In February 2023, Fortra notified users about a zero-day remote code vulnerability in the GoAnywhere MFT. The vendor provided an immediate response with mitigations and indicators of compromise. However, a week later, they released a patch.
It is claimed that over 1,000 instances of GoAnywhere are accessible through the internet. However, in order to exploit them, one needs to have access to the admin console of the application.
About the CVE-2023-0669 vulnerability
CVE-2023-0669 is related to a pre-authentication command injection in GoAnywhere MFT, affecting version 7.1.1 and its earlier versions. If the vulnerability is successfully exploited, attackers can remotely execute code on vulnerable instances of GoAnywhere MFT.
The vulnerability has been marked as High. The CVSS score for this vulnerability is 7.2.
The version affected by the vulnerability is the License Response Servlet and the exact code block impacted is unknown.
The vulnerability arises due to the manipulation of an unknown input, which causes a deserialization vulnerability. This indicates that the application is deserializing untrusted data without properly confirming that the resulting data is valid. As a result, confidentiality and integrity are impacted.
What is GoAnywhere MFT?
GoAnywhere MFT is a secure file transfer solution that enables organizations to securely exchange files and data between internal systems, business partners, and cloud services. GoAnywhere MFT is designed to simplify the transfer of data, automate file transfers, and provide detailed audit trails of all file transfer activities.
GoAnywhere MFT uses a licensing system that is designed to prevent unauthorized use of the product. The licensing system uses a custom encryption algorithm to encrypt the license file. The encrypted license file is then sent to GoAnywhere MFT, where it is decrypted and verified.
What is insecure deserialization?
Insecure deserialization is a well-known vulnerability that has been exploited in a wide range of applications. It is a vulnerability that arises when an application deserializes an untrusted or malicious data stream. This data stream may contain data that can exploit the deserialization process and cause arbitrary code execution.
Insecure deserialization vulnerability in GoAnywhere MFT
GoAnywhere MFT is vulnerable to an insecure deserialization vulnerability that allows an attacker to execute arbitrary code on the server.
The vulnerability is caused by the way GoAnywhere MFT handles serialized objects. In particular, the com.linoma.license.gen2.BundleWorker.unbundle(String, KeyConfig) method is vulnerable to this attack.
Let’s look at the vulnerable code snippet:
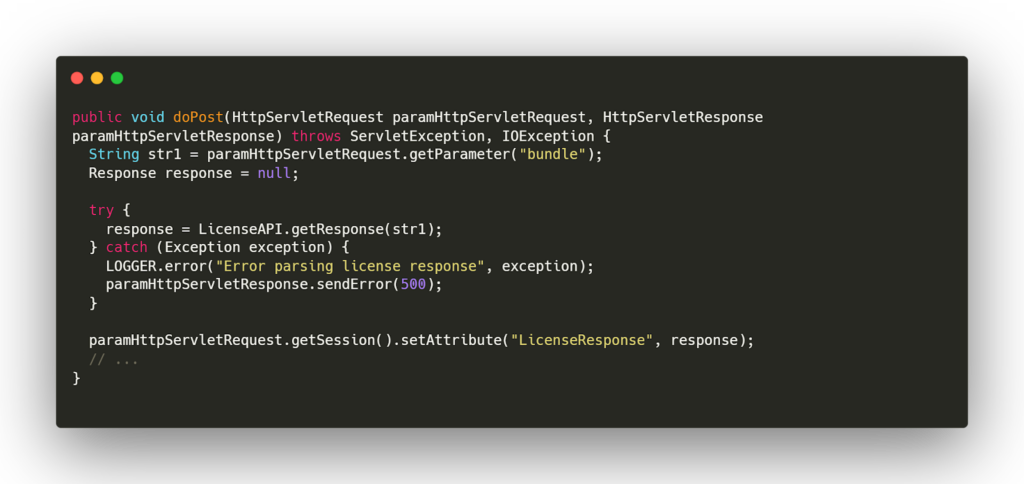
This code snippet is from a Java servlet called `LicenseResponseServlet` that processes HTTP POST requests sent to a server. The servlet receives a parameter called “bundle” from the request, which is then passed as an argument to the `LicenseAPI.getResponse()` method. The getResponse() method returns a Response object, which is stored in the response variable.
However, the `LicenseAPI.getResponse()` method does not properly validate the “bundle” parameter. As a result, an attacker can pass in a specially crafted “bundle” parameter that can cause the server to return an arbitrary file, including sensitive files that should not be accessible to the public.
