Twitter, it seems fair to say, is going through some turbulent times, and whatever else people might say about the microblogging social platform, there’s no doubt that it’s a major source of information exchange in the cybersecurity world. From infosec news to threat actor IoCs, open source PoCs, conference announcements, and OSINT intelligence – not to mention plenty of entertainment and pet pics – Twitter has long been the social media platform of choice for the cybersecurity world.
The last two weeks, however, have seen massive interest in a rival platform, Mastodon. Many in infosec have said they are moving to Mastodon exclusively, others are using Mastodon as well as Twitter, while thousands of others wait and wonder what this fragmentation might look like in the weeks and months ahead, unsure of how to get started with this alternative social media platform or whether it will work for them.
In this post, we provide an essential guide to getting up and running with Mastodon, discuss how it differs from Twitter, and how to navigate some of its more challenging aspects. We’ll explain how to find and hook up with the rest of the infosec community, including some of our favorite cybersecurity Twitter stars.

What is Mastodon?
Although most people have only just become aware of it, Mastodon is a social media sharing platform, much like Twitter, that has been around since 2016. Starting out as a Patreon project, it was launched in part to help combat some of the problems facing Twitter users, in particular privacy and harassment issues.
The central idea behind Mastodon is that smaller communities can better self-regulate than larger ones, and Mastodon itself is a collection or “federation” of multiple small communities, each on its own server, or ‘instance’.
There is no central body or organization – individuals own the servers, and users can choose and move between servers as they wish. Some servers may block feeds from other servers (e.g., porn sites, extremist views), but most will subscribe to the “federated” feed. This ‘federation’ of servers means users have two distinct timelines: a local one from users on the same instance and a federated one from users across (what Mastodon calls) ‘the fediverse’.
Users who don’t like the feed they’re getting are free to move to another instance. It’s also possible to join multiple instances with the same user name and email address, a ‘feature’ that has both pros and cons that we’ll discuss below.
How to Join Mastodon
With that in mind, the first thing new users need to do when joining Mastodon is to choose an ‘instance’ to join. Start at the joinmastodon page. Alternatively, if you know the address of the instance you want to join, you can go directly to its home page. For cybersecurity, ioc.exchange and infosec.exchange appear to be the most popular.
Aside from that, it’s the usual sign up and verify routine.
After creating an account, visit the Settings page to configure various preferences, set up 2FA for account security and enable tweetdeck-like panels for viewing multiple columns.
Differences Between Mastodon and Twitter
There’s a familiar Twitter-like feel to Mastodon, but there’s some important differences to be aware of, too.
First, there is no identity verification, meaning anyone can impersonate anyone else. This is compounded by the fact that user names are only unique to an instance, so there could be as many accounts with the same username as there are instances in the entire fediverse. That means it’s both easy to impersonate someone else and difficult to prevent someone impersonating you or a business. “Squatting” names is practically impossible, since anybody could start up their own instance and add it to the fediverse.
Just as with Twitter, users can “like” each other’s posts, but on Mastodon, liking a post does not result in boosting the post so that it is seen by more users. On Mastodon, the ‘boost’ feature serves that purpose and is more akin to Twitter’s “retweet”.
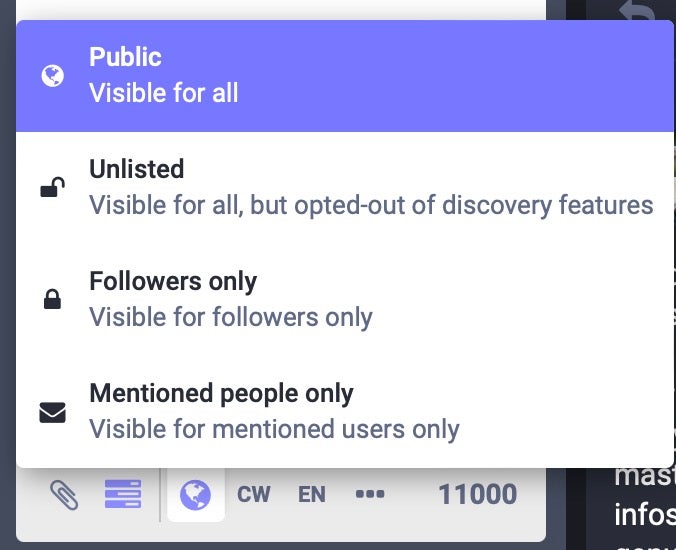
Some other useful features are that each post can be restricted to Mentioned people only, followers only, visible for all but opted-out of discovery features, or public.
