Ryuk Ransomware: In-Depth Analysis, Detection, and Mitigation
Ryuk ransomware is widely known as perhaps one of the most dangerous types of malware in existence today. Its origins may be debatable, but the threat it poses to private and public sector organizations is not.
Using open-source malware, Ryuk enables threat actors to move laterally across a target’s systems to launch ransomware attacks. Most notably, Ryuk is responsible for disabling computer systems of some of the largest healthcare providers in the world.
Understanding Ryuk ransomware and how it works may help organizations avoid ransomware attacks using this type of malware in the future. However, an extended threat detection and response (XDR) platform such as SentinelOne’s Singularity XDR may provide the most protection, especially for high-value organizations.
What Is Ryuk Ransomware?
Ryuk is a ransomware family typically used in targeted attacks on high-value organizations. This type of malware is designed to lock essential files via encryption in exchange for ransom. It is one of the first ransomware families that can identify and encrypt network drives and resources, and delete shadow copies on endpoints, which means attackers can disable Windows System Restore for users. This can make it nearly impossible for targets to recover from Ryuk attacks without external backups.
The ransomware is typically disseminated by TrickBot, a malware program that allows Ryuk to enter the system undetected as a Trojan horse. Once inside, threat actors can manually navigate Ryuk to conduct reconnaissance on the target’s systems to locate high-value assets. Then, once data is stolen or encrypted, the threat actors typically demand ransom payments in Bitcoin or other cryptocurrencies to avoid being traced.
Who Created Ryuk Ransomware?
Ryuk ransomware was first discovered in August 2018. It was initially believed to be a variant of the Hermes ransomware, which was used in the attack on the South Korean company Shinhan Bank in 2017. However, further analysis revealed that Ryuk was a new, and more advanced, strain of ransomware.
Ryuk ransomware is believed to have been developed by a group of Russian-speaking cybercriminals, known as the Wizard Spider or Grim Spider group. This group is thought to be responsible for several high-profile ransomware attacks, including the attack on the newspaper publisher Tribune in 2019 and the attack on the cloud provider Blackbaud in 2020. In addition, Ryuk is very closely intertwined with Trickbot and its associated crimeware operations. Ryuk remains active and prolific as of 2022.
What Does Ryuk Ransomware Target?
Ryuk ransomware typically targets high-value businesses, government agencies, hospitals, and other organizations that may have sensitive or valuable data, or that may be willing to pay a high ransom to regain access to their systems.
Some of the most widely known Ryuk attacks include the attack on United Health Care conducted by Wizard Spider, the attack on the Onslow Water and Sewer Authority (OWASA) in Florida, and the Tribune Publishing Company which affected the Los Angeles Times.
How Does Ryuk Ransomware Work?
Ryuk ransomware is typically spread through phishing emails, which contain a malicious attachment or link that, when clicked, installs the ransomware on the victim’s device. They may use spoofed sender addresses, or recognizable logos or branding, to trick the victim into thinking that the email is legitimate. They may also use urgent or urgent language, or false promises or threats, to convince the victim to click on the attachment or link.
When clicked, it installs the ransomware on the victim’s device. Once the ransomware is installed, it begins to encrypt the files on the victim’s device, using a strong encryption algorithm.
Ryuk ransomware may also use other malware, such as Trojans or backdoors, to gain access to the victim’s device, or to spread within the network. It may also exploit vulnerabilities in the victim’s system or use other means, such as peer-to-peer networks or drive-by downloads, to spread further.
Ryuk is a later-stage payload, often being dropped by other common (and adjacent) frameworks, such as Cobalt Strike, Emotet, GrimAgent or Trickbot. These same frameworks are typically utilized to move and distribute the ransomware payload across the target environment. However, there are variants of Ryuk with self-spreading (aka worm-like) capabilities.
Publicly disclosed vulnerabilities are used to escalate privilege – CVE-2020-1472 – Microsoft Windows
Ryuk Ransomware Technical Details
Ryuk is a derivative of Hermes Ransomware.
- Encryption: A combination of RSA-2048 and AES-256 (asymmetric and symmetric, respectively).
- Capabilities: Ryuk is capable of encrypting local, logical, drives very rapidly, while also intelligently avoiding any processes or disk locations that may inhibit or otherwise interfere with the encryption process (e.g., Windows folder). The malware also attempts to kill or terminate specific processes to avoid interference (e.g., SQL Server, AV Products).
- Persistence: Ryuk ransomware is designed to be persistent, and to remain active on a victim’s device, even if the device is restarted or rebooted. Various persistence mechanisms have been observed with Ryuk infections, including the modification of HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run (MITRE ATT&CK T1547.001). System recovery is inhibited through destruction of Volume Shadow copies (VSS) though vssadmin.
How to Detect Ryuk Ransomware
The SentinelOne Singularity XDR Platform detects and prevents malicious behaviors and artifacts associated with Ryuk.
If you do not have SentinelOne deployed, here are a few ways you can identify Ryuk ransomware in your network:
Ransom notes or messages
Ryuk ransomware typically displays a ransom note or message on the victim’s computer, informing them of the encryption, and demanding a payment in exchange for the decryption key.
The ransom note may be displayed on the screen, or may be included in a text file on the victim’s device.
File extensions
Ryuk ransomware typically appends a new extension to the encrypted files, such as “.ryk” or “.ryk-encrypted”, to indicate that they have been encrypted.
Processes and services
Ryuk ransomware may also create new processes or services on the victim’s computer, such as “ryuk.exe” or “ryk-encrypted.exe”, which may be visible in the Task Manager or the Services list.
