SentinelOne is pleased to announce general availability (GA) of Cloud Rogues, an exciting new feature of our real-time cloud workload protection platform (CWPP), Singularity Cloud Workload Security. Cloud Rogues continuously monitors virtual machines (VMs) in all AWS accounts where it is enabled, across all regions. It automates a complete inventory of unprotected VMs and identifies any newly created VMs. With this knowledge, cloud security practitioners may take next steps, such as deploying the SentinelOne CWS agent on running VMs or updating machine images to ensure that future VMs are protected when created.
Singularity Cloud Workload Security delivers real-time CWPP for workloads running in servers, VMs, containers, and Kubernetes, and across AWS, Azure, Google Cloud, private, and other clouds. The Cloud Rogues feature itself presently supports Amazon EC2 and services such as Amazon ECS and Amazon EKS, which are backed by Amazon EC2. Support for cloud compute from other CSPs (cloud service providers) is coming.

Getting Started with Cloud Rogues
To get started, Singularity Cloud Workload Security customers need to first grant SentinelOne read-only access to their AWS cloud accounts. This onboarding process may be for a single cloud account, or for an entire AWS Organization. Within minutes, SentinelOne discovers all VMs, Linux or Windows, in the specified AWS accounts which the customer has onboarded.
Here is a simple step-by-step guide to onboard a single AWS account. SentinelOne customers may consult the Knowledge Base (KB) article, How to Integrate Your AWS Cloud Accounts for more details or for step-by-step guidance to onboard an AWS Organization.
- From within the SentinelOne management console, go to Settings > Integrations > AWS Accounts and click
Add AWS Accounts.
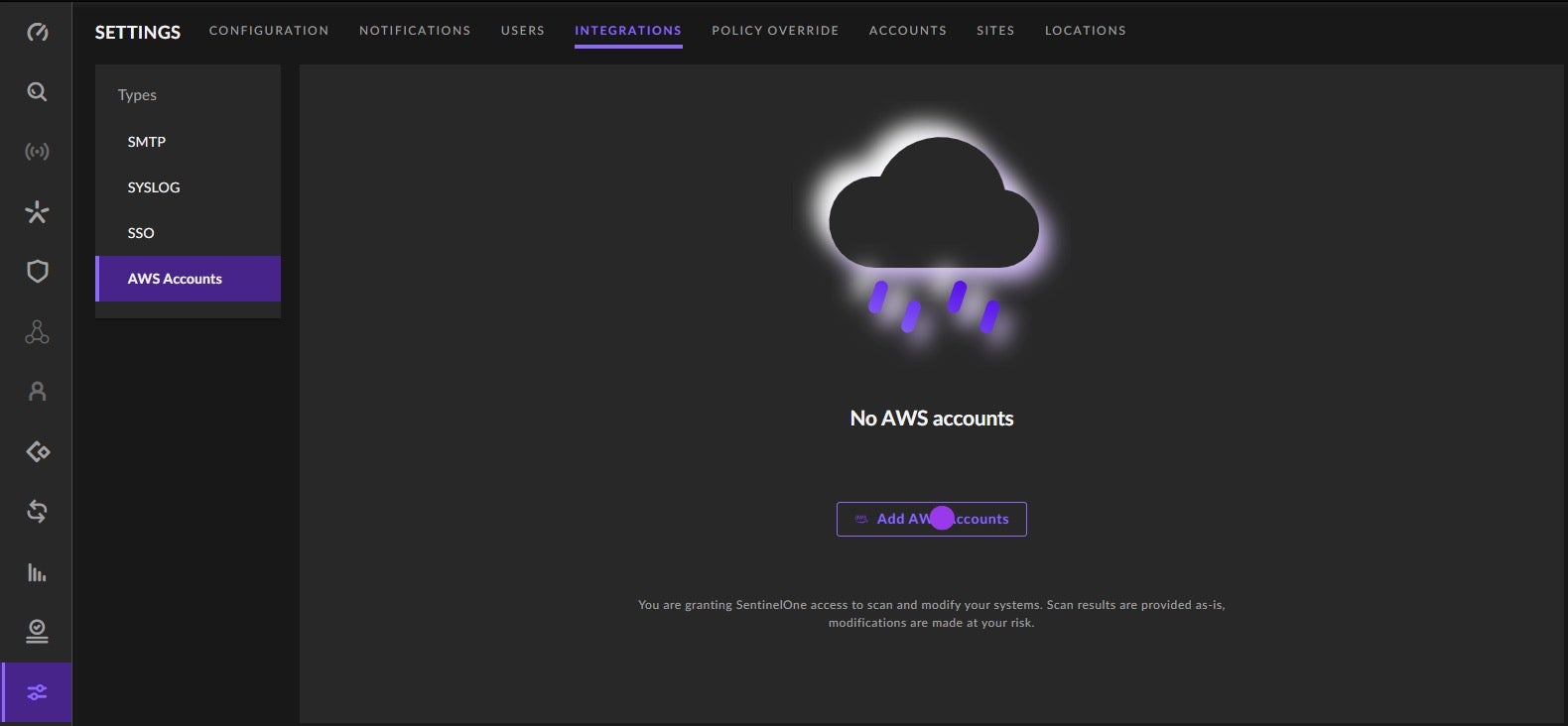
- Choose AWS Account and click
Next.
