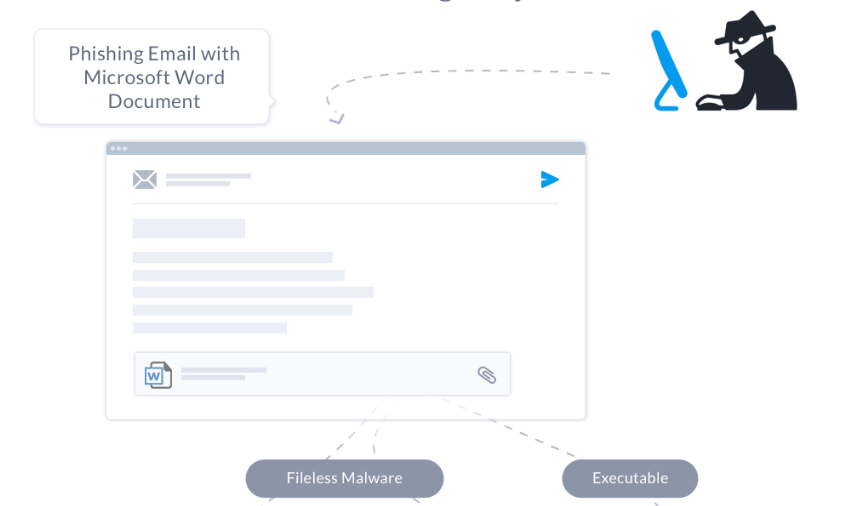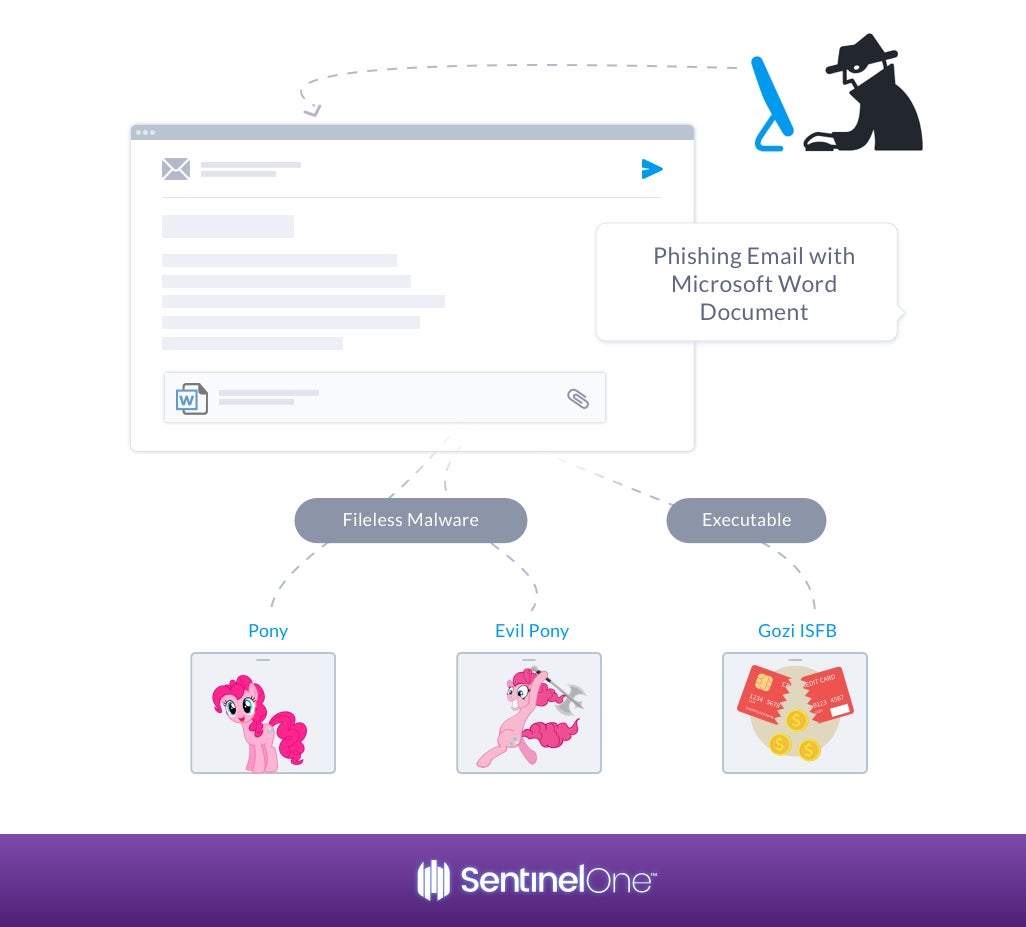
The Hancitor trojan, also known as Chanitor, is a downloader first observed in 2014. Back then, it distributed its payload via a Microsoft Word document email attachment with embedded malicious macros. Over the years, several flavors have been seen in the wild using a variety of infection techniques. A few examples:
- A macro in an attached document contains encoded shellcode and uses native API calls within Visual Basic (VB) to pass execution, carving out and decrypting the embedded malware.
