CVE-2023-23752 is an authentication bypass vulnerability that allows unauthenticated users to access sensitive information about Joomla! Installation. The vulnerability was found by Zewei Zhang from NSFOCUS TIANJI Lab on February 24, 2023, allowing unauthenticated users to access sensitive information about Joomla! Installation, and was assigned CVS 5.3 medium. It affects Joomla versions 4.0.0 to 4.2.7; the patch was released in version 4.2.8.
CVE-2023-23752 Impact
Affected websites may suffer severe consequences due to this vulnerability. Attackers can exploit it to gain unauthorized access to web service endpoints, which may lead to the leakage of sensitive information such as usernames, passwords, and database names. Furthermore, there is speculation that attackers attempted to use the authentication bypass vulnerability to execute code.
Attackers exploit this vulnerability by using the authentication bypass to leak the system’s configuration. This reveals Joomla! MySQL database credentials are in plaintext, which attackers can use to gain further access to the system.
In February 2023, a Chinese-language blog shared the technical details of the vulnerability and described it as an authentication bypass that allows an attacker to leak privileged information. Following the blog’s disclosure, a stream of exploits hit GitHub, and multiple indicators of exploitation appeared in the wild.
The public exploits focus on leaking the victim’s MySQL database credentials. Most public exploits use the bypass to reveal the system’s configuration, which contains the Joomla! MySQL database credentials in plaintext.
Threat Detection using FOFA
A series of exploits targeting the vulnerability appeared on GitHub, and there were multiple indicators of exploitation in the wild. However, these exploits focused on leaking the victim’s MySQL database credentials, which is not particularly exciting as it is generally considered a dangerous misconfiguration to expose a database to the internet.
Nevertheless, attackers appeared interested in the vulnerability, prompting us to investigate further.
To determine the significance of the vulnerability, we examined the number of internet-facing systems that were affected by it.
Using FOFA, we found approximately 7.5 lacks internet-facing Joomla! Installations.
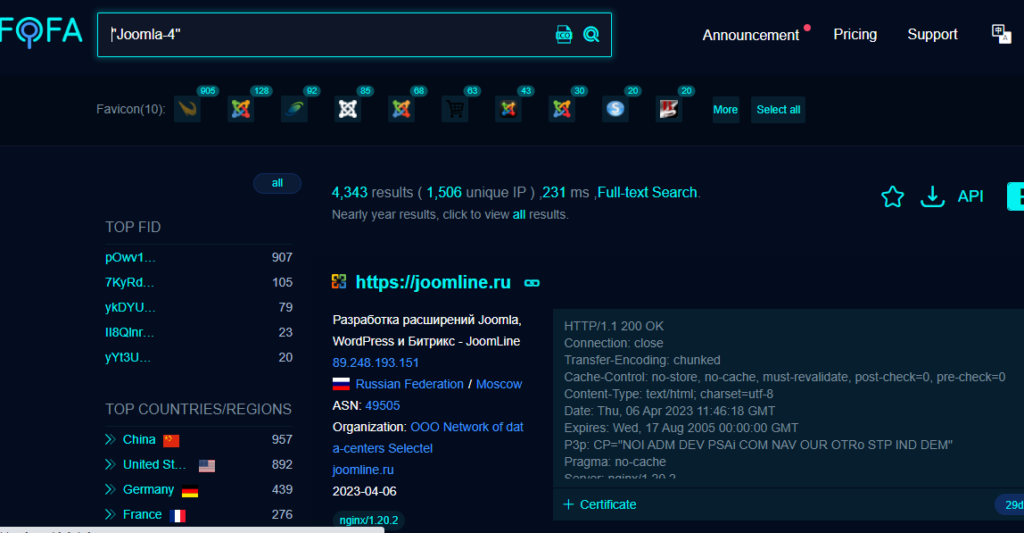
However, after sorting the Joomla installation by version 4.0 indexed by FOFA, we discovered that Joomla! 4 was not very popular, with only around 4k results responding to Joomla! Instances using that version.
