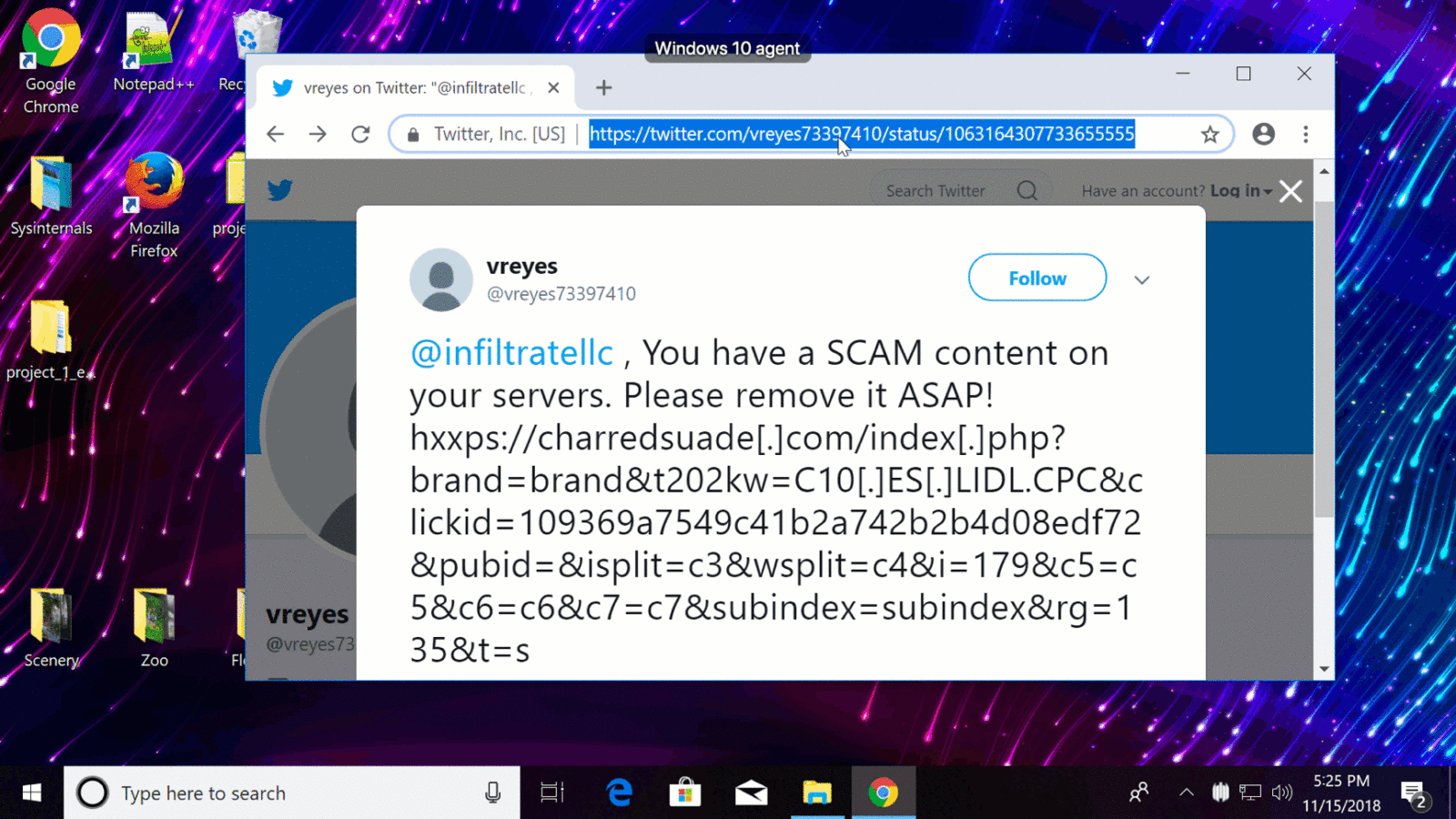
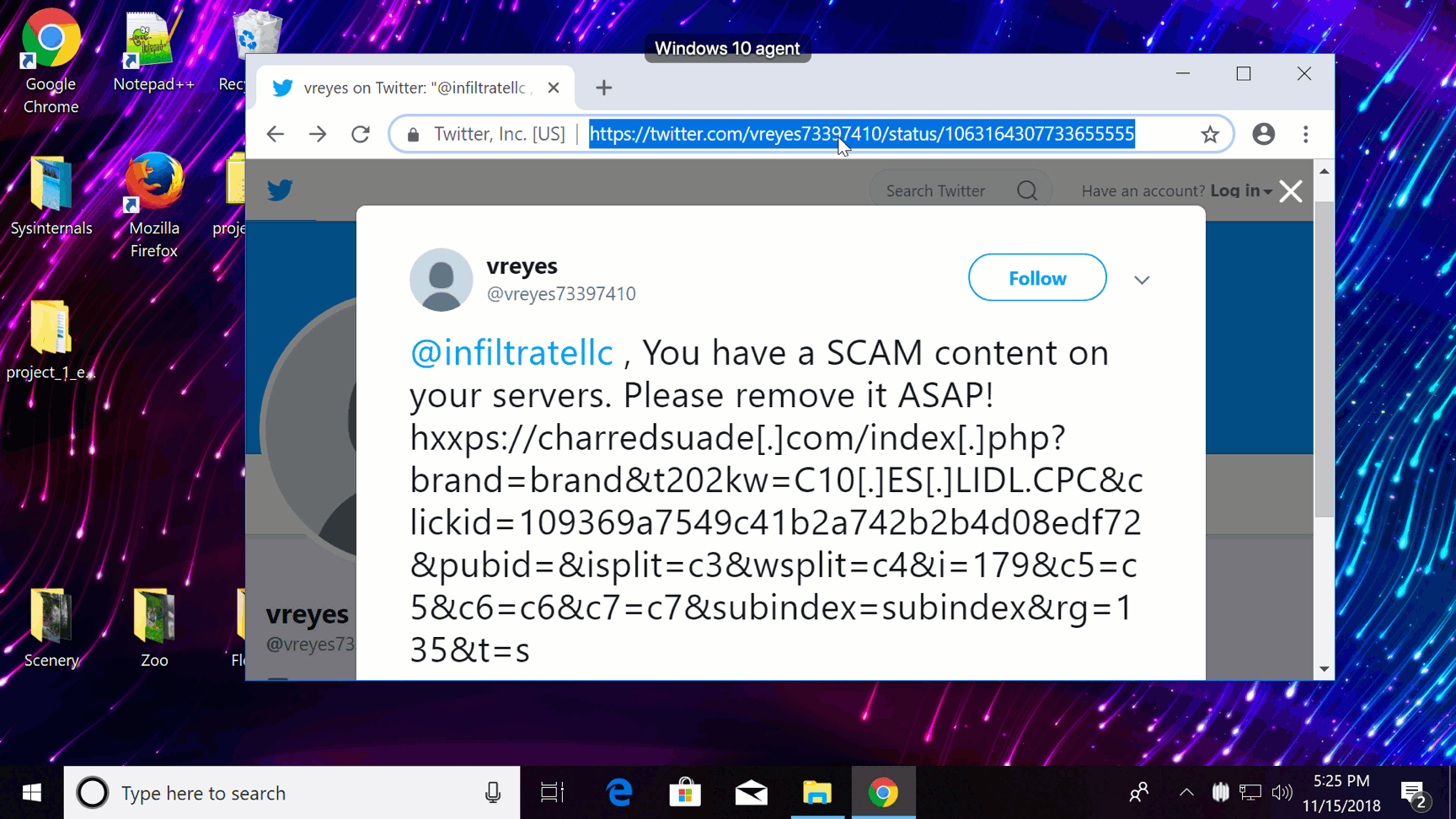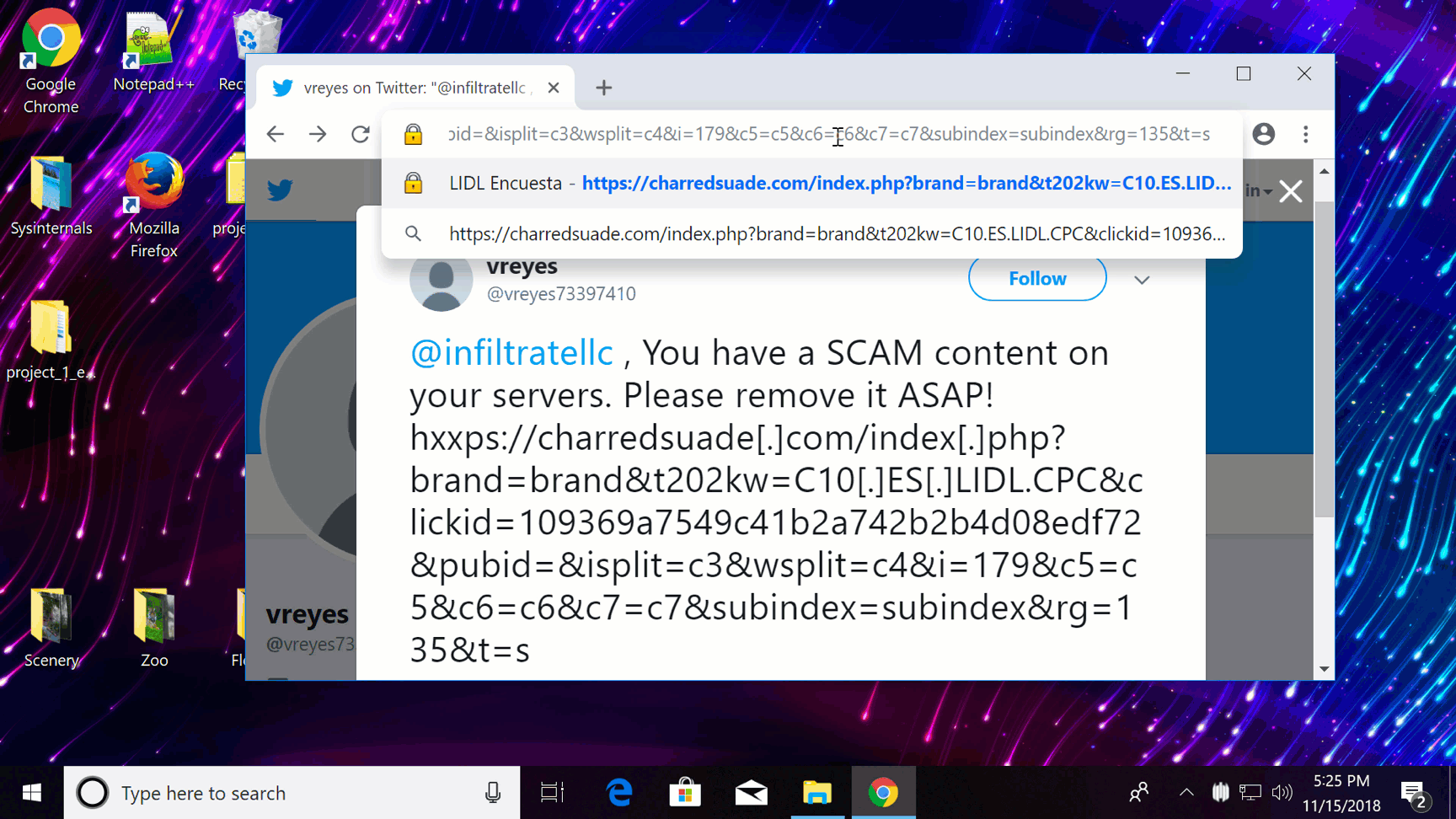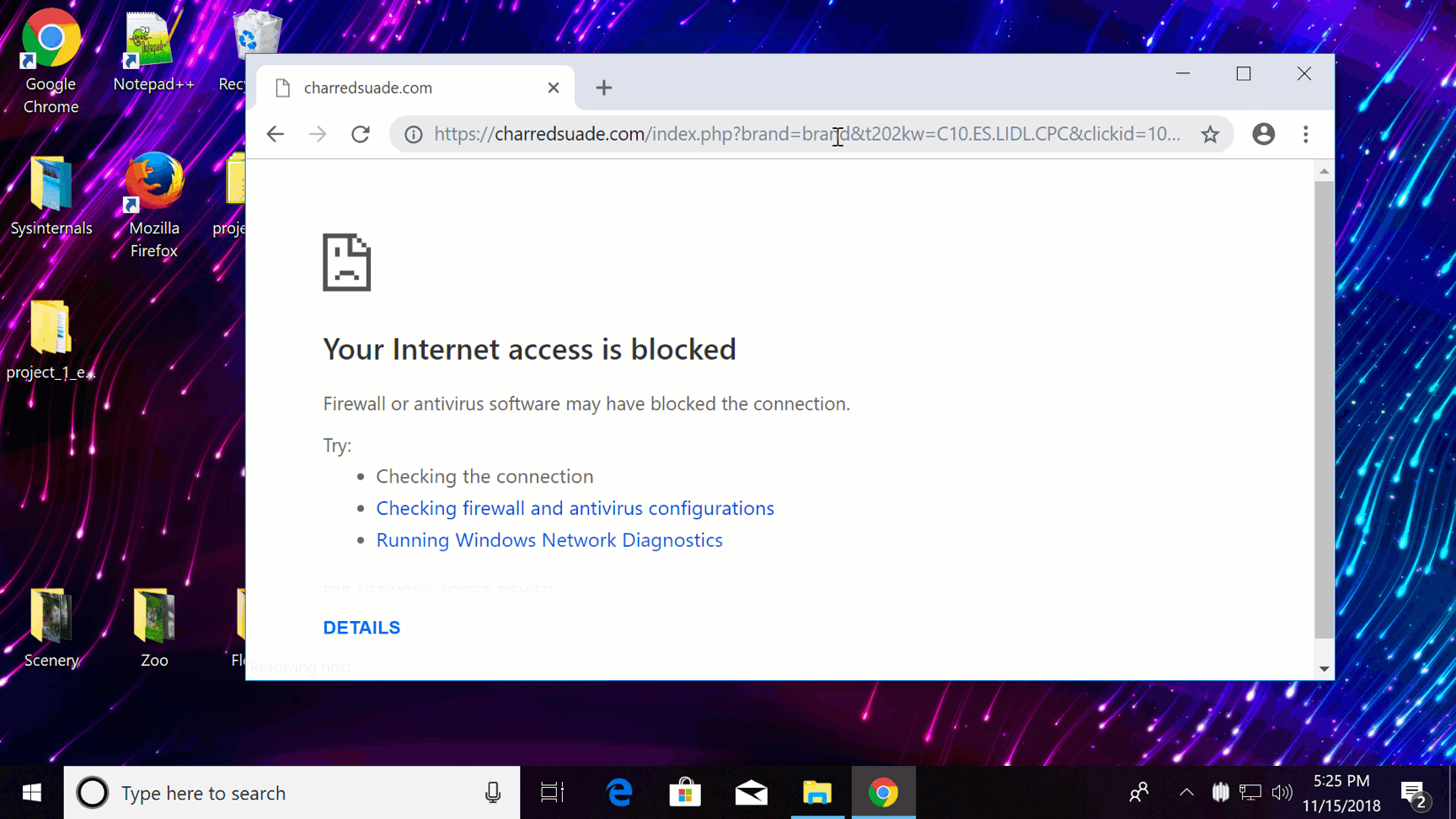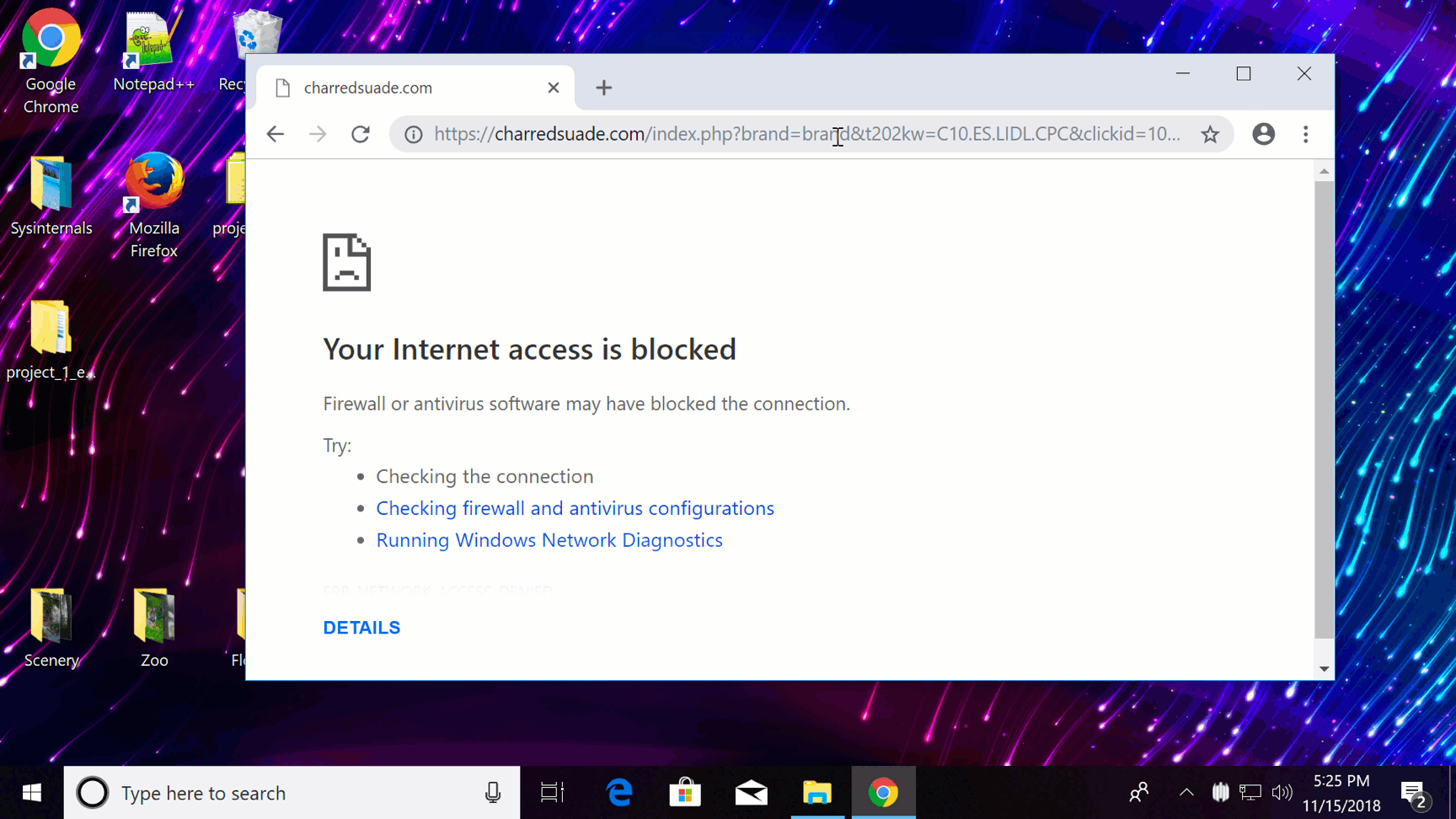
Consider the following scenario: IT gets an intelligence feed indicating that a specific phishing URL is scraping credentials globally. To protect users on the network, administrators immediately add a rule to the network firewall to block the URL. But what about remote users not behind the firewall? And what if the perimeter protection fails or is circumvented?
