In a study prepared for SentinelOne, the researchers have examined a selection of 76 ransomware splash screens collected from a variety of sources. These splash screens were analyzed according to surface information, including aspects of visual appearance, the use of language, cultural icons, payment and payment types. The results from the current study showed that whilst there was a wide variation in the construction of ransomware splash screens, there was a good degree of commonality, particularly in terms of the structure and use of key aspects of social engineering used to elicit payment from the victims. The research was conducted by Dr. Lee Hadlington and De Montfort University.
On Social Media, a Picture is Worth a Thousand Lies
The concept of social engineering is influenced by an attacker to obtain sensitive information. In the case of ransomware, social engineering techniques are also seen as a mechanism to leverage payment from victims.
There are 3 goals for the ransomware splash screens:
- Scarcity: People find objects or opportunities more attractive if they are rare, scarce or hard to obtain. Scarcity is often matched with the use of urgency, usually linked to a time-critical offer which means people are quick to react and will make fundamental errors in decision-making.
- Authority: individuals are more willing to respond to requests, or follow directions, from someone they view as being in authority. This is usually irrespective of whether the individual in question holds authority – if we believe they do, we will follow their instructions. An example of this is a legal authority, a principle that is based on the individual being a member of law enforcement or a government body.
- Liking: this is a straightforward concept and details the fact that if you get someone to like you, they will likely comply with your requests. Examples of this in this study include the use of humor as well as a conversational tone in the ransomware splash screens.
How to Get Bitcoins?
Many of the splash screens also provided clear instructions on how victims could obtain Bitcoins as well as included links to local sites where they could be purchased, as Bitcoin (BTC) was the attackers preferred mechanism for payment, with 75% of ransomware splash screens asking for payment in BTC. One example even included a short video tutorial showing how to buy BTCs, demonstrating the importance of making sure the ‘customer’ is well informed. The splash screens provide the victim with essential information, mainly where they