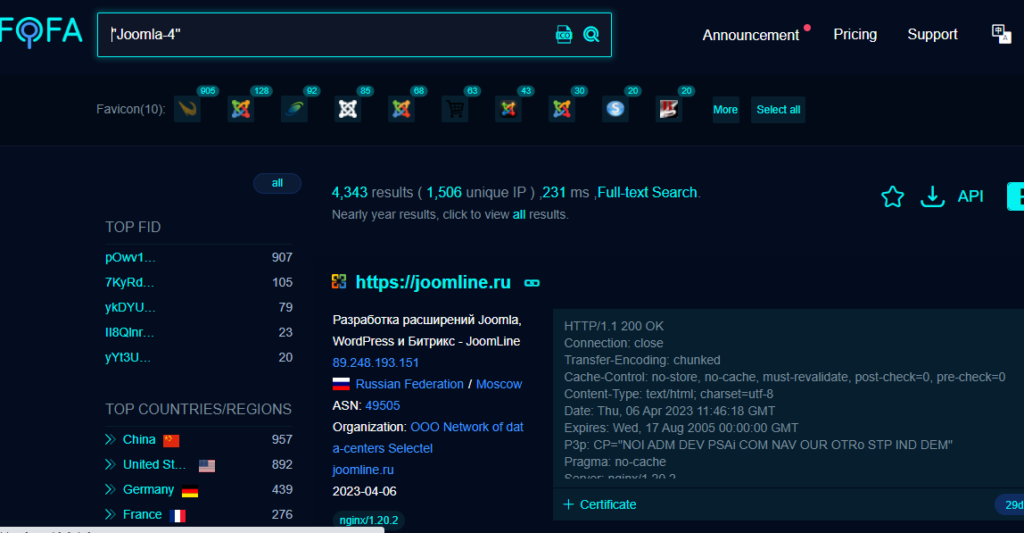
Furthermore, only a few of the responding Joomla! Servers remained vulnerable to the attack, which amounted to fewer than 500 internet-facing installations.
Based on the versions of Joomla! In using internet-facing systems, we conclude that while the vulnerability was dangerous, it was never a significant issue. Despite this, attackers continued to show interest in the vulnerability and posted new exploits on GitHub.
CVE-2023-23752 Exploitation
The public exploits for CVE-2023-23752 mostly used the authentication bypass to leak the system’s configuration, which contained the Joomla! MySQL database credentials in plaintext. This information could be accessed remotely by querying the /language/en-GB/langmetadata.xml or /administrator/manifests/files/joomla.xml endpoints without authentication.
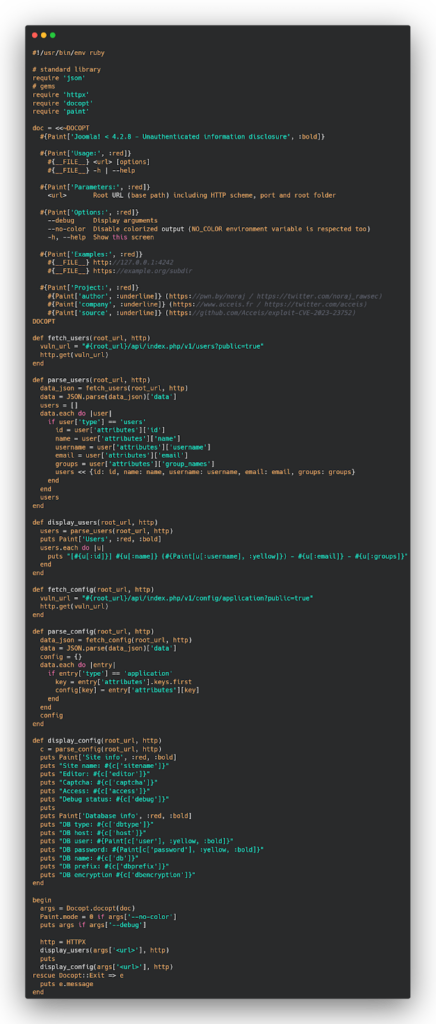
This is a Ruby script for exploiting the Joomla unauthorized access vulnerability (CVE-2023-23752) that allows an attacker to disclose sensitive information, such as user credentials and site configuration details, without authentication.
