In October 2022, a critical vulnerability was discovered in the SAML authentication feature of the software, which could allow an attacker to bypass authentication, gain unauthorized access, and execute arbitrary code on the affected system. The vulnerability has been assigned as CVE-2022-47966.
SAML Information Flow
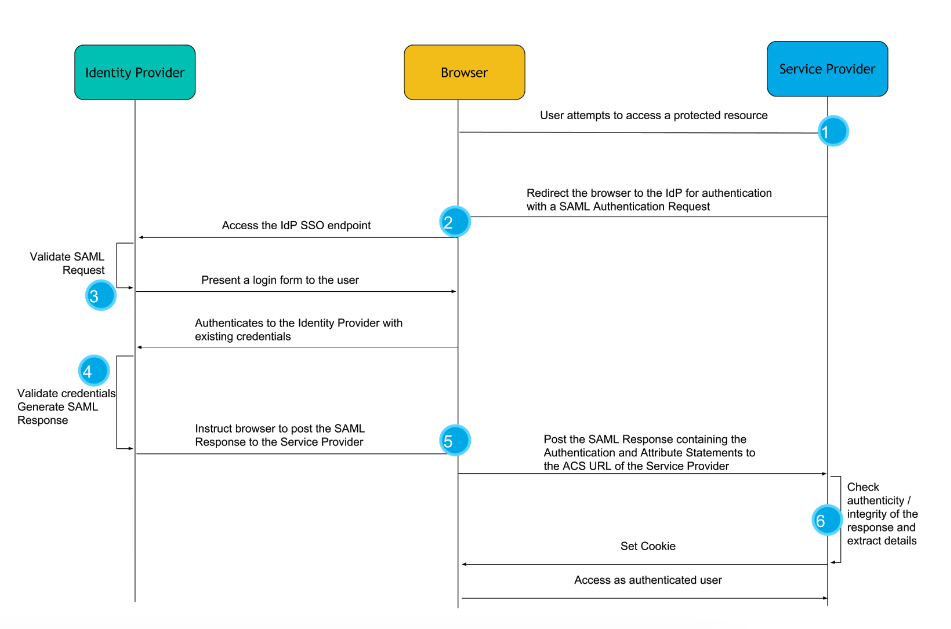
Before we dive into the technical details, let’s discuss what SAML is and how it works. SAML (Security Assertion Markup Language) is an XML-based protocol used for exchanging authentication and authorization data between parties, specifically between an identity provider (IdP) and a service provider (SP).
The SAML process involves three parties: the user, the SP, and the IdP.
First, the user requests access to a protected resource on the SP’s server.
The SP then requests authentication from the IdP, which returns a SAML assertion containing the user’s identity and authorization data.
Finally, the SP then grants access to the user based on the SAML assertion.
About the CVE-2022-47966 vulnerability
CVE-2022-47966 is a critical vulnerability that affects Zoho ManageEngine versions before 14.3 build 14330. The vulnerability has been marked as critical. The CVSS score for this vulnerability is 9.8.
The vulnerability in Zoho ManageEngine’s SAML authentication feature occurs due to improper validation of XML signatures in SAML assertions. Specifically, the vulnerability is due to using an insecure XSLT (Extensible Stylesheet Language Transformations) processor in the signature validation process.
An attacker can exploit this vulnerability by crafting a malicious SAML assertion that includes a specially crafted XSLT stylesheet that triggers the vulnerable XSLT processor, allowing the attacker to execute arbitrary code on the affected system.