have no knowledge of such payment methods or how to buy them. It also provides another mechanism for the attacker to get the ransom; merely stating that the payment needs to be given in BTCs has the potential to create confusion and further panic in the victim, leading to a delay in payment. Presenting this information in the form of Frequently Asked Questions (FAQs) is also an interesting approach and further emulates well know practices from business.
Not all splash screens are the same – there is a distinct difference in terms of the level of sophistication of mechanisms used to gain payment, presentation of the splash screens and provision of information for a further contact. However, there is no further data to explore how such differences map to their success in terms of eliciting payment.
The ransomware splash screens utilize critical aspects of influence and persuasion, concepts that are often used in the context of social engineering, to present a convincing argument for the victim to pay their ransom.
A small subset of ransomware splash screens served to intimidate the victim by claiming to be from an official source or law enforcement agency, but that did not explicitly ask for a specific ransom be paid. These were termed ‘cuckoo’ ransomware, and utilized official branding and badges to enhance the authority element.
Guy Fawkes vs. Jigsaw
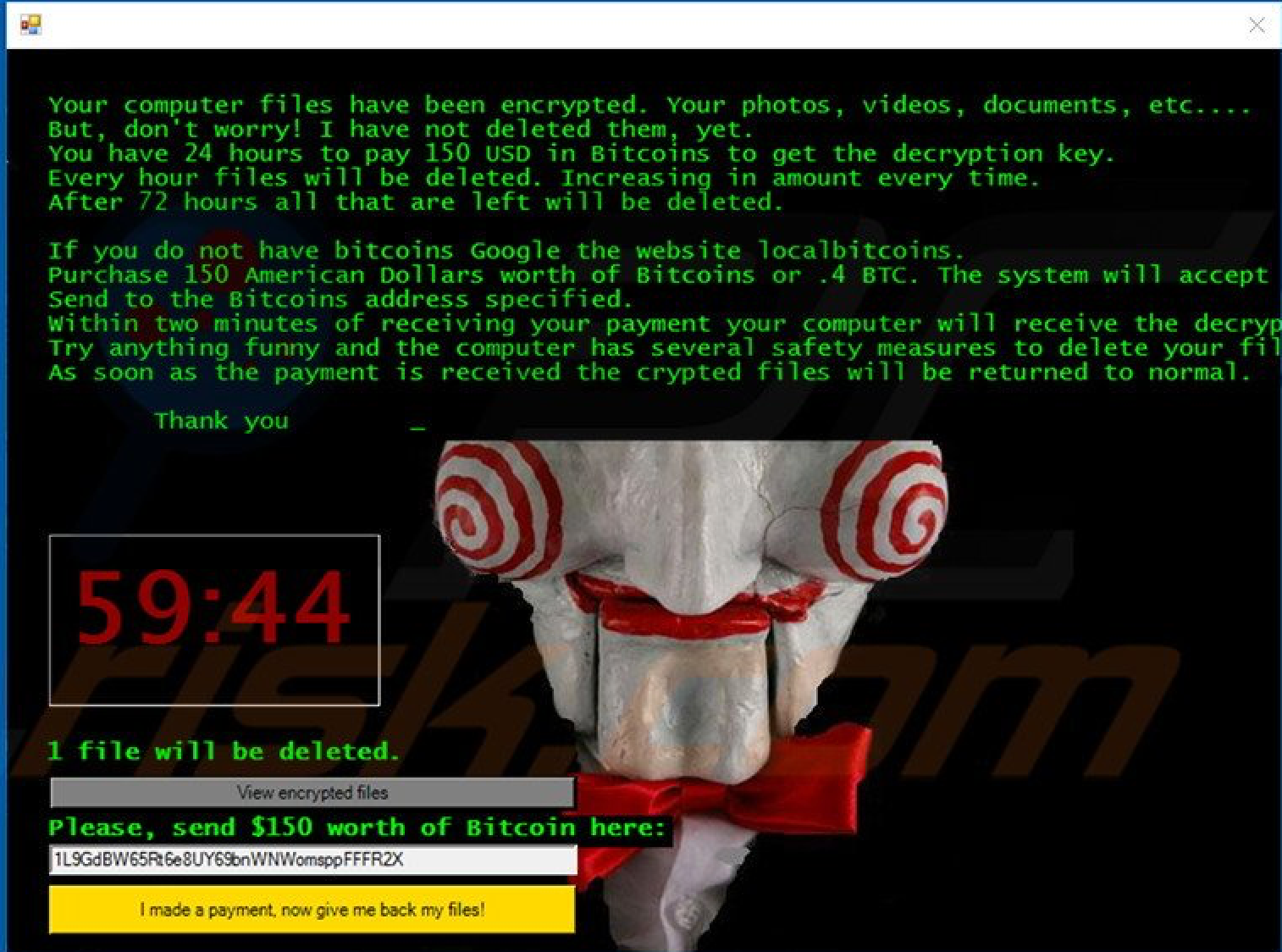
One of the most prominent pop cultural images used was that of “Jigsaw”, a character that appears in the Saw horror movie series. The character acts as a spokesperson for an often-unseen attacker and has a menacing appearance. The use of such imagery is interesting as it almost gives a substance to what is generally seen as a faceless crime, although it is noted that just a few of the splash screens used this image. Another image that was often used in the samples was the Guy Fawkes mask, used most notably with the hacking group Anonymous. Again, this symbol is used to enhance the authority element associated with social engineering, with many individuals (irrespective of their technical background) having some familiarity with Anonymous and their associated exploits. The use of these pop cultural icons is an interesting element of the ransomware splash screen and, as yet, is something that has not been fully explored in the context of research. It would be useful to understand how the victims of such attacks perceive such cultural symbols and how they feed into the decision-making process aligned with paying the ransom.
