Organizations have the practice of using the same password for local administrator accounts across all domain-joined computers. Such accounts are vulnerable to credential theft attacks like Pass-the-Hash (PtH) attacks. Microsoft’s Local Administrator Password Solution(LAPS) simplifies password management and stores passwords centrally in the existing Active Directory (AD) infrastructure.
Organizations can implement defenses against cyberattacks by looking at the security risks associated with LAPS misconfigurations and remediating them.
Why is LAPS so important?
Attackers can capture account login credentials from a compromised endpoint and then use those captured credentials to perform lateral movement throughout the network. One way to reduce lateral attacks in a network is to remove common local administrator passwords.
LAPS solution mitigates the risk of lateral movement and privilege escalation resulting from an organization using the same local administrator account and password combination on computer systems. LAPS provides local account password management for domain-joined systems. The following are key features of LAPS related to security and manageability:
Key Features of LAPS
- Randomly generate local administrator passwords and securely store them in the Active Directory(AD) infrastructure.
- Effectively mitigate PtH attacks that rely on identical local account passwords.
- Use access control lists (ACLs) to protect passwords in AD.
- Configure password parameters, including age, complexity, and length.
- Force password reset on a per-machine basis.
- Protect against computer account deletion.
What are the security risks with LAPS?
While organizations can benefit from implementing LAPS in an AD environment, they must manage LAPS configurations properly. A misconfiguration can leave them exposed to attacks, such as attackers dumping LAPS passwords in clear-text and poisoning AdmPwd.dll for malicious intent. The following security risks exist with LAPS misconfigurations.
Security Risk 1: Dumping of LAPS password in clear text
LAPS uses a Group Policy client-side extension (CSE) on managed computers to perform all management tasks. The LAPS initial install includes schema extensions that add the following two new attributes for computer objects in Active Directory:
- ms-mcs-AdmPwd: This attribute is a clear-text password, can only be viewed by Domain Admins by default.
- ms-mcs-AdmPwdExpirationTime: This attribute indicates the date/time when the password gets expires.
The first security risk lies with LAPS attribute delegation and permissions on the objects. Attackers can enumerate accounts on the compromised endpoints and misuse their permissions to view the LAPS passwords of local administrators. A security administrator must configure Group Policy Object (GPO) to enable and configure LAPS management of local administrator account. Setting the LAPS GPO setting, “Do not allow password expiration time longer than required by policy” to “Enabled,” as shown in the below image, can prevent attackers from enumerating attributes.
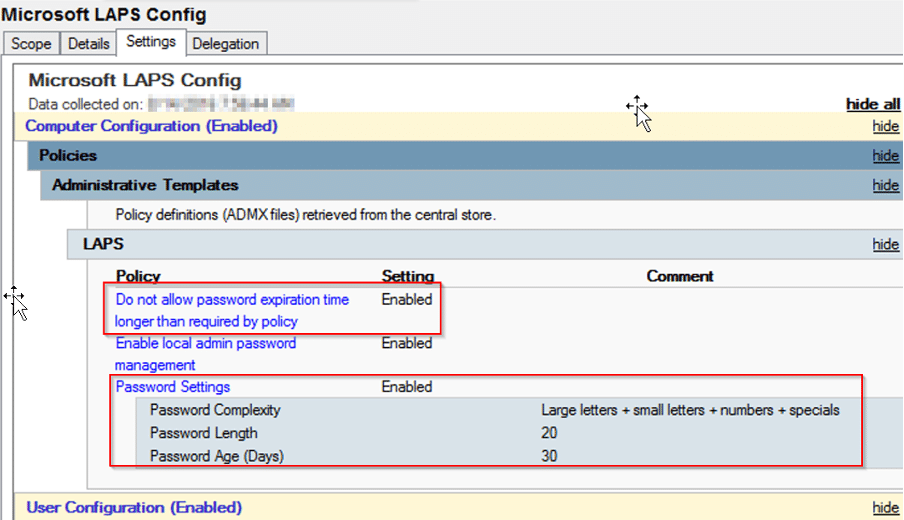
The next recommended step is to configure LAPS password settings. The “Password Settings” configures parameters like password complexity, length, and expiration date. This step is very important to ensure LAPS passwords are complex enough and changed frequently.
