Rancoz Ransomware: In-Depth Analysis, Detection, and Mitigation
What Is Rancoz Ransomware?
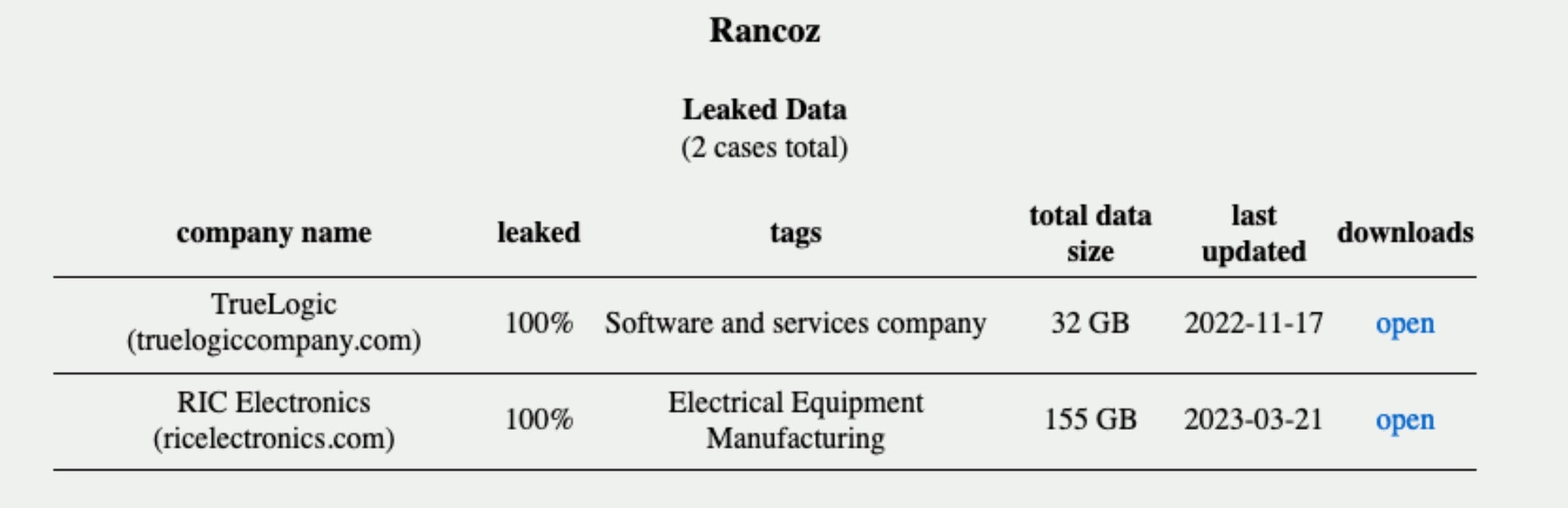
Rancoz ransomware was first observed in-the-wild May of 2023 and operates as a multi-extortion group, hosting a TOR-based website with non-compliant-victim names and associated data. Associated attack campaigns have been tracked across multiple industries and geographies.
What Does Rancoz Ransomware Target?
Rancoz attackers do not discriminate when it comes to victimology outside of targeting large enterprises. There does not appear to be any clear exclusion zones or industries (e.g., medical or educational institutions) for threat actors deploying Rancoz.
How Does Rancoz Ransomware Work?
Rancoz payloads share some code similarities with Vice Society’s custom-branded ransomware strains of the past. That said, there is no firm evidence of a direct relationship between Rancoz and any other specific group or actor at this time. There are, however, visual similarities between Rancoz’s DLS (data leak site) and other known groups. The same can be said for the formatting, structure, and generation of ransom notes. To reiterate, these similarities are surface level and do not denote an immediate relationship between Rancoz and other families or threat actors.