Pro Tip: Cloud Rogues also supports AWS Organizations to help onboard accounts at scale. - Select CWS (for Cloud Workload Security) and click
Next. - In the AWS Standalone Account Protection pop-up, click the link next to Create the connection stack. This opens the AWS CloudFormation console. From there, choose Create a Stack; consult the AWS docs for details. Create a unique Stack Name and Role Name, then click
Create.
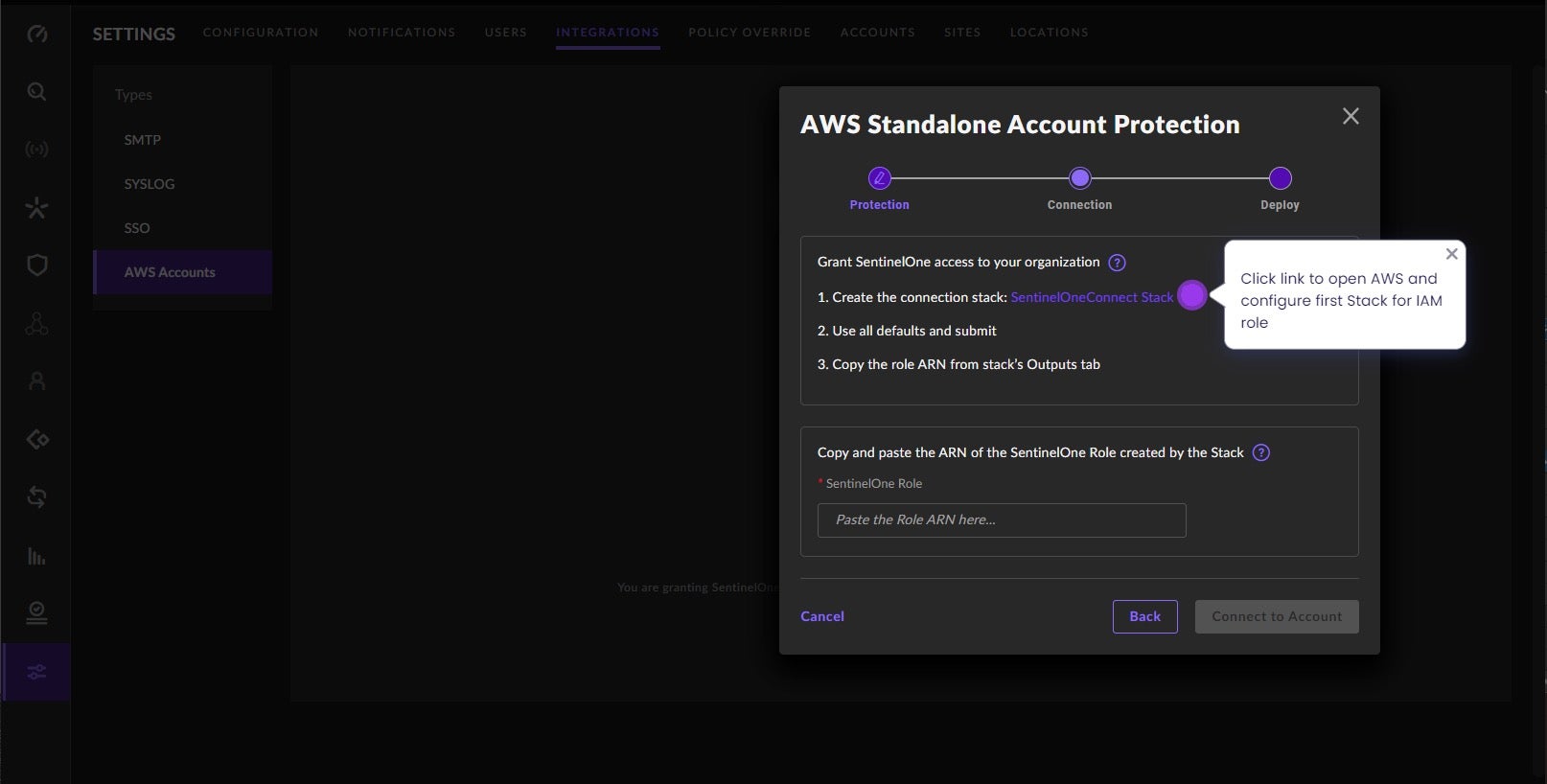
- Once creation of the Connection Stack is complete, copy the Role ARN value, return to the SentinelOne console, and paste the Role ARN value where indicated in the AWS Standalone Account Protection pop-up. Click
Connect to Account. - In the AWS Standalone Account Protection – Deploy window, click
SentinelOneDeploy Stack. This opens the AWS console. Select a CloudTrail to monitor for changes and clickSubmit. - Back in the SentinelOne console, click
Finish.
SentinelOne and the AWS account are now connected. The next step is to prepare for deployment.
Cloud Rogues is now active, automatically discovering unprotected Amazon EC2 instances (VMs) in the chosen AWS account. Knowing that many organizations have dozens if not hundreds of AWS accounts, onboarding via AWS Organizations is preferred at scale. Of course, the vast majority of users will prefer to start with a single AWS account to “test” the Cloud Rogues functionality. Discussion of onboarding via AWS Organizations is found in the aforementioned SentinelOne Knowledge Base (KB) article.
Discovering Unprotected VMs
Any VMs not currently protected by a SentinelOne agent are listed in the SentinelOne management console under Sentinels > Cloud Rogues. Details such as cloud account ID, instance ID, tags, network, and OS are shown in the inventory. Users may export the inventory in a CSV or JSON file. Newly created VMs are reported shortly after their creation.
