The autonomous SOC: A well-grounded vision for the future of machine speed, AI-driven cyber defense, or nothing more than a pipe dream? Few concepts in modern security have been as polarizing, with sides painted as distinct camps of “believers” versus “non-believers”, each accompanied by increasingly hyperbolic claims.
At SentinelOne, you will hear us and our customers talk about the autonomous SOC and the fundamental shifts it will bring to day-to-day security operations. Today, we want to be clear about what we mean when we say that.
Like everything in cybersecurity, it’s not the half-sentence definitions that count but rather the real-world applications. The truth of the matter is this: We as a security community have much more in common with each other regarding the vision of AI and automation and where we are on the journey than the pundits and posturing would have you believe.

Aligning on The Common Problem
The main point of common ground is the realities facing the modern SOC. Today’s security teams are up against increasingly complex challenges, including a surge in sophisticated attacks, growing alert volumes, an expanding attack surface, and a shortage of skilled personnel. It’s hardly a stretch to say that at no time has it ever been more difficult for SOC teams to quickly and effectively triage, investigate, and respond to threats than it is today. At the same time, the work that we know would make the most significant difference at scale, like proactive posture management and threat hunting measures, are frequently sidelined due to the time and expertise required.
Defining the Autonomous SOC
Some have posited that the Autonomous SOC is a futuristic human-free hub where machines unilaterally defend an organization against attacks. Is that a possible future? Perhaps someday, but that possibility is, at best, many years away. Better questions might be: What kind of autonomy is desirable, and to what degree can we realize it?
At SentinelOne, we define the Autonomous SOC as a conceptual journey with distinct stages – a journey where machines increasingly augment the work of human SecOps teams by automating manual, laborious work to radically accelerate detection and response. It is a growing area of behavioral and generative AI security innovation with a range of automation types and levels that advance the work of human SOC analysts. By freeing security experts to focus on strategic, high-value work and decisions, these tools maximize the application of human intelligence to security operations. Working in concert with humans means AI and automation become more effective and accurate through a continuous feedback loop. This symbiotic relationship amplifies the strengths of both, transforming the SOC into a more efficient, agile, and intelligent team.
Empowering the Autonomous SOC Journey
The Autonomous SOC vision and concept is deeply embedded in SentinelOne’s product development ethos. We believe the future of cybersecurity lies in empowering security teams with seamlessly integrated AI and automation tools across every SOC workflow to amplify human speed and impact. Our AI innovation is intentionally designed to complement SOC analysts so security teams can confidently adopt autonomous capabilities on their terms, all while future-proofing their security investments.
SentinelOne believes there are critical stages in the Autonomous SOC journey leading towards our ideal of delivering autonomous SecOps capabilities – each designed to align with the natural evolution of security operations. By introducing incremental innovation and improvements, including rules-based automation, AI-enhanced detection, autonomous triage and investigations, and more, we are helping organizations gradually build toward high autonomous security. This step-by-step approach ensures our customers have the tools to advance their own autonomous SOC journey at the pace and direction they choose.
Mapping the Autonomous SOC Maturity Model
At SentinelOne, we see the Autonomous SOC through the lens of a maturity model. We welcome debate on where we, as an industry, are on this evolutionary revolution. We hope most will agree that this is a better way to look at Autonomous SOC innovation and adoption – far better than the binary, all-or-nothing debates that have long fueled analyst, vendor, and industry watcher blogs and keynotes.
Our five-stage model outlines the crucial role of automation and AI in driving advancements and the concrete security tasks that security teams can automate.