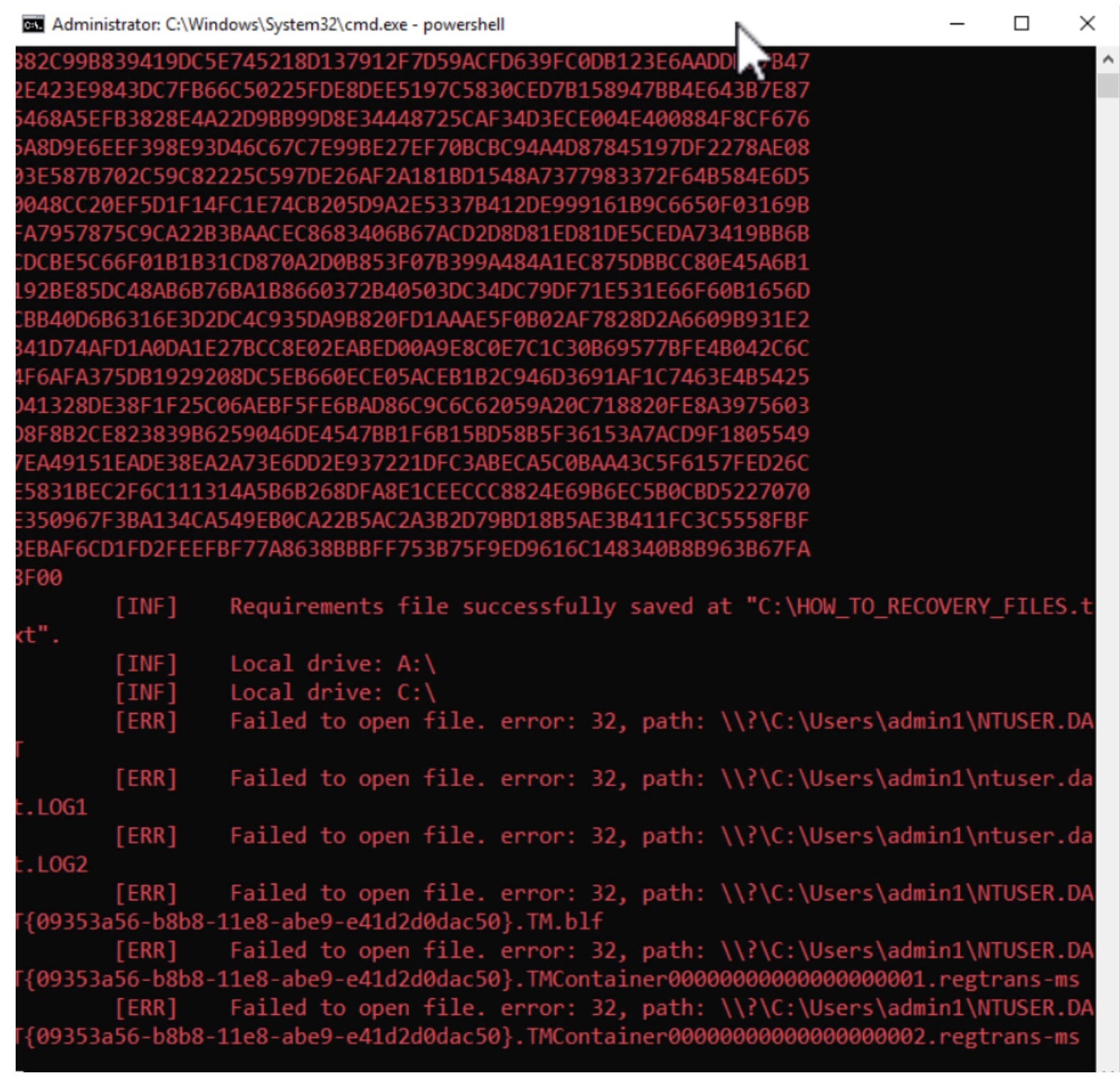
Upon execution, the ransomware will enumerate all local drives and attempt to encrypt all available and applicable file types. Command-line parameters can be used to target the encryption to specific files or folders. Otherwise, the ransomware will attempt to encrypt all local and accessible volumes. Rancoz will also delete VSS (Volume Shadow Copies) via VSSADMIN.EXE and then reconfigure RDP/Terminal Server settings for affected hosts. Encrypted files are noted with the “.rec_rans” file extension.
When launched, Rancoz payloads display a visible command window, displaying current encryption status, and any other output from related routines including volume enumeration, use of command-line parameters, or error messages.