Further options include an optional ‘content warning’ and posting only to the local instance.
Those are all plusses, but beware a couple of privacy concerns pointed out by Mike Masnick on Mastodon and re-tweeted by Marcus Hutchins on Twitter: DMs are posts that are set to only be visible to the people messaged. If you mention someone’s full handle in a DM, it adds them to the conversation, just like tagging someone in a tweet does. DMs are also visible to server owners and admins, so don’t assume any kind of privacy here (the same is true of Twitter, of course).
On Mastodon, mentioning someone in a DM adds them to the conversation the same way mentioning them in a thread would. That has got to have led to some awkward experiences 🤣 pic.twitter.com/nLJVFzFdLe
— [email protected] (@MalwareTechBlog) November 7, 2022
Finding Your Twitter Users on Mastodon
For most new users of Mastodon, the tricky part is curating that feed so that you’re getting the content that’s most relevant to you. Joining the right instance helps a lot – remember that the ‘local’ feeds is from those on the same instance, so choosing an instance where a large number of people have the same interests is key. Aside from that, the next most important step is to populate your lists of follows.
For Twitter users that follow a large number of other Twitter accounts, it might seem daunting trying to replicate that on a completely different social media platform. Fortunately, there’s a tool to help with that. Here’s how to use it.
Navigate to fedfinder.glitch.me, and click the “Authorize” button in the “Find fediverse handles of Twitter contacts” box. After authorizing access to your Twitter account, in the next page, click the ‘Scan followings’ and ‘Scan followers’ buttons and wait while the lists are populated.
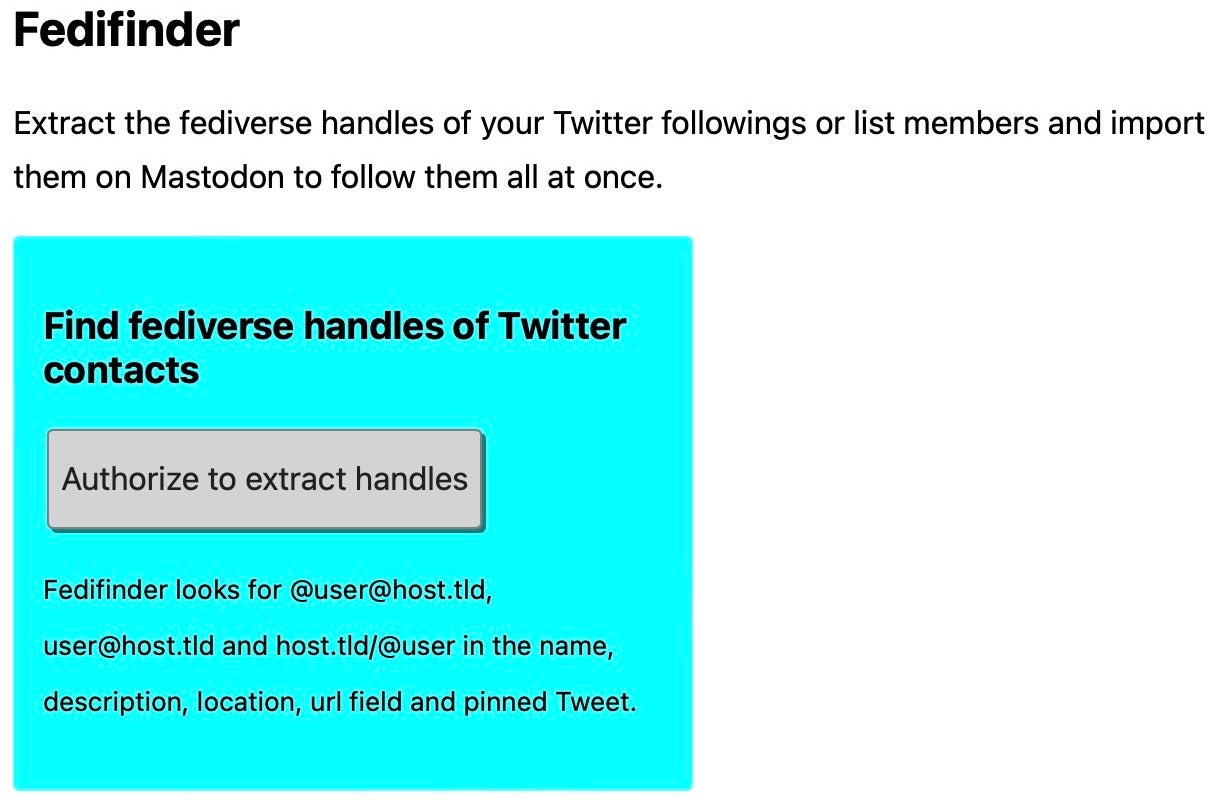
From this point there are two choices. Option one is to scroll down the list and manually choose which accounts to follow by clicking the button for each account.

