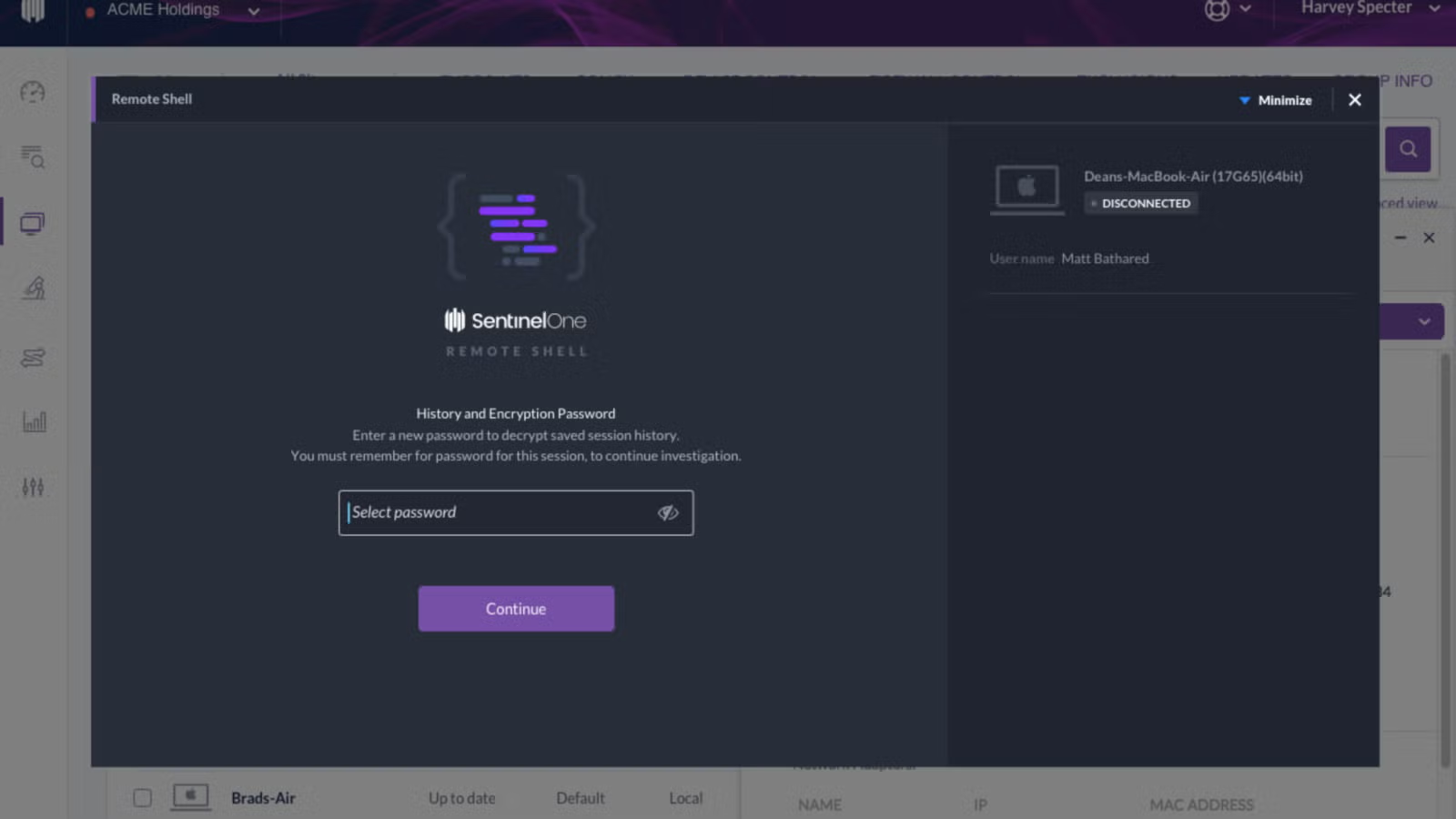
Full Remote Shell gives your security team a rapid way to investigate attacks, collect forensic data, and remediate breaches no matter where the compromised endpoints are located, eliminating uncertainty and greatly reducing any downtime that results from an attack.
Today we are glad to announce another useful feature of the SentinelOne platform, the Full Remote Shell. As the name indicates, it allows an authorized administrator to securely access their managed endpoints directly from the SentinelOne console. This way, sysadmins and SecOps can quickly establish a full remote shell session to troubleshoot end-user issues without having to go on-site.
Savvy admins know that having the capability to see and interact with any device on the network can make the difference between “problem solved” and “late for dinner”. With so much noise on the network today, the remote shell is an essential tool for better endpoint management.

Why You Need Remote Shell Capability
The endpoint landscape is constantly changing. Users install a wide variety of software to perform their jobs more efficiently, and that makes it challenging to keep up with best practices for security and risk management. In such a demanding environment, admins will find a vast number of use cases for a powerful, full remote shell capability.
Here are a few suggestions to get you started:
- Faster troubleshooting as admins don’t have to be physically next to an endpoint device to solve problems
- Better support for remote users as there’s no need to ask users to come by the office or visit the IT department
- Easily change local configuration without leaving the premises
- Initiate a remote control in a secure way
- Go deeper into forensic investigation with a memory dump and other advanced tools
- Terminate an unwanted application or process running on an endpoint
- Query any device on the network, locally
Is it Secure?
For security products, allowing a remote shell into every device is to some extent against their DNA. On the other hand, we want to ensure that SentinelOne meets the security needs of the enterprise. We listened to you, our customers, and here’s how we met the dual needs of usability and security:
- Full Remote Shell access must be specifically enabled in the management policy
- For each session, the administrator is required to choose a dedicated password to encrypt the session
- Prior to allowing access, the admin must enable two factor authentication
- Full auditing – every session is logged, including every access, usage and session history
How SentinelOne Full Remote Shell is Different
When we came to design the full remote shell, we interviewed admins about their experience using similar capabilities in other products. The main pain these users reported was the limited amount of commands they could execute. If they needed another command, it required a feature request to the vendor and other lengthy processes. To avoid that pain, we use native shell capabilities. In other words, anything you can do with PowerShell and Bash, you can also do with SentinelOne Full Remote Shell, and that provides a lot of options. We even support command completion and other means to simplify the sysadmin’s life.
Demo
Conclusion
SentinelOne’s Full Remote Shell helps your business avoid the “IT nightmare” of managing a distributed network securely. It allows IT personnel to respond quickly and efficiently when employees experience technical problems without having to go to each device. The remote shell capability has all the power you would expect in a regular shell session, implemented in the simple and secure way that is the hallmark of the SentinelOne offering. Full Remote Shell is available starting agent version 3.0.