FunkLocker Ransomware: In-Depth Analysis, Detection, and Mitigation
What Is FunkLocker Ransomware?
FunkLocker is the ransomware associated with the FunkSec hacktivist group. The FunkLocker ransomware-as-a-service (RaaS) operation emerged in late 2024 in parallel with the group’s expanded branding efforts. FunkSec models themselves after the Five Families/BlackForums/SiegedSec/GhostSec communities.

Their targeting and rhetoric suggest anti-Israel, anti-Iran, and anti-United States leanings. Early FunkLocker payloads have pro-Algerial branding tied to the “Ghost Algeria” hacktivist group. There are common threat actors, affiliates in this context, observed within the Algerian hacktivism community and FunkSec.

FunkLocker RaaS openly recruits the public. They use their data leak site (DLS) and social media accounts to name victims and post/leak any stolen data. Their DDoS and defacement victims are included amongst the targets they disclose. In early 2025, FunkSec launched their own forum, along with multiple TOR-based mirrors of their data leak site and marketplace.
What Does FunkLocker Ransomware Target?
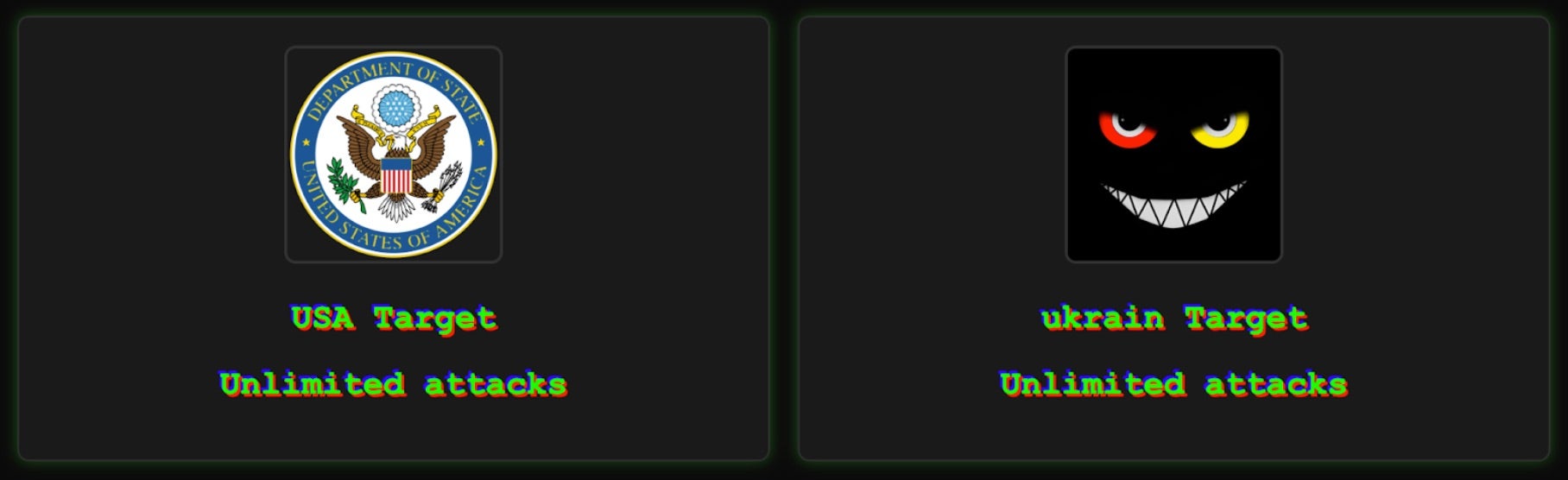
FunkLocker operates as an entry-level RaaS with varying targeting. However, the group does have specific geopolitical leanings and is open about targeting entities in the United States, Iran, and India.

The targets listed on the group’s DLS are largely government entities. The group has also openly announced targeting within Ukraine.
FunkSec also engages in nuisance/availability attacks in the form of hacktivist-style defacements and low-volume distributed-denial-of-service (DDoS) attacks.
How Does FunkLocker Ransomware Work?