Option 2 is the more efficient for anything but a few accounts: scroll to the bottom of the list and export all the accounts as a .csv file.
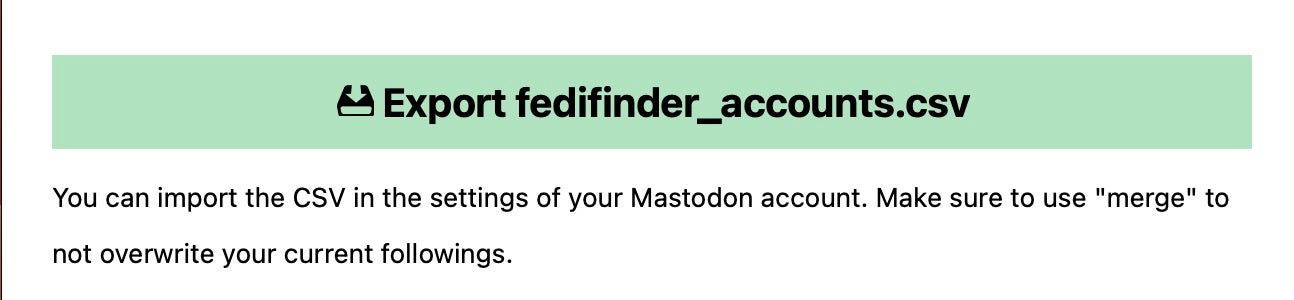
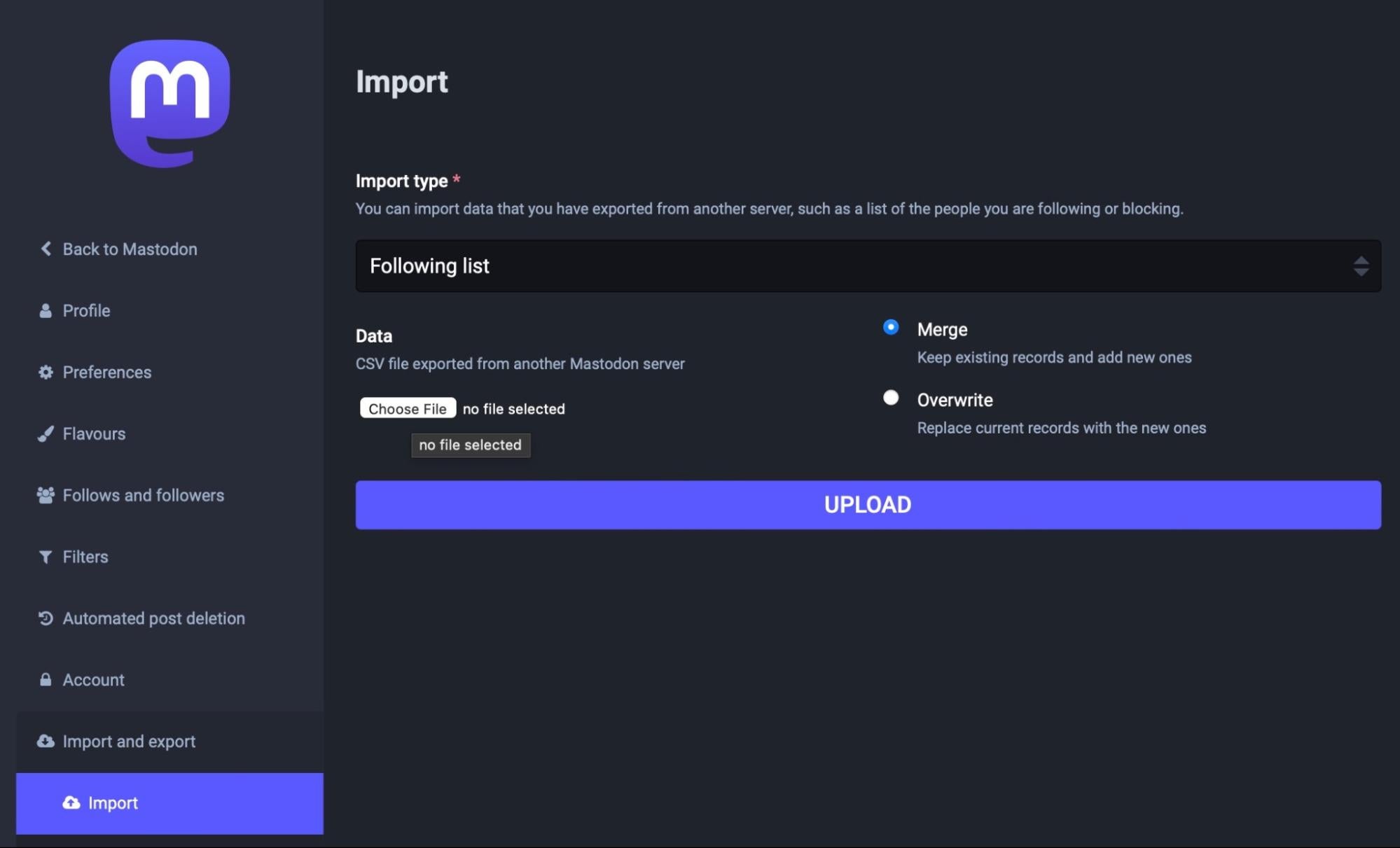
To import the list in Mastodon, go to the Settings page and choose ‘Import’ in the sidebar. Click ‘Choose File’ under “Data” and then Upload the .csv file from your local drive.
Top Twitter Cybersecurity Accounts on Mastodon
Another good way to find cybersecurity and infosec accounts on Mastodon is to look at the followers of some of those that you imported from Twitter or those of some of the most popular cybersecurity-related accounts that have already jumped from Twitter.
Unsurprisingly, you’ll find that many of your favorite Infosec Tweeters and re-tweeters are already on Mastodon. Those that have made the jump include many from our list of 22 top Twitter accounts.
| Mastodon | |
| @campuscodi | Catalin Cimpanu | mastodon.social/@campuscodi |
| @gcluley | Graham Cluley | mastodon.green/@gcluley |
| @GossiTheDog | Kevin Beaumont | nfosec.exchange/@gossithedog |
| @hacks4pancakes | Lesley Carhart | infosec.exchange/@hacks4pancakes |
| @hostilespectrum | JD Work | infosec.exchange/@hacks4pancakes |
| @JohnHultquist | John Hultquist | infosec.exchange/@Johnhultquist |
| @juanandres_gs | J. A. Guerrero-Saade | infosec.exchange/@jags |
| @k8em0 | Katie Moussouris | infosec.exchange/@k8em0 |
| @KimZetter | Kim Zetter | infosec.exchange/@kimzetter |
| @likethecoins | Katie Nickels | infosec.exchange/@likethecoins |
