Linux admins are being urged to check for and patch three TCP networking vulnerabilities discovered by Netflix researchers. While patches have been made available, testing patches against a full stack of software applications can sometimes be a lengthy process. Given the urgency and widespread nature of the vulnerabilities, SentinelOne has released a free tool that can quickly identify affected Linux systems and immediately protect against these new vulnerabilities.
What Did Netflix Discover?
A security advisory from Netflix researchers on Friday identified three vulnerabilities that affect Linux kernels. The vulnerabilities are catalogued as
- CVE-2019-11477: SACK Panic (Linux >= 2.6.29) Severity: Important
- CVE-2019-11478: SACK Excess Resource Usage (Linux < 4.15 / All Linux Versions) Severity: Moderate
- CVE-2019-11479: Excess Resource Usage (all Linux versions) Severity: Moderate
A fourth, related, vulnerability, CVE-2019-5599 also affects devices running FreeBSD.
Affected Linux systems may be vulnerable to attacks from maliciously crafted TCP packets that use low MMS (Maximum Segment Size) values and manipulate TCP SACK (Selective TCP Acknowledgement) processing.
Exploiting these vulnerabilities could result in excess resource consumption or trigger a kernel panic, leading to a possible Denial-of-Service attack.
Why is the Linux Kernel Vulnerable to SACK Panic?