Rancoz payloads accept the following command-line parameters:
- /s – Output syntax/arguments
- /f – Targeted file, aka encrypt specific files (provided via path)
- /d – Targeted directory, aka encrypt specific directories (provided via path)
File encryption is achieved using a combination of NTRUEncrypt (asymmetric) and the ChaChapoly cipher (symmetric). Encryption operations are a multi=thread operation utilizing the CreateThread() API. Subsequent threads operate on blocks of data which are then written back to the affected files. Rancoz ransomware payloads also contain lists of extension and ‘strings’ (folder names) to exclude from the encryption process.
The following commands are observed during the execution of Rancoz ransomware payloads:
Removal of VSS (Volume Shadow Copies)
“C:\Windows\system32\cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet
Disruption of Remote Desktop / TS Connectivity
reg delete “HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default” /va /f
reg delete “HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers” /f
reg add “HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers”
Removal of RDP settings / Log Removalattrib Default.rdp -s -h
del Default.rdp
for /F “tokens=*” %1 in (‘wevtutil.exe el’) DO wevtutil.exe cl “%1”
Rancoz will also replace the desktop background of infected hosts, via modifying the registry to display their dropped “noise.bmp”.
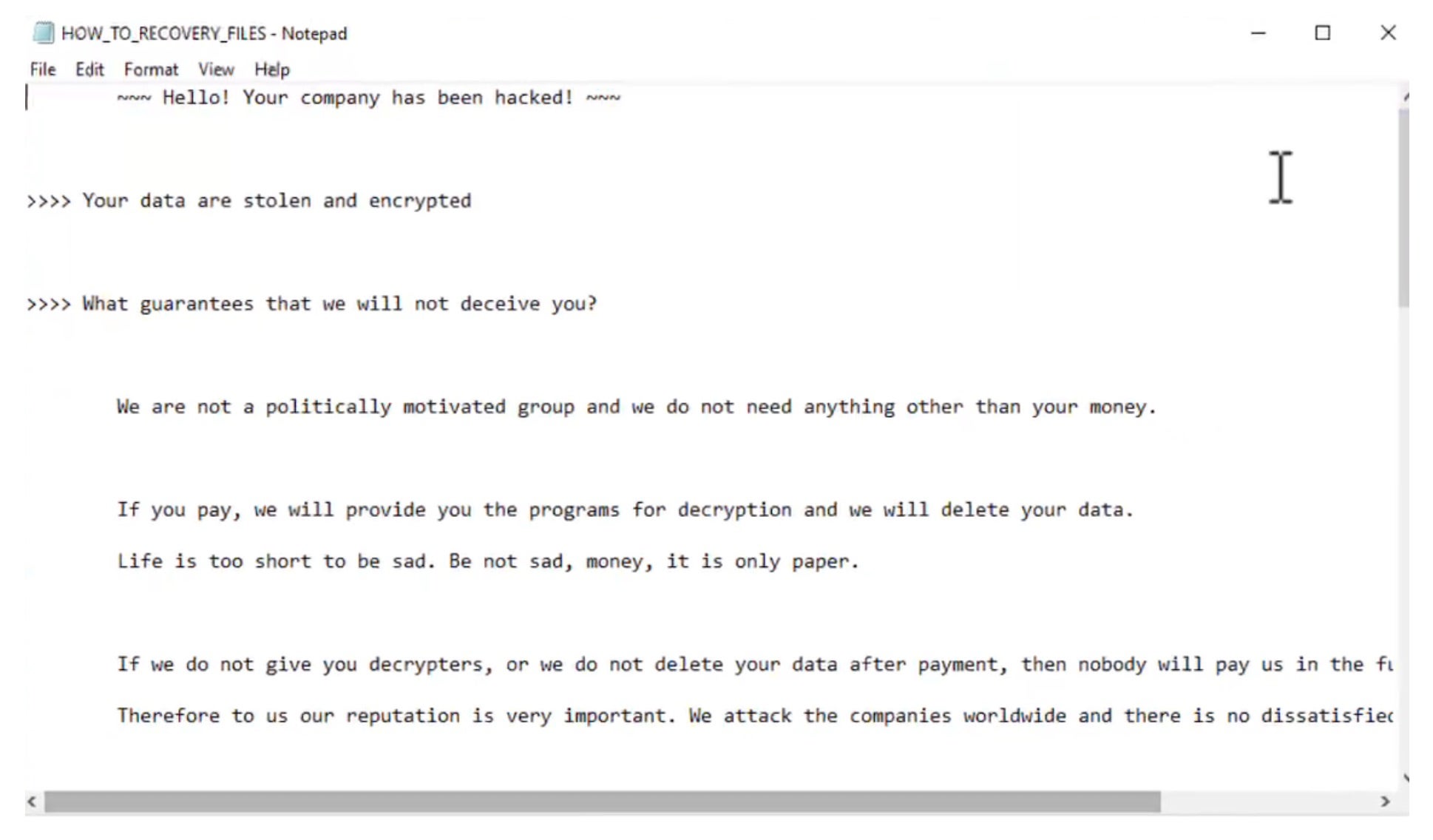
Post-encryption, affected files are noted with the “.rec_ranz” extension. Victims are instructed to contact the attackers via their TOR-based web portal via the dropped ransom note HOW_TO_RECOVERY_FILES.txt.
How to Detect Rancoz Ransomware
The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to Rancoz ransomware.
In case you do not have SentinelOne deployed, detecting Rancoz ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To detect Rancoz ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate Rancoz Ransomware
The SentinelOne Singularity XDR Platform can return systems to their original state using either the Repair or Rollback feature.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of Rancoz ransomware attacks:
Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
Rancoz Ransomware FAQs
What is Rancoz ransomware?
Rancoz is a ransomware strain derived from leaked source code. It emerged early in 2023. The perpetrators stop security services from running prior to encryption. They seek victims via deceptive emails and phony downloads. Following successful infiltration, Rancoz encrypts data and requires a payment to restore it. It can be recognised by its ransom note and the .rancoz file extension for encrypted data can recognise it.