| @MalwareTechBlog | Marcus Hutchins | infosec.exchange/@malwaretech |
| @malwareunicorn | infosec.exchange/@malwareunicorn |
| @philofishal | Phil Stokes | infosec.exchange/@philofishal |
| @RidT | Thomas Rid | infosec.exchange/@ridt |
| @theJoshMeister | Josh Long | infosec.exchange/@theJoshMeister |
| @TomHegel | Tom Hegel | infosec.exchange/@hegel |
| @mRr3b00t | Daniel Card | infosec.exchange/@UK_Daniel_Card |
| @milenkowski | Aleksandar Milenkowski | infosec.exchange/@milenkowski |
| @DAlperovitch | Dmitri Alperovitch | mas.to/@dmitri |
| @SwiftOnSecurity | SwiftOnSecurity | infosec.exchange/@SwiftOnSecurity |
| @ryanaraine | Ryan Naraine | infosec.exchange/@ryanaraine |
| @SentinelOne | infosec.exchange/@sentinelone |
Conclusion
Whether Mastodon serves to replace or only supplement Twitter, there’s certainly advantages to be had in the platform’s ad-free, decentralized structure, as well as some challenges for both new users and servers. The sudden and extra load over the last few weeks has caused at least one instance to announce it’s shutting its doors, but therein also lies the beauty of the open-source “fediverse” – anyone can set up another server and join the platform, and users can easily migrate their data from one server to another, or occupy multiple servers simultaneously.
Twitter’s recent problems led users to look for an alternative, and Mastodon looks to have answered that call. Whether Twitter will get its house in order and tempt those users back remains to be seen; in the meantime, there’s lots of infosec content to enjoy and explore on Mastodon.