The script takes the root URL of the target Joomla site as an argument and uses the Joomla API to fetch and display user details and site configuration information.
The script uses the HTTPX gem to make requests and the Docopt gem to handle command-line arguments. Finally, the user details and site configuration information are displayed using the Paint gem to format the output.
POC steps to reproduce
- Clone the GitHub exploit repo from here and set up a Joomla cluster with a vulnerable version, v4.2.7, using docker.
- Now execute the following command: docker-compose up –build.
- When the cluster is started, browse the Web console on http://127.0.0.1:4242/installation/index.php.
- Complete the installation by entering credentials (db credentials are root / MYSQL_ROOT_PASSWORD (cf. docker-compose.yml), and the host is MySQL, not localhost).
- Get the requirements installed for the ruby script(make sure you install ruby in your system) by running any of the following commands
gem install httpx docopt paint
#or
bundle install
- Now run the Ruby script and check the required parameters by running the following command: ruby exploit.rb -h
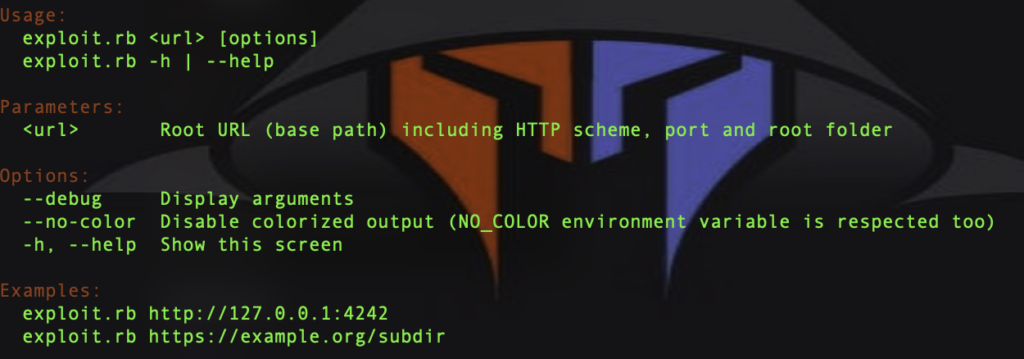
- Now execute the exploit script with the vulnerable Joomla url parameter.
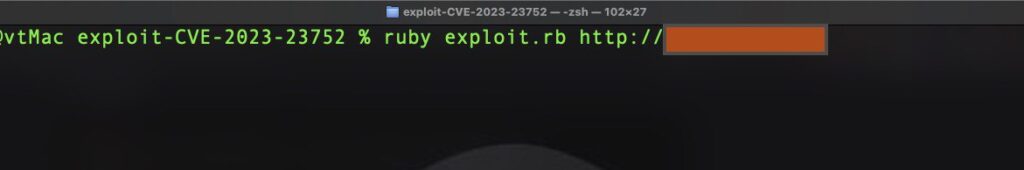

- The exploit was a success and got the desired results.
CVE-2023-23752 Mitigation
The best way to mitigate this vulnerability is to update your Joomla! Software to a version that is not affected by this issue. If you are using Joomla Versions 4.0.0 through 4.2.7, updating your software as soon as possible is crucial to protect against this vulnerability.
Conclusion
In summary, CVE-2023-23752 is a severe vulnerability that can leak sensitive information.
While the CVE-2023-23752 vulnerability was potentially dangerous, it did not affect any internet-facing systems. However, it is crucial for users of affected Joomla! Versions to update their software to a version that is not vulnerable.