5cd68 76053ee8c572b2cae49843ff6450fe2b75f0e4ec 717901e4fdbe9a3e69aacec943e3fef9f6fe880e 6fe84c129f76d309032e26aba3c33ba0b64172e8 6f63cfd1239b97fa6e51bda2cbfeb75d7ef8c558 6dacf7e2b65ed65fc5fb132c9fdc483620a29806 6ce0a97038ee51dc579409eb33c3e370f200c047 6acfbb3c2ea50fd90c2d4f75e2f3ac7f6564487e 69e837896d501bd8dc2bc9043421cdd2f75478a9 68bee72acfd5371b1122490bd072228ceb672cef 67aacef9422498071ed7395fdd2cd0538e2c9fee 66aff0c5f1bd49cbf08a427b4764ca6e9ef5785e 66303b6eae62c18556d18012d5e7dead0c7c7b3a 62f8788e8fac62d0faf75c5debdf8375f272609e 613caff760da9b0f5d2f948bf2cd1d6f046cd005 6072dffc994f5ab22a4b7320d9caba21b137b34b 5f080d7290fdf743e1392991124b722a7c6921ff 5e75c057e25c43d0cf003088abc1c3468f917867 5da94b438de46224200d89510121e2ef0f637015 5d430461fa3aabc094e3db9e91b69f703b9e94cb 5a59f2ef0e4b7adbc0780748063d5cee64f8a1a6 57d2f9cc6f11cdffde757fac79fe398192364c17 5788c6ce7f3a9a28e55b137a51b761bd6c4fc40c 56af94995d5336302c86fc492afd3969c4eb33c8 5658a84dbc703aac52e4df4c9912572b322cd62a 54d3d706d65e3d529cf81eadacbbd5b8de4cb43a 54cee4272bbd4bdd774214f76143331f374201ed 4db627cff2af5de1f7ceec1ad1125a4a9dcefdab 4da6fef533b37a12ed1e357df66802de29c1ab5c 4d74de5d8a269eb22bdc2ab3563d7fd4f819d1a9 4b03914c7cbb4bc61e6097846e3cc49bad153140 4975bcdee32d06a04701f578d0a38d7ed7614ed3 44409df06ee5d7a95c18a4823f52e10fa75afaa5 41c37321b305f05c38c61e7423216e4b42f9a4bf 40122f34140303cef9883d73ba69e53ccf39d6c0 3f4ad39c829f9ee919a6304faf439000686f93e2 3dd1b9f3dc6fc02af5919453d22d635c251998a9 3c92dc7f262b8261e25580397038b1704d8c3309 3758f502cdfda460b72b74ecd39c9e509955df6e 3699d1e8d42e18cd40c81daf683fe9feb32e7331 3676e7009f6860667d6aa43810a8161b218dc15d 35c3e82d8c15b8a95aaca126779b61b16a703690 357419f9f553b44d84f05f8426f7123305fc7535 327847bcece765728abb142b482bafdc5442cc58 2eda4e6246f9dcb28b7886d9731a478d818884d7 2d3bc2856c015914f2856331a0315298f3c34b0c 2d0e694de0833b228722228ef7520d553db35ff5 2be1be4d8781d29c9fa49720408769d14864b087 2bbc7301056a3479106c53e0f131cfda6836bd23 2b7aec03db17f9a274bc4a18a8e1f07d5cbe9ff1 2a232f2522da3fe7089d46a634741d29826520cf 29fcae649c1421dccd0bdf253869257d633052ee 29aef3c31e2371e1572b54a10c66b2ecd5d4dc02 289f9fba2266eb0479899f30c54e1f8bff3e3467 287f1058a3272acf3075777ef523d1d9a93b34a3 287dca5b16df751bfb0bcf0c33a01bb384fc7ca5 286c1ad277a337938d6b962d036969eeafe449e6 26ab576a0abf7085ecf6321a311a7b3088ee48ae 23e0ca5808d3d3c3e4d9a3b5a9c012488d0abb28 21d92fb5aa818f9e4c4f17287630c17e47c3cb23 2055f2597dc75bb7ad444ad5a307360d372569e0 1e2e8860d5f7a73f921f6bc4e4247bcc2ed2afa3 1b159fbbb46b796af684b9aa012abac5efbfa64d 12b3b7b9ff68d1cb406f41cb352e8b82a01a7689 125f0459d0ad317da34e2d3301ae460844183fe5 0dd27a3e30b3cbacf337c6ac0e460bded7162415 0daae99f60eb00b2353a5e5194b3d3c01f9bf176 0caff508627beadb48a3c662f0f476e03c085604 0bb88b80294f3f13570b3b1f074b14a9cc7fa260 0a6e4a9bc84ae988f2a3d2d41816cf29dff5f46d 06e0c9440ccd755c2613ace21447841f0fbb4e2e
Black Basta Ransomware FAQs
What is Black Basta Ransomware?
Black Basta is a ransomware strain that came out in early 2022. It’s an evolved version of the Conti, Ryuk, and Hermes families. You can find it heavily advertised in underground cybercrime markets, and it practices double extortion, which means it demands payment for decryption and the non-release of stolen data.
How does Black Basta Ransomware operate?
The Black Basta ransomware group operates by launching hundreds of attacks against their global targets in different sectors. They will release Windows and Linux variants of Black Basta ransomware. They target healthcare institutions, government organizations, financial services, media firms, and educational bodies. They don’t go after entities within the Commonwealth of Independent States. The group’s earnings can range to hundreds of millions of dollars.
What encryption methods does Black Basta use?
Black Basta uses NgINX-based proxies, rotates VPS instances for C2, and uses FTP servers for staging and data storage. They use Telegram and Matrix as their preferred communication platforms.
The group employs secretsdump.py alongside various other commodity keyloggers for credential harvesting and extraction. PowerShell commands and other LOL methods are used for firewall manipulation and traffic tunneling.
For network scanning, Black Basta uses the SoftPerfect network scanner, netscan.exe. In addition, the WMI service is used to enumerate installed security solutions. The ransomware will disable commonly used endpoint security products before encrypting.
How can organizations defend against Black Basta Ransomware?
You can use anti-malware software and other security tools to block known Black Basta variants. Monitor your network traffic. Look for indicators of compromises like unusual network traffic patterns and communications with known command and control centers. Conduct regular security audits and assessments. Educate and train your employees on the best cybersecurity practices, including identifying and reporting Black Basta threats. You must implement a solid backup and recovery plan and have a copy of your data to restore or roll back changes during an attack.
What should victims do if infected by Black Basta Ransomware?
Use SentinelOne Singularity XDR Platform to detect and prevent malicious behaviors and artifacts associated with Black Basta. It can return systems to their original state using its repair or rollback feature.