Vulnerable Code Snippet:
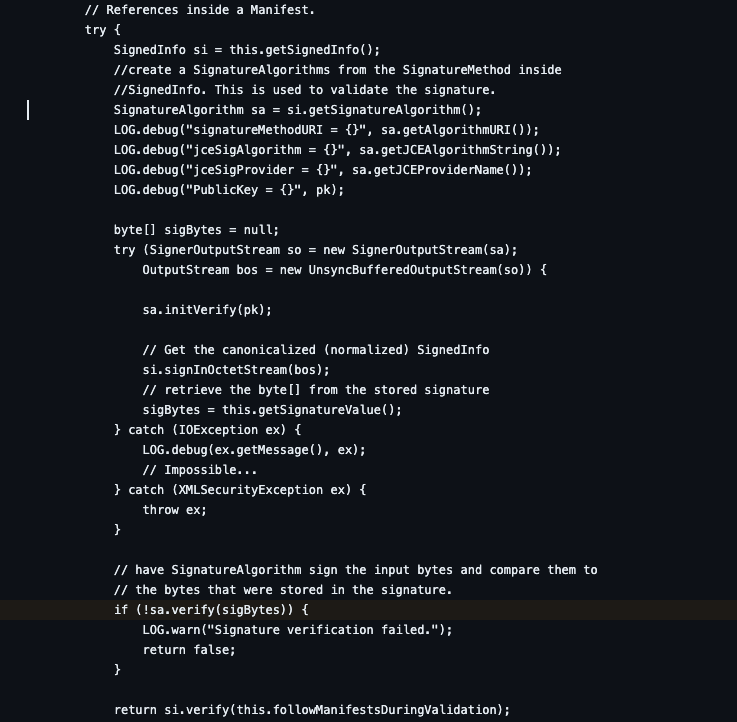
The vulnerability (CVE-2022-47966) exists in the jar file xmlsec version 1.4.1 and earlier versions. In those versions, the signature verification using sa.verify(sigBytes) is performed before the reference validation using si.verify().
An attacker can exploit this by using a specially crafted SAML message with a valid signature but with invalid references. The code will verify the signature and validate the references, which will pass without any error.
Once an attacker successfully exploits the vulnerability, they can execute arbitrary code on the affected server. This can allow them to take control of the server and perform various malicious activities, including stealing sensitive data, installing malware, or causing the server to crash.
Proof-of-Concept (PoC) – CVE-2022-47966
A proof-of-concept (PoC) exploit for CVE-2022-47966 has been publicly released. The PoC uses a malicious SAML response to execute a reverse shell on the affected system. The exploit can be found on GitHub.
Affected versions
CVE-2022-47966 affecting the following ManageEngine products:
- Access Manager Plus
- Active Directory 360
- ADAudit Plus
- ADManager Plus
- ADSelfService Plus
- Analytics Plus
- Application Control Plus
- Asset Explorer
- Browser Security Plus
- Device Control Plus
- Endpoint Central
- Endpoint Central MSP
- Endpoint DLP
- Key Manager Plus
- OS Deployer
- PAM 360
- Password Manager Pro
- Patch Manager Plus
- Remote Access Plus
- Remote Monitoring and Management (RMM)
- ServiceDesk Plus
- ServiceDesk Plus MSP
- SupportCenter Plus
- Vulnerability Manager Plus
CVE-2022-47966 Mitigations
If you are using Zoho ManageEngine, it is important to take immediate action to protect yourself from this vulnerability. The first step is to ensure that you are using a version of the software that is not affected by the vulnerability. If you are using an affected version, upgrade to version 14.3 build 14330, or later as soon as possible.
In addition to upgrading, it is also important to ensure that your server is properly secured. This includes implementing strong passwords, using firewalls to restrict access to the server, and monitoring the server for suspicious activity.
It is also recommended that you regularly patch your server with the latest security updates and scan it for vulnerabilities. By doing so, you can help to reduce the risk of a successful attack.
Conclusion
CVE-2022-47966 is a serious vulnerability that can allow attackers to execute arbitrary code remotely and take control of affected systems. If you are using Zoho ManageEngine, it is important to take immediate action to protect yourself from this vulnerability.
This includes upgrading to the latest software version, patching your server with the latest security updates, and properly securing your server.