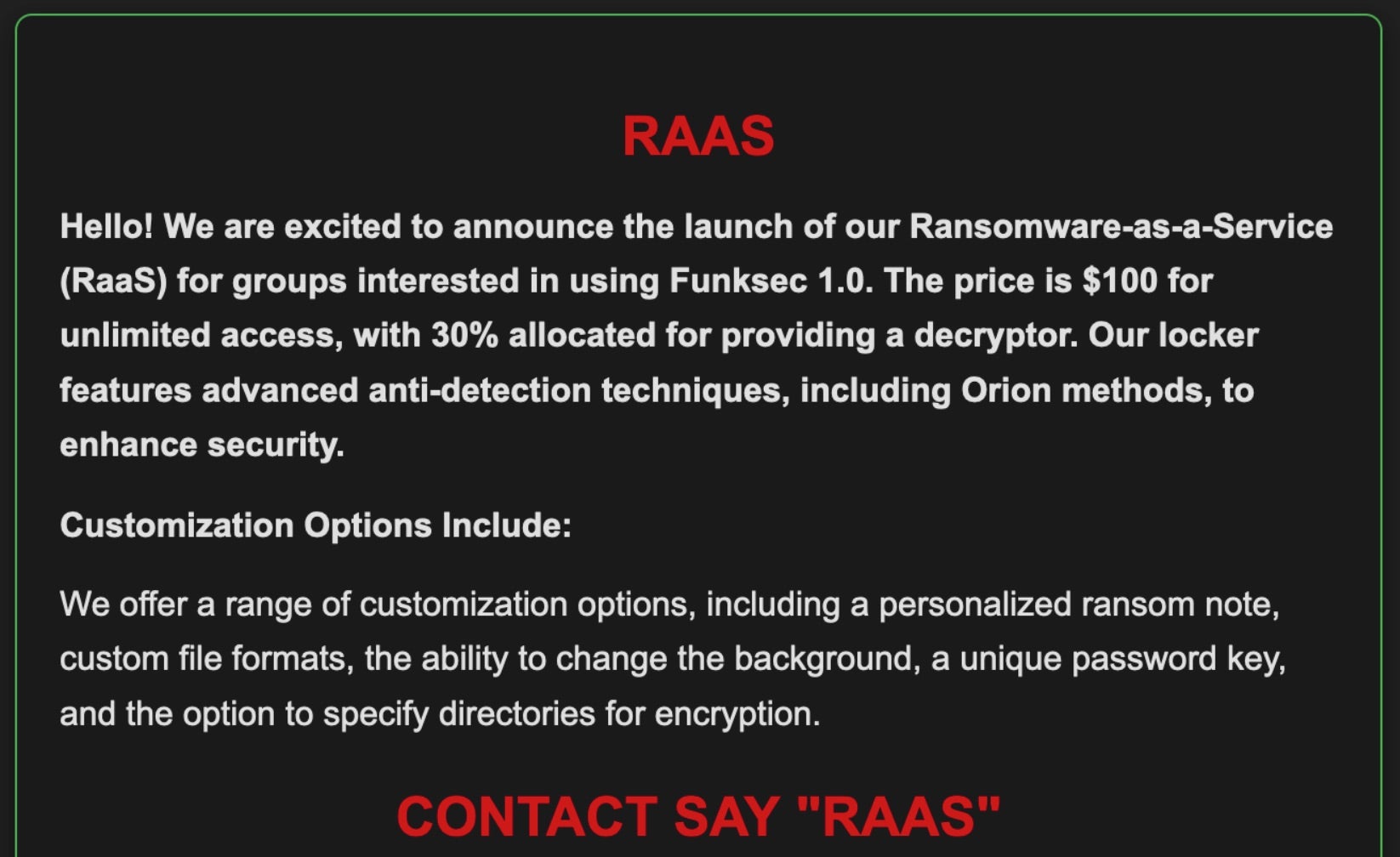
FunkLocker RaaS openly recruits affiliates across their own forums and social media accounts. Currently, FunkLocker is at version 1.5, though the group has started to preview an upcoming release of the 2.0 version. The group offers affiliates the ability to buy into the program at $100.00 USD for lifetime access. This includes a build of the malware, with customization options around the targeted directories for encryption, a modified wallpaper, ransom note contents, and a unique password key. The payloads are written in Rust and currently support Windows only.
When first launched, the ransomware will verify that it has either administrative or elevated privileges. The ransomware will then target the C:\ directory only (files and subdirectories).
