The macOS user community has, relative to its counterpart on Windows, been markedly slow to recognise the importance of security software and similarly shy of recommending endpoint security to new users. In public forums such as Apple Support Communities, MacRumors and MacWorld, responses to users requesting advice on installing security software typically run along these lines: “macOS is safer than other platforms because there are few credible threats, and the OS has built-in security mechanisms. As such, AV-software is largely a waste of time. The best way to stay safe on a Mac is to follow safe computing practices and use your common-sense”.
It’s a line of reasoning that could be reasonably supported when macOS was both relatively insignificant and comparatively unsophisticated. But if the threats have started to become more credible, and the holes in XProtect and Gatekeeper more visible, just how much safety will “safe computing practices” and “common-sense” really provide? Let’s examine five common pieces of advice given to macOS users on how to practice safe computing in light of the current threatscape.

1. Avoid unsafe websites
There’s no doubt that by far the majority of threats to macOS users come from visiting malicious websites, so advising people to use the internet safely makes good sense, save for the fact that discerning the good from the bad is no easy task for an unprotected user. Popular games platforms like Steam are a prime target for scammers, and it doesn’t take much skill to create a clone of a genuine website that is almost indistinguishable from the real thing. Even IT professionals may fall for tricks like picture-in-picture attacks:
One enterprising security tester…made a visually-perfect spoofing site of Paypal, where even the user gestures that displayed the ephemeral browser UI were intercepted and fake indicators were shown.
On top of that, the increasing use of DNS Changers and router exploits means attackers could take control of your browsing despite your best efforts to avoid unsafe sites.
2. Only download software from trusted sources
Knowing who to trust is essential for any kind of security, but following the advice to stick to mainstream or “trusted” software distributors has become murky at best. Third-party distribution outlets like CNET’s Download.com and Softonic.com that were once considered safe have moved to monetize their own income by bundling potentially unwanted software. MacUpdate.com similarly experimented with paid installs and has also been inadvertently responsible for serving up cryptominers to unsuspecting users. Even Apple’s own App Store, usually held-up as a paragon of safe software distribution, has fallen victim to hosting apps that steal user’s browser history, even from reputable vendors like Trend Micro.
3. Keeping your software up-to-date
Ensuring your software and OS are patched against the latest threats is an essential of safe practice, but updates can bring their own security risks. Apple’s annual update cycle has put pressure on both themselves and third-party developers to constantly reinvent their software with new, compelling features, and that inevitably means less time for thorough security testing. There’s been a few high profile slip-ups as a result: from blank passwords in High Sierra that allowed root access:
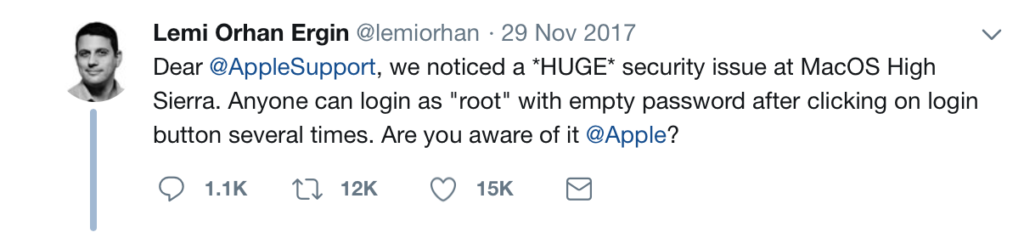
to security bypasses in Mojave. Apple’s refusal to initiate a bug bounty program for macOS does nothing to encourage security researchers and means there’s no telling what other zero-days are lurking out there. Security bugs even in Apple’s hardware were recently discovered only because researchers were hunting bugs for an Intel bug bounty program.
4. Source directly from developers and do your research
If distribution sources can’t be trusted, users are often advised to source directly from developers that they have researched or that are mainstream. It’s true that there’s no substitute for knowledge, and anyone considering adding new software to their computer should vet it like a property owner vet’s a new tenant. The complexity of today’s computing landscape means every new process you let into your environment is gaining access to large parts of your personal world.
The problem here is that ‘do your research’ isn’t just a case of reading a few reviews and sticking with “big name” vendors. The blogosphere is full of fake websites and even the most reputable websites often post sponsored reviews masquerading as independent opinion. Whether you’re actually getting a genuine review or subtle sales promo is often impossible to tell.
And as we saw with Trend Micro and the App Store, a mainstream software developer can breach trust, unwittingly or otherwise, just as easily as any other. It wasn’t that long ago that Dropbox famously used a SQL injection hack to bypass user preferences in earlier versions of macOS. In short, the size or reputation of a company is no guarantee that their software will conform to safe or even best practices.
Finally on this point, mainstream vendors are also often the target of forgery and supply chain attacks. It is precisely because of their ubiquity on the macOS platform that fake Adobe Flash Player installers are the most common form of trojan.
5. Install security software only if you have a specific concern
This is probably the worst piece of advice that we’ve seen regarding security:
“No AV programs are needed or recommended on Mac OS…if you happen to download malware, you can use MalwareBytes to get rid of it”.
This line of thinking amounts to “avoid security software until you have a security problem”. Quite apart from the illogic of advising someone to avoid security software while admitting it would be useful in the event of a security issue, after-the-fact security is no security at all. By the time you realise you have a problem, the damage has already been done, your data exfiltrated or possibly lost forever in a ransomware attack.
How Can SentinelOne Help?
If practicing unprotected “safe computing” isn’t really that safe, what is the argument for avoiding security products? Historically, legacy AV solutions on macOS have been widely criticised for either failing to offer adequate protection and/or for causing system slowdowns. Neither of these issues pertain to a modern behavioural AI solution like SentinelOne. In their most recent report, independent research institute AV-TEST from Germany gave the SentinelOne agent full marks (6/6) in all three categories of Protection, Performance and Usability.
Moreover, SentinelOne’s Next-Generation Endpoint Protection protects against diverse modes of attack, including browser attacks, credentials scraping, fileless malware and more.