This vulnerability can be exploited by an attacker to gain unauthorized access to sensitive files and data on the server.
Affected versions of the vulnerability
Version 7.1.1 and earlier are impacted by CVE-2023-0669. Users, especially those with an admin portal exposed to the internet, have been advised to install the patch quickly.
Additionally, users are encouraged to review log files for any evidence of a system being targeted through the exploitation of the zero-day vulnerability. If the logs show signs of compromise, users should inspect their installation for any unusual administrator users.
How to fix the CVE-2023-0669 – GoAnywhere MFT
The attack vector of this exploit requires access to the administrative console of the application, which in most cases is accessible only from within a private company network, through VPN, or by allow-listed IP addresses (when running in cloud environments, such as Azure or AWS).
To find out how many GoAnywhere instances are publicly accessible on the internet, We ran a Shodan search and found 100 publicly available admin pages on port 8000.
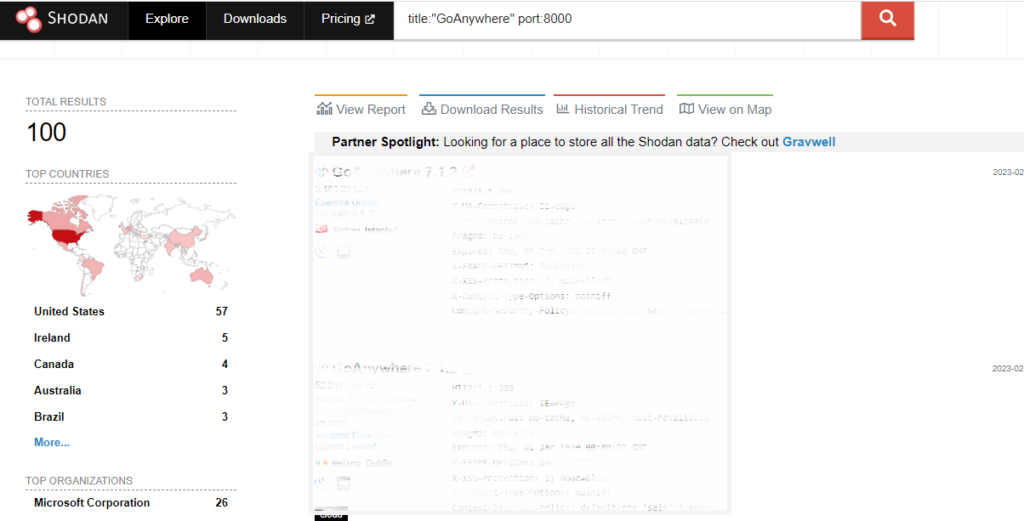
If the administrative console is exposed to the public internet, it is highly recommended to partner with our customer support team to put in place appropriate access controls to limit trusted sources.
Fortra released a patch on February 13, 2023, with version 7.1.2, specifically for customers with an admin portal accessible through the internet. GoAnywhere users have been notified that the patch is now available, and it is recommended that they promptly install GoAnywhere MFT 7.1.2.
To fix this vulnerability, GoAnywhere MFT has released a mitigation configuration.
The first step is to review all administrator users, looking for anything suspicious such as unrecognized usernames or accounts created by ‘system’ when you would not have been working with the platform.
If there are admin accounts created by the ‘system’ that aren’t recognized, further investigation is required.
The second step is to apply the mitigation configuration by editing the file [install_dir]/adminroot/WEB-INF/web.xml on the file system where GoAnywhere MFT is installed.
If GoAnywhere MFT is clustered, this change must happen on every instance node in the cluster.
Closure
Insecure deserialization is a serious vulnerability that can lead to remote code execution and other critical security issues.
To mitigate the risk of Insecure deserialization, it is important to sanitize and validate all input data, especially when it comes from untrusted sources. In addition, it is recommended to use a secure deserialization framework that can protect against Insecure deserialization attacks.
In conclusion, CVE-2023-0669 has been classified as high with a CVSS score of 7.2, and it affects version 7.1.1 and earlier of GoAnywhere. As such, it is crucial for users using GoAnywhere MFT to apply the latest security patches and updates as soon as possible to mitigate the risk of exploitation. Fortra has released a fix to mitigate the vulnerability and urged users to install GoAnywhere MFT 7.1.2 promptly.