- Another flavor seen in the wild involves a malicious attachment that drops an additional payload to download the Pony/Evil Pony fileless malware or Gozi ISFB executables, which then steals data and connects to a C2 server.
The Hancitor trojan typically uses phishing emails as an infection method. Several phishing email campaigns delivered bogus parking ticket notifications. The message requests the recipient to click the link to pay their ticket and directs the victim to a malicious Microsoft Word document.
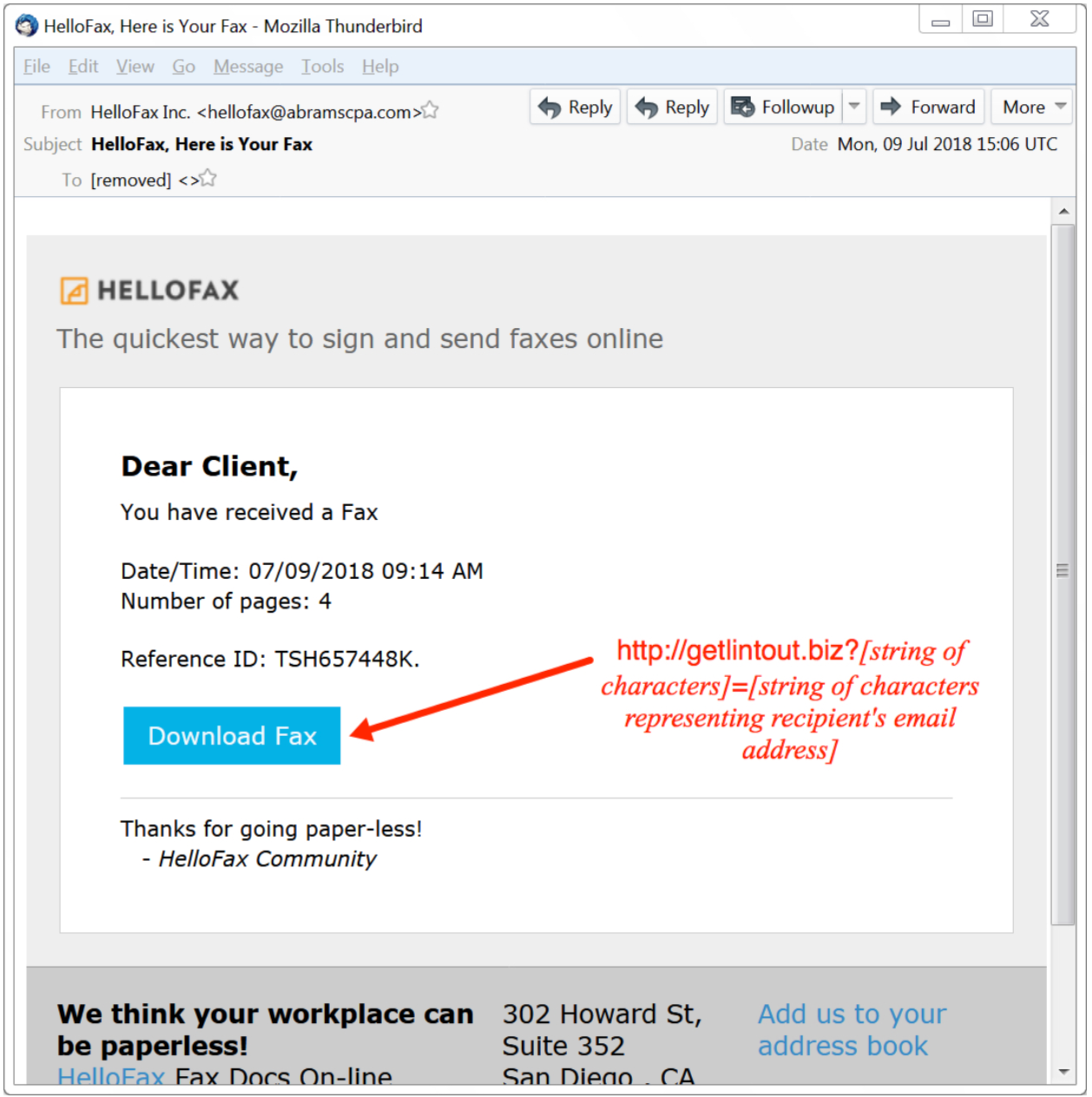
Another common email spam seen is originating from Intuit or HalloFax, encourages the user to download a fax, which then triggers the infection.
SentinelOne Detecting Hancitor Demo
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Want to see how SentinelOne can help improve your security efforts? Request a Demo Now