Security Risk 2: Poisoning AdmPwd.dll
Installing the LAPS client configures the Group Policy Client Side Extension (CSE) on the computer. The CSE runs admpwd.dll to manage passwords. The admpwd.dll is located in c:program filesLAPSCSE and configured in the registry under
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsNTCurrentVersionWinlogonGPExtensions.
Once an attacker gets a foothold on the victim’s endpoint, they can identify if LAPS is present by using the PowerShell cmdlet “Get-ChildItem’ c:program filesLAPSCSEAdmpwd.dll’”. An attacker can poison the DLL and create a backdoor to read the password in plain text.
The organization should check the hash and validate the digital signature on the LAPS DLL to prevent exploitation.
- Get-FileHash ‘c:program filesLAPSCSEAdmpwd.dll’
- Get-AuthenticodeSignature ‘c:program filesLAPSCSEAdmpwd.dll’
Security Risk 3: Modifying searchFlags attribute
The third risk associated with LAPS is proper identification of the “searchFlags” attribute for ms-Mcs-AdmPwd. An attacker can change the “searchFlag” attribute value to 776 (0x308) from 904 (0x388). By doing so, anyone can read the LAPS password and further extend their attack. Microsoft documented all valid search flags usage on the attributes here.
Microsoft recommends removing the “All Extended Rights” permission by following the steps below.
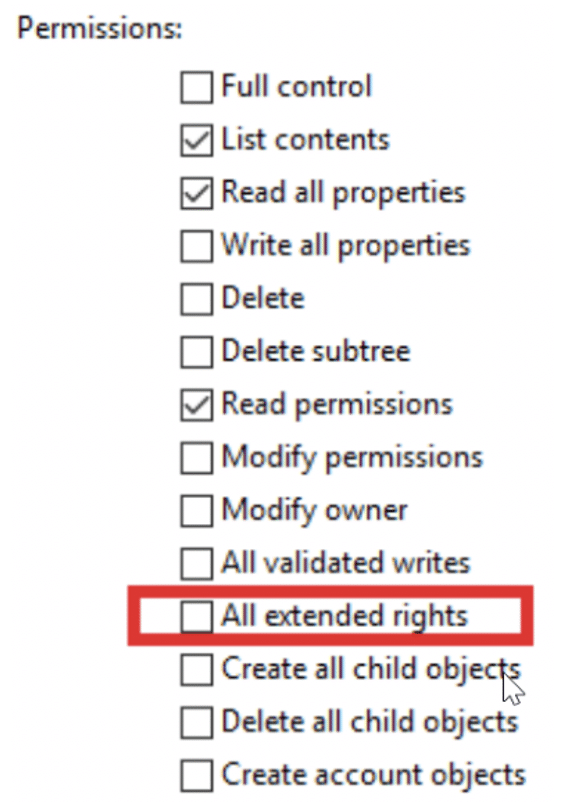
- Navigate to Active Directory Users and Computers.
- Right-Click on the OU that contains the computer accounts with the LAPS solution enabled and select Properties.
- Click on the Security tab->Advanced.
- Select the Group(s) or User(s) to modify permissions for and edit.
- Uncheck the “All Extended Rights” checkbox.
This procedure will prevent users and groups from viewing confidential attributes, including the LAPS attribute ms-mcs-admpwd, containing the clear text password.
Conclusion
Organizations should consider LAPS as part of a credential theft mitigation strategy. Enabling LAPS is just one part, but continuous assessment and validation of LAPS configurations can avoid being vulnerable to lateral movement and privilege escalations.
Singularity™ Ranger AD is a cloud-delivered solution designed to uncover vulnerabilities in Active Directory and Azure AD. Get additional AD attack detection and conditional access capabilities to protect enterprise identity infrastructure with Singularity Ranger AD Protect.