SACK or Selective TCP Acknowledgement is a technology designed to make TCP more efficient. When a device receives a data stream over TCP, it doesn’t need to care about the order the packets arrive in. TCP is designed so that packets can be reassembled in the right order by making use of sequence numbers in the TCP headers. As part of the two-way communication between host and receiver, Selective TCP Acknowledgements are sent back to the host so that both the host and receiver know which packets have arrived and which need to be resent.
The SACK Panic vulnerability lies in the way the receiver holds on to the data while waiting for the transmission to be complete. When a packet is processed with a low MMS, it’s possible for the sequence of SACKs to exceed the number of segments that can be stored in the Socket Buffer (SKB) at any one time. When that happens, an integer overflow occurs and causes a kernel panic.
How Can I Protect Against SACK Panic?
To exploit the SACK Panic and related vulnerabilities, attackers would need to attack a Linux box that has both TCP probing and SACK processing enabled. These are, however, common defaults.
Fortunately, we can effectively close these vulnerabilities either by manipulating the tables used by the Linux kernel firewall, using iptables to drop packets received with a low MMS or by disabling SACK processing entirely. We also need to ensure that TCP probing is disabled by setting the appropriate value with sysctl.
In order to determine if you’re running an affected system and to quickly apply the needed workarounds, SentinelOne researcher Dor Dankner has developed this script.