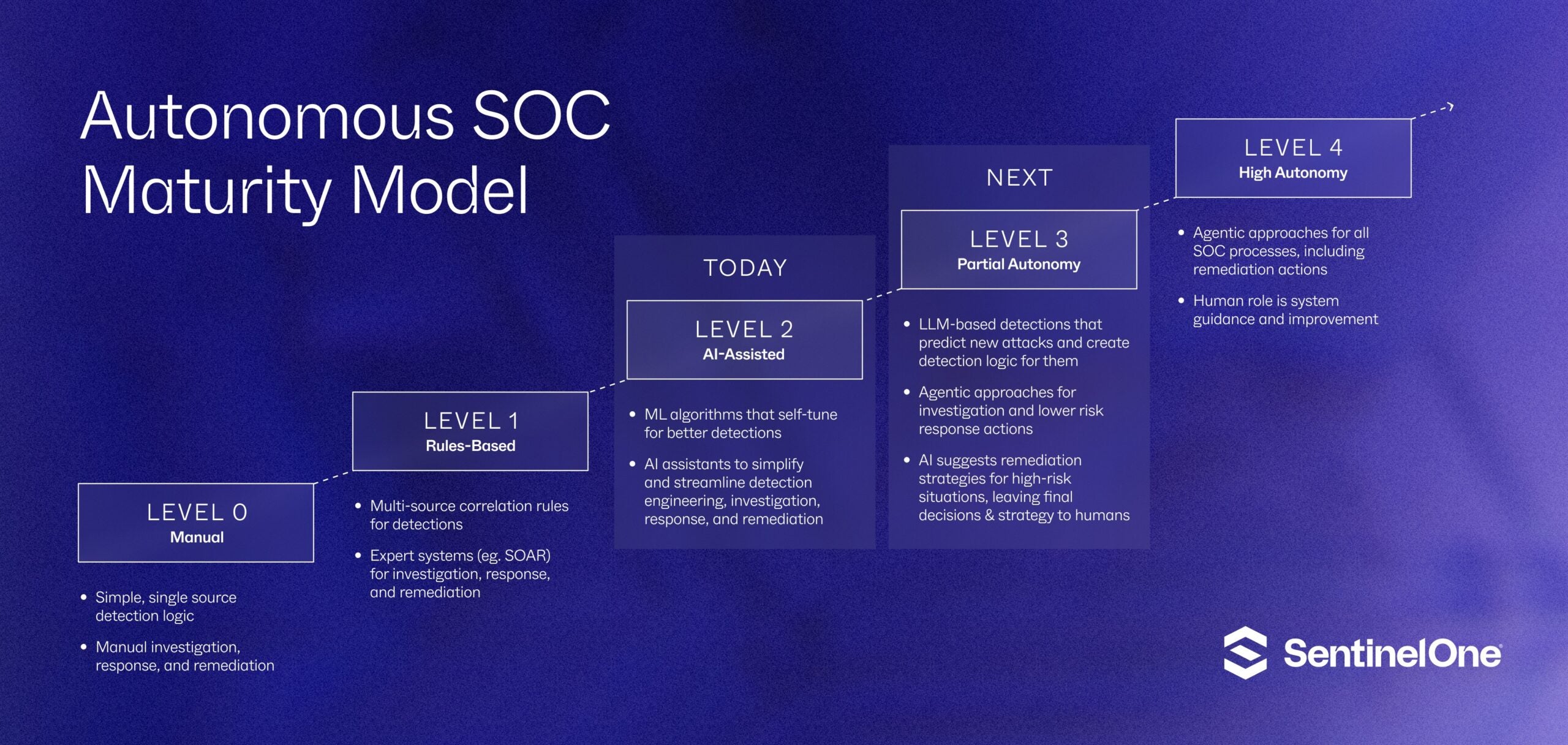
Level 0 | Manual Operations
At Level 0 of the Autonomous SOC Maturity Model, security operations rely heavily on manual processes and simple, single-source detection logic. For instance, a typical scenario might involve an alert from a Fortinet FortiGate firewall signaling suspicious traffic, triggering a lengthy manual investigation. The analyst would need to gather context from various sources, such as network logs or endpoint data, to reconstruct the event. Remediation actions like blocking an IP or isolating a compromised machine are carried out manually.
Threat hunting at this maturity level demands deep expertise and extensive, time-consuming analysis, such as sifting through network logs to identify unusual patterns. Without automation or AI assistance, this labor-intensive approach slows detection and response, increasing the risk of advanced threats evading detection and escalating to a breach.
Level 1 | Rules-Based Operations
At Level 1 of the Autonomous SOC Maturity Model, organizations introduce rules-based detection and response systems. SOCs use correlation rules to combine data from multiple sources, improving the accuracy of threat detections. Security Orchestration, Automation, and Response (SOAR) platforms begin to automate parts of the investigation and response process, reducing the manual workload. At this level, security teams might configure a rule that correlates multiple failed login attempts with a sudden spike in outbound network traffic from the same IP address. This triggers a SOAR system to automatically investigate whether the IP is associated with known threats and, if necessary, quarantine the endpoint.