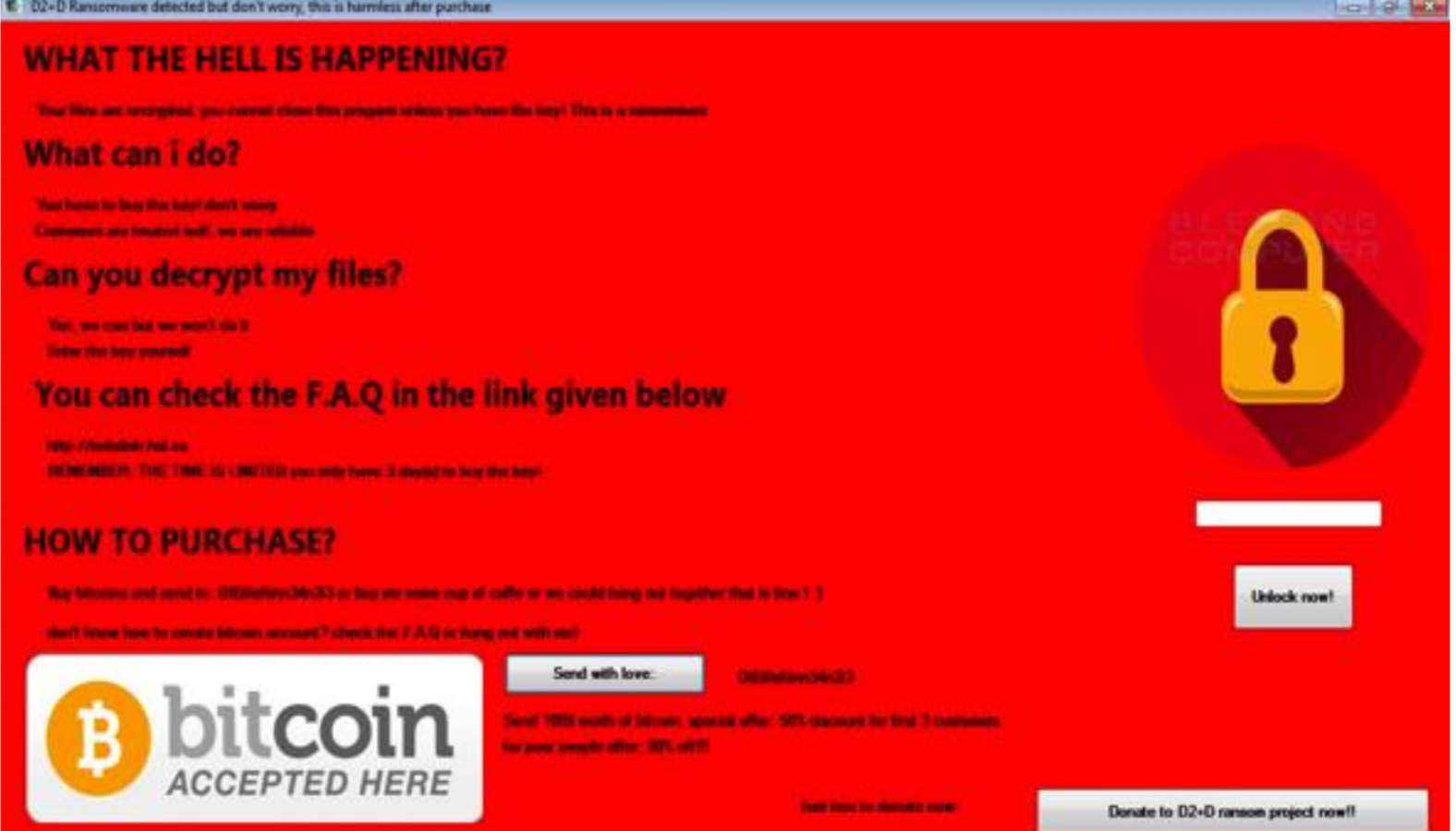
Brother, Can You Spare a Dime?
The text attempts to be humorous and conversational, perhaps an attempt to elicit an aspect of liking, another tactic used in social engineering. The two further interesting elements are contained under the header of “How to Purchase?” where the attacker asks the victim to send Bitcoins “or buy me some cup of coffee or we could hang out together that is fine! 😊”, as well as “check the F.A.Q. or hang out with me!”. The final aspect of this is the option to send Bitcoins and is labeled “send with love”. This splash screen is filled with paradoxes, as the attacker obviously wants the victim to pay the relevant ransom, but then also appears to want the victim to like them, attempting to engage them in conversational and interpersonal interactions. The offer to allow the victim to “donate” to the ransomware project is another element to this splash screen that makes it unusual. One final notable element is the offer of a discount for individuals who are “poor”, which makes this attacker perhaps the only one to exhibit an aspect of “social conscience”; however it is also noted that if they had such an aspect to their personality they would not have initiated the attack in the first instance.
You can find the full research here.