The complexity of today’s cyber threats presents unique challenges for IT administrators and security practitioners. You may know a specific file is malicious, but how did it get there? How did it bypass your security measures? Where is the hole that you need to seal?
Due to the complex nature of today’s cyber risks, it is vital that admins have the tools and standards to make sense of an attack in its entirety. Understanding today’s attack complexity requires a two-fold solution:
- Access to data, including context; and,
- Framework and programs that allow structuring information to reveal the meaningful business impact.
What Are Behavioral Indicators & Why Are They Useful
The information the SentinelOne platform is both unique and content-rich. Most security products provide data based on reputation or running the sample on a remote sandbox, not based on what really happened on the device. While any sensor can provide an uncorrelated IOC stream from endpoints, such unstructured data lacks context and requires a SOC expert to analyze and comprehend the tangled relationships across a vast set of data points. Data for the sake of data is worthless.
With SentinelOne, the heavy lifting is done automatically by our patented Behavioral AI engine, and the full attack story is provided directly from where visibility is best – on the endpoints themselves. SentinelOne’s Behavioral Indicators provide yet another way to understand the nature of a detection, even if it was stopped and did not cause any harm. A few examples of Indicators include:
Read sensitive information from LSASS. MITRE: Credential Access {T1003}
Attempt to evade monitoring using the “Process hollowing” technique. MITRE: Defense Evasion {T1093}

Data is Only Half the Story
Even though Behavioral Indicators solve the problem for the security analyst, they are not enough to provide meaningful understanding to the non-security audience and other stakeholders within your organization. Therefore, the second part of the solution needs to take the Behavioral Indicators and make them accessible and understandable to the broader corporate audience. For this, a security methodology or framework is needed.