Endpoint Firewall Control answers these challenges by governing permitted communications to and from every endpoint. It allows an administrator to control and enforce a policy.
The Why
There are 4 reasons why we’ve built this capability into the SentinelOne agent:
1. Visibility
According to a SentinelOne Ransomware survey, almost seven in ten (69%) of those whose organization had suffered a ransomware attack in the last 12 months said that the attacker was able to gain access to their organization’s network by phishing via email or social media. Around two in five reported that access was gained by a drive-by-download caused by clicking on a compromised website (44%). This clearly shows that the network is the most prevalent infection vector. To make things more challenging, most network traffic is encrypted, which improves privacy but eliminates the option for network firewalls to see beyond the headers. At the same time, a growing number of users are remote, making the network firewall ineffective in providing a defensive shield. Your users can work from anywhere, and the only certainty you have is they are going to use their endpoint device.
The answer is to increase asset protection by dealing with network-related infections using network access control. The ability to see all traffic is part of SentinelOne Deep Visibility feature, which also supports visibility into encrypted traffic.
2. Malware Prevention
There are two primary reasons for network traffic when it comes to malicious adversaries:
- Most malware infections attempt to connect to a Command and Control (C2) server to establish remote control or exfiltrate data.
- Ransomware typically stores encryption keys on a remote server to increase the chances for a payout.
3. Enterprise Data Loss Prevention
Firewall Control can block unauthorized transfer of data to and from all your endpoints, both on and off the corporate network. This allows you to reduce the risk of data leakage from your assets. Data theft occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a computer. Malware typically tries to stay undetected and to scrape personal data, either for extortion or espionage. For example, earlier this year, we learned about a Tesla employee who shared sensitive information after writing software to periodically export gigabytes of proprietary data and funnel it outside of the organization. Network access control could have prevented this loss.