However, despite these improvements, human expertise remains crucial for designing detection rules and managing response playbooks. To keep pace with the evolving threat landscape, SOC teams must continuously refine these rules for this Level 1 automation to remain relevant.
Level 2 | AI-Assisted Security Operations
At Level 2 of the Autonomous SOC Maturity Model, AI and machine learning (ML) are introduced to elevate SOC operations beyond static rules. AI models for detection engines can self-tune based on supervised feedback or unsupervised learning, improving accuracy and reducing false positives. For example, SentinelOne’s Static AI engine, trained on over half a billion malware samples, can automatically predict whether a file or object is malware based on its characteristics.
AI assistants leverage generative AI to further simplify essential tasks like detection engineering, triage, investigation, and response, enabling analysts to focus on higher-value activities. For example, an AI assistant or virtual security analyst, such as Purple AI, can conduct natural language-based threat investigations or hunting. Analysts can ask plain language questions like, “Have there been any unusual login attempts across the network?” The AI assistant interprets the query, scans through data sources, identifies patterns, and provides prioritized results, eliminating the need for end users to write complex queries or understand the underlying data mapping or fields.
This streamlines the investigation process and makes threat hunting more accessible, even to less experienced team members. By introducing AI, Level 2 enables faster, more accurate responses while continuously learning from past events to adapt to evolving threats.
Level 3 | Partial Autonomy
At Level 3 of the Autonomous SOC Maturity Model, security operations would move toward partial autonomy, with LLM-based systems predicting new attacks and automatically creating detection logic. This is the next logical stage of advancement for industry-leaders. AI systems would also leverage agentic approaches to perform lower-risk response actions, such as creating tickets or forcing re-authentication, while human analysts would focus on supervising AI outputs and handling tasks that require deeper contextual judgment.
For example, during an unseen ransomware attack, an LLM-based system could analyze the malware’s behavior, generate detection rules, suggest verdicts, and autonomously respond by creating a ticket for the asset owner without requiring users to write complex queries or understand data mappings. Meanwhile, human analysts would review AI-generated findings, adjust detection logic where necessary, and validate the overall response strategy. Human experts would manage higher-risk decisions, such as determining whether to escalate or engage in broader incident containment efforts, ensuring the AI’s alignment with security strategy.
Level 4 | High Autonomy
At Level 4, the potential final future stage of the Autonomous SOC Maturity Model, security operations would reach high autonomy. Generally, it is agreed that the timing and possibility of achieving this stage are still in question, with the potential of Level 4 dependent on whether AI models move towards thought reasoning and full artificial general intelligence (AGI).
However, in this potential future hypothetical state, agentic approaches would handle all SOC processes, from detection and investigation to response and remediation, with minimal human intervention. Human analysts would also take on a more strategic role, guiding and refining AI to adapt to emerging threats and maintain resilience.
This model would then enable a 24/7, hands-off approach to security, drastically reducing response times and minimizing the impact of attacks. For example, in a highly autonomous SOC, AI systems could independently detect threats, investigate them, and initiate remediation actions such as rolling back malware-infected systems, revoking compromised credentials, and updating firewall rules.
The Road to the Autonomous SOC
The journey from manual operations to more autonomy in SecOps requires careful planning, investment in AI, and continuous improvement. It also requires aligning on common understandings and rational debate.
We believe that progressing along the journey towards the Autonomous SOC is the future of cybersecurity, where AI and automation reduce workloads, enhance detection accuracy, and improve response times. Achieving high autonomy does require a fundamental shift in perspective. As SOCs advance, the security analyst role shifts from monotonous tasks and laborious hands-on investigations to system supervision and optimization. We see security professionals embracing AI and Autonomous SOC innovation as an amplification of their expertise, not a replacement, ultimately creating a more secure and resilient digital environment.
The tools to start down this path exist today. SentinelOne is one such company innovating in this space with AI and Automation investments in solutions such as Purple AI, AI SIEM, and the broader Singularity platform.
Together, equipped with the latest innovation and human expertise, and empowered by a shared understanding, we can get past the hyperbole and focus on empowering SOCs to protect our organizations, our data, and our people.
This article is intended to provide thought leadership and our latest ideas around the future of cybersecurity and is not intended to be a description of current SentinelOne feature availability.