We have integrated with the ATT&CK™ knowledge base developed by MITRE, a non-profit organization that operates several Federally Funded Research and Development Centers (FFRDCs). The MITRE ATT&CK™ matrix is an open source tool that provides a comprehensive dataset of attacker techniques and technologies. It aims to describe an adversary’s steps at a high enough level to be applied widely across platforms, but still maintain enough details to be technically useful.
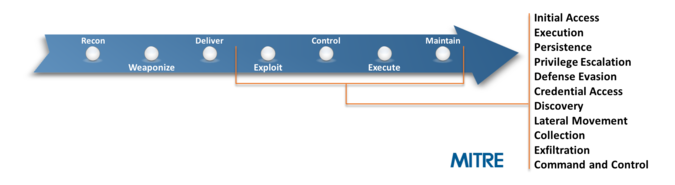
The collaboration between the SentinelOne platform and MITRE ATT&CK™ for Enterprise provides a complete story, incorporating both context and relevance.
When Visibility and Structure Work Together
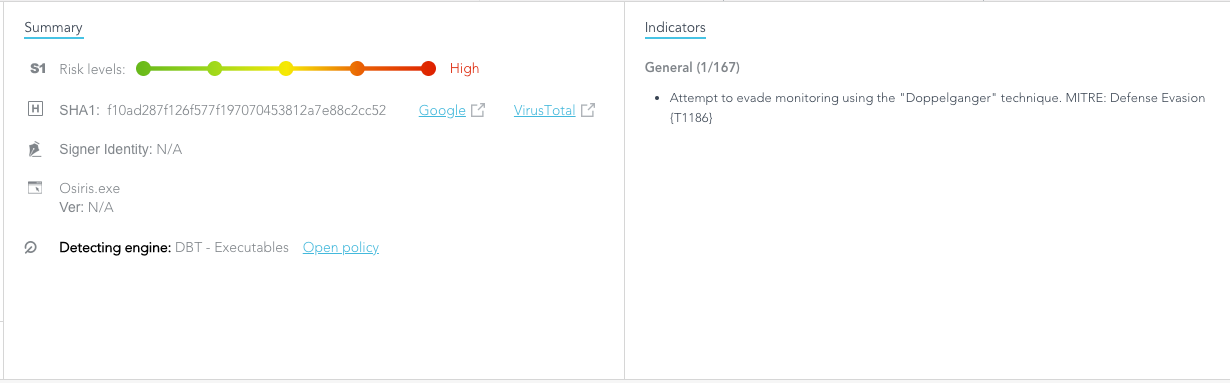
Let’s look at an attempt to evade monitoring using the “Doppelgänging” technique (classed by MITRE as Defense Evasion {T1186}). When a malicious actor attempts to perform an attack such as Osiris on an endpoint protected by SentinelOne, the threat is immediately blocked and the behavioral indicators are revealed in the console:
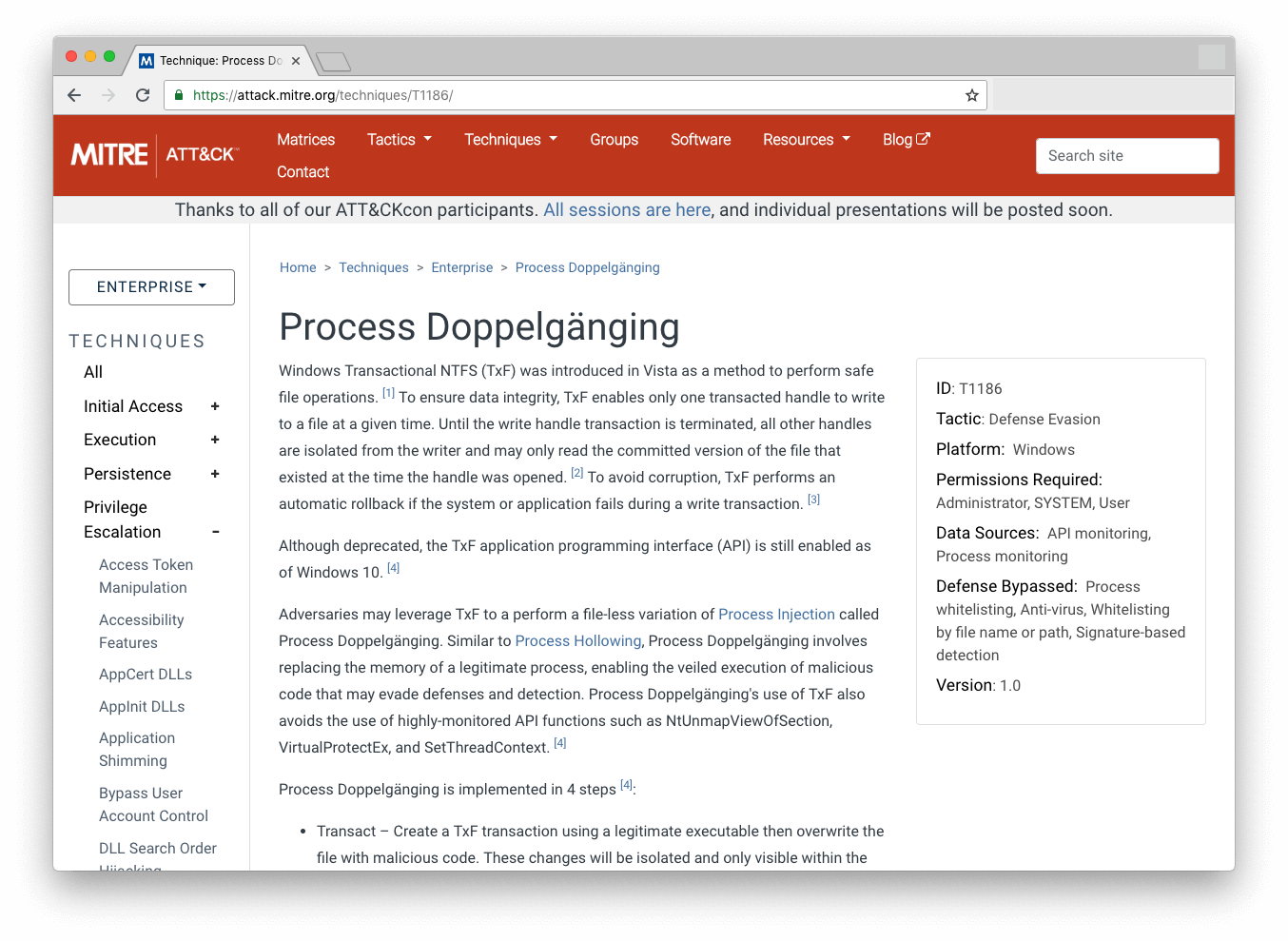
A full description of the technique is provided by MITRE. This includes vital information such as the permissions required, the steps implemented and defenses bypassed:
Demo
Take Aways
There are many security solutions that provide information based on how an alert is seen in a sandbox or a remote VM. By introducing behavioral indicators, we provide the exact behavioral reason for the detection at its true source. These indicators make it easier to understand the exact nature of a threat, also correlated with the ATT&CK™ Matrix for Enterprise.
Behavioral Indicators and MITRE ATT&CK™ for Enterprise Support is publicly available starting in agent version 2.8.