File encryption is achieved via a combination of RSA (private key generation) and AES (encryption of file data).
- An RSA-2048 private key is generated via the Rust 0sRng random number generator, along with creation of the corresponding public key.
- A 256-bit AES key is initialized and then used to encrypt the file data. This AES-encrypted file data is then further encrypted using the RSA public key.
Fully encrypted files are given the .funksec extension. Following file encryption, the ransom note is written to disk as readme.txt or a similar variation thereof.
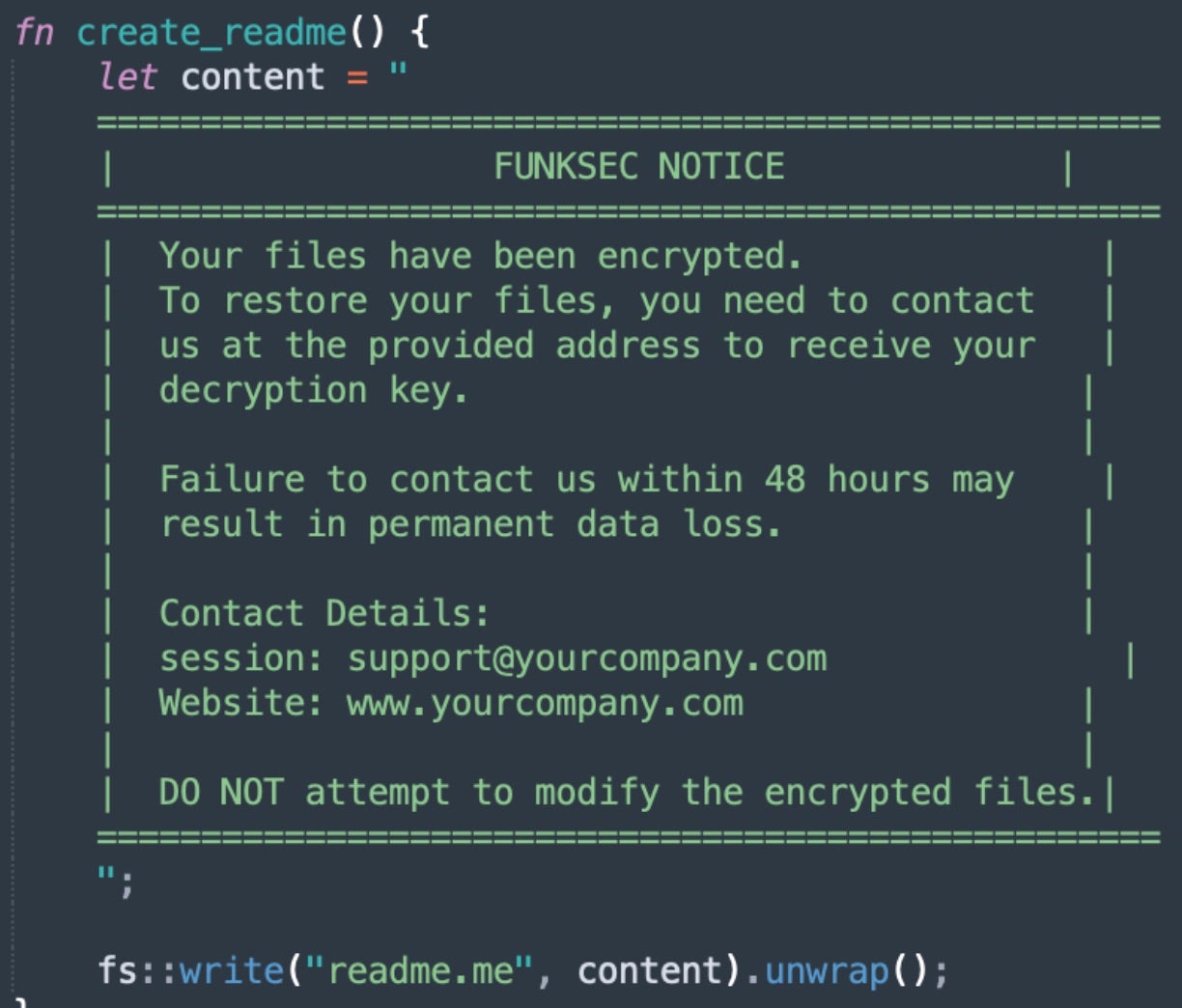
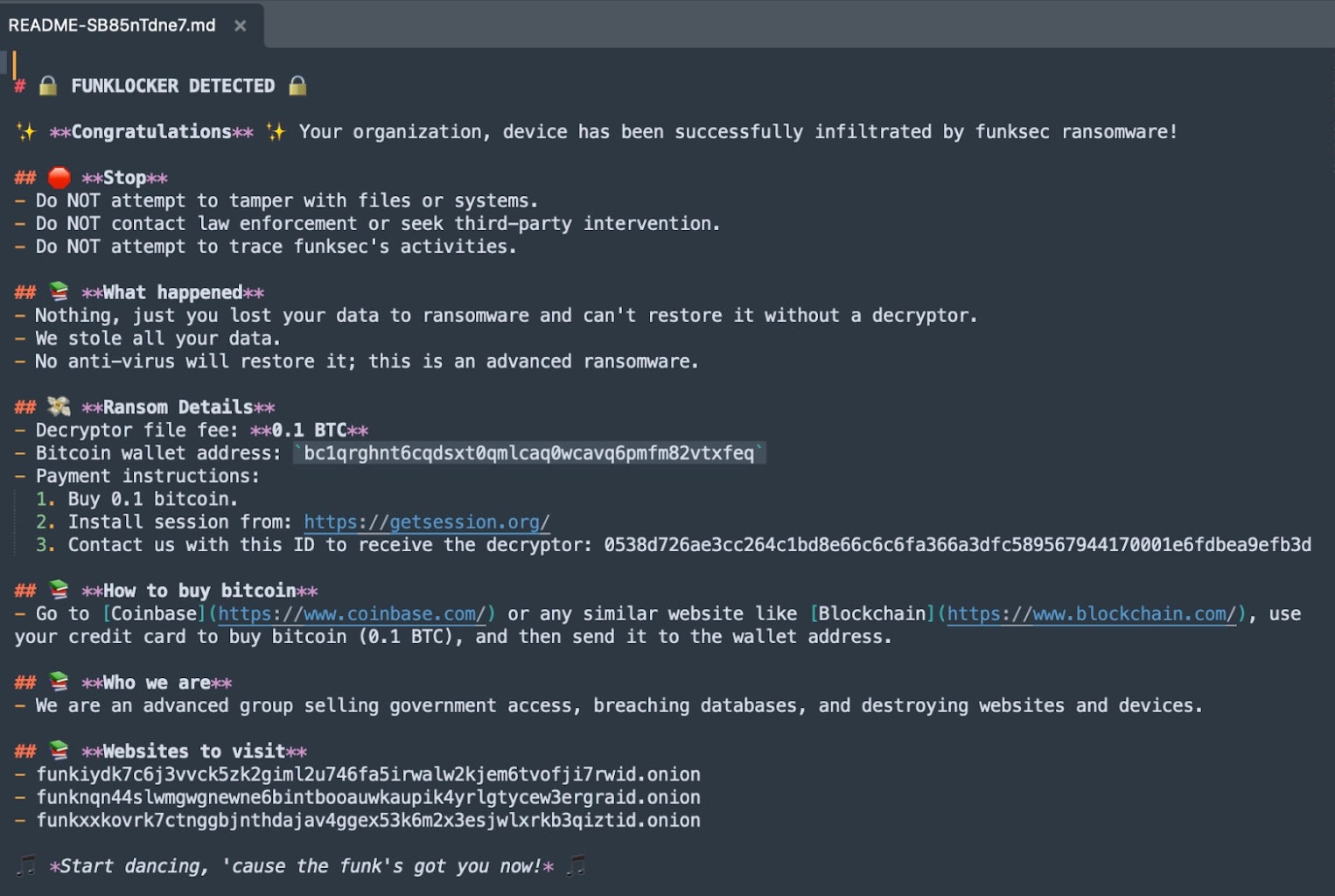
Victims are instructed to communicate with the attacker via supplied Session ID, along with instructions for payment via cryptocurrency.
FunkSec has also distributed trojanized versions of AVAST Premium Security tools. The group posted a free version of this tool for distribution, which in turn drops and executes a copy of their FunkLocker v1.5 ransomware.