4. Compliance
As Firewall Control provides yet another measure to mitigate risk in the enterprise, it may help your organization to achieve compliance where network access control is required.
Ease of Management
Adding features to a platform is always a desirable move, but it cannot come at the expense of usability. Building products that require highly-trained personnel to manage might solve some customers’ needs, but it creates another problem. You can still see cases out there where products are not configured correctly or are just not monitored effectively because of the difficulty of using them. The result is complex products can fail to tackle the very problems they were intended to solve. In the case of Firewall Control, we’ve implemented a straightforward rule-based experience that provides flexibility without complexity.
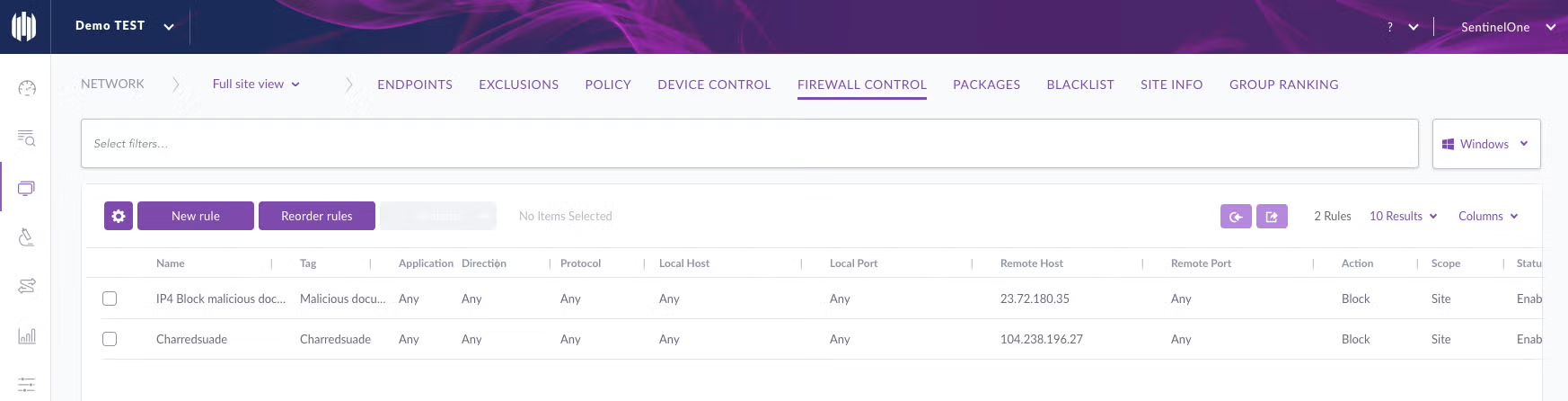
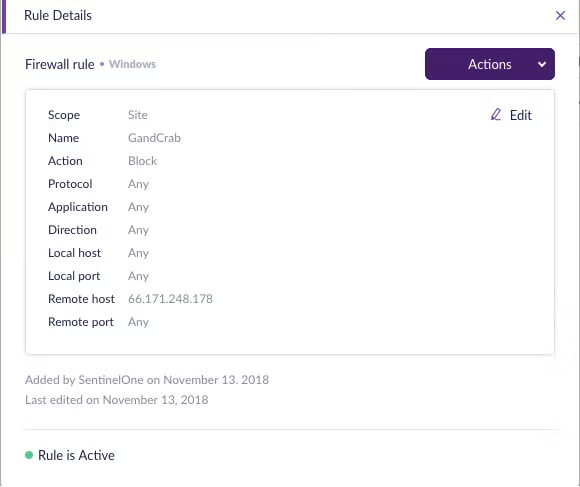
Demo
On this demo you can see how Firewall Control can be used to block a phishing attempt.
Take Away
Security is not only about preventing malware. Good hygiene across your network can help win the battle before it’s fought. Endpoint Firewall Control is an important part of a layered security model. Securing network traffic is not new to SentinelOne. We’ve seen many attempted attacks and have an automated response to it. The power of the platform is that you get all these capabilities in a single autonomous agent – no additional install is needed.
Firewall Control is supported starting with 2.8 agents (with Eiffel console) and is part of the SentinelOne “Complete” offering.
Liked this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.