In a recent event, Google released an emergency security update to address a zero-day vulnerability in the Chromium-based browser. The vulnerability, CVE-2023-2033, is a type confusion issue in the V8 JavaScript engine used by Chromium Open Source Software (OSS), which is consumed by browsers like Google Chrome, Microsoft Edge (Chromium-based), etc. This vulnerability could allow attackers to execute remote code and gain unauthorized access to sensitive information. In this blog post, we will delve deeper into what type confusion vulnerability is and provide details on the CVE-2023-2033 vulnerability.
The vulnerability has a CVSS score of 8.8, classified as HIGH.
What is type confusion vulnerability?
Type confusion vulnerability happens when code lacks type-checking by not verifying the type of an object it uses. Exploiting this vulnerability allows attackers to corrupt memory, leading to unauthorized access to sensitive information or execution of arbitrary code. Type confusion bugs are especially dangerous as they can exploit vulnerabilities in popular software, like the V8 JavaScript engine utilized by Google Chrome.
Vulnerability Analysis
The vulnerability can exploited by attackers using a specially crafted HTML page to trigger a memory corruption (heap corruption) vulnerability.
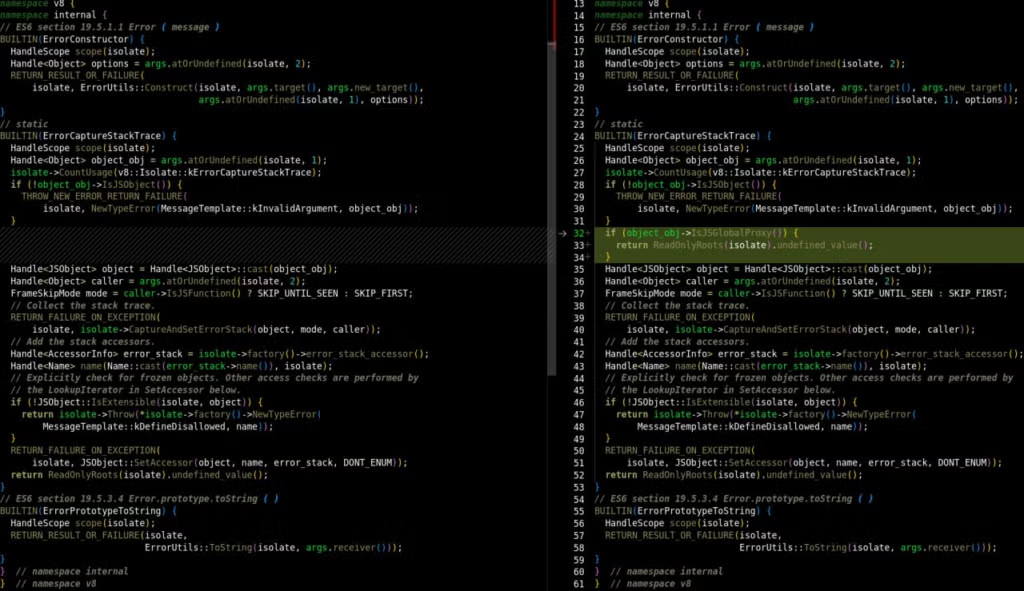
The V8 type confusion vulnerability can happen if attackers manipulate the JavaScript object given to the ErrorCaptureStackTrace function.
In the vulnerable code, the Error Capture StackTrace function expects a single argument, which is an Error object. If an attacker can pass a different type of object, such as a plain JavaScript object or a string, to this function, then a type confusion vulnerability can occur. This is because the code assumes that the argument passed to ErrorCaptureStackTrace is always an Error object and tries to access its stack property. If the passed object is not an Error object but rather a different type, attempting to access its stack property could lead to unexpected behavior, including crashing the application or exposing sensitive data.
An attacker can create a specially crafted JavaScript object that exploits the type confusion vulnerability in the code. When the vulnerable code executes, it may interpret the object type incorrectly, leading to a type mismatch and an incorrect memory layout. This can result in an attacker being able to overwrite memory locations with arbitrary data, including pointers to other parts of the program, potentially leading to the execution of arbitrary code.
For example, an attacker could create an object that appears normal in JavaScript but contains a hidden field pointing to a piece of executable code in memory. If the vulnerable code incorrectly interprets the object’s type, it may use the hidden field as a pointer to execute the code, leading to arbitrary code execution.
Affected Versions
The CVE-2023-2033 vulnerability affects Google Chrome browser users on all platforms, including Windows, Mac, and Linux systems. The vulnerability exists in Chrome versions prior to version 112.0.5615.121.
CVE-2023-2033 Mitigation
- To protect against this vulnerability, it is recommend to update your Google Chrome browser to the latest version (version 112.0.5615.137). You can do this by opening the Chrome menu, selecting Help, and selecting About Google Chrome. If an update is available, it will be installed automatically. Find more details here.
- Another way to mitigate the risk of exploitation is to disable JavaScript. This can be done by going to Chrome settings and turning off the JavaScript option. This could affect functionality of some websites and web applications, making it impractical for some users as a solution.
- Enabling site isolation is another security feature in Google Chrome that can help prevent attackers from exploiting vulnerabilities like CVE-2023-2033. You can enable site isolation by going to chrome://flags/#enable-site-per-process in the Chrome address bar and enabling the feature.
Summary
Attackers exploit type confusion vulnerability, a software bug, to gain unauthorized access to sensitive information or to execute arbitrary code. The CVE-2023-2033 vulnerability is a type confusion issue in the V8 JavaScript engine used by the Google Chrome browser.
The vulnerability affects all Chrome users on all platforms, and the exploit would triggered using a specially crafted HTML page. Google has confirmed the existence of an exploit and advises immediate update to latest Chrome version to mitigate the risk.