Network traffic
Ryuk ransomware may also generate unusual network traffic, such as outbound connections to known command and control servers, or inbound connections from infected devices.
How to Mitigate Ryuk Ransomware
SentinelOne Singularity XDR Platform prevents Ryuk infections. In case of an infection, The SentinelOne Singularity XDR Platform detects and prevents malicious behaviors and artifacts associated with Ryuk.
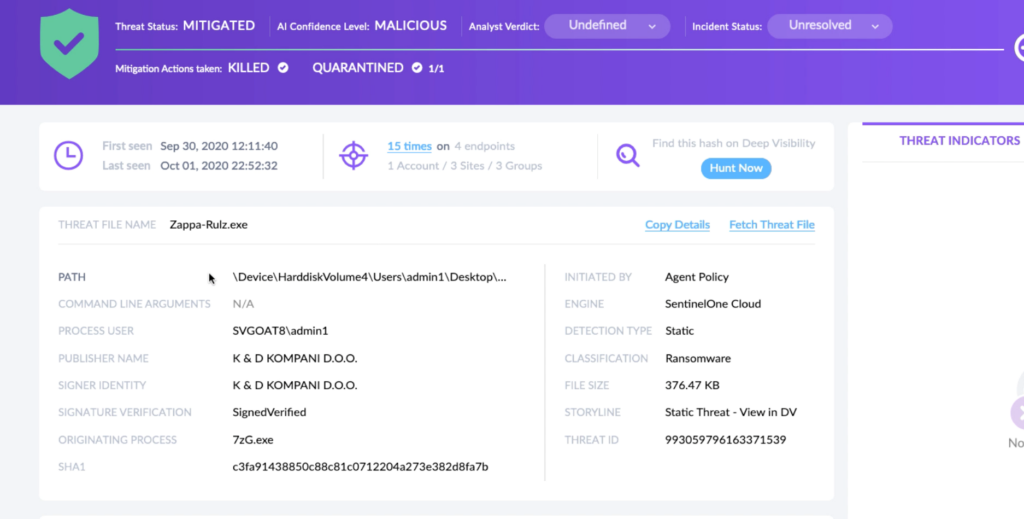
SentinelOne customers are protected from Ryuk without any need to update or take action. In cases where the policy was set to Detect Only and a device became infected, remove the infection by using SentinelOne’s unique rollback capability. As the accompanying video shows, the rollback will revert any malicious impact on the device and restore encrypted files to their original state.
If you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of Ryuk ransomware attacks.
Educate Employees
Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
Implement Strong Passwords
Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
Enable Multi-factor Authentication
Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
Update and Patch Systems
Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement Backup and Disaster Recovery
Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location.
The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
Ryuk Ransomware FAQs
What is Ryuk ransomware?
Ryuk makes one of the highest ransom demands, going up to USD 12.5 billion. It targets governments, academic institutions, healthcare and manufacturing firms, and technology organisations. Ryuk has been linked to the hacker group WIZARD Spider and first appeared between the mid-to-late 2018s.
Ryuk caused a significant infection at Tribune Publishing, which the New York Times reported. It disrupted their printing processes in Florida and San Diego, causing distribution issues. Ryuk was responsible for three out of the year’s 10 most considerable ransom demands. It is also considered a variant of the older Hermes ransomware.
What encryption algorithms does Ryuk ransomware use?
After infecting a system, Ryuk shuts down 180 services and 40 processes. It then encrypts photos, videos, databases, and documents, including all the sensitive data you care about. Ryuk uses AES-256 encryption, and its symmetric encryption keys are further encrypted using asymmetric RSA-4096.
What ransom notes are left behind by Ryuk ransomware?
Hackers will send you a ransom note as RyukReadMe.txt and a UNIQUE_ID_DO_NOT_REMOVE.txt file. You will then receive a screenshot that contains instructions on how to interact with them and pay the ransom.
What file extension is added by Ryuk to encrypted files?
Ryuk appends the .ryuk extension to encrypted files. Some variants use random extensions like .crypt or R4A to complicate identification. To confirm a Ryuk attack, check for ransom notes and system-wide encryption.
What are the indicators of compromise (IOCs) for Ryuk ransomware?
Look for .ryuk files, ransom notes, and suspicious PowerShell commands like vssadmin delete shadows. Ryuk often arrives after a TrickBot or Emotet infection. Network connections to IPs in Russia or Ukraine and abnormal SMB traffic are additional IOCs.
Ryuk is installed through droppers sent via phishing emails. It comes with malware like BazarBackdoor, Trickbot, Zloader, and more. Ryuk can install Cobalt Strike Beacon to communicate with command and control (C2) networks. It can also take advantage of ZeroLogon vulnerability exploits in Windows servers.
How can organisations detect a Ryuk ransomware infection early?
Monitor for TrickBot or Emotet activity, as these often precede Ryuk. Use EDR tools to detect lateral movement via PsExec or WMI. If your security logs show multiple failed RDP login attempts followed by successful access, it could signal Ryuk operators breaching your network.
What security solutions are effective against Ryuk ransomware?
Endpoint security tools are effective in detecting some Ryuk ransomware strains, but not all of them. To stay protected, we recommend using SentinelOne Singularity XDR Platform.
What should victims do immediately after detecting Ryuk ransomware?
Victims should disconnect infected devices and shut down VPNs to prevent the spread. They must preserve logs for forensic analysis and contact incident response teams. If backups are unavailable, consult cybersecurity experts before considering payment. Report the attack to the FBI’s IC3 and update all credentials used on compromised systems.