Threat actors have been using various countermeasures to evade detection for some time.
For example, some malware will check if they are running on a virtual machine to avoid being detected by sandbox and later having signatures generated against them. Another typical method is to check whether the target device is running certain security products that can identify the malware, and if so, to delete themselves before doing anything malicious. It has become a game of cat-and-mouse where malware authors take steps to deploy evasion techniques while the defenders seek to trigger those techniques in return. We’ve seen security products relying on this to help reduce the attack surface. SentinelOne also embeds similar measures as part of our defensive techniques.
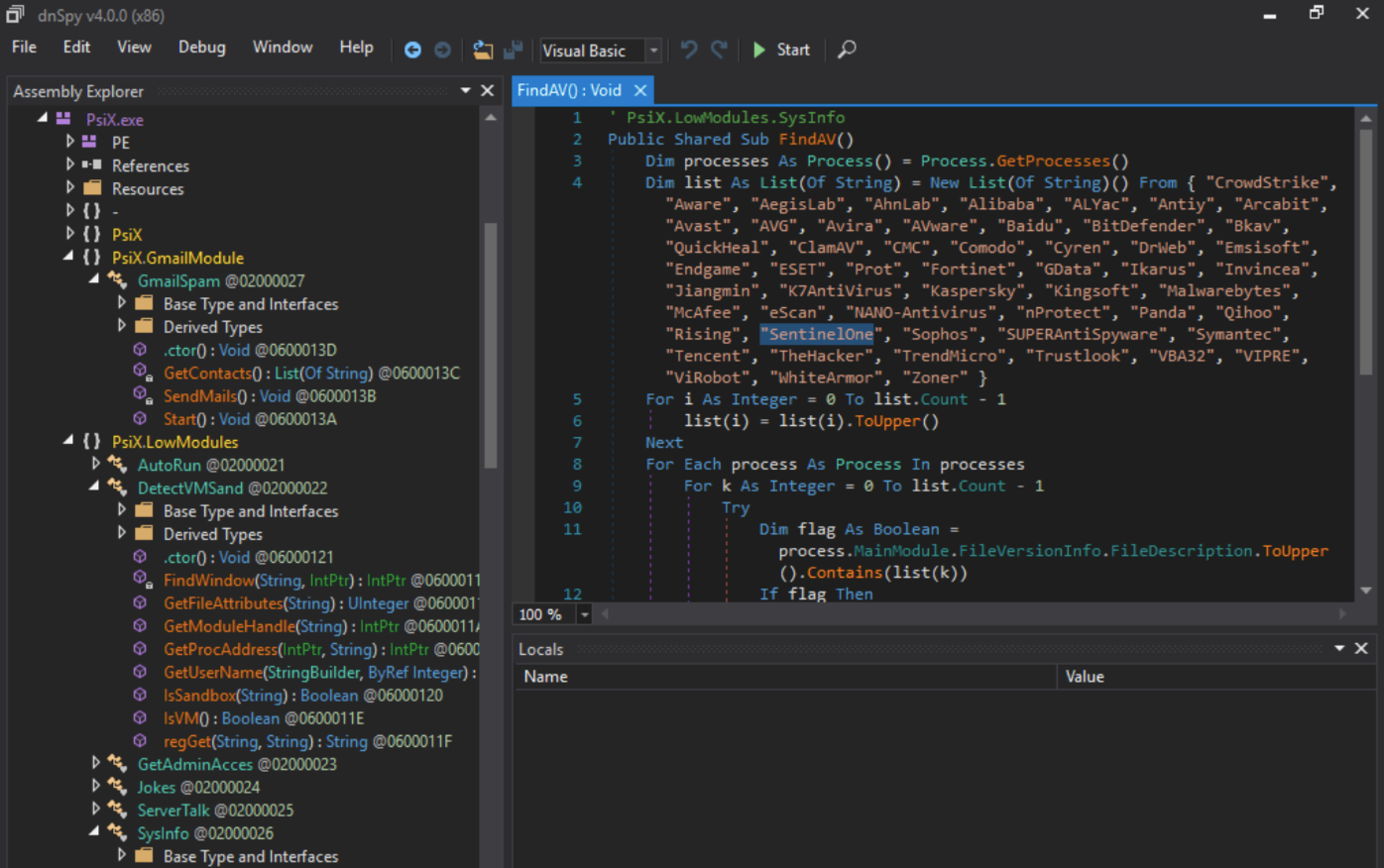
While it is now common-place to see malware attempting to evade detection by security solutions, it’s rare to see malware avoiding victims. With RAPID 2.0 RANSOMWARE, this is precisely the case, as it will not run if it identifies the locale as Russian on the target Windows device.