With this information, security practitioners can make better risk management decisions. They may choose to deploy a SentinelOne CWPP agent (Singularity Cloud Workload Security for Servers/VMs) directly to the running VM. Alternatively, they may choose to update the Amazon Machine Image (AMI), from which the EC2 instance was spawned, to include the CWPP agent so that all future EC2 instances are protected when created. Less likely, but still possible, is that the security team elects to do nothing, and simply document an exception indicating that they understand that this cloud VM lacks any runtime protection or forensic workload visibility.
Available To All SentinelOne Customers
Existing SentinelOne customers (endpoint, identity) who have not yet purchased Singularity Cloud Workload Security can still benefit from Cloud Rogues. The Cloud Rogues feature itself is agentless, using AWS APIs to identify Amazon EC2 instances in the account/organization of interest. As such, any SentinelOne customer can use Cloud Rogues to understand the extent of the unprotected compute infrastructure in their AWS accounts. Armed with this knowledge, customers can build a business case to justify purchasing Singularity Cloud Workload Security. Of course, the benefits of our real-time CWPP solution go far beyond simple visibility – namely, maximum workload integrity and availability, forensic analytics for use during triage and incident response, and more.
Taking the Next Step with Real-Time CWPP
Better cloud security begins with visibility of the attack surface. By automatically identifying unprotected cloud compute instances in their AWS footprint, organizations are better able to manage the attack surface, reduce risk, and take informed actions.
Next steps may include deploying a CWPP agent to the unprotected instance, updating the machine image to include an agent, or documenting an exception. With Singularity Cloud Workload Security, customers have real-time cloud workload protection and forensic visibility into all workload telemetry.
To learn more about the value of real-time CWPP in your cloud security stack, head over to the solution homepage. Or see how Singularity Cloud Workload Security works with a 2-minute guided walk-through here. And of course, whenever you are ready, you may connect with one of our cloud security experts for a personalized demo.