Which sectors and regions have been targeted by Rancoz ransomware?
Rancoz aggressors primarily target sectors like healthcare, education, and finance. Their geographic focus is on North America and Europe. Small enterprises are typical victims, and many national government agencies have also been victimized.
How does Rancoz ransomware encrypt files, and what file extension does it append?
Rancoz uses AES-256 and RSA-2048 encryption to lock files. It scans all connected drives for documents, images, and databases. The ransomware adds the .rancoz extension to encrypted files. It creates encryption keys and sends them to command servers. Encrypted files have changed icons and won’t open with normal programs.
What methods does Rancoz ransomware use to propagate within networks?
After the initial infection, Rancoz moves through network shares. It exploits weak RDP settings and steals credentials to spread laterally. The ransomware scans for other vulnerable machines on the same network and uses tools like PsExec to run itself on other computers. It can be found spreading through domains and workgroups.
What indicators of compromise (IOCs) are associated with Rancoz ransomware?
Rancoz leaves several telltale signs. The ransomware will create registry entries in the Run keys. You can spot unusual connections to command servers in Eastern Europe. They will place ransom notes named “HOW_TO_RECOVER_FILES.txt” in each folder. Process names like “ranc.exe” indicate infection. If you see files suddenly getting the .rancoz extension, you’re infected.
How can organisations detect an ongoing Rancoz ransomware attack?
Rancoz is identifiable by certain behaviors. Track your files and note failures on login attempts and when creating new accounts. Be aware of deactivated security features and antivirus notifications. When Rancoz encrypts data, it creates excessive CPU usage. If breaches are evident in network monitoring, look for activity to unrecognisable IP addresses. Take care of these issues immediately; if any are discovered, sever the connection from the impacted systems immediately.
What steps should be taken immediately after a Rancoz ransomware infection?
Disconnect infected systems from the network right away. Isolating affected machines can stop the spread. Report the incident to law enforcement and your security team. Do not pay the ransom without expert advice. If you have clean backups, prepare them for restoration. Check other systems for compromise signs. Document everything for the investigation.