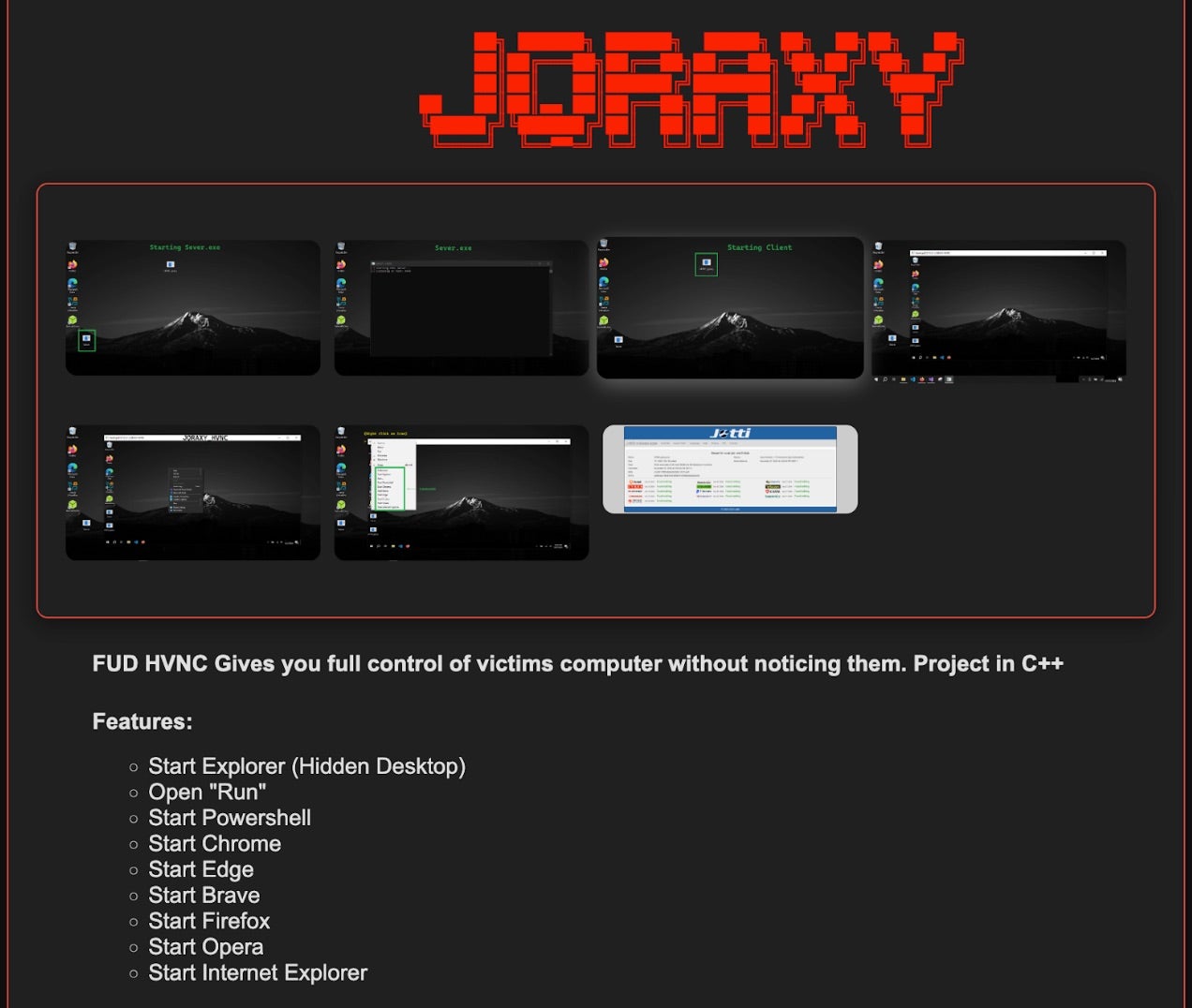
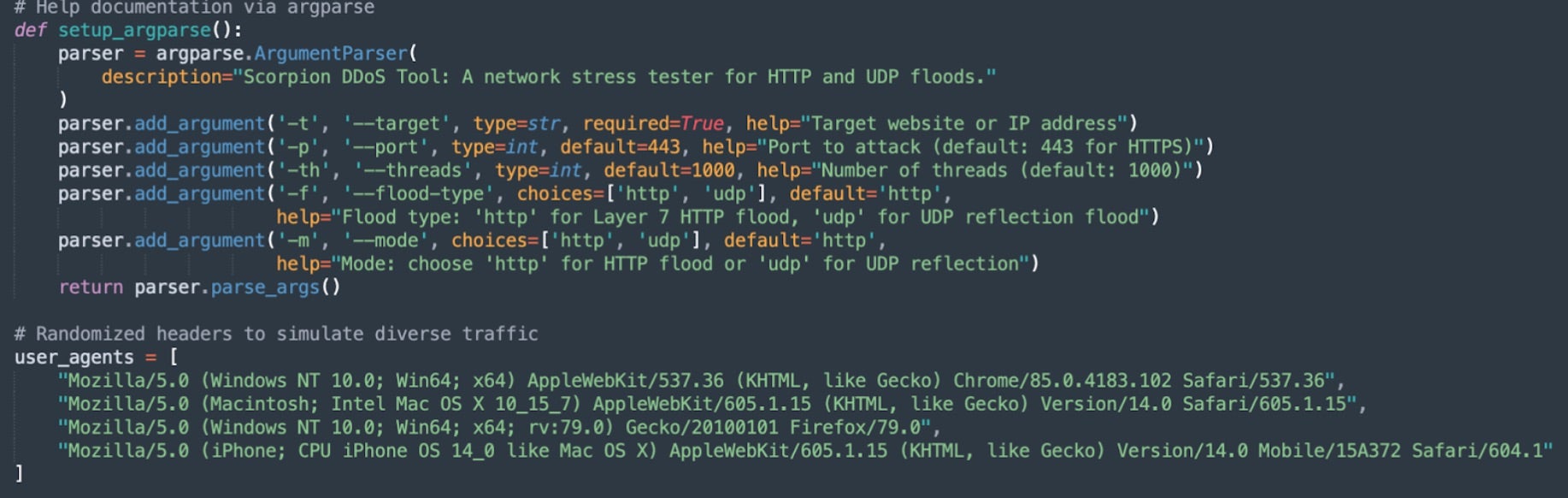
In terms of services additional to ransomware, FunkSec has been observed offering data sorting services and remote access tools such as (e.g. JQRAXY RAT), DDoS tools (e.g. Scorpion), and password scraping/generation tools.
FunkLocker / FunkSec IOCs
File
ff96db4b937971ca2d60e785ff9f706a50e51de4
082258d125f9fb3ea080da1b1fa86bf0a0302cd8
0246696395c8514494435f645cdff034d70d0951
1732202d4d9f130fafc3b9a4cad9995e0eda03d7
4c0c4941a31f9e45b422704a18fdfb44c2c1c4fa
aa8e0f879f1b6a0d83d2657e86cca4b66d8235cf
f78a6b537244b544dc75a07bdbc7eda6ca15699e
2c13d842e788e6c981b2fae65834b1220d55f5a8
b1022afe74471f945b18efed4366598bc6abb192
c6c334c5d3d6942e842c7c413a931a87e3e4b7cf
Network
funksec[.]top
funkzx6xrrgsyqdsl2jvq52zzrvjcizife4eig7bvjeh5okrlsadypid[.]onion
funk4ph7igelwpgadmus4n4moyhh22cib723hllneen7g2qkklml4sqd[.]onion
funkiydk7c6j3vvck5zk2giml2u746fa5irwalw2kjem6tvofji7rwid[.onion
pke2vht5jdeninupk7i2thcfvxegsue6oraswpka35breuj7xxz2erid[.]onion
funknqn44slwmgwgnewne6bintbooauwkaupik4yrlgtycew3ergraid[.]onion
funkxxkovrk7ctnggbjnthdajav4ggex53k6m2x3esjwlxrkb3qiztid[.]onion
7ixfdvqb4eaju5lzj4gg76kwlrxg4ugqpuog5oqkkmgfyn33h527oyyd[.]onion
How to Detect FunkLocker Ransomware
The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to FunkLocker ransomware.
In case you do not have SentinelOne deployed, detecting FunkLocker ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To detect FunkLocker ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate FunkLocker Ransomware
The SentinelOne Singularity XDR Platform can return systems to their original state using either the Quarantine or Repair.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of FunkLocker ransomware attacks:
Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.