You can use the script to first check if your system is vulnerable, and if so to apply the workarounds. The script makes a backup copy of your current settings to allow you to easily revert if needed, and it also ensures that the settings are persistent across reboots.
Running as root, let’s first use the script’s check option to see if we’re vulnerable.
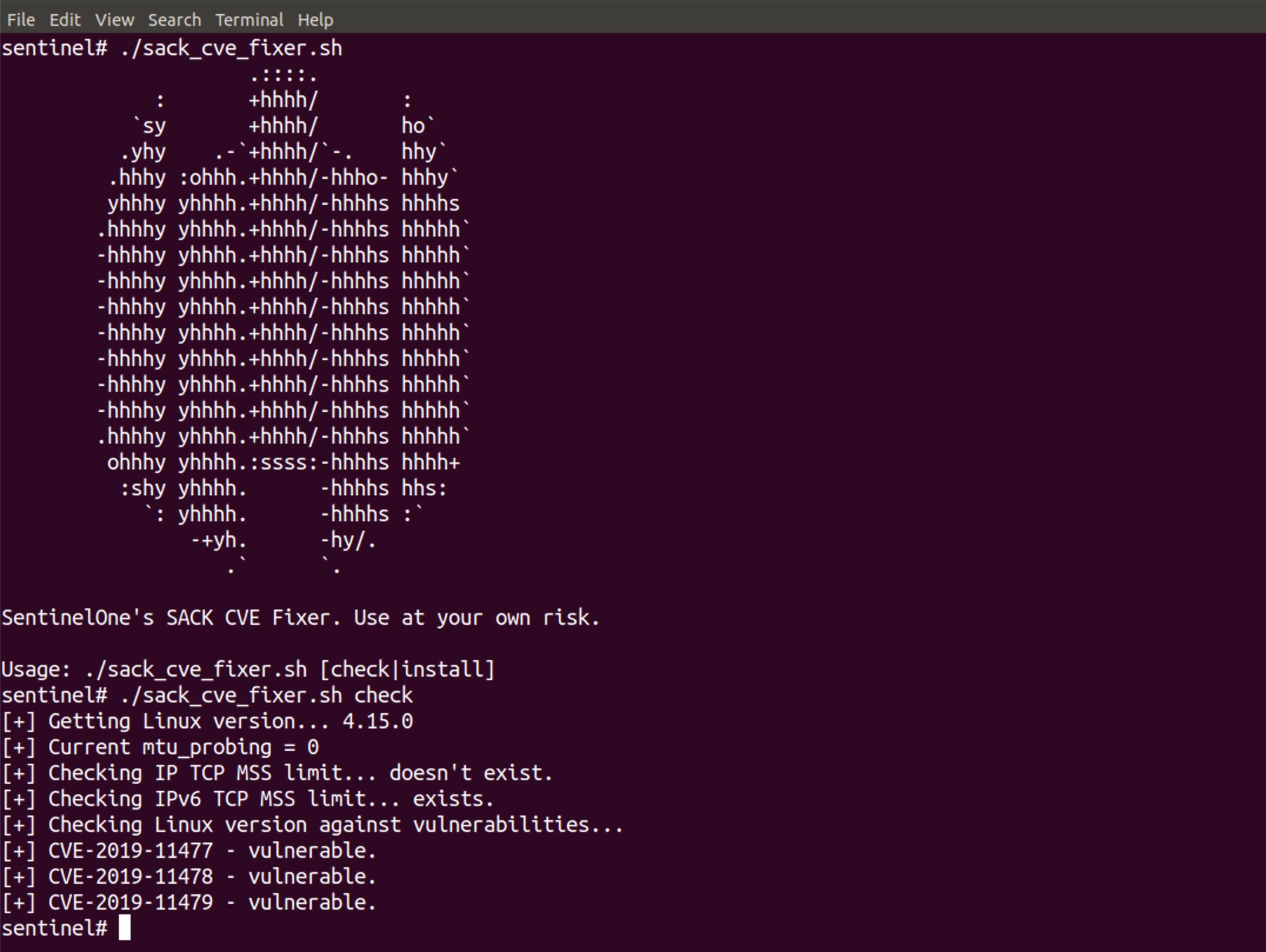
In this case, it looks like we are, so we’ll now use install to enable the protection:
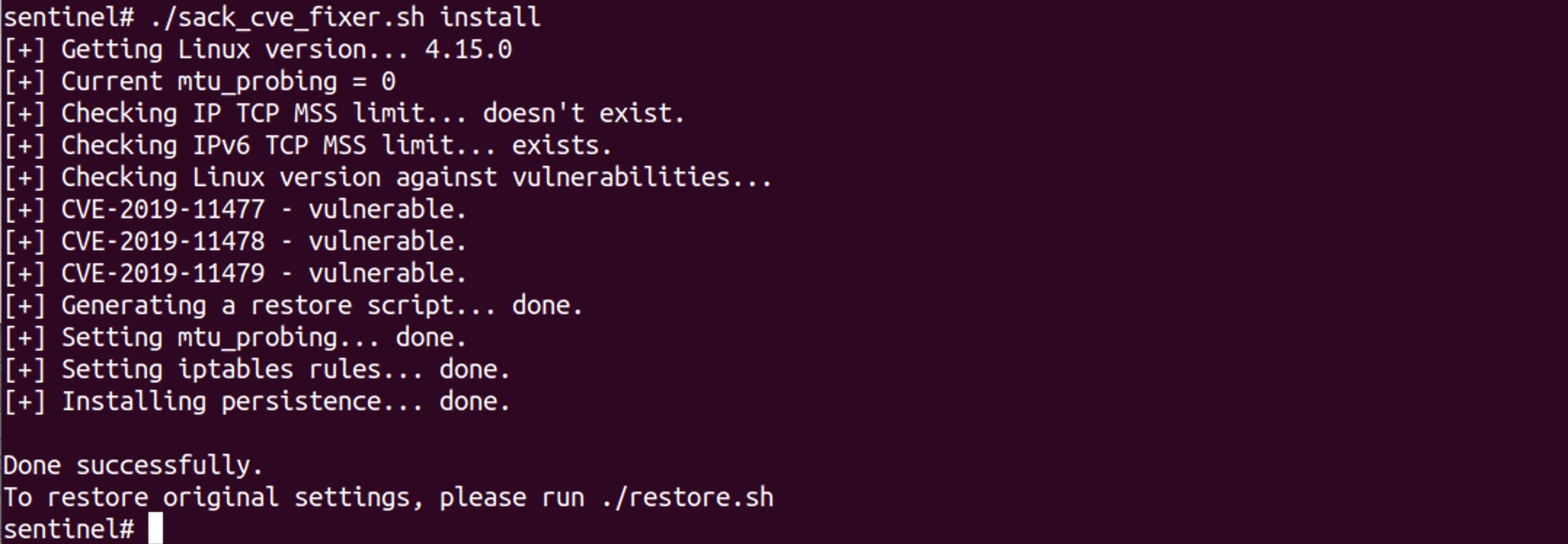
All looks good, and we have the option to restore if needed. Persistence is also enabled. Let’s just confirm by running check again.
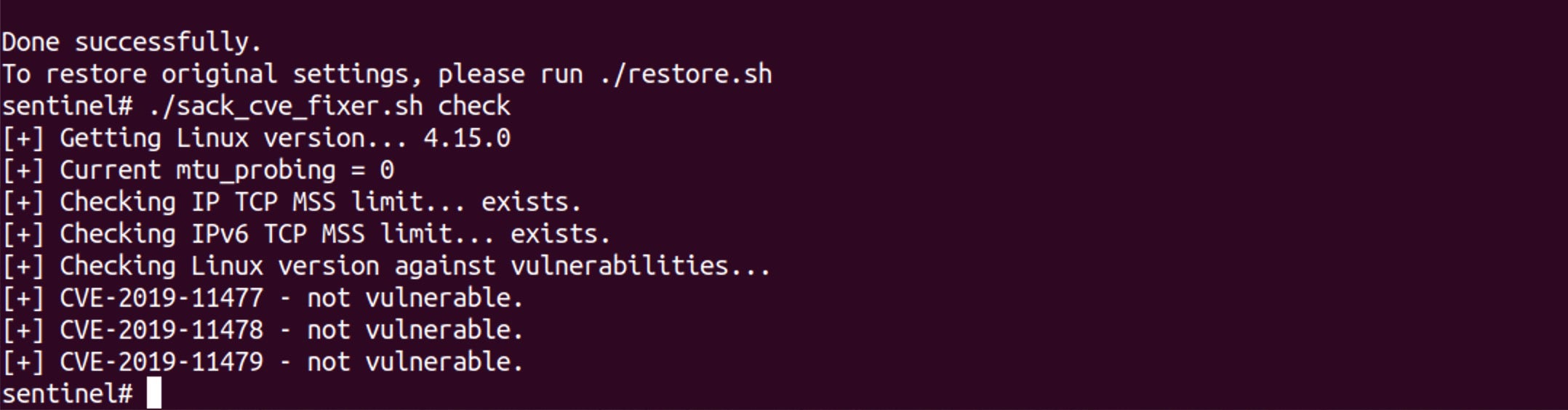
As expected, the script now reports that this device is no longer vulnerable to the three Linux kernel TCP networking vulnerabilities discovered by Netflix.
Be aware that there is an edge case here, which is that by preventing a low MMS, legitimate connections utilising a low MMS will also be dropped. Therefore, it’s a good idea to test and apply appropriate patches at your earliest opportunity for a more robust, long-term solution.
Where is the Free Tool Available?
You can download the free tool from SentinelOne’s public Github repository here.
Conclusion
Given the huge number of affected devices, it’s only a matter of time before threat actors move to develop exploits for Linux machines that are not protected against these TCP networking vulnerabilities. Using the free SentinelOne tool, you can secure your endpoints immediately from any such attacks.