Demo: Rapid 2.0 Ransomware VS SentinelOne
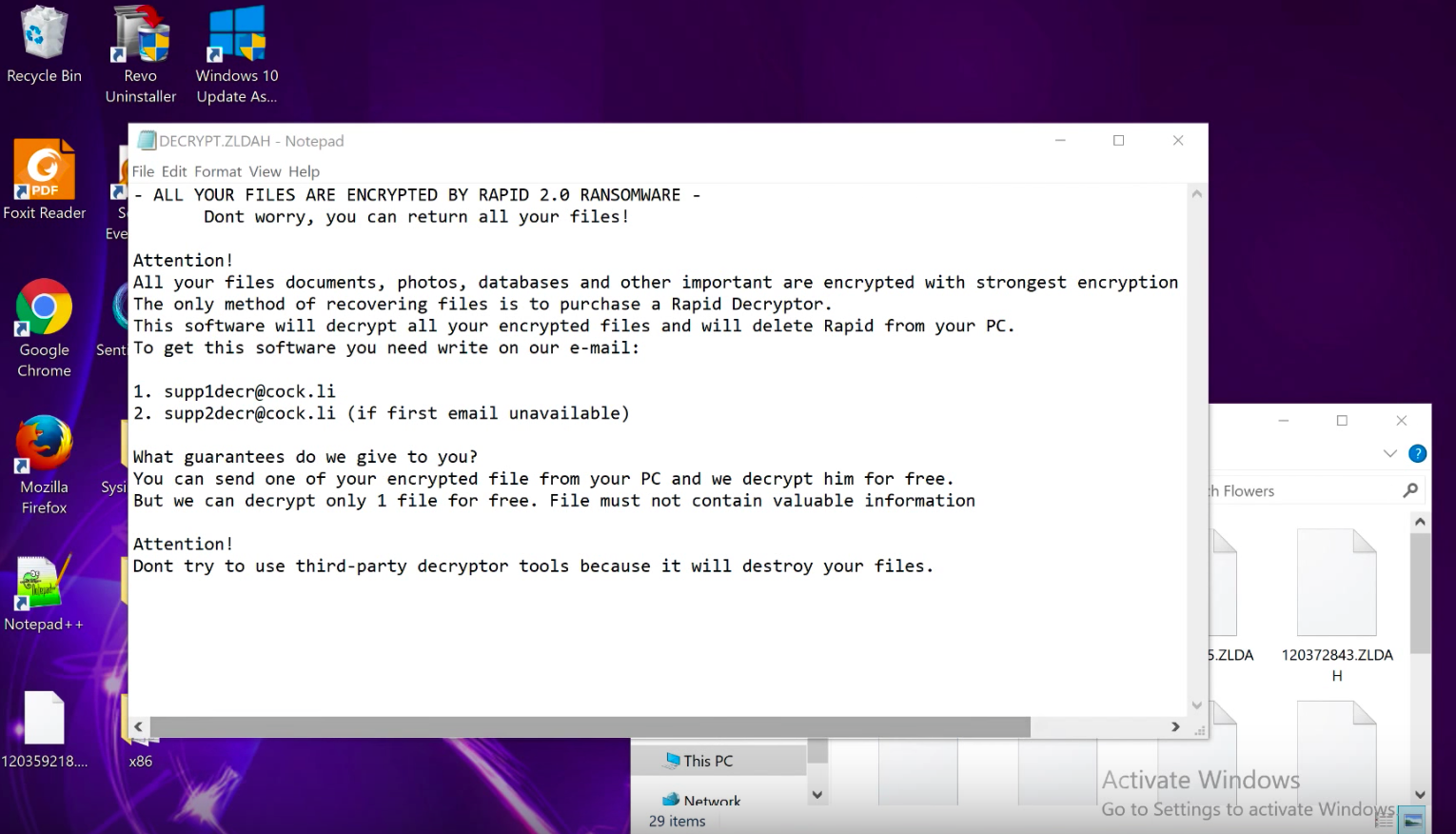
Since RAPID 2.0 RANSOMWARE will not encrypt any data on devices with a Russian locale, we used English in this demonstration. In this video, you can see how SentinelOne detects and protects against the ransomware with both its Static AI and Behavioral AI engines, even when offline. Once the device is disconnected from the network, we copy the malicious sample to the Desktop, where it is immediately detected by the SentinelOne Static AI. As the policy is set to Detect-only, the ransomware is not quarantined. Then, allowing it to execute for the purposes of the demonstration, notice how it is instantly detected again by SentinelOne’s Behavioral AI.
Once the device is re-connected to the network, we see the ransomware has encrypted 298 files and initiate a rollback. In a matter of seconds, the endpoint is back to its pre-infected state and the user’s files are entirely recovered.
In a real-life scenario with SentinelOne’s policy set to ‘Protect’, this ransomware would have been prevented automatically. When so many devices are getting infected so quickly, it is clear that what is needed is an automated solution that is capable of preventing it in milliseconds. The cost to business of having some or all of the devices in their fleet infected can be catastrophic. If SentinelOne already protects you, we’ve got you covered.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Want to see how SentinelOne can help improve your security efforts? Request a